- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cannot ping outside from ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 07:22 PM
Cannot ping outside from ASA 5510
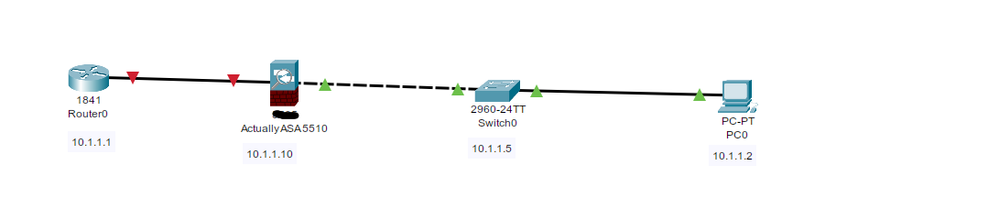
Network Topology
Problem Description
"ping" only got timeout error between Router(10.1.1.1) and ASA5510(10.1.1.10)
Any two devices can ping each other except them.
And ASA cannot ping the Internet too.
I Have Tried
- Reboot everyone
- Check if ACL block the traffic
- ICMP inspection configed
Error Information
Ping Fail:
CYA-Cisco-ASA5510# ping 10.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds: ????? Success rate is 0 percent (0/5)
ASA Debug:
CYA-Cisco-ASA5510# show logging | i 10.1.1.1 Jan 02 2003 12:00:25 CYA-Cisco-ASA5510 : %ASA-6-302020: Built outbound ICMP connection for faddr 10.1.1.1/0 gaddr 10.1.1.10/54097 laddr 10.1.1.10/54097 Jan 02 2003 12:00:35 CYA-Cisco-ASA5510 : %ASA-5-111008: User 'enable_15' executed the 'ping 10.1.1.1' command. Jan 02 2003 12:00:35 CYA-Cisco-ASA5510 : %ASA-6-302021: Teardown ICMP connection for faddr 10.1.1.1/0 gaddr 10.1.1.10/54097 laddr 10.1.1.10/54097
Packet Capture:
CYA-Cisco-ASA5510(config)# show capture capin 10 packets captured 1: 11:28:35.458853 10.1.1.10 > 10.1.1.1: icmp: echo request 2: 11:28:35.459754 10.1.1.1 > 10.1.1.10: icmp: echo reply 3: 11:28:37.450385 10.1.1.10 > 10.1.1.1: icmp: echo request 4: 11:28:37.451270 10.1.1.1 > 10.1.1.10: icmp: echo reply 5: 11:28:39.450355 10.1.1.10 > 10.1.1.1: icmp: echo request 6: 11:28:39.451209 10.1.1.1 > 10.1.1.10: icmp: echo reply 7: 11:28:41.450355 10.1.1.10 > 10.1.1.1: icmp: echo request 8: 11:28:41.451255 10.1.1.1 > 10.1.1.10: icmp: echo reply 9: 11:28:43.450355 10.1.1.10 > 10.1.1.1: icmp: echo request 10: 11:28:43.451240 10.1.1.1 > 10.1.1.10: icmp: echo reply 10 packets shown
Useful Information
- ASA 5510 works in transparent mode
Config File:
: Saved : : Serial Number: XXXXXXXX : Hardware: ASA5510, 1024 MB RAM, CPU Pentium 4 Celeron 1599 MHz : ASA Version 8.2(5)59 ! firewall transparent hostname CYA-Cisco-ASA5510 enable password XXXXXXXX encrypted passwd XXXXXXXX encrypted names dns-guard ! interface Ethernet0/0 nameif outside security-level 0 ! interface Ethernet0/1 nameif inside security-level 100 ! interface Ethernet0/2 shutdown no nameif no security-level ! interface Ethernet0/3 shutdown no nameif no security-level ! interface Management0/0 shutdown no nameif no security-level management-only ! boot system disk0:/asa825-59-k8.bin ftp mode passive clock timezone CST 8 same-security-traffic permit inter-interface access-list out extended permit ospf any any access-list out extended permit esp any any access-list out extended permit tcp any any access-list out extended permit udp any any access-list out extended permit icmp any any access-list in extended permit ospf any any access-list in extended permit esp any any access-list in extended permit tcp any any access-list in extended permit udp any any access-list in extended permit icmp any any access-list 100 extended permit icmp any any echo-reply access-list 100 extended permit icmp any any source-quench access-list 100 extended permit icmp any any unreachable access-list 100 extended permit icmp any any time-exceeded pager lines 24 logging enable logging timestamp logging buffer-size 102400 logging asdm-buffer-size 512 logging console errors logging monitor informational logging buffered debugging logging trap warnings logging asdm notifications logging device-id hostname mtu outside 1500 mtu inside 1500 ip address 10.1.1.10 255.255.255.0 no failover icmp unreachable rate-limit 1 burst-size 1 icmp deny any outside icmp permit any outside asdm image disk0:/asdm-621.bin no asdm history enable arp timeout 14400 access-group out in interface outside access-group out out interface outside access-group in in interface inside access-group in out interface inside route outside 0.0.0.0 0.0.0.0 10.1.1.1 2 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy aaa authentication ssh console LOCAL aaa authentication http console LOCAL http server enable http 10.1.1.0 255.255.255.0 inside no snmp-server location no snmp-server contact no snmp-server enable crypto ipsec security-association lifetime seconds 28800 crypto ipsec security-association lifetime kilobytes 4608000 telnet timeout 5 ssh 0.0.0.0 0.0.0.0 outside ssh 0.0.0.0 0.0.0.0 inside ssh timeout 5 ssh version 2 console timeout 0 threat-detection basic-threat threat-detection scanning-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept username XXXXXXXX password XXXXXXXX encrypted ! class-map inspection_default ! ! policy-map global_policy class inspection_default inspect icmp inspect ip-options ! prompt hostname context no call-home reporting anonymous call-home profile CiscoTAC-1 no active destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address email callhome@cisco.com destination transport-method http subscribe-to-alert-group diagnostic subscribe-to-alert-group environment subscribe-to-alert-group inventory periodic monthly subscribe-to-alert-group configuration periodic monthly subscribe-to-alert-group telemetry periodic daily Cryptochecksum:fab62ad2e20c7144860c5b6e20f797de : end
