- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: ASA5505 This deployment possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2011 02:02 AM - edited 03-11-2019 12:51 PM
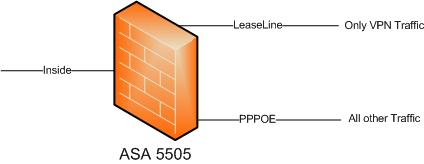
Hi all,
can i do this with the ASA5505?
i plan to use the Lease Line only for VPN Traffic and the PPPOE Line for Internet Traffic.
Config
interface Vlan1
nameif inside
security-level 100
ip address 172.20.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 80.118.x.x 255.255.255.248
!
interface Vlan3
nameif vpn
security-level 0
pppoe client vpdn group DialOut
ip address pppoe setroute
!object network NETWORK_OBJ_172.20.1.0
subnet 172.20.1.0 255.255.255.0
object network NETWORK_OBJ_10.0.1.0
subnet 10.0.1.0 255.255.255.0
object network Use_For_Internet
subnet 172.20.1.0 255.255.255.0
!
object network Use_For_Internet
nat (inside,outside) dynamic interface
!
access-list outside_1_cryptomap extended permit ip object NETWORK_OBJ_172.20.1.0 object NETWORK_OBJ_10.0.1.0
access-list inside_access_in extended permit ip object NETWORK_OBJ_172.20.1.0 object NETWORK_OBJ_10.0.1.0
!
nat (inside,vpn) source static NETWORK_OBJ_172.20.1.0 NETWORK_OBJ_172.20.1.0 destination static NETWORK_OBJ_10.0.1.0 NETWORK_OBJ_10.0.1.0
!
access-group inside_access_in in interface inside
access-group global_access global
!route vpn 62.24.x.x 255.255.255.255 80.118.x.x 1
-- Route to VPN Peer --
or
route vpn 0.0.0.0 0.0.0.0 80.118.x.x 1 tunneled
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group5
crypto map outside_map 1 set peer 62.24.x.x
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map outside_map interface vpn
crypto isakmp enable vpn
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
tunnel-group 62.24.x.x type ipsec-l2l
tunnel-group 62.24.x.x ipsec-attributes
pre-shared-key <KEY>
!
i know that the ASA does not support PBR and load balancing.
mfg
Michael
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2011 02:08 AM
It is only possibly if you only have static site-to-site VPN, other types of VPN, ie dynamic site-to-site or remote access vpn client are not supported as you can't configure 2 default gateways out 2 interfaces on an ASA.
Also, the following route is incorrect:
route vpn 0.0.0.0 0.0.0.0 80.118.x.x 1 tunneled
The "tunneled" keyword is only used when you would like to push VPN traffic that has been decrypted through an specific internal default gateway. It is not used for encrypted traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2011 02:08 AM
It is only possibly if you only have static site-to-site VPN, other types of VPN, ie dynamic site-to-site or remote access vpn client are not supported as you can't configure 2 default gateways out 2 interfaces on an ASA.
Also, the following route is incorrect:
route vpn 0.0.0.0 0.0.0.0 80.118.x.x 1 tunneled
The "tunneled" keyword is only used when you would like to push VPN traffic that has been decrypted through an specific internal default gateway. It is not used for encrypted traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2011 02:16 AM
Ok,
yes i plan only site-to-site VPN with Static IP address.
Then i must write for all VPN Peers static routes. That is ok.
route vpn 1.1.1.1 255.255.255.255 80.118.x.x 1
route vpn 2.2.2.2 255.255.255.255 80.118.x.x 1
route vpn 3.3.3.3 255.255.255.255 80.118.x.x 1
Is planned to implement in the future PBR and SBR?
mfg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-17-2011 02:20 AM
Yes, that is correct then. You will need to configure static route for each of the peer as you have.
No, I personally haven't heard of any plan to include PBR or SBR on ASA.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