Solved! Go to Solution.
- Labels:
-
ACI
-
Device Admin
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 11:44 PM
@sfc9982 this configuration does not look complete for transparent mode.
There is no BVI configured.
None of the interfaces appear to have been configured with the IP address 10.1.1.10. The only reference I can find for that IP address is right in the middle of the configuration, copy and paste error?
mtu outside 1500 mtu inside 1500 ip address 10.1.1.10 255.255.255.0 no failover icmp unreachable rate-limit 1 burst-size 1
Use this as a reference guide.
https://integratingit.wordpress.com/2021/05/30/asa-transparent-mode/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 12:01 AM
I know what happened, Bridge Group need ASA 8.4, I'm 8.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 09:05 PM
HI,
You need
- icmp permit any inside
- icmp permit any outside
icmp permit any inside allows inside devices and asa to ping each other
icmp permit any outside allows outside devices and asa to ping each other
In your config you have "icmp deny any outside" which is preventing the asa from pinging the outside and the outside pinging the asa
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 09:25 PM - edited 04-11-2022 09:27 PM
I removed icmp deny any outside and add permit, but still got timeout
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 10:28 PM
Hi,
How is your network configured? What is the ip address of the ASA firewall and on what interface. Are you using the management interface?
Thanks
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 10:33 PM
See picture above.
Management interface is not used
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 11:44 PM
@sfc9982 this configuration does not look complete for transparent mode.
There is no BVI configured.
None of the interfaces appear to have been configured with the IP address 10.1.1.10. The only reference I can find for that IP address is right in the middle of the configuration, copy and paste error?
mtu outside 1500 mtu inside 1500 ip address 10.1.1.10 255.255.255.0 no failover icmp unreachable rate-limit 1 burst-size 1
Use this as a reference guide.
https://integratingit.wordpress.com/2021/05/30/asa-transparent-mode/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2022 11:59 PM
But in interface config, there isnt an "bridge-group" option
CYA-Cisco-ASA5510(config-if)# ?
Interface configuration commands:
default Set a command to its defaults
description Interface specific description
duplex Configure duplex operation
exit Exit from interface configuration mode
flowcontrol Configure flowcontrol operation
help Interactive help for interface subcommands
ipv6 IPv6 interface subcommands
mac-address Assign MAC address to interface
nameif Assign name to interface
no Negate a command or set its defaults
security-level Specify the security level of this interface after this
keyword, Eg: 0, 100 etc. The relative security level between
two interfaces determines the way the Adaptive Security
Algorithm is applied. A lower security_level interface is
outside relative to a higher level interface and equivalent
interfaces are outside to each other
shutdown Shutdown the selected interface
speed Configure speed operationCYA-Cisco-ASA5510(config-if)# bridge-group 123
^
ERROR: % Invalid input detected at '^' marker.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 12:02 AM
@sfc9982 then it probably isn't supported in Packet Tracer simulator, not all features are unfortunately.
You'd need to use physical hardware or EVE-NG with ASAv image.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 12:03 AM
No, I'm using a physical machine. the Packet Tracer is for showing network strcuture.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 12:01 AM
I know what happened, Bridge Group need ASA 8.4, I'm 8.2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2022 03:01 AM - edited 04-12-2022 08:33 AM
Thanks for sharing the solution.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide