- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco ASA 5506-X PAT to interface problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2020 05:10 AM - edited 03-04-2020 06:43 AM
Hi people,
I hope somebody can help me. I don't know what to do =(
Cisco ASA5506-X (9.9(2)36)
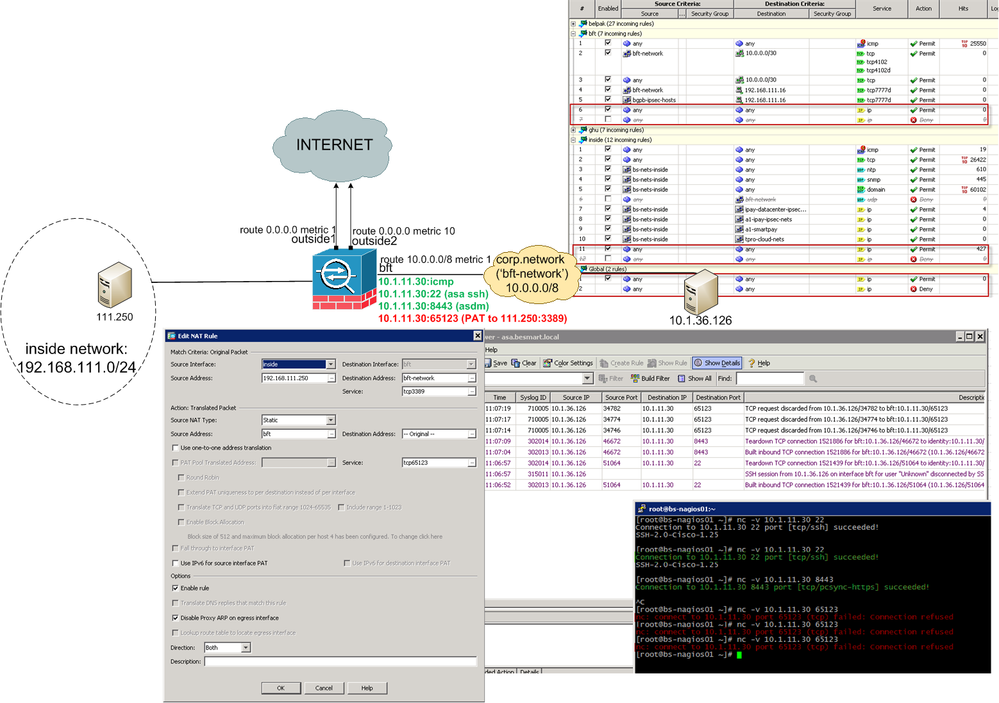
I have 3 outside interfaces: two for internet (security level 0) and third one (name 'bft', security level 10, but I tried set 0 as well) connected to corporate network (10.0.0.0/8). + inside interface (192.168.111.0/24, sec.level 100)
When I create PAT to my 'BFT' interface I can't access it from other side of corporate network;
nat (inside,bft) 46 source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123
, where bft-network = 10.0.0.0/8
TCP request discarded from 10.1.36.126/59802 to bft:10.1.11.30/65123
I applied allow any IP traffic on all my interfaces, but without luck.
If I ping 10.1.11.30 or access ASDM/SSH ports - no problems.
packet-tracer input bft tcp 10.1.36.126 59802 10.1.11.30 65123 detailed:
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.11.30 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac19858c0, priority=0, domain=nat-per-session, deny=false
hits=11579208, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2c6a640, priority=0, domain=permit, deny=true
hits=130, user_data=0xa, cs_id=0x0, use_real_addr, flags=0x1000, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=bft, output_ifc=any
Result:
input-interface: bft
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rulepacket-tracer input bft icmp 10.1.36.126 8 0 10.1.11.30
Phase: 1 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 10.1.11.30 using egress ifc identity Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: Phase: 3 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 4 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 5 Type: CLUSTER-REDIRECT Subtype: cluster-redirect Result: ALLOW Config: Additional Information: Phase: 6 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 7 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 8 Type: VPN Subtype: ipsec-tunnel-flow Result: ALLOW Config: Additional Information: Phase: 9 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 10969831, packet dispatched to next module Phase: 10 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 0.0.0.0 using egress ifc identity Phase: 11 Type: ADJACENCY-LOOKUP Subtype: next-hop and adjacency Result: ALLOW Config: Additional Information: adjacency Active next-hop mac address 0000.0000.0000 hits 3167600 reference 119 Result: input-interface: bft input-status: up input-line-status: up output-interface: NP Identity Ifc Action: allow
If I make PAT not into BFT interface, but into additional IP address on the interface - PAT works!
I have no problem with PAT to others uplink interfaces.
Tried the same scenario on my second ASA 5506-X version 9.8.2.20 without luck.
Could somebody help please??
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 03:54 PM
Recreate interface fixed and all releated objects (IPSecs, NATs, ACLs, Routes and etc.) fixed my glitch.
Thank you very much to anyone who tried to help me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2020 07:17 PM
Can you explain what you to do?
Nat any inside to bft interface?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2020 10:02 PM
I'm trying to make port mapping (for example)
Inside host (192.168.111.250):3389 ---> BFT-interface (10.1.11.30):65123 in direction to bft-network (10.0.0.0/8).
ASA discards income connections as explained in first message.
It seems ASA don't let me make PAT to interface BFT (10.1.11.30), but allows PAT to others outside interfaces which have public 'white' IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 12:23 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 12:52 AM
Hi,
Post your interface configuration, NAT configuration, ACL configuration for ACL's applied globally or at interface level and the access-group commands.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 02:04 AM
Hi Cristian,
Thank you very much for respond.
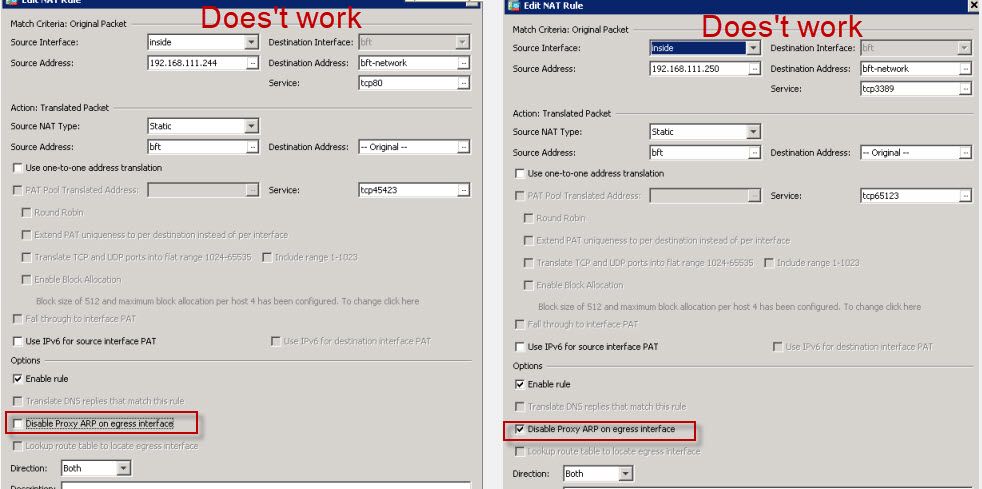
Please keep in mind, I tried to PAT to 'bft' interface different ports from different inside hosts without luck.=(
Here is my full config (all sensitive data have been wiped):
: Saved
:
: Serial Number: -------
: Hardware: ASA5506, 4096 MB RAM, CPU Atom C2000 series 1250 MHz, 1 CPU (4 cores)
: Written by yury at 12:38:53.070 AST Thu Mar 5 2020
!
ASA Version 9.9(2)36
!
hostname bs-asa5506x
domain-name mydomain.by
enable password *******
passwd ****** encrypted
names
name 172.17.19.0 vpn-client-netwotk
name 192.168.115.0 bgpb-ipsec-net
name 212.98.YY.XX trsbk-ipsec-host
name 192.168.3.0 datacenter-ipsec-net
name 10.1.40.82 trsbk-ipsec-gw
name 10.1.5.29 bgpb-ipsec-gw
name 10.16.0.142 life-ussd-host
name 82.209.YY.XX belpack.stand.bs description For incoming testings
name 82.209.YY.XX belpack.work.bs
name 93.125.XXX.XXX ghu.bs
name 192.168.233.32 dkv-network
name 81.30.YY.XX life-smsc
name 10.117.10.0 uis-network
name 192.168.111.40 George_Lan
name 192.168.4.0 datacenter-dmz-ipsec-network
name 192.168.111.0 inside-network
name 172.16.192.0 interlink-nework description link to mikrotik
name 172.16.177.0 bs-users-network
name 172.16.61.0 ipy-network
name 10.7.7.64 vtbk-stand description VTB-Bank stand
name 172.16.177.40 George_Wifi description George_Wifi
name 172.16.10.0 autopark-network
name 192.168.1.0 ticketpro-inside
name 172.19.21.0 ticketpro-dmz
name 172.31.255.1 partner1-ipsec-host
name 192.168.200.0 parking-mogilev7601
name 10.93.1.24 blil-stand
name 93.85.YY.XX access.mnssis.blil.by
name 172.18.152.0 parking-grodno401
name 172.22.22.0 multicarta-ipsec-net
name 10.54.0.0 erip-network
name 10.0.0.0 bft-network
name 10.9.1.2 paritet-host
name 172.17.191.0 datacenter-vpn-ipsec-net description cod vpn pool
name 172.30.71.0 bps-ipsec-net
name 172.17.176.0 stylesoftvpnpool
name 192.168.203.0 parkomats-vpn-pool
name 192.168.191.0 a1-ipy-ipsec-dmz
name 172.17.18.0 a1-ipy-ipsec-inside
name 172.16.61.131 d.vyrvich
name 172.17.18.32 a1-smartpay-inside
name 192.168.191.32 a1-smartpay-dmz
name 172.17.18.64 tpro-inside
name 192.168.192.0 a1-ipy-border
ip local pool VPNClientPool 172.17.19.100-172.17.19.200 mask 255.255.255.0
!
interface GigabitEthernet1/1
nameif belpak
security-level 0
ip address 82.209.XXX.XXX 255.255.255.248
!
interface GigabitEthernet1/2
nameif ghu
security-level 5
ip address ghu.bs 255.255.255.224
!
interface GigabitEthernet1/3
nameif bft
security-level 30
ip address 10.1.11.30 255.255.255.252
!
interface GigabitEthernet1/4
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8.1
vlan 192
nameif inside
security-level 100
ip address 172.16.192.2 255.255.255.0
!
interface Management1/1
description Mgmt
management-only
nameif mgmt
security-level 100
ip address 192.168.11.254 255.255.255.248
!
ftp mode passive
clock timezone AST 3
dns domain-lookup inside
dns server-group DefaultDNS
name-server 192.168.111.246 inside
name-server 192.168.111.247 inside
domain-name mydomain.local
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network datacenter-ipsec-net
subnet 192.168.3.0 255.255.255.0
object network datacenter-dmz-ipsec-net
subnet 192.168.4.0 255.255.255.0
object network vpn-client-net
subnet 172.17.19.0 255.255.255.0
object network bps-ipsec-net
subnet 172.30.71.0 255.255.255.0
object network paritet-host
host 10.9.1.2
object network erip-network
subnet 10.54.0.0 255.255.0.0
object network multicarta-ipsec-net
subnet 172.22.22.0 255.255.255.0
object network parking-grodno401
subnet 172.18.152.0 255.255.255.240
object network access.mnssis.blil.by
host 93.85.92.194
object network blil-stand
host 10.93.1.24
object network parking-mogilev7601
subnet 192.168.200.0 255.255.255.0
object network partner1-ipsec-host
host 172.31.255.1
object network vtbk-stand64
host 10.7.7.64
object network life-smsc
host 81.30.80.42
object network dkv-network
subnet 192.168.233.32 255.255.255.224
object network ipy-net
subnet 172.16.61.0 255.255.255.0
object network users-net
subnet 172.16.177.0 255.255.255.0
object network servers-net
subnet 192.168.111.0 255.255.255.0
object network mgmt-net
subnet 172.16.154.0 255.255.255.0
object network datacenter-vpn-ipsec-net
subnet 172.17.191.0 255.255.255.224
object network belpack.work.bs
host 82.209.233.251
object network belpack.stand.bs
host 82.209.233.252
object network 192.168.111.2
host 192.168.111.2
object service ssh22
service tcp source eq ssh
object service ftp21
service tcp source eq ftp
object network 192.168.111.246
host 192.168.111.246
object service http9080
service tcp source eq 9080
object network 192.168.111.72
host 192.168.111.72
object service tcp8090
service tcp source eq 8090
object service tcp8443
service tcp source eq 8443
object network boil-stand
host 10.93.1.24
object network 192.168.181.0
subnet 192.168.181.0 255.255.255.0
object network 192.168.182.1
host 192.168.182.1
object network 172.17.221.100
host 172.17.221.100
object network 192.168.152.1
host 192.168.152.1
object network 172.18.196.100
host 172.18.196.100
object network 91.212.63.183
host 91.212.63.183
object network 212.98.183.211
host 212.98.183.211
object network 193.176.181.151
host 193.176.181.151
object network trsbk-ipsec-host
host 212.98.162.139
object network 192.168.21.100
host 192.168.21.100
object network parkomats-vpn-pool
subnet 192.168.203.0 255.255.255.192
object network 192.168.22.1
host 192.168.22.1
object network 192.168.20.100
host 192.168.20.100
object network bft-network
subnet 10.0.0.0 255.0.0.0
object network stylesoftvpnpool
subnet 172.17.176.0 255.255.255.0
object network 192.168.111.115
host 192.168.111.115
object service tcp6001
service tcp source eq 6001
object network 192.168.111.26
host 192.168.111.26
object service tcp45401
service tcp source eq 45401
object service tcp1521
service tcp source eq sqlnet
object service tcp45402
service tcp source eq 45402
object service tcp1158
service tcp source eq 1158
object service tcp45403
service tcp source eq 45403
object network 192.168.111.27
host 192.168.111.27
object service tcp45411
service tcp source eq 45411
object service tcp7001
service tcp source eq 7001
object service tcp45412
service tcp source eq 45412
object service tcp9704
service tcp source eq 9704
object service tcp45413
service tcp source eq 45413
object service tcp9703
service tcp source eq 9703
object service tcp45414
service tcp source eq 45414
object network 192.168.111.23
host 192.168.111.23
object service tcp1522
service tcp source eq 1522
object service tcp45421
service tcp source eq 45421
object network 192.168.111.43
host 192.168.111.43
object service tcp55443
service tcp source eq 55443
object network 192.168.111.102
host 192.168.111.102
object service tcp7779
service tcp source eq 7779
object service tcp45423
service tcp source eq 45423
object service tcp7777
service tcp source eq 7777
object service tcp45422
service tcp source eq 45422
object service tcp45025
service tcp source eq 45025
object service tcp45110
service tcp source eq 45110
object service tcp9080
service tcp source eq 9080
object service tcp45580
service tcp source eq 45580
object network 192.168.111.24
host 192.168.111.24
object service tcp8077
service tcp source eq 8077
object network 192.168.111.42
host 192.168.111.42
object service tcp46599
service tcp source eq 46599
object network 192.168.111.16
host 192.168.111.16
object service tcp4102
service tcp source eq 4102
object network 172.22.147.51
host 172.22.147.51
object network 192.168.111.38
host 192.168.111.38
object service tcp80
service tcp source eq www
object service tcp38080
service tcp source eq 38080
object service tcp38022
service tcp source eq 38022
object service tcp4443
service tcp source eq 4443
object service tcp8097
service tcp source eq 8097
object service tcp443
service tcp source eq https
object network 192.168.111.74
host 192.168.111.74
object service tcp9443
service tcp source eq 9443
object service tcp8098
service tcp source eq 8098
object service tcp9777
service tcp source eq 9777
object network 192.168.111.15
host 192.168.111.15
object service tcp4070
service tcp source eq 4070
object network 10.52.31.190
host 10.52.31.190
object network 192.168.111.234
host 192.168.111.234
object network 82.209.YY.XX
host 82.209.YY.XX
object service tcp8008
service tcp source eq 8008
object network 172.16.128.119
host 172.16.128.119
object network 172.16.128.68
host 172.16.128.68
object service tcp25010
service tcp source eq 25010
object service tcp45599
service tcp source eq 45599
object service tcp50013
service tcp source eq 50013
object service tcp50012
service tcp source eq 50012
object network 172.16.177.7
host 172.16.177.7
object service tcp64443
service tcp source eq 64443
object network 192.168.111.100
host 192.168.111.100
object service tcp1194
service tcp source eq 1194
object service tcp27512
service tcp source eq 27512
object service tcp27256
service tcp source eq 27256
object network 172.16.177.220
host 172.16.177.220
object service tcp8080
service tcp source eq 8080
object service tcp9988
service tcp source eq 9988
object service tcp44251
service tcp source eq 44251
object network 192.168.111.73
host 192.168.111.73
object service tcp7999
service tcp source eq 7999
object service tcp6443
service tcp source eq 6443
object service tcp7990
service tcp source eq 7990
object service tcp7443
service tcp source eq 7443
object network 192.168.111.250
host 192.168.111.250
object network 178.124.YY.XX
host 178.124.163.162
object network 212.98.YY.XX
subnet 212.98.163.80 255.255.255.240
object service tcp3389
service tcp source eq 3389
object service tcp65123
service tcp source eq 65123
object network 192.168.111.44
host 192.168.111.44
object service tcp27128
service tcp source eq 27128
object network 172.16.177.221
host 172.16.177.221
object network 82.209.233.254
host 82.209.233.254
object network 172.16.177.223
host 172.16.177.223
object service tcp8081
service tcp source eq 8081
object network 192.168.111.224
host 192.168.111.224
object service tcp42000
service tcp source eq 42000
object service tcp42001
service tcp source eq 42001
object network 192.168.181.22
host 192.168.181.22
object network 172.17.125.100
host 172.17.125.100
object network vtbk-stand65
host 10.7.7.65
object network vtbk-stand66
host 10.7.7.66
object network 192.168.129.100
host 192.168.129.100
object network 172.27.143.33
host 172.27.143.33
object network 192.168.142.1
host 192.168.142.1
object network 192.168.133.1
host 192.168.133.1
object network 192.168.111.1
host 192.168.111.1
object network 192.168.222.2
host 192.168.222.2
object network 192.168.223.3
host 192.168.223.3
object network 192.168.223.4
host 192.168.223.4
object network bs-wifi-guest-network
subnet 172.16.189.0 255.255.255.0
object network bs-interlink
subnet 172.16.192.0 255.255.255.0
object network 192.168.18.254
host 192.168.18.254
object network 192.168.18.107
host 192.168.18.107
object network 192.168.130.100
host 192.168.130.100
object network 192.168.142.0
subnet 192.168.142.0 255.255.255.0
object network 172.17.221.0
subnet 172.17.221.0 255.255.255.0
object network 172.27.143.32
subnet 172.27.143.32 255.255.255.240
object network 192.168.22.0
subnet 192.168.22.0 255.255.255.248
object network 192.168.133.0
subnet 192.168.133.0 255.255.255.0
object service tcp22
service tcp source eq ssh
object service tcp65123d
service tcp destination eq 65123
object service tcp3389d
service tcp destination eq 3389
object service tcp8443d
service tcp destination eq 8443
object service tcp4102d
service tcp destination eq 4102
object service tcp7777d
service tcp destination eq 7777
object service tcp80d
service tcp destination eq www
object service tcp4070d
service tcp destination eq 4070
object service tcp8008d
service tcp destination eq 8008
object service tcp22d
service tcp destination eq ssh
object service tcp2222
service tcp source eq 2222
object network 82.209.233.251
host 82.209.YY.XX
object service tcp443d
service tcp destination eq https
object service tcp22223d
service tcp destination eq 22223
object service tcp22223
service tcp source eq 22223
object network belpak-range
range 82.209.YY.XX 82.209.233.254
object service tcp45421d
service tcp destination eq 45421
object network 172.16.192.0
subnet 172.16.192.0 255.255.255.0
object network inside-net
subnet 172.16.192.0 255.255.255.0
description link to mikrotik
object network obj_82.209.233.251
host 82.209.YY.XX
object network obj_82.209.XXX.XXX
host 82.209.XXX.XXX
object service tcp8090d
service tcp destination eq 8090
object service tcp6001d
service tcp destination eq 6001
object service tcp45401d
service tcp destination eq 45401
object service tcp45402d
service tcp destination eq 45402
object service tcp45403d
service tcp destination eq 45403
object service tcp45411d
service tcp destination eq 45411
object service tcp45412d
service tcp destination eq 45412
object service tcp45413d
service tcp destination eq 45413
object service tcp45414d
service tcp destination eq 45414
object service tcp55443d
service tcp destination eq 55443
object service tcp1521d
service tcp destination eq sqlnet
object service tcp1158d
service tcp destination eq 1158
object service tcp7001d
service tcp destination eq 7001
object service tcp9704d
service tcp destination eq 9704
object service tcp9703d
service tcp destination eq 9703
object service tcp1522d
service tcp destination eq 1522
object service tcp7779d
service tcp destination eq 7779
object service tcp45025d
service tcp destination eq 45025
object service tcp9080d
service tcp destination eq 9080
object service tcp4443d
service tcp destination eq 4443
object service tcp9443d
service tcp destination eq 9443
object service tcp25010d
service tcp destination eq 25010
object service tcp50013d
service tcp destination eq 50013
object service tcp1194d
service tcp destination eq 1194
object service tcp8080d
service tcp destination eq 8080
object service tcp7999d
service tcp destination eq 7999
object service tcp6443d
service tcp destination eq 6443
object service tcp7990d
service tcp destination eq 7990
object service tcp7443d
service tcp destination eq 7443
object service tcp8081d
service tcp destination eq 8081
object service tcp42000d
service tcp destination eq 42000
object service tcp42001d
service tcp destination eq 42001
object network 10.1.36.0
subnet 10.1.36.0 255.255.255.0
object network 192.168.111.205
host 192.168.111.205
object service tcp17777d
service tcp destination eq 17777
object service tcp17777
service tcp source eq 17777
object network 192.168.111.206
host 192.168.111.206
object network 172.16.177.50
host 172.16.177.50
object service tcp27777
service tcp source eq 27777
object service tcp37777
service tcp source eq 37777
object service tcp27777d
service tcp destination eq 27777
object service tcp37777d
service tcp destination eq 37777
object network 192.168.23.100
host 192.168.23.100
object network 192.168.24.100
host 192.168.24.100
object network 10.1.11.29
host 10.1.11.29
object-group network bs-nets-inside
description Inside Bsmr networks
network-object object vpn-client-net
network-object object ipy-net
network-object object mgmt-net
network-object object servers-net
network-object object users-net
network-object object 172.16.192.0
object-group network cod-nets
description Datacenter nets
network-object object datacenter-ipsec-net
network-object object datacenter-dmz-ipsec-net
network-object datacenter-ipsec-net 255.255.255.0
network-object datacenter-dmz-ipsec-network 255.255.255.0
object-group network belapb-ipsec-hosts
network-object host 172.16.128.117
network-object host 172.16.128.119
network-object host 172.16.128.68
network-object host 172.16.62.20
object-group network bgpb-ipsec-hosts
network-object host 172.22.147.10
network-object host 172.22.147.50
network-object host 172.22.147.51
network-object host 172.22.147.5
network-object bgpb-ipsec-net 255.255.255.0
network-object host 172.22.147.38
network-object host 172.22.147.2
network-object host 172.22.147.45
network-object host 172.22.133.15
network-object host 192.168.77.15
object-group network DM_INLINE_NETWORK_1
network-object object datacenter-ipsec-net
network-object object datacenter-vpn-ipsec-net
object-group network DM_INLINE_NETWORK_2
network-object object datacenter-dmz-ipsec-net
network-object object datacenter-ipsec-net
network-object object trsbk-ipsec-host
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service bs44660 tcp-udp
port-object eq 44660
object-group service bs44668 tcp
port-object eq 44668
object-group service bsrdp tcp
port-object eq 45388
port-object eq 30389
object-group service nod32upd tcp
port-object eq 45391
object-group service vtb-to-asa tcp
port-object eq 45392
object-group service blil-rep-db tcp
port-object eq 45401
port-object eq 45402
port-object eq 45403
object-group service blil-rep-app tcp
description biee.blil.local
port-object eq 45411
port-object eq 45412
port-object eq 45413
port-object eq 45414
port-object eq 3389
object-group service bsmail tcp
port-object eq 45025
port-object eq 45110
object-group service blil-ws tcp
port-object eq 45580
object-group service sou-panda.ua tcp
port-object eq 45590
port-object eq 45591
port-object eq 45592
port-object eq 45593
object-group service sou tcp
port-object eq 45598
port-object eq 45599
object-group service iperf tcp-udp
port-object eq 5001
object-group service erip-offline tcp
port-object range 4070 4102
object-group service ticketpro-external tcp
port-object eq 8097
object-group service ticketpro-internal tcp
port-object eq 10003
object-group service x-ufk tcp
port-object range 6000 6063
object-group service 44421 tcp
port-object eq 44421
object-group service ftp44421 tcp
port-object eq 44421
object-group network to-belpak-nat
description Dynamic NAT to Belpak
network-object host 192.168.111.250
network-object host 192.168.111.252
object-group network to-bft-nat
description Dynamic NAT to BFT nework
network-object host 192.168.111.250
object-group network to-ghu-nat
description Dynamic NAT to GHU
network-object host 192.168.111.250
object-group network DM_INLINE_NETWORK_4
network-object host 10.1.100.115
network-object host 10.1.5.125
object-group service DM_INLINE_TCP_7 tcp
port-object eq www
port-object eq https
port-object eq 4443
object-group network bta-bank-hosts
network-object host 192.168.14.11
network-object host 192.168.14.4
network-object host 192.168.4.64
network-object host 192.168.5.224
object-group service ipy-allowed-services tcp
port-object eq domain
port-object eq ftp
port-object eq www
port-object eq https
port-object eq pop3
port-object eq smtp
port-object eq sqlnet
port-object eq 3389
port-object eq 465
port-object eq 995
port-object eq 2525
port-object eq imap4
port-object eq 9080
port-object eq pptp
object-group service ipy-allowed-udp udp
port-object eq 389
port-object eq bootpc
port-object eq bootps
port-object eq domain
port-object eq netbios-dgm
port-object eq netbios-ns
port-object eq ntp
port-object eq isakmp
object-group network ipy-to-bft-hosts
network-object host 172.16.61.102
network-object host 172.16.61.103
network-object host 172.16.61.104
network-object host 172.16.61.105
object-group service TicketproFTP tcp
port-object eq 10021
object-group network dkv-users
description Users allowed to DKV network
network-object host 192.168.111.102
network-object host 192.168.111.110
network-object host 192.168.111.16
network-object host 192.168.111.23
network-object host 192.168.111.240
network-object host 192.168.111.250
object-group network vpn-users-to-bft
description VPN users with BFT access
network-object host 172.17.19.109
object-group network blil-users
description Users with NAT to Beloil networks
network-object host George_Lan
network-object host 192.168.111.45
network-object host 192.168.111.50
network-object host 192.168.111.102
network-object host 192.168.111.90
network-object host 192.168.111.250
object-group service 1crdp tcp
port-object eq 65123
object-group network bps-hosts
network-object host 172.30.71.100
network-object host 172.30.71.60
network-object host 172.30.71.61
network-object host 172.30.71.18
object-group service ipsec-ports tcp-udp
port-object eq 10000
port-object eq 4500
port-object eq 500
port-object eq 10001
object-group network allow-to-internet
network-object host 172.16.177.220
network-object host 192.168.111.100
network-object host 192.168.111.102
network-object host 192.168.111.115
network-object host 192.168.111.16
network-object host 192.168.111.23
network-object host 192.168.111.244
network-object host 192.168.111.246
network-object host 192.168.111.247
network-object host 192.168.111.24
network-object host 192.168.111.250
network-object host 192.168.111.26
network-object host 192.168.111.27
network-object host 192.168.111.38
network-object host 192.168.111.42
network-object host 192.168.111.43
network-object host 192.168.111.72
network-object host 192.168.111.73
network-object host 192.168.111.80
object-group network a1-ipy-ipsec-nets
description a1 cloud ipy ipsec subnets
network-object a1-ipy-border 255.255.255.224
network-object a1-ipy-ipsec-dmz 255.255.255.224
object-group network allowed-to-a1
description allowed to a1 ipy and smartpay subnets
network-object host d.vyrvich
network-object host George_Wifi
network-object host 192.168.111.2
network-object host George_Lan
network-object host 192.168.111.50
network-object host 172.16.177.106
network-object host 192.168.111.90
network-object host 192.168.111.101
network-object host 192.168.111.102
network-object host 192.168.111.250
object-group network a1-smartpay
description a1 cloud smartpay ipsec subnets
network-object a1-smartpay-inside 255.255.255.224
network-object a1-smartpay-dmz 255.255.255.224
object-group network tpro-cloud-nets
network-object tpro-inside 255.255.255.224
object-group network allowed-to-tpro-cloud
description allowed to activecloud tpro subnets
network-object host George_Wifi
network-object host 192.168.111.250
network-object host 192.168.111.2
network-object host George_Lan
network-object host 192.168.111.50
network-object host 192.168.111.90
object-group network DM_INLINE_NETWORK_3
group-object bs-nets-inside
network-object object datacenter-dmz-ipsec-net
network-object object datacenter-ipsec-net
object-group network DM_INLINE_NETWORK_5
network-object object 172.16.128.119
network-object object 172.16.128.68
object-group network DM_INLINE_NETWORK_6
network-object object 172.16.128.119
network-object object 172.16.128.68
object-group network yura-networks
network-object object 178.124.YY.XX
network-object object 212.98.YY.XX
object-group network DM_INLINE_NETWORK_7
group-object bs-nets-inside
network-object object bs-wifi-guest-network
object-group network DM_INLINE_NETWORK_8
group-object bs-nets-inside
network-object object bs-wifi-guest-network
object-group service DM_INLINE_SERVICE_1
service-object tcp
service-object object tcp4102
service-object object tcp4102d
object-group network DM_INLINE_NETWORK_10
network-object object vtbk-stand64
network-object object vtbk-stand65
network-object object vtbk-stand66
object-group network DM_INLINE_NETWORK_11
network-object object 172.16.128.119
network-object object 172.16.128.68
object-group network DM_INLINE_NETWORK_12
network-object object 172.16.128.119
network-object object 172.16.128.68
object-group network ipy-datacenter-ipsec-nets
network-object object datacenter-dmz-ipsec-net
network-object object datacenter-ipsec-net
object-group network DM_INLINE_NETWORK_15
network-object object access.mnssis.blil.by
network-object object boil-stand
group-object bs-nets-inside
object-group network DM_INLINE_NETWORK_16
network-object object datacenter-vpn-ipsec-net
group-object ipy-datacenter-ipsec-nets
object-group service DM_INLINE_TCP_1 tcp
port-object eq ftp
port-object eq www
port-object eq https
port-object eq imap4
port-object eq pop3
port-object eq smtp
object-group network DM_INLINE_NETWORK_9
network-object object datacenter-dmz-ipsec-net
network-object object datacenter-ipsec-net
network-object object trsbk-ipsec-host
object-group network DM_INLINE_NETWORK_17
group-object bs-nets-inside
network-object object datacenter-dmz-ipsec-net
network-object object datacenter-ipsec-net
object-group network DM_INLINE_NETWORK_18
network-object object datacenter-ipsec-net
network-object object datacenter-vpn-ipsec-net
object-group network DM_INLINE_NETWORK_19
network-object object 172.16.177.50
network-object object 192.168.111.205
network-object object 192.168.111.206
object-group network DM_INLINE_NETWORK_63
network-object object servers-net
network-object object users-net
access-list ftp-pasv-list remark Serv-U passive FTP ports
access-list ftp-pasv-list extended permit tcp any any range 57020 57099 inactive
access-list ftp-pasv-list remark Serv-U passive FTP ports
access-list global_mpc remark Serv-U passive FTP ports
access-list global_mpc extended permit tcp any any range 57020 57099
access-list global_mpc remark Serv-U passive FTP ports
access-list bft_access_in extended permit icmp any any
access-list bft_access_in extended permit object-group DM_INLINE_SERVICE_1 object bft-network 10.0.0.0 255.255.255.252
access-list bft_access_in extended permit tcp any 10.0.0.0 255.255.255.252
access-list bft_access_in extended permit object tcp7777d object bft-network host 192.168.111.16
access-list bft_access_in extended permit object tcp7777d object-group bgpb-ipsec-hosts host 192.168.111.16
access-list bft_access_in extended permit ip any any
access-list bft_access_in extended deny ip any any inactive
access-list ghu_access_in extended permit icmp any any
access-list ghu_access_in extended permit tcp any object 192.168.111.2 eq ftp
access-list ghu_access_in extended permit tcp any object 192.168.111.2 eq ssh
access-list ghu_access_in extended permit object tcp1521d any object 192.168.111.23
access-list ghu_access_in remark 1C RDP for Yura
access-list ghu_access_in extended permit object tcp3389d object-group yura-networks object 192.168.111.250
access-list ghu_access_in extended permit ip any any
access-list ghu_access_in extended deny ip any any inactive
access-list ghu_access_in remark 1C RDP for Yura
access-list belpak_access_in extended permit icmp any any
access-list belpak_access_in remark 1C RDP for Yura
access-list belpak_access_in extended permit object tcp3389d object-group yura-networks object 192.168.111.250
access-list belpak_access_in extended permit object tcp80d object-group DM_INLINE_NETWORK_11 object 192.168.111.2
access-list belpak_access_in extended permit object tcp7777d object-group DM_INLINE_NETWORK_12 object 192.168.111.2
access-list belpak_access_in remark Bestcard.by
access-list belpak_access_in extended permit object tcp80d any object 192.168.111.234
access-list belpak_access_in remark Payterminal for Primaka
access-list belpak_access_in extended permit object tcp8008d any object 192.168.111.234
access-list belpak_access_in remark brsmsmart. BSNET-77
access-list belpak_access_in extended permit object tcp80 any object-group DM_INLINE_NETWORK_63
access-list belpak_access_in remark brsmsmart. BSNET-77
access-list belpak_access_in extended permit object tcp443d any object 172.16.177.221
access-list belpak_access_in extended permit object tcp22d any object 192.168.111.2
access-list belpak_access_in extended permit tcp any host 192.168.111.2 eq ftp
access-list belpak_access_in remark hsm1.boil. BPC Emulator
access-list belpak_access_in extended permit object tcp6001d any object 192.168.111.115 inactive
access-list belpak_access_in extended permit object tcp1521d any object 192.168.111.43
access-list belpak_access_in extended permit object tcp80d any object 192.168.111.43
access-list belpak_access_in extended permit object tcp443d any object 192.168.111.43
access-list belpak_access_in extended permit object tcp1194d any object 192.168.111.100
access-list belpak_access_in extended permit object tcp1194d any object 192.168.111.102
access-list belpak_access_in remark parking.bsmr.by
access-list belpak_access_in extended permit object tcp8080d any object 172.16.177.220
access-list belpak_access_in remark parking.bsmr.by
access-list belpak_access_in extended permit object tcp1521d any host 172.16.177.220
access-list belpak_access_in remark bitbucket.bsmr.by
access-list belpak_access_in extended permit object tcp7999d any object 192.168.111.73
access-list belpak_access_in remark BSNET-76
access-list belpak_access_in extended permit object tcp1194d any object 192.168.111.44
access-list belpak_access_in remark brsmsmart. BSNET-77
access-list belpak_access_in extended permit object tcp80d any object 172.16.177.221
access-list belpak_access_in remark BSNET-103
access-list belpak_access_in extended permit object tcp8081d any object 172.16.177.223
access-list belpak_access_in remark BSNET-82
access-list belpak_access_in extended permit object tcp42000d any object 192.168.111.224
access-list belpak_access_in remark BSNET-82
access-list belpak_access_in extended permit object tcp42001d any object 192.168.111.224
access-list belpak_access_in remark BSNET-107 for boil
access-list belpak_access_in extended permit object tcp7777d any object-group DM_INLINE_NETWORK_19
access-list belpak_access_in extended permit ip any any
access-list belpak_access_in extended deny ip any any log debugging inactive
access-list belpak_access_in remark 1C RDP for Yura
access-list inside_access_in extended permit icmp any any
access-list inside_access_in remark allow outgoing tcp any
access-list inside_access_in extended permit tcp any any
access-list inside_access_in extended permit udp object-group bs-nets-inside any eq ntp
access-list inside_access_in extended permit udp object-group bs-nets-inside any eq snmp
access-list inside_access_in extended permit object-group TCPUDP object-group bs-nets-inside any eq domain
access-list inside_access_in extended deny udp any object bft-network inactive
access-list inside_access_in extended permit ip object-group bs-nets-inside object-group ipy-datacenter-ipsec-nets
access-list inside_access_in extended permit ip object-group bs-nets-inside object-group a1-ipy-ipsec-nets
access-list inside_access_in extended permit ip object-group bs-nets-inside object-group a1-smartpay
access-list inside_access_in extended permit ip object-group bs-nets-inside object-group tpro-cloud-nets
access-list inside_access_in extended permit ip any any
access-list inside_access_in extended deny ip any any inactive
access-list inside_access_in remark allow outgoing tcp any
access-list bft_cryptomap_5 extended permit ip object 192.168.23.100 object 192.168.24.100
access-list bft_cryptomap_1 extended permit ip object 192.168.21.100 object trsbk-ipsec-host
access-list bft_cryptomap_2 extended permit ip object 192.168.20.100 object-group bgpb-ipsec-hosts
access-list bft_cryptomap_3 extended permit ip object 192.168.130.100 object life-smsc
access-list bft_cryptomap_4 extended permit ip object 192.168.142.0 object-group bta-bank-hosts
access-list belpak_cryptomap extended permit ip object 172.17.221.0 object parking-mogilev7601
access-list belpak_cryptomap_1 extended permit ip object 172.17.125.100 object partner1-ipsec-host
access-list ghu_cryptomap extended permit ip object 192.168.222.2 object-group a1-ipy-ipsec-nets
access-list ghu_cryptomap_5 extended permit ip object 192.168.223.3 object-group a1-smartpay
access-list ghu_cryptomap_2 extended permit ip object 192.168.223.4 object-group tpro-cloud-nets
access-list belpak_cryptomap_2 extended permit ip object 192.168.21.100 object trsbk-ipsec-host
access-list belpak_cryptomap_3 extended permit ip object 172.27.143.32 object multicarta-ipsec-net
access-list belpak_cryptomap_4 extended permit ip object 192.168.129.100 object vtbk-stand64
access-list belpak_cryptomap_5 extended permit ip object 192.168.152.1 object parking-grodno401
access-list ghu_cryptomap_3 extended permit ip object-group DM_INLINE_NETWORK_15 object-group DM_INLINE_NETWORK_16
access-list belpak_cryptomap_6 extended permit ip object 192.168.182.1 object-group belapb-ipsec-hosts
access-list belpak_cryptomap_7 extended permit ip object 192.168.22.0 object bps-ipsec-net
access-list belpak_cryptomap_8 extended permit ip object 192.168.133.0 object dkv-network
access-list belpak_cryptomap_9 extended permit ip object 192.168.181.0 object blil-stand
access-list PBR-to-ghu extended permit object-group TCPUDP object-group bs-nets-inside any inactive
access-list PBR-to-ghu remark send outgoing web,ftp, mail and icmp to ghu
access-list PBR-to-ghu extended permit tcp object-group bs-nets-inside any object-group DM_INLINE_TCP_1
access-list bs-office-vpn-split standard permit 192.168.111.0 255.255.255.0
access-list bs-office-vpn-split standard permit 172.16.177.0 255.255.255.0
access-list bs-office-vpn-split standard permit 172.16.154.0 255.255.255.0
access-list bs-office-vpn-split standard permit 172.16.61.0 255.255.255.0
access-list bs-office-vpn-split standard permit 192.168.3.0 255.255.255.0
access-list bs-office-vpn-split standard permit 192.168.4.0 255.255.255.0
access-list bs-office-vpn-split standard permit host 10.93.1.24
access-list bs-office-vpn-split standard permit 10.0.0.0 255.0.0.0
access-list bs-office-vpn-split standard permit host 212.98.162.139
access-list bs-office-vpn-split standard permit 192.168.200.0 255.255.255.0
access-list bs-office-vpn-split standard permit 172.16.128.0 255.255.255.0
access-list bs-office-vpn-split standard permit host 172.16.62.20
access-list bs-office-vpn-split standard permit 172.22.147.0 255.255.255.0
access-list bs-office-vpn-split standard permit 172.18.152.0 255.255.255.240
access-list bs-office-vpn-split standard permit 172.30.71.0 255.255.255.0
access-list bs-office-vpn-split standard permit host 91.212.63.183
access-list bs-office-vpn-split standard permit host 212.98.183.211
access-list bs-office-vpn-split standard permit host 192.168.77.15
access-list bs-office-vpn-split standard permit host 193.176.181.151
access-list bs-office-vpn-split standard permit host 93.85.YY.XX
access-list bs-office-vpn-split standard permit 192.168.191.0 255.255.255.0
access-list bs-office-vpn-split standard permit 192.168.192.0 255.255.255.224
access-list bs-office-vpn-split standard permit 172.17.18.32 255.255.255.224
access-list bs-office-vpn-split standard permit 172.17.18.64 255.255.255.224
access-list ghu_cryptomap_10 extended permit ip object 192.168.181.0 object blil-stand
access-list global_access extended permit ip any any
access-list ghu_cryptomap_4 extended permit ip object 192.168.222.2 object-group a1-ipy-ipsec-nets
pager lines 24
logging enable
logging monitor warnings
logging buffered warnings
logging trap warnings
logging asdm debugging
logging queue 1024
logging host inside 192.168.111.50
logging host inside 192.168.111.244
logging message 113015 level warnings
logging message 605005 level warnings
logging message 605004 level warnings
logging message 111008 level warnings
mtu belpak 1500
mtu ghu 1500
mtu bft 1500
mtu inside 1500
mtu mgmt 1500
no failover
no monitor-interface inside
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
icmp permit any belpak
icmp permit any ghu
icmp permit any bft
icmp permit any inside
icmp permit any mgmt
asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (inside,belpak) source static bs-nets-inside bs-nets-inside destination static DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 no-proxy-arp route-lookup description Exampt to COD
nat (inside,ghu) source static bs-nets-inside bs-nets-inside destination static DM_INLINE_NETWORK_18 DM_INLINE_NETWORK_18 no-proxy-arp route-lookup description Exampt to COD
nat (inside,belpak) source static DM_INLINE_NETWORK_3 DM_INLINE_NETWORK_3 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
nat (inside,ghu) source static DM_INLINE_NETWORK_17 DM_INLINE_NETWORK_17 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
nat (inside,ghu) source static bs-nets-inside bs-nets-inside destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
nat (bft,belpak) source static DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
nat (bft,ghu) source static DM_INLINE_NETWORK_9 DM_INLINE_NETWORK_9 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
nat (belpak,bft) source static stylesoftvpnpool stylesoftvpnpool destination static paritet-host paritet-host no-proxy-arp route-lookup description Exampt to paritet for stylesoft vpn
nat (belpak,ghu) source static vpn-client-net 192.168.181.0 destination static boil-stand boil-stand description vpn client to boil stand
nat (belpak,belpak) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
nat (belpak,ghu) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
nat (belpak,belpak) source dynamic vpn-client-net 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
nat (belpak,belpak) source dynamic vpn-client-net 192.168.152.1 destination static parking-grodno401 parking-grodno401
nat (belpak,belpak) source dynamic vpn-client-net 172.18.196.100 destination static bps-hosts bps-hosts
nat (belpak,belpak) source dynamic vpn-client-net interface destination static 91.212.63.183 91.212.63.183 description NAT to RIB Staging for access from VPN i.karpov
nat (belpak,ghu) source dynamic vpn-client-net interface destination static 91.212.63.183 91.212.63.183 description NAT to RIB Staging for access from VPN i.karpov
nat (belpak,belpak) source dynamic vpn-client-net interface destination static 212.98.183.211 212.98.183.211
nat (belpak,ghu) source dynamic vpn-client-net interface destination static 212.98.183.211 212.98.183.211
nat (belpak,belpak) source dynamic vpn-client-net interface destination static 193.176.181.151 193.176.181.151 description ticketpro hosting
nat (belpak,ghu) source dynamic vpn-client-net interface destination static 193.176.181.151 193.176.181.151 description ticketpro hosting
nat (belpak,belpak) source dynamic vpn-client-net 192.168.21.100 destination static trsbk-ipsec-host trsbk-ipsec-host
nat (belpak,belpak) source static parkomats-vpn-pool 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net description Parkomats to BPS authontication servers
nat (belpak,bft) source dynamic vpn-client-net 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
nat (belpak,bft) source dynamic vpn-client-net 192.168.21.100 destination static trsbk-ipsec-host trsbk-ipsec-host
nat (belpak,bft) source dynamic vpn-client-net interface destination static bft-network bft-network
nat (belpak,bft) source dynamic stylesoftvpnpool interface destination static paritet-host paritet-host description Stylesoft to Paritet NAT
nat (ghu,ghu) source static datacenter-ipsec-net 192.168.181.0 destination static boil-stand boil-stand
nat (ghu,belpak) source static datacenter-ipsec-net 192.168.181.0 destination static boil-stand boil-stand
nat (ghu,belpak) source dynamic vpn-client-net 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
nat (ghu,ghu) source dynamic vpn-client-net 192.168.152.1 destination static parking-grodno401 parking-grodno401
nat (ghu,belpak) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
nat (ghu,ghu) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
nat (ghu,belpak) source dynamic parkomats-vpn-pool 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net
nat (ghu,belpak) source dynamic datacenter-vpn-ipsec-net interface destination static access.mnssis.blil.by access.mnssis.blil.by
nat (ghu,ghu) source dynamic datacenter-vpn-ipsec-net interface destination static access.mnssis.blil.by access.mnssis.blil.by
nat (ghu,bft) source dynamic vpn-client-net 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
nat (ghu,bft) source dynamic vpn-client-net 192.168.21.100 destination static trsbk-ipsec-host trsbk-ipsec-host
nat (ghu,bft) source dynamic vpn-client-net interface destination static bft-network bft-network
nat (belpak,ghu) source dynamic vpn-client-net 192.168.222.2 destination static a1-ipy-ipsec-nets a1-ipy-ipsec-nets
nat (belpak,ghu) source dynamic vpn-client-net 192.168.223.3 destination static a1-smartpay a1-smartpay
nat (belpak,ghu) source dynamic vpn-client-net 192.168.223.4 destination static tpro-cloud-nets tpro-cloud-nets
nat (ghu,bft) source dynamic stylesoftvpnpool interface destination static paritet-host paritet-host
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
nat (inside,bft) source static 192.168.111.16 192.168.20.100 destination static 172.22.147.51 172.22.147.51 service tcp7777 tcp4102 no-proxy-arp
nat (inside,bft) source static 192.168.111.2 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts service ftp21 ftp21 no-proxy-arp
nat (inside,bft) source static 192.168.111.250 192.168.23.100 destination static 192.168.24.100 192.168.24.100 service tcp3389 tcp65123 no-proxy-arp
nat (inside,belpak) source static 192.168.111.2 192.168.182.1 destination static DM_INLINE_NETWORK_5 DM_INLINE_NETWORK_5 service tcp80 tcp8097 no-proxy-arp
nat (inside,belpak) source static 192.168.111.2 192.168.182.1 destination static DM_INLINE_NETWORK_6 DM_INLINE_NETWORK_6 service tcp7777 tcp9777 no-proxy-arp
nat (inside,belpak) source static 192.168.111.234 82.209.233.253 service tcp80 tcp80
nat (inside,belpak) source static 192.168.111.234 82.209.233.253 service tcp8008 tcp8008
nat (inside,ghu) source static 192.168.111.250 interface service tcp3389 tcp65123 no-proxy-arp
nat (inside,belpak) source static 192.168.111.250 interface service tcp3389 tcp65123
nat (inside,belpak) source static 192.168.111.2 belpack.work.bs service ftp21 ftp21
nat (inside,belpak) source static 192.168.111.2 belpack.work.bs service ssh22 ssh22
nat (inside,belpak) source static 192.168.111.115 belpack.stand.bs service tcp6001 tcp6001 inactive description hsm1.boil
nat (inside,belpak) source static 192.168.111.43 belpack.work.bs service tcp1521 tcp55443 description ticketpro for test module
nat (inside,belpak) source static 192.168.111.43 belpack.work.bs service tcp80 tcp80
nat (inside,belpak) source static 192.168.111.43 belpack.work.bs service tcp443 tcp443
nat (inside,ghu) source static 192.168.111.2 interface service ftp21 ftp21 no-proxy-arp
nat (inside,ghu) source static 192.168.111.23 interface service tcp1521 tcp45421 no-proxy-arp
nat (inside,belpak) source static 192.168.111.100 belpack.stand.bs service tcp1194 tcp27512
nat (inside,belpak) source static 192.168.111.102 belpack.stand.bs service tcp1194 tcp27256
nat (inside,belpak) source static 172.16.177.220 belpack.work.bs service tcp8080 tcp9988 description parking ords
nat (inside,belpak) source static 172.16.177.220 belpack.work.bs service tcp1521 tcp44251 description parking sqlnet
nat (inside,belpak) source static 192.168.111.73 belpack.work.bs service tcp7999 tcp7999
nat (inside,belpak) source static 192.168.111.73 belpack.work.bs service tcp7990 tcp7990
nat (inside,belpak) source static 192.168.111.44 belpack.stand.bs service tcp1194 tcp27128 description ahramovich
nat (inside,belpak) source static 172.16.177.221 82.209.233.254 service tcp80 tcp80
nat (inside,belpak) source static 172.16.177.221 82.209.233.254 service tcp443 tcp443
nat (inside,belpak) source static 172.16.177.223 belpack.work.bs service tcp8081 tcp8081
nat (inside,belpak) source static 192.168.111.224 belpack.stand.bs service tcp42000 tcp42000
nat (inside,belpak) source static 192.168.111.224 belpack.stand.bs service tcp42001 tcp42001
nat (inside,belpak) source static 192.168.111.205 belpack.stand.bs service tcp7777 tcp17777 description BSNET-107 for boil
nat (inside,belpak) source static 192.168.111.206 belpack.stand.bs service tcp7777 tcp27777 description BSNET-107 for boil
nat (inside,belpak) source static 172.16.177.50 belpack.stand.bs service tcp7777 tcp37777 description BSNET-107 for boil
nat (inside,ghu) source dynamic bs-nets-inside 192.168.181.22 destination static boil-stand boil-stand
nat (inside,belpak) source dynamic bs-nets-inside 192.168.181.22 destination static boil-stand boil-stand
nat (inside,belpak) source dynamic bs-nets-inside 172.17.125.100 destination static partner1-ipsec-host partner1-ipsec-host
nat (inside,belpak) source dynamic bs-nets-inside 192.168.21.100 destination static trsbk-ipsec-host trsbk-ipsec-host
nat (inside,bft) source dynamic bs-nets-inside 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
nat (inside,bft) source dynamic bs-nets-inside 192.168.21.100 destination static trsbk-ipsec-host trsbk-ipsec-host
nat (inside,belpak) source dynamic bs-nets-inside 192.168.129.100 destination static DM_INLINE_NETWORK_10 DM_INLINE_NETWORK_10
nat (inside,belpak) source dynamic bs-nets-inside 172.27.143.33 destination static multicarta-ipsec-net multicarta-ipsec-net
nat (inside,bft) source dynamic bs-nets-inside 192.168.142.1 destination static bta-bank-hosts bta-bank-hosts
nat (inside,belpak) source dynamic dkv-users 192.168.133.1 destination static dkv-network dkv-network
nat (inside,bft) source dynamic bs-nets-inside 192.168.130.100 destination static life-smsc life-smsc
nat (inside,bft) source dynamic bs-nets-inside interface destination static bft-network bft-network
nat (inside,ghu) source dynamic bs-nets-inside 192.168.111.1 destination static datacenter-dmz-ipsec-net datacenter-dmz-ipsec-net
nat (inside,belpak) source dynamic bs-nets-inside 192.168.152.1 destination static parking-grodno401 parking-grodno401
nat (inside,belpak) source dynamic bs-nets-inside 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
nat (inside,belpak) source dynamic bs-nets-inside 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
nat (inside,belpak) source dynamic bs-nets-inside 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net
nat (inside,ghu) source dynamic bs-nets-inside 192.168.222.2 destination static a1-ipy-ipsec-nets a1-ipy-ipsec-nets
nat (inside,ghu) source dynamic allowed-to-a1 192.168.223.3 destination static a1-smartpay a1-smartpay
nat (inside,ghu) source dynamic allowed-to-tpro-cloud 192.168.223.4 destination static tpro-cloud-nets tpro-cloud-nets
nat (inside,belpak) source dynamic DM_INLINE_NETWORK_7 interface description Dynamic outgoing NAT
nat (inside,ghu) source dynamic DM_INLINE_NETWORK_8 interface description Dynamic outgoing NAT
access-group belpak_access_in in interface belpak
access-group ghu_access_in in interface ghu
access-group bft_access_in in interface bft
access-group inside_access_in in interface inside
access-group global_access global
!
route-map pbr1 permit 10
match ip address PBR-to-ghu
set ip next-hop verify-availability 93.125.XXX.YYY 1 track 129
set ip next-hop 93.125.XXX.YYY
!
route belpak trsbk-ipsec-host 255.255.255.255 82.209.233.249 1 track 14
route ghu datacenter-dmz-ipsec-network 255.255.255.0 93.125.111.129 30 track 101
route ghu datacenter-ipsec-net 255.255.255.0 93.125.111.129 10 track 102
route ghu 0.0.0.0 0.0.0.0 93.125.111.129 10 track 129
route belpak 0.0.0.0 0.0.0.0 82.209.233.249 5 track 249
route bft bft-network 255.0.0.0 10.1.11.29 1
route belpak vtbk-stand 255.255.255.255 82.209.233.249 1
route belpak 10.7.7.65 255.255.255.255 82.209.233.249 1
route belpak 10.7.7.66 255.255.255.255 82.209.233.249 1
route bft life-ussd-host 255.255.255.255 10.1.11.29 1
route ghu blil-stand 255.255.255.255 93.125.111.129 100
route belpak blil-stand 255.255.255.255 82.209.233.249 111
route inside uis-network 255.255.255.0 172.16.192.1 1
route belpak 74.125.136.108 255.255.255.254 82.209.233.249 1
route belpak 79.98.55.50 255.255.255.255 82.209.233.249 1
route bft life-smsc 255.255.255.255 10.1.11.29 1
route belpak 82.196.67.178 255.255.255.255 82.209.233.249 1
route belpak 82.209.214.25 255.255.255.255 82.209.233.249 10
route ghu 82.209.214.25 255.255.255.255 93.125.111.129 11
route belpak 86.57.147.21 255.255.255.255 82.209.233.249 1
route belpak 86.57.159.167 255.255.255.255 82.209.233.249 1
route belpak 86.57.167.46 255.255.255.255 82.209.233.249 1
route ghu 86.57.253.144 255.255.255.240 93.125.111.129 10
route belpak 86.57.253.144 255.255.255.240 82.209.233.249 120
route belpak 86.57.255.167 255.255.255.255 82.209.233.249 1
route belpak 87.252.232.9 255.255.255.255 82.209.233.249 1
route belpak 89.106.184.89 255.255.255.255 82.209.233.249 1
route ghu 91.90.223.252 255.255.255.255 93.125.111.129 100
route belpak 91.90.223.252 255.255.255.255 82.209.233.249 110
route belpak access.mnssis.blil.by 255.255.255.255 82.209.233.249 1
route belpak 93.125.122.55 255.255.255.255 82.209.233.249 1
route inside 172.16.0.0 255.255.255.252 172.16.192.1 1
route inside autopark-network 255.255.255.0 172.16.192.1 1
route inside ipy-network 255.255.255.0 172.16.192.1 1
route belpak 172.16.62.20 255.255.255.255 82.209.233.249 1
route belpak 172.16.128.0 255.255.255.0 82.209.233.249 1
route inside 172.16.154.0 255.255.255.0 172.16.192.1 1
route inside bs-users-network 255.255.255.0 172.16.192.1 1
route inside 172.16.189.0 255.255.255.0 172.16.192.1 1
route ghu a1-ipy-ipsec-inside 255.255.255.0 93.125.111.129 1
route ghu tpro-inside 255.255.255.224 93.125.111.129 1
route belpak parking-grodno401 255.255.255.240 82.209.233.249 1
route belpak ticketpro-dmz 255.255.255.0 82.209.233.249 1
route belpak multicarta-ipsec-net 255.255.255.0 82.209.233.249 1
route bft 172.22.133.15 255.255.255.255 10.1.11.29 1
route bft 172.22.147.0 255.255.255.0 10.1.11.29 1
route belpak bps-ipsec-net 255.255.255.0 82.209.233.249 1
route belpak partner1-ipsec-host 255.255.255.255 82.209.233.249 1
route belpak 178.62.1.203 255.255.255.255 82.209.233.249 1
route belpak 178.124.182.101 255.255.255.255 82.209.233.249 1
route ghu 185.183.120.59 255.255.255.255 93.125.111.129 1
route ghu 185.183.120.62 255.255.255.255 93.125.111.129 1
route belpak datacenter-ipsec-net 255.255.255.0 82.209.233.249 20
route bft datacenter-ipsec-net 255.255.255.0 10.1.11.29 30
route belpak datacenter-dmz-ipsec-network 255.255.255.0 82.209.233.249 50
route bft datacenter-dmz-ipsec-network 255.255.255.0 10.1.11.29 80
route bft 192.168.4.64 255.255.255.255 10.1.11.29 1
route bft 192.168.5.224 255.255.255.255 10.1.11.29 1
route bft 192.168.14.4 255.255.255.255 10.1.11.29 1
route bft 192.168.14.11 255.255.255.255 10.1.11.29 1
route bft 192.168.24.100 255.255.255.255 10.1.11.29 1
route bft 192.168.77.15 255.255.255.255 10.1.11.29 1
route inside inside-network 255.255.255.0 172.16.192.1 1
route bft bgpb-ipsec-net 255.255.255.0 10.1.11.29 1
route ghu a1-ipy-ipsec-dmz 255.255.255.0 93.125.111.129 1
route ghu a1-ipy-border 255.255.255.224 93.125.111.129 1
route belpak parking-mogilev7601 255.255.255.0 82.209.233.249 1
route belpak dkv-network 255.255.255.224 82.209.233.249 1
route ghu 193.176.180.10 255.255.255.255 93.125.111.129 1
route ghu 193.176.181.151 255.255.255.255 93.125.111.129 1
route belpak 195.222.75.24 255.255.255.255 82.209.233.249 1
route bft trsbk-ipsec-host 255.255.255.255 10.1.11.29 10
route ghu 212.98.163.80 255.255.255.240 93.125.111.129 1
route belpak 212.98.165.14 255.255.255.255 82.209.233.249 1
route belpak 212.98.165.29 255.255.255.255 82.209.233.249 1
route belpak 212.98.173.36 255.255.255.255 82.209.233.249 1
route belpak 212.98.189.97 255.255.255.255 82.209.233.249 1
route belpak 217.23.123.194 255.255.255.255 82.209.233.249 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
aaa-server BS-LDAP protocol radius
aaa-server BS-LDAP (inside) host 192.168.111.246
key *****
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
aaa authentication http console LOCAL
aaa authorization command LOCAL
aaa authentication login-history duration 40
http server enable 8443
http 0.0.0.0 0.0.0.0 mgmt
http 178.124.163.162 255.255.255.255 belpak
http 86.57.253.144 255.255.255.240 belpak
http 212.98.163.80 255.255.255.240 belpak
http 86.57.253.144 255.255.255.240 ghu
http 212.98.163.80 255.255.255.240 ghu
http 0.0.0.0 0.0.0.0 inside
http 178.124.163.162 255.255.255.255 ghu
http 10.1.36.126 255.255.255.255 bft
snmp-server host bft 10.1.36.126 poll community snmp*** version 2c
snmp-server host inside 192.168.111.41 poll community snmp***
snmp-server host inside 192.168.111.50 poll community snmp***
snmp-server host inside 192.168.3.90 poll community snmp*** version 2c
snmp-server host inside 192.168.3.99 poll community snmp*** version 2c
snmp-server host belpak 86.57.253.146 poll community snmp*** version 2c
no snmp-server location
no snmp-server contact
snmp-server community snmp***
sla monitor 14
type echo protocol ipIcmpEcho 212.98.173.36 interface belpak
num-packets 5
request-data-size 10
frequency 10
sla monitor schedule 14 life forever start-time now
sla monitor 101
type echo protocol ipIcmpEcho 86.57.253.146 interface ghu
num-packets 5
frequency 10
sla monitor schedule 101 life forever start-time now
sla monitor 102
type echo protocol ipIcmpEcho 86.57.253.146 interface ghu
num-packets 5
frequency 10
sla monitor schedule 102 life forever start-time now
sla monitor 121
type echo protocol ipIcmpEcho 86.57.253.146 interface ghu
num-packets 5
request-data-size 18
frequency 10
sla monitor schedule 121 life forever start-time now
sla monitor 129
type echo protocol ipIcmpEcho 93.125.111.129 interface ghu
num-packets 5
timeout 7000
frequency 10
sla monitor schedule 129 life forever start-time now
sla monitor 141
type echo protocol ipIcmpEcho 86.57.253.146 interface ghu
num-packets 5
request-data-size 18
frequency 10
sla monitor schedule 141 life forever start-time now
sla monitor 146
type echo protocol ipIcmpEcho 86.57.253.146 interface ghu
num-packets 5
request-data-size 19
timeout 7000
threshold 7000
frequency 10
sla monitor schedule 146 life forever start-time now
sla monitor 249
type echo protocol ipIcmpEcho 82.209.233.249 interface belpak
num-packets 5
request-data-size 19
timeout 7000
threshold 7000
frequency 10
sla monitor schedule 249 life forever start-time now
service sw-reset-button
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec security-association pmtu-aging infinite
crypto ipsec df-bit clear-df belpak
crypto ipsec df-bit clear-df ghu
crypto ipsec df-bit clear-df bft
crypto ipsec df-bit clear-df inside
crypto ipsec df-bit clear-df mgmt
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES
crypto map bft_map 1 match address bft_cryptomap_5
crypto map bft_map 1 set pfs group5
crypto map bft_map 1 set peer 10.1.36.126
crypto map bft_map 1 set ikev1 transform-set ESP-AES-256-SHA
crypto map bft_map 2 match address bft_cryptomap_1
crypto map bft_map 2 set pfs
crypto map bft_map 2 set peer trsbk-ipsec-gw
crypto map bft_map 2 set ikev1 transform-set ESP-3DES-MD5
crypto map bft_map 3 match address bft_cryptomap_2
crypto map bft_map 3 set pfs
crypto map bft_map 3 set peer bgpb-ipsec-gw
crypto map bft_map 3 set ikev1 transform-set ESP-3DES-SHA
crypto map bft_map 4 match address bft_cryptomap_3
crypto map bft_map 4 set pfs
crypto map bft_map 4 set peer 10.131.11.19
crypto map bft_map 4 set ikev1 transform-set ESP-3DES-SHA
crypto map bft_map 5 match address bft_cryptomap_4
crypto map bft_map 5 set pfs
crypto map bft_map 5 set peer 10.36.2.129
crypto map bft_map 5 set ikev1 transform-set ESP-AES-192-MD5
crypto map bft_map interface bft
crypto map belpak_map 2 match address belpak_cryptomap_1
crypto map belpak_map 2 set pfs
crypto map belpak_map 2 set peer 178.62.1.203
crypto map belpak_map 2 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 3 match address belpak_cryptomap_2
crypto map belpak_map 3 set pfs
crypto map belpak_map 3 set peer 212.98.173.36
crypto map belpak_map 3 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 4 match address belpak_cryptomap_3
crypto map belpak_map 4 set pfs
crypto map belpak_map 4 set peer 82.196.67.178
crypto map belpak_map 4 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 5 match address belpak_cryptomap_4
crypto map belpak_map 5 set pfs
crypto map belpak_map 5 set peer 86.57.147.21
crypto map belpak_map 5 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 6 match address belpak_cryptomap_5
crypto map belpak_map 6 set pfs
crypto map belpak_map 6 set peer 86.57.167.46
crypto map belpak_map 6 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 7 match address belpak_cryptomap_6
crypto map belpak_map 7 set pfs
crypto map belpak_map 7 set peer 86.57.255.167
crypto map belpak_map 7 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 8 match address belpak_cryptomap_7
crypto map belpak_map 8 set peer 87.252.232.9
crypto map belpak_map 8 set ikev1 transform-set ESP-AES-256-SHA
crypto map belpak_map 9 match address belpak_cryptomap_8
crypto map belpak_map 9 set peer 89.106.184.89
crypto map belpak_map 9 set ikev1 transform-set ESP-AES-256-SHA
crypto map belpak_map 10 match address belpak_cryptomap_9
crypto map belpak_map 10 set peer 91.90.223.252
crypto map belpak_map 10 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 12 match address belpak_cryptomap
crypto map belpak_map 12 set pfs
crypto map belpak_map 12 set peer 178.124.182.101
crypto map belpak_map 12 set ikev1 transform-set ESP-3DES-SHA
crypto map belpak_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map belpak_map interface belpak
crypto map ghu_map 1 match address ghu_cryptomap_4
crypto map ghu_map 1 set pfs group5
crypto map ghu_map 1 set peer 185.183.120.59
crypto map ghu_map 1 set ikev1 transform-set ESP-AES-256-SHA
crypto map ghu_map 2 match address ghu_cryptomap_5
crypto map ghu_map 2 set pfs group5
crypto map ghu_map 2 set peer 185.183.120.62
crypto map ghu_map 2 set ikev1 transform-set ESP-AES-256-SHA
crypto map ghu_map 2 set security-association lifetime seconds 3600
crypto map ghu_map 3 match address ghu_cryptomap_2
crypto map ghu_map 3 set pfs group5
crypto map ghu_map 3 set peer 193.176.181.151
crypto map ghu_map 3 set ikev1 transform-set ESP-AES-256-SHA
crypto map ghu_map 4 match address ghu_cryptomap_3
crypto map ghu_map 4 set pfs
crypto map ghu_map 4 set peer 86.57.253.146
crypto map ghu_map 4 set ikev1 transform-set ESP-3DES-MD5
crypto map ghu_map 10 match address ghu_cryptomap_10
crypto map ghu_map 10 set peer 91.90.223.252
crypto map ghu_map 10 set ikev1 transform-set ESP-3DES-SHA
crypto map ghu_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map ghu_map interface ghu
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.11.254,CN=bs-asa5506x
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpoint bsmr
keypair bsmr
crl configure
crypto ca trustpoint bsmr-1
crl configure
crypto ca trustpoint bsmr-local
keypair bsmr-local
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate 2b1f545e
308202da 308201c2 a0030201 0202042b 1f545e30 0d06092a 864886f7 0d01010b
0500302f 31143012 06035504 03130b62 732d6173 61353530 36783117 30150603
55040313 0e313932 2e313638 2e31312e 32353430 1e170d32 30303232 34313931
3634305a 170d3330 30323231 31393136 34305a30 2f311430 12060355 0403130b
62732d61 73613535 30367831 17301506 03550403 130e3139 322e3136 382e3131
2e323534 30820122 300d0609 2a864886 f70d0101 01050003 82010f00 3082010a
02820101 00f0b719 8d81e9c6 263bcdca 50537a41 401387af 680310c1 513c770a
7c2ce0d2 0444c360 2aa8993c 5fbf0c17 8382f287 d6abc691 b60c8a2c 16014d53
d4413d51 cf32bd3d f9f1acda 0231aabb e64cc7b0 78315d1b d2185f9e 0b99756c
4ed7ecb8 55be9c6d 4cd9048a b9db9850 93578424 3a8a722a 572516f8 5d8906fb
cdd2aead 5f3749c4 7f7de8fe 6790576f 80b11057 fe53076a 4e1aa631 04d46c26
7d2c56ed 0078a2fd d0b950b0 48a55db3 727ac4be c1128f7b 076f6590 09696a67
3c3ee6be 93ad2a82 51017285 f0cbb4e7 afdd36a3 3d5afde3 05bc2701 20c0d50c
d155a5c6 e40d003d 6e862e41 006db8f3 84daa6c3 9953e0d9 878b28f7 9f60a9c3
8f446bc0 bd020301 0001300d 06092a86 4886f70d 01010b05 00038201 01004533
bd5179c2 627baf95 7787b1bf 3c8335a8 32cf0326 941e5d03 42711525 1a4337ac
79643efe 94c0d6bd 8750b817 076d9232 a60992f5 c3db80b0 34972988 a135392b
bd52ae86 2ebad8de 4d9a797f 7079d6a0 79880559 1008342c 2eb3f8fd 630e76f4
cc25f151 183e5d0d db3c0cb4 8ebf2fae 74940192 e4711c6a 687ec49f c0911c24
b8c815a5 8b6512b6 ba8c71b3 7a2f83a0 3d5ea8c8 eaea1cc3 a266c228 10272ed6
c8522c4a 6c7be8cf 5d8f5730 7fef9860 8ff0081b 197f294b c262c4d3 9dc747fb
d10f8681 59528a17 fa5b1da2 4ed9c937 c5e933e0 597d2477 d424e032 03960412
b4e00c75 45df6506 d56a26f2 c6505d15 ef4b57c9 36d6005c 56032b0c d552
quit
crypto ca certificate chain bsmr
certificate ca 08a5a246cd4b5c8c83d702b4bbab5349
308204b1 30820399 a0030201 02021008 a5a246cd 4b5c8c83 d702b4bb ab534930
0d06092a 864886f7 0d01010b 05003061 310b3009 06035504 06130255 53311530
13060355 040a130c 44696769 43657274 20496e63 31193017 06035504 0b131077
77772e64 69676963 6572742e 636f6d31 20301e06 03550403 13174469 67694365
72742047 6c6f6261 6c20526f 6f742043 41301e17 0d313731 31303631 32323333
335a170d 32373131 30363132 32333333 5a305e31 0b300906 03550406 13025553
31153013 06035504 0a130c44 69676943 65727420 496e6331 19301706 0355040b
13107777 772e6469 67696365 72742e63 6f6d311d 301b0603 55040313 14526170
69645353 4c205253 41204341 20323031 38308201 22300d06 092a8648 86f70d01
01010500 0382010f 00308201 0a028201 0100e52d a88a1128 f679e97b 3a33883b
71e1658b 2c2965fd ed2dd446 1e984e67 f8c80fe6 f89a1cbc be5691cf fa7757e4
3d7c20d2 2eb8057c c05ab6e8 a1795345 8d219890 a7a98bb4 85a351e5 833c0dbc
39eca14e 58fd4cb9 366decad 6ed154eb 2a5ba565 25b66bd8 e55f2782 ca42ee71
513428e9 7e70c40f 6911c89c cef32a0a 305cf827 8244f0de cd035b89 c1410531
4bc72ecd 2c70ba0f 66429c7b 02119b54 55d80c66 150c4991 d7fb60df 4f724922
7f65e09b 76f8f016 67d337f4 a97b1278 6bbce2e6 bd830ce3 cc8eed6d 30636b24
e94fefd7 a56b8156 fe9fbdaa c8e9b8a4 281f39f4 e48642ec 3bdd75e0 7ae17010
f1d3211a 14b64cee dff110f8 bb70ce79 24750203 010001a3 82016630 82016230
1d060355 1d0e0416 041453ca 1759fc6b c003212f 1aaee4aa a81c8256 da75301f
0603551d 23041830 16801403 de503556 d14cbb66 f0a3e21b 1bc397b2 3dd15530
0e060355 1d0f0101 ff040403 02018630 1d060355 1d250416 30140608 2b060105
05070301 06082b06 01050507 03023012 0603551d 130101ff 04083006 0101ff02
01003034 06082b06 01050507 01010428 30263024 06082b06 01050507 30018618
68747470 3a2f2f6f 6373702e 64696769 63657274 2e636f6d 30420603 551d1f04
3b303930 37a035a0 33863168 7474703a 2f2f6372 6c332e64 69676963 6572742e
636f6d2f 44696769 43657274 476c6f62 616c526f 6f744341 2e63726c 30630603
551d2004 5c305a30 37060960 86480186 fd6c0102 302a3028 06082b06 01050507
0201161c 68747470 733a2f2f 7777772e 64696769 63657274 2e636f6d 2f435053
300b0609 60864801 86fd6c01 01300806 0667810c 01020130 08060667 810c0102
02300d06 092a8648 86f70d01 010b0500 03820101 007e23c7 f2ca356e 5992515c
616b3c12 36e6d27c b329e642 d8a39561 1ecff207 af2b2b25 5a6e17a3 8052ccaa
f6df916c 278685b7 ac808afd 5e634b59 fd9375f1 b3864864 ada0473f 244e2870
8cebf0fe 4c835d64 4581db9a 0627af54 717a48b9 99279bdf d0c6c53a 490f8906
86ce655c da28e1ca 27522889 c0a6aa1f bbe1d9b6 abc9df29 30849a83 cdc952ac
9519cdad 58fa4ed3 7dbdfc25 aada4af2 aafeba39 2323c2e9 54cf4757 7f838741
ab11ec23 5f22bfb8 29271ce8 00654394 4317ce8f 19e13a91 dc124241 6207f710
cac372ab 48c40d04 e47dada9 8e6b96b4 c08d6c19 e1157058 7a37ee6c 885a51b1
2fd85390 0777426a ff853e0e 5e12f797 4d5c8c9c 6a
quit
certificate 0e5ba9dfeef847fce4e0ee6d28066eac
30820628 30820510 a0030201 0202100e 5ba9dfee f847fce4 e0ee6d28 066eac30
0d06092a 864886f7 0d01010b 0500305e 310b3009 06035504 06130255 53311530
13060355 040a130c 44696769 43657274 20496e63 31193017 06035504 0b131077
77772e64 69676963 6572742e 636f6d31 1d301b06 03550403 13145261 70696453
534c2052 53412043 41203230 3138301e 170d3139 31303039 30303030 30305a17
0d323131 32303731 32303030 305a3017 31153013 06035504 030c0c2a 2e626573
6d617274 2e627930 82012230 0d06092a 864886f7 0d010101 05000382 010f0030
82010a02 82010100 ca7d9163 66b1a078 fb744c89 99be68b3 8648096f f608db07
9d0beda0 7a6852d7 3ab1eff6 5cc73780 a6d72c5f c6cbee3d 5242b173 a9b86289
bbda9aee 322edf33 386b988f d87bab9d b633c8e4 78deec2e c185193d 74f7adf3
3fc56e29 e15a085f 83d43d56 88287b83 c8f1e2f9 d366830b 9cd0041c fa742fe8
bfbcb84b 9109a9b2 209ba6a5 458d2052 6e3f4638 10b7a9c7 3bbcda3f 901b107d
1251222d c0b4caf2 bb68b3fa 8b489895 dc0a177f bc138a04 1ce1f273 0b313436
a55f859c e7e459c9 f7c3df4c 9fa1b82f 1d69c4c3 eb799848 27e6bd9e 20b1b683
3066face 6f055653 5c634260 68c0bb4c fd749de1 0c6a4f27 f50db373 e234bf99
cfff272d 8530d561 02030100 01a38203 27308203 23301f06 03551d23 04183016
801453ca 1759fc6b c003212f 1aaee4aa a81c8256 da75301d 0603551d 0e041604
143398d2 f9d4c17e add4db36 c769120d 37d88b8a 54302306 03551d11 041c301a
820c2a2e 6265736d 6172742e 6279820a 6265736d 6172742e 6279300e 0603551d
0f0101ff 04040302 05a0301d 0603551d 25041630 1406082b 06010505 07030106
082b0601 05050703 02303e06 03551d1f 04373035 3033a031 a02f862d 68747470
3a2f2f63 64702e72 61706964 73736c2e 636f6d2f 52617069 6453534c 52534143
41323031 382e6372 6c304c06 03551d20 04453043 30370609 60864801 86fd6c01
02302a30 2806082b 06010505 07020116 1c687474 70733a2f 2f777777 2e646967
69636572 742e636f 6d2f4350 53300806 0667810c 01020130 7506082b 06010505
07010104 69306730 2606082b 06010505 07300186 1a687474 703a2f2f 73746174
75732e72 61706964 73736c2e 636f6d30 3d06082b 06010505 07300286 31687474
703a2f2f 63616365 7274732e 72617069 6473736c 2e636f6d 2f526170 69645353
4c525341 43413230 31382e63 72743009 0603551d 13040230 00308201 7b060a2b
06010401 d6790204 02048201 6b048201 67016500 7500a4b9 0990b418 581487bb
13a2cc67 700a3c35 9804f91b dfb8e377 cd0ec80d dc100000 016db043 fb5b0000
04030046 30440221 0086a565 1456c476 c4d791fe 80ed689f 9b0dcce4 249f2a13
d5298b04 94a57225 bb021f7c 68ac9ff7 d03cfae9 823c9c73 0addbed6 804e3029
6ae1573c 670954b7 bcef0075 008775bf e7597cf8 8c43995f bdf36eff 568d4756
36ff4ab5 60c1b4ea ff5ea083 0f000001 6db043fb c7000004 03004630 4402205d
835d0c43 8077cac4 c997b4a0 01b08542 35c6c418 3fc95f0d 6860e6ae 79063902
20761e90 3220944e b7b05719 da5aea3b 4452757a e3f3708d db876670 fd43de47
1b007500 4494652e b0eeceaf c44007d8 a8fe28c0 dae682be d8cb31b5 3fd33396
b5b681a8 0000016d b043fad0 00000403 00463044 022074e4 535cfd30 f31cf425
37fa6104 6ab6b29b d5fa3ecf 15f3682e 2743c7fb 52fc0220 48867d47 7f09e403
67ec536b 45525bb8 4b635cb8 032ad7fd bf9fa87a cca00938 300d0609 2a864886
f70d0101 0b050003 82010100 4e87a1f9 2573d77a 5c3d8065 4df6035c 093600f9
6b0b4ebe 1ccac259 0634fee2 b462f497 a0084eaf 424df5b8 ea4f8810 0abd571e
7627c2d3 59139964 e6755593 4fcb4ee2 d5570fbd e0ed1e33 4882f80b e3c26ade
ba56fcdd 61d24f39 2d0556d0 1890b806 5dabe910 234e71d9 b4ecbd4b e32e0b54
b8156340 96d71ddd 46bb8eaf 75a60314 de64cc85 88773d63 f685a69f 0cf02905
1442d444 6d63d8d0 bc9bc7ef ac445a0a 97c651b7 1772e3fa 72ce3cd8 63e9ab81
2b79cb57 7b01c12d 35234dd0 ed88bd7e 74b10d16 9876c091 ebb2af5a 5a6b8145
b0e3e786 b35bca4c 81cb1120 22469851 907542e4 14d81164 9f660028 390099ab
4593c808 c231b229 6fcfad89
quit
crypto ca certificate chain bsmr-1
certificate ca 083be056904246b1a1756ac95991c74a
308203af 30820297 a0030201 02021008 3be05690 4246b1a1 756ac959 91c74a30
0d06092a 864886f7 0d010105 05003061 310b3009 06035504 06130255 53311530
13060355 040a130c 44696769 43657274 20496e63 31193017 06035504 0b131077
77772e64 69676963 6572742e 636f6d31 20301e06 03550403 13174469 67694365
72742047 6c6f6261 6c20526f 6f742043 41301e17 0d303631 31313030 30303030
305a170d 33313131 31303030 30303030 5a306131 0b300906 03550406 13025553
31153013 06035504 0a130c44 69676943 65727420 496e6331 19301706 0355040b
13107777 772e6469 67696365 72742e63 6f6d3120 301e0603 55040313 17446967
69436572 7420476c 6f62616c 20526f6f 74204341 30820122 300d0609 2a864886
f70d0101 01050003 82010f00 3082010a 02820101 00e23be1 1172dea8 a4d3a357
aa50a28f 0b7790c9 a2a5ee12 ce965b01 0920cc01 93a74e30 b753f743 c4690057
9de28d22 dd870640 008109ce ce1b83bf dfcd3b71 46e2d666 c705b376 27168f7b
9e1e957d eeb748a3 08dad6af 7a0c3906 657f4a5d 1fbc17f8 abbeee28 d7747f7a
78995985 686e5c23 324bbf4e c0e85a6d e370bf77 10bffc01 f685d9a8 44105832
a97518d5 d1a2be47 e2276af4 9a33f849 08608bd4 5fb43a84 bfa1aa4a 4c7d3ecf
4f5f6c76 5ea04b37 919edc22 e66dce14 1a8e6acb fecdb314 6417c75b 299e32bf
f2eefad3 0b42d4ab b74132da 0cd4eff8 81d5bb8d 583fb51b e84928a2 70da3104
ddf7b216 f24c0a4e 07a8ed4a 3d5eb57f a390c3af 27020301 0001a363 3061300e
0603551d 0f0101ff 04040302 0186300f 0603551d 130101ff 04053003 0101ff30
1d060355 1d0e0416 041403de 503556d1 4cbb66f0 a3e21b1b c397b23d d155301f
0603551d 23041830 16801403 de503556 d14cbb66 f0a3e21b 1bc397b2 3dd15530
0d06092a 864886f7 0d010105 05000382 010100cb 9c37aa48 13120afa dd449c4f
52b0f4df ae04f579 7908a324 18fc4b2b 84c02db9 d5c7fef4 c11f58cb b86d9c7a
74e79829 ab11b5e3 70a0a1cd 4c889993 8c9170e2 ab0f1cbe 93a9ff63 d5e40760
d3a3bf9d 5b09f1d5 8ee353f4 8e63fa3f a7dbb466 df6266d6 d16e418d f22db5ea
774a9f9d 58e22b59 c04023ed 2d288245 3e795492 2698e080 48a837ef f0d67960
16deace8 0ecd6eac 4417382f 49dae145 3e2ab936 53cf3a50 06f72ee8 c457496c
612118d5 04ad783c 2c3a806b a7ebaf15 14e9d889 c1b9386c e2916c8a ff64b977
255730c0 1b24a3e1 dce9df47 7cb5b424 080530ec 2dbd0bbf 45bf50b9 a9f3eb98
0112adc8 88c69834 5f8d0a3c c6e9d595 956dde
quit
crypto ca certificate chain bsmr-local
certificate ca 28f6803d0119f69a4dcf117581af0df9
3082036d 30820255 a0030201 02021028 f6803d01 19f69a4d cf117581 af0df930
0d06092a 864886f7 0d01010b 05003049 31153013 060a0992 268993f2 2c640119
16056c6f 63616c31 17301506 0a099226 8993f22c 64011916 07426553 6d617274
31173015 06035504 03130e42 65536d61 72742d44 43322d43 41301e17 0d323030
32303531 39353835 345a170d 33303032 30353230 30383533 5a304931 15301306
0a099226 8993f22c 64011916 056c6f63 616c3117 3015060a 09922689 93f22c64
01191607 4265536d 61727431 17301506 03550403 130e4265 536d6172 742d4443
322d4341 30820122 300d0609 2a864886 f70d0101 01050003 82010f00 3082010a
02820101 00bf1a7b f91da277 3793d07d 0102bc64 6de73659 a98dba2f 320dcd90
969a45d1 8ad77f98 a838d143 45602d42 53de8ac9 725a7c8a f5873ae2 dd5515f7
20f2541d 141a8022 0ee9baf3 0276132e a15d9eae d445ec06 e5979998 24bf075a
2e69c1c8 3e095ed1 c607908f ac600d58 30ea2eb3 68b2f1f9 871be428 4521c094
6c0b4d9b d02bf9f7 be601619 bc713d50 8f46ebef d153d88e 7bfaeaac b5d3ff18
2eaca5d8 419cdd81 66ba53f3 85901e6b b1cf0325 bca01f30 abac4686 7f0f076c
31161785 387d6c90 c3c9a5ce 3a9899c2 c075c019 c76633d5 74c77a56 d036e762
e7d1ac79 ea8f28e6 90e50da7 efed26e2 caf6ed8e b32f2129 f788ca7c 905deb05
a23f1da0 5f020301 0001a351 304f300b 0603551d 0f040403 02018630 0f060355
1d130101 ff040530 030101ff 301d0603 551d0e04 16041442 42a57fda 8beeeb60
a2cfc2e7 c757878d d026cd30 1006092b 06010401 82371501 04030201 00300d06
092a8648 86f70d01 010b0500 03820101 006c18d4 e226bf42 10d104cd ceb49c0c
ec4c77d9 dc11f413 d11fdecf 021ff57f 96c2a832 99039a63 f243230f e60af500
41626ce5 67d637b8 4b3a42e3 c57171ac b3279f0b 1e2f5d26 53c902ce 545e7824
e25dcff4 3eabdece 5c09663f b44119e0 3b843c6f ad1ae2d4 5c17c93f ec26e36c
915856df a4c2384e 41afb083 fcaaa83a 3549cafd 6e7b95ad b8bed779 2e40e296
a12ec820 aa59bb17 caea495c 4e60a2d9 42538c9c 050efd39 d860aa8d 52f20402
ac33bed2 e1054db6 64adbd49 fd766c05 5be0d8e2 15bb401a f6f99ad9 8699e1bc
b57b321e 2478c6fc 0073ab7f 9e28f2a9 899fea13 f2d675fa 9aa86211 efcde0a2
bd4d522b 42c57d5b bbd5d203 5f7bf686 ab
quit
certificate 1f0fb7dc000000000032
30820598 30820480 a0030201 02020a1f 0fb7dc00 00000000 32300d06 092a8648
86f70d01 010b0500 30493115 3013060a 09922689 93f22c64 01191605 6c6f6361
6c311730 15060a09 92268993 f22c6401 19160742 65536d61 72743117 30150603
55040313 0e426553 6d617274 2d444332 2d434130 1e170d32 30303232 37323031
3535375a 170d3232 30323236 32303135 35375a30 7a310b30 09060355 04061302
4259310e 300c0603 55040713 054d696e 736b3110 300e0603 55040a13 07426553
6d617274 310b3009 06035504 0b130249 54311a30 18060355 04031311 6173612e
6265736d 6172742e 6c6f6361 6c312030 1e06092a 864886f7 0d010901 16116273
2d6e6574 40626573 6d617274 2e627930 82012230 0d06092a 864886f7 0d010101
05000382 010f0030 82010a02 82010100 aa11bef4 48769ce0 ae4e44d0 47c70469
8d03d4a9 22fcb9c0 66f0dd40 334c683d 74112079 53a5d5e0 9bb41306 333da03b
25d83f80 0d67979b a2fcd990 eb56d85b 40bd7000 00685e7e 50262aca b19703a6
12bb1286 6b41cc72 c4cd51f8 5a8c5da4 c2b824d3 eaba91cd 340f1d52 97d5ebb8
e223a141 738dd025 ac1a830c dade4d69 8d155554 47383fb8 18eea604 c0075664
e8ea4060 7ae71582 d88cbcf1 20b2929c dcfde148 71802a23 e0781b3c ad5eab34
311ce452 11d53555 03853ff6 aa479432 88111ea4 96d2f328 af479812 629cb501
b637a2ed 70058a5a b9c90c7d 5ba0f4e2 9b5efbce 235d880f 6c98b831 bc986847
f24df53b c19c38fc c936ba18 4590e3e7 02030100 01a38202 4f308202 4b302f06
03551d11 04283026 82116173 612e6265 736d6172 742e6c6f 63616c82 03617361
820c3137 322e3136 2e313932 2e32301d 0603551d 0e041604 14ab5fc0 00d967d1
775f2ef2 51aa96a0 3a07d75b c4301f06 03551d23 04183016 80144242 a57fda8b
eeeb60a2 cfc2e7c7 57878dd0 26cd3081 ca060355 1d1f0481 c23081bf 3081bca0
81b9a081 b68681b3 6c646170 3a2f2f2f 434e3d42 65536d61 72742d44 43322d43
412c434e 3d444332 2c434e3d 4344502c 434e3d50 75626c69 63253230 4b657925
32305365 72766963 65732c43 4e3d5365 72766963 65732c43 4e3d436f 6e666967
75726174 696f6e2c 44433d42 65536d61 72742c44 433d6c6f 63616c3f 63657274
69666963 61746552 65766f63 6174696f 6e4c6973 743f6261 73653f6f 626a6563
74436c61 73733d63 524c4469 73747269 62757469 6f6e506f 696e7430 81c20608
2b060105 05070101 0481b530 81b23081 af06082b 06010505 07300286 81a26c64
61703a2f 2f2f434e 3d426553 6d617274 2d444332 2d43412c 434e3d41 49412c43
4e3d5075 626c6963 2532304b 65792532 30536572 76696365 732c434e 3d536572
76696365 732c434e 3d436f6e 66696775 72617469 6f6e2c44 433d4265 536d6172
742c4443 3d6c6f63 616c3f63 41436572 74696669 63617465 3f626173 653f6f62
6a656374 436c6173 733d6365 72746966 69636174 696f6e41 7574686f 72697479
30210609 2b060104 01823714 0204141e 12005700 65006200 53006500 72007600
65007230 0e060355 1d0f0101 ff040403 0205a030 13060355 1d25040c 300a0608
2b060105 05070301 300d0609 2a864886 f70d0101 0b050003 82010100 6399f4a6
2f8c9da8 1860de39 e70dfa36 4d6644f3 e8b54556 5811c83d 14d2161c a0121c18
574ecb08 6aaca0e6 d34fabd1 2e5520f7 c6f97485 ab944bf9 e987366b a63a0fde
dddd939b 5412804b eb130a15 e26eae67 a2fea657 54e2e469 d8bb8ffb 549e600a
6f0e0f69 9a38c3b2 d3113021 c5f7d228 68bcc52a 0cce5bd7 446d05eb 2fb5adf4
9ebe9f66 ce88604e cb9e59be 627b6c43 6d0a0afe b7878a17 4999be16 5f101209
67ba33ac 912f1957 f57190a1 6f4f5c1e 6d8f3485 da9220ba a2cb251c ac010b58
6e0c407c aff7afa5 82fc0b28 0561386f 7853af4a a885dbf1 9b81fb43 a5626d14
8a4a6e6a e906e7f8 17ff3fc5 8c8362c7 61ab21f0 f32884ee deb49fa3
quit
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable belpak client-services port 443
crypto ikev2 enable ghu client-services port 34443
crypto ikev2 enable bft
crypto ikev2 remote-access trustpoint bsmr
crypto ikev1 enable belpak
crypto ikev1 enable ghu
crypto ikev1 enable bft
crypto ikev1 ipsec-over-tcp port 7979
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 28800
crypto ikev1 policy 11
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 12
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 policy 13
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 3600
crypto ikev1 policy 100
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 3600
crypto ikev1 policy 101
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 103
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
crypto ikev1 policy 198
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto ikev1 policy 199
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
!
track 14 rtr 14 reachability
!
track 49 rtr 49 reachability
!
track 101 rtr 101 reachability
!
track 102 rtr 102 reachability
!
track 129 rtr 129 reachability
!
track 249 rtr 249 reachability
telnet timeout 5
ssh stricthostkeycheck
ssh 178.124.163.162 255.255.255.255 belpak
ssh 86.57.253.144 255.255.255.240 belpak
ssh 212.98.163.80 255.255.255.240 belpak
ssh 212.98.163.80 255.255.255.240 ghu
ssh 86.57.253.144 255.255.255.240 ghu
ssh 178.124.163.162 255.255.255.255 ghu
ssh 10.1.36.126 255.255.255.255 bft
ssh 0.0.0.0 0.0.0.0 inside
ssh 0.0.0.0 0.0.0.0 mgmt
ssh timeout 15
ssh version 2
ssh key-exchange group dh-group14-sha1
console timeout 35
management-access inside
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ntp server 192.168.111.247 source inside
ntp server 192.168.111.246 source inside prefer
tftp-server inside 192.168.111.250 /
ssl trust-point bsmr belpak
ssl trust-point bsmr ghu
ssl trust-point bsmr bft
ssl trust-point bsmr inside
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 mgmt
ssl trust-point ASDM_Launcher_Access_TrustPoint_0 mgmt vpnlb-ip
ssl trust-point bsmr domain asa.bsmr.by
ssl trust-point bsmr-local domain asa.bsmr.local
ssl trust-point bsmr domain ftp3.bsmr.by
ssl trust-point bsmr domain vpn1.bsmr.by
webvpn
port 34443
enable belpak
enable ghu
dtls port 54443
anyconnect image disk0:/anyconnect-win-4.7.04056-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-linux64-4.7.04056-webdeploy-k9.pkg 2
anyconnect image disk0:/anyconnect-macos-4.7.04056-webdeploy-k9.pkg 3
anyconnect profiles Anyconnect-BS-Office-NODNS_client_profile disk0:/Anyconnect-BS-Office-NODNS_client_profile.xml
anyconnect profiles Anyconnect-BS-Office_client_profile disk0:/Anyconnect-BS-Office_client_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy GroupPolicy_10.1.XX.YY internal
group-policy GroupPolicy_10.1.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_10.131.YY.XX internal
group-policy GroupPolicy_10.131.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_10.36.XX.YY internal
group-policy GroupPolicy_10.36.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_87.252.YY.XX internal
group-policy GroupPolicy_87.252.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_89.106.YY.XX internal
group-policy GroupPolicy_89.106.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_185.183.YY.XX internal
group-policy GroupPolicy_185.183.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_82.196.YY.XX internal
group-policy GroupPolicy_82.196.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_86.57.YY.XX internal
group-policy GroupPolicy_86.57.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_212.98.YY.XX internal
group-policy GroupPolicy_212.98.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_86.57.YY.XX internal
group-policy GroupPolicy_86.57.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_86.57.YY.XX internal
group-policy GroupPolicy_86.57.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_10.1.YY.XX internal
group-policy GroupPolicy_10.1.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_Anyconnect-BS-Office internal
group-policy GroupPolicy_Anyconnect-BS-Office attributes
wins-server none
dns-server value 192.168.111.246 192.168.111.247
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value bs-office-vpn-split
default-domain value bsmr.local
webvpn
anyconnect profiles value Anyconnect-BS-Office_client_profile type user
group-policy GroupPolicy_178.62.YY.XX internal
group-policy GroupPolicy_178.62.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_Anyconnect-BS-Office-NODNS internal
group-policy GroupPolicy_Anyconnect-BS-Office-NODNS attributes
wins-server none
dns-server none
vpn-tunnel-protocol ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value bs-office-vpn-split
default-domain none
webvpn
anyconnect profiles value Anyconnect-BS-Office-NODNS_client_profile type user
group-policy GroupPolicy_10.1.YY.XX internal
group-policy GroupPolicy_10.1.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_91.90.YY.XX internal
group-policy GroupPolicy_91.90.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_185.183.YY.XX internal
group-policy GroupPolicy_185.183.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_178.124.YY.XX internal
group-policy GroupPolicy_178.124.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_193.176.YY.XX internal
group-policy GroupPolicy_193.176.YY.XX attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy_86.57.YY.XX internal
group-policy GroupPolicy_86.57.1YY.XX attributes
vpn-tunnel-protocol ikev1
dynamic-access-policy-record DfltAccessPolicy
password-policy minimum-length 6
password-policy minimum-lowercase 1
password-policy minimum-uppercase 1
password-policy minimum-numeric 1
password-policy minimum-special 1
password-policy username-check
username yura password *** pbkdf2 privilege 15
username george password *** encrypted privilege 15
username adm1n password *** encrypted privilege 15
username elic password *** encrypted privilege 15
username nagios password *** encrypted privilege 3
username nagios attributes
service-type nas-prompt
tunnel-group 10.1.YY.XX type ipsec-l2l
tunnel-group 10.1.YY.XX general-attributes
default-group-policy GroupPolicy_10.1.YY.XX
tunnel-group 10.1.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 10.1.YY.XX type ipsec-l2l
tunnel-group 10.1.YY.XX general-attributes
default-group-policy GroupPolicy_10.1.YY.XX
tunnel-group 10.1.40.82 ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group 10.1.YY.XX type ipsec-l2l
tunnel-group 10.1.YY.XX general-attributes
default-group-policy GroupPolicy_10.1.YY.XX
tunnel-group 10.1.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 10.131.YY.XX type ipsec-l2l
tunnel-group 10.131.YY.XX general-attributes
default-group-policy GroupPolicy_10.131.YY.XX
tunnel-group 10.131.11.19 ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 10.36.YY.XX type ipsec-l2l
tunnel-group 10.36.YY.XX general-attributes
default-group-policy GroupPolicy_10.36.YY.XX
tunnel-group 10.36.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 178.124.YY.XX type ipsec-l2l
tunnel-group 178.124.YY.XX general-attributes
default-group-policy GroupPolicy_178.124.YY.XX
tunnel-group 178.124.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 178.62.YY.XX type ipsec-l2l
tunnel-group 178.62.YY.XX general-attributes
default-group-policy GroupPolicy_178.62.YY.XX
tunnel-group 178.62.YY.XX ipsec-attributes
ikev1 pre-shared-key **
tunnel-group 185.183.YY.XX type ipsec-l2l
tunnel-group 185.183.YY.XX general-attributes
default-group-policy GroupPolicy_185.183.YY.XX
tunnel-group 185.183.YY.XX ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 185.183.YY.XX type ipsec-l2l
tunnel-group 185.183.YY.XX general-attributes
default-group-policy GroupPolicy_185.183.YY.XX
tunnel-group 185.183.120.62 ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 193.176.YY.XX type ipsec-l2l
tunnel-group 193.176.YY.XX general-attributes
default-group-policy GroupPolicy_193.176.YY.XX
tunnel-group 193.176.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 212.98.YY.XX type ipsec-l2l
tunnel-group 212.98.YY.XX general-attributes
default-group-policy GroupPolicy_212.98.YY.XX
tunnel-group 212.98.YY.XX ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group 82.196.YY.XX type ipsec-l2l
tunnel-group 82.196.YY.XX general-attributes
default-group-policy GroupPolicy_82.196.YY.XX
tunnel-group 82.196.YY.XX ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group 86.57.YY.XX type ipsec-l2l
tunnel-group 86.57.YY.XX general-attributes
default-group-policy GroupPolicy_86.57.YY.XX
tunnel-group 86.57.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 86.57.YY.XX type ipsec-l2l
tunnel-group 86.57.YY.XX general-attributes
default-group-policy GroupPolicy_86.57.YY.XX
tunnel-group 86.57.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 86.57.YY.XX type ipsec-l2l
tunnel-group 86.57.YY.XX general-attributes
default-group-policy GroupPolicy_86.57.YY.XX
tunnel-group 86.57.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 86.57.YY.XX type ipsec-l2l
tunnel-group 86.57.YY.XX general-attributes
default-group-policy GroupPolicy_86.57.YY.XX
tunnel-group 86.57.YY.XX ipsec-attributes
ikev1 pre-shared-key ****
tunnel-group 87.252.YY.XX type ipsec-l2l
tunnel-group 87.252.YY.XX general-attributes
default-group-policy GroupPolicy_87.252.YY.XX
tunnel-group 87.252.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 89.106.YY.XX type ipsec-l2l
tunnel-group 89.106.YY.XX general-attributes
default-group-policy GroupPolicy_89.106.YY.XX
tunnel-group 89.106.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group 91.90.YY.XX type ipsec-l2l
tunnel-group 91.90.YY.XX general-attributes
default-group-policy GroupPolicy_91.90.YY.XX
tunnel-group 91.90.YY.XX ipsec-attributes
ikev1 pre-shared-key ***
tunnel-group Anyconnect-BS-Office type remote-access
tunnel-group Anyconnect-BS-Office general-attributes
address-pool VPNClientPool
authentication-server-group BS-LDAP LOCAL
default-group-policy GroupPolicy_Anyconnect-BS-Office
tunnel-group Anyconnect-BS-Office webvpn-attributes
group-alias Anyconnect-BS-Office enable
tunnel-group Anyconnect-BS-Office-NODNS type remote-access
tunnel-group Anyconnect-BS-Office-NODNS general-attributes
address-pool VPNClientPool
authentication-server-group BS-LDAP LOCAL
default-group-policy GroupPolicy_Anyconnect-BS-Office-NODNS
tunnel-group Anyconnect-BS-Office-NODNS webvpn-attributes
group-alias Anyconnect-BS-Office-NODNS enable
!
class-map ftp-pasv-class
match access-list ftp-pasv-list
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect rsh
inspect sunrpc
inspect xdmcp
inspect tftp
inspect ip-options
inspect http
inspect ipsec-pass-thru
inspect esmtp
inspect sip
inspect snmp
inspect icmp
inspect icmp error
inspect ftp
class ftp-pasv-class
inspect ftp
!
service-policy global_policy global
mount ftpipy type ftp
server 86.57.YY.XX
path /
username TEMP
password ****
mode passive
status enable
mount qnap type cifs
server 172.16.YY.XX
share /backups/ADMIN/NETWORK/bs-asa5506x
username cisco_bkp
password ****
status enable
mount qnap-ftp type ftp
server 172.16.YY.XX
path /backups/ADMIN/NETWORK/bs-asa5506x
username cisco_bkp
password ***
mode passive
status enable
privilege cmd level 3 mode exec command perfmon
privilege cmd level 3 mode exec command copy
privilege cmd level 3 mode exec command ping
privilege cmd level 3 mode exec command who
privilege cmd level 3 mode exec command logging
privilege cmd level 3 mode exec command failover
privilege cmd level 3 mode exec command packet-tracer
privilege show level 5 mode exec command running-config
privilege show level 3 mode exec command reload
privilege show level 3 mode exec command mode
privilege show level 3 mode exec command firewall
privilege show level 3 mode exec command cpu
privilege show level 3 mode exec command interface
privilege show level 3 mode exec command clock
privilege show level 3 mode exec command dns-hosts
privilege show level 3 mode exec command access-list
privilege show level 3 mode exec command logging
privilege show level 3 mode exec command vlan
privilege show level 3 mode exec command ip
privilege show level 3 mode exec command failover
privilege show level 3 mode exec command asdm
privilege show level 3 mode exec command arp
privilege show level 3 mode exec command route
privilege show level 3 mode exec command aaa-server
privilege show level 3 mode exec command aaa
privilege show level 3 mode exec command crypto
privilege show level 3 mode exec command ssh
privilege show level 3 mode exec command vpn-sessiondb
privilege show level 3 mode exec command vpn
privilege show level 3 mode exec command dhcpd
privilege show level 3 mode exec command blocks
privilege show level 3 mode exec command wccp
privilege show level 3 mode exec command uauth
privilege show level 3 mode exec command ospf
privilege show level 3 mode exec command eigrp
privilege show level 3 mode configure command interface
privilege show level 3 mode configure command clock
privilege show level 3 mode configure command access-list
privilege show level 3 mode configure command logging
privilege show level 3 mode configure command ip
privilege show level 3 mode configure command failover
privilege show level 5 mode configure command asdm
privilege show level 3 mode configure command arp
privilege show level 3 mode configure command route
privilege show level 3 mode configure command aaa-server
privilege show level 3 mode configure command aaa
privilege show level 3 mode configure command crypto
privilege show level 3 mode configure command ssh
privilege show level 3 mode configure command ssh
privilege show level 3 mode configure command dhcpd
privilege show level 5 mode configure command privilege
privilege clear level 3 mode exec command crypto
privilege clear level 3 mode exec command dns-hosts
privilege clear level 3 mode exec command logging
privilege clear level 3 mode exec command arp
privilege clear level 3 mode exec command aaa-server
privilege clear level 3 mode exec command ipsec
privilege cmd level 3 mode configure command failover
privilege clear level 3 mode configure command logging
privilege clear level 3 mode configure command crypto
privilege clear level 3 mode configure command arp
privilege clear level 3 mode configure command aaa-server
prompt hostname context
no call-home reporting anonymous
event manager applet backupcfg
event timer absolute time 4:35:40
action 1 cli command "backup /noconfirm interface inside location ftp://cisco_bkp:****@172.16.YY.XX:21/ADMIN/NETWORK/bs-asa5506x/"
output none
Cryptochecksum:4a4478537d36ba2a1c218463fd83505e
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 02:35 AM
Hi,
Paste the output of "packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.29 65123 detailed"
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 03:34 AM
10.1.11.29 is gateway in our corporate ISP (10.0.0.0/8)
10.1.11.30 is IP of my ASA (interface bft) to network 10.0.0.0/8.
Anyway, here are two packet tracers:
bs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.29 65123 detailed
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2d3da30, priority=1, domain=permit, deny=false
hits=7439307, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=inside, output_ifc=any
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
NAT divert to egress interface bft
Untranslate 10.1.11.29/65123 to 10.1.11.29/65123
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inside_access_in in interface inside
access-list inside_access_in remark allow outgoing tcp any
access-list inside_access_in extended permit tcp any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac331b0b0, priority=13, domain=permit, deny=false
hits=35468, user_data=0x2aaabbe535c0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
Static translate 192.168.111.250/3389 to 10.1.11.30/65123
Forward Flow based lookup yields rule:
in id=0x2aaac8501c40, priority=6, domain=nat, deny=false
hits=0, user_data=0x2aaac2fd1f00, cs_id=0x0, flags=0x0, protocol=6
src ip/id=192.168.111.250, mask=255.255.255.255, port=3389, tag=any
dst ip/id=bft-network, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=bft
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac1983a80, priority=0, domain=nat-per-session, deny=false
hits=2097614, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2d46950, priority=0, domain=inspect-ip-options, deny=true
hits=1576326, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 7
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
Forward Flow based lookup yields rule:
out id=0x2aaac50a2150, priority=6, domain=nat-reverse, deny=false
hits=1, user_data=0x2aaac5f940b0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=192.168.111.250, mask=255.255.255.255, port=3389, tag=any
dst ip/id=bft-network, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=bft
Phase: 8
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x2aaac1983a80, priority=0, domain=nat-per-session, deny=false
hits=2097616, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 9
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x2aaac2c7c2e0, priority=0, domain=inspect-ip-options, deny=true
hits=51545, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=bft, output_ifc=any
Phase: 10
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 1969503, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Phase: 11
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.11.29 using egress ifc bft
Phase: 12
Type: ADJACENCY-LOOKUP
Subtype: next-hop and adjacency
Result: ALLOW
Config:
Additional Information:
adjacency Active
next-hop mac address 68bd.ab8f.b9f1 hits 28808 reference 14
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: bft
output-status: up
output-line-status: up
Action: allowbs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.30 65123 detailed
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
NAT divert to egress interface bft
Untranslate 10.1.11.30/65123 to 10.1.11.30/65123
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group inside_access_in in interface inside
access-list inside_access_in remark allow outgoing tcp any
access-list inside_access_in extended permit tcp any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac331b0b0, priority=13, domain=permit, deny=false
hits=35531, user_data=0x2aaabbe535c0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 3
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
Static translate 192.168.111.250/3389 to 10.1.11.30/65123
Forward Flow based lookup yields rule:
in id=0x2aaac8501c40, priority=6, domain=nat, deny=false
hits=1, user_data=0x2aaac2fd1f00, cs_id=0x0, flags=0x0, protocol=6
src ip/id=192.168.111.250, mask=255.255.255.255, port=3389, tag=any
dst ip/id=bft-network, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=bft
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac1983a80, priority=0, domain=nat-per-session, deny=false
hits=2099863, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2d46950, priority=0, domain=inspect-ip-options, deny=true
hits=1578268, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 6
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
nat (inside,bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
Additional Information:
Forward Flow based lookup yields rule:
out id=0x2aaac50a2150, priority=6, domain=nat-reverse, deny=false
hits=2, user_data=0x2aaac5f940b0, cs_id=0x0, use_real_addr, flags=0x0, protocol=6
src ip/id=192.168.111.250, mask=255.255.255.255, port=3389, tag=any
dst ip/id=bft-network, mask=255.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=bft
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: bft
output-status: up
output-line-status: up
Action: drop
Drop-reason: (sp-security-failed) Slowpath security checks failed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 06:09 AM
Hi,
One more packet-tracer: "packet-tracer input bft 10.10.10.10 40000 10.1.11.30 65123 detailed".
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 06:13 AM
bs-asa5506x# packet-tracer input bft tcp 10.10.10.10 40000 10.1.11.30 65123 detailed
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2c74ca0, priority=1, domain=permit, deny=false
hits=123886, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=bft, output_ifc=any
Phase: 2
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.11.30 using egress ifc identity
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac1983a80, priority=0, domain=nat-per-session, deny=false
hits=2457862, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 4
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2c760d0, priority=0, domain=permit, deny=true
hits=24, user_data=0xa, cs_id=0x0, use_real_addr, flags=0x1000, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=bft, output_ifc=any
Result:
input-interface: bft
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 06:47 AM
Hi,
The problem is that traffic coming inbound on BFT, destined for your RDP server, does not match the NAT statement and thus the ASA considers it's destined for itself, it does not run any service on TCP 65123 and packet gets dropped. Place the output of "show nat detail" command, issue "clear asp drop", initiate real RDP session and post the output of "show asp drop".
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 08:22 AM
I've added one more PAT statement. This host has no NAT to any other networks (only in bft). Doesn't work as well((
object network 192.168.111.244 host 192.168.111.244 nat (inside,bft) 43 source static 192.168.111.244 interface destination static bft-network bft-network service tcp80 tcp45423
Here is output of 'show nat detail':
bs-asa5506x# show nat detail
Manual NAT Policies (Section 1)
1 (inside) to (belpak) source static bs-nets-inside bs-nets-inside destination static DM_INLINE_NETWORK_1 DM_INLINE_NETWORK_1 no-proxy-arp route-lookup description Exampt to COD
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24
Destination - Origin: datacenter-ipsec-net/24, datacenter-vpn-ipsec-net/27, Translated: datacenter-ipsec-net/24, datacenter-vpn-ipsec-net/27
2 (inside) to (ghu) source static bs-nets-inside bs-nets-inside destination static DM_INLINE_NETWORK_18 DM_INLINE_NETWORK_18 no-proxy-arp route-lookup description Exampt to COD
translate_hits = 1713483, untranslate_hits = 1721237
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24
Destination - Origin: datacenter-ipsec-net/24, datacenter-vpn-ipsec-net/27, Translated: datacenter-ipsec-net/24, datacenter-vpn-ipsec-net/27
3 (inside) to (belpak) source static DM_INLINE_NETWORK_3 DM_INLINE_NETWORK_3 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
translate_hits = 3, untranslate_hits = 3
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, Translated: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24
Destination - Origin: 172.17.19.0/24, Translated: 172.17.19.0/24
4 (inside) to (ghu) source static DM_INLINE_NETWORK_17 DM_INLINE_NETWORK_17 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, Translated: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24
Destination - Origin: 172.17.19.0/24, Translated: 172.17.19.0/24
5 (inside) to (ghu) source static bs-nets-inside bs-nets-inside destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24
Destination - Origin: 172.17.19.0/24, Translated: 172.17.19.0/24
6 (bft) to (belpak) source static DM_INLINE_NETWORK_2 DM_INLINE_NETWORK_2 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
translate_hits = 0, untranslate_hits = 0
Source - Origin: datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, trustbank-ipsec-host/32, Translated: datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, trustbank-ipsec-host/32
Destination - Origin: 172.17.19.0/24, Translated: 172.17.19.0/24
7 (bft) to (ghu) source static DM_INLINE_NETWORK_9 DM_INLINE_NETWORK_9 destination static vpn-client-net vpn-client-net no-proxy-arp route-lookup description Exampt to vpn client net
translate_hits = 0, untranslate_hits = 0
Source - Origin: datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, trustbank-ipsec-host/32, Translated: datacenter-dmz-ipsec-network/24, datacenter-ipsec-net/24, trustbank-ipsec-host/32
Destination - Origin: 172.17.19.0/24, Translated: 172.17.19.0/24
8 (belpak) to (bft) source static stylesoftvpnpool stylesoftvpnpool destination static paritet-host paritet-host no-proxy-arp route-lookup description Exampt to paritet for stylesoft vpn
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.176.0/24, Translated: 172.17.176.0/24
Destination - Origin: 10.9.1.2/32, Translated: 10.9.1.2/32
9 (belpak) to (ghu) source static vpn-client-net 192.168.181.0 destination static boil-stand boil-stand description vpn client to boil stand
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.181.0/24
Destination - Origin: 10.93.1.24/32, Translated: 10.93.1.24/32
10 (belpak) to (belpak) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32, Translated: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32
11 (belpak) to (ghu) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32, Translated: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32
12 (belpak) to (belpak) source dynamic vpn-client-net 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 172.17.221.100/32
Destination - Origin: 192.168.200.0/24, Translated: 192.168.200.0/24
13 (belpak) to (belpak) source dynamic vpn-client-net 192.168.152.1 destination static parking-grodno401 parking-grodno401
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.152.1/32
Destination - Origin: 172.18.152.0/28, Translated: 172.18.152.0/28
14 (belpak) to (belpak) source dynamic vpn-client-net 172.18.196.100 destination static bps-hosts bps-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 172.18.196.100/32
Destination - Origin: 172.30.71.100/32, 172.30.71.60/32, 172.30.71.61/32, 172.30.71.18/32, Translated: 172.30.71.100/32, 172.30.71.60/32, 172.30.71.61/32, 172.30.71.18/32
15 (belpak) to (belpak) source dynamic vpn-client-net interface destination static 91.212.63.183 91.212.63.183 description NAT to RIB Staging for access from VPN i.karpov
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 82.209.233.250/29
Destination - Origin: 91.212.63.183/32, Translated: 91.212.63.183/32
16 (belpak) to (ghu) source dynamic vpn-client-net interface destination static 91.212.63.183 91.212.63.183 description NAT to RIB Staging for access from VPN i.karpov
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: ghu.bs/27
Destination - Origin: 91.212.63.183/32, Translated: 91.212.63.183/32
17 (belpak) to (belpak) source dynamic vpn-client-net interface destination static 212.98.183.211 212.98.183.211
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 82.209.233.250/29
Destination - Origin: 212.98.183.211/32, Translated: 212.98.183.211/32
18 (belpak) to (ghu) source dynamic vpn-client-net interface destination static 212.98.183.211 212.98.183.211
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: ghu.bs/27
Destination - Origin: 212.98.183.211/32, Translated: 212.98.183.211/32
19 (belpak) to (belpak) source dynamic vpn-client-net interface destination static 193.176.181.151 193.176.181.151 description ticketpro hosting
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 82.209.233.250/29
Destination - Origin: 193.176.181.151/32, Translated: 193.176.181.151/32
20 (belpak) to (ghu) source dynamic vpn-client-net interface destination static 193.176.181.151 193.176.181.151 description ticketpro hosting
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: ghu.bs/27
Destination - Origin: 193.176.181.151/32, Translated: 193.176.181.151/32
21 (belpak) to (belpak) source dynamic vpn-client-net 192.168.21.100 destination static trustbank-ipsec-host trustbank-ipsec-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.21.100/32
Destination - Origin: 212.98.162.139/32, Translated: 212.98.162.139/32
22 (belpak) to (belpak) source static parkomats-vpn-pool 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net description Parkomats to BPS authontication servers
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.203.0/26, Translated: 192.168.22.1/32
Destination - Origin: 172.30.71.0/24, Translated: 172.30.71.0/24
23 (belpak) to (bft) source dynamic vpn-client-net 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.20.100/32
Destination - Origin: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32, Translated: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32
24 (belpak) to (bft) source dynamic vpn-client-net 192.168.21.100 destination static trustbank-ipsec-host trustbank-ipsec-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.21.100/32
Destination - Origin: 212.98.162.139/32, Translated: 212.98.162.139/32
25 (belpak) to (bft) source dynamic vpn-client-net interface destination static bft-network bft-network
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
26 (belpak) to (bft) source dynamic stylesoftvpnpool interface destination static paritet-host paritet-host description Stylesoft to Paritet NAT
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.176.0/24, Translated: 10.1.11.30/30
Destination - Origin: 10.9.1.2/32, Translated: 10.9.1.2/32
27 (ghu) to (ghu) source static datacenter-ipsec-net 192.168.181.0 destination static boil-stand boil-stand
translate_hits = 2015, untranslate_hits = 2015
Source - Origin: 192.168.3.0/24, Translated: 192.168.181.0/24
Destination - Origin: 10.93.1.24/32, Translated: 10.93.1.24/32
28 (ghu) to (belpak) source static datacenter-ipsec-net 192.168.181.0 destination static boil-stand boil-stand
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.3.0/24, Translated: 192.168.181.0/24
Destination - Origin: 10.93.1.24/32, Translated: 10.93.1.24/32
29 (ghu) to (belpak) source dynamic vpn-client-net 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 172.17.221.100/32
Destination - Origin: 192.168.200.0/24, Translated: 192.168.200.0/24
30 (ghu) to (ghu) source dynamic vpn-client-net 192.168.152.1 destination static parking-grodno401 parking-grodno401
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.152.1/32
Destination - Origin: 172.18.152.0/28, Translated: 172.18.152.0/28
31 (ghu) to (belpak) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32, Translated: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32
32 (ghu) to (ghu) source dynamic vpn-client-net 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32, Translated: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32
33 (ghu) to (belpak) source dynamic parkomats-vpn-pool 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.203.0/26, Translated: 192.168.22.1/32
Destination - Origin: 172.30.71.0/24, Translated: 172.30.71.0/24
34 (ghu) to (belpak) source dynamic datacenter-vpn-ipsec-net interface destination static access.mnssis.beloil.by access.mnssis.beloil.by
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.191.0/27, Translated: 82.209.233.250/29
Destination - Origin: 93.85.92.194/32, Translated: 93.85.92.194/32
35 (ghu) to (ghu) source dynamic datacenter-vpn-ipsec-net interface destination static access.mnssis.beloil.by access.mnssis.beloil.by
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.191.0/27, Translated: ghu.bs/27
Destination - Origin: 93.85.92.194/32, Translated: 93.85.92.194/32
36 (ghu) to (bft) source dynamic vpn-client-net 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.20.100/32
Destination - Origin: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32, Translated: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32
37 (ghu) to (bft) source dynamic vpn-client-net 192.168.21.100 destination static trustbank-ipsec-host trustbank-ipsec-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.21.100/32
Destination - Origin: 212.98.162.139/32, Translated: 212.98.162.139/32
38 (ghu) to (bft) source dynamic vpn-client-net interface destination static bft-network bft-network
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
39 (belpak) to (ghu) source dynamic vpn-client-net 192.168.222.2 destination static a1-ipay-ipsec-nets a1-ipay-ipsec-nets
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.222.2/32
Destination - Origin: a1-ipay-border/27, a1-ipay-ipsec-dmz/27, Translated: a1-ipay-border/27, a1-ipay-ipsec-dmz/27
40 (belpak) to (ghu) source dynamic vpn-client-net 192.168.223.3 destination static a1-smartpay a1-smartpay
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.223.3/32
Destination - Origin: a1-smartpay-inside/27, a1-smartpay-dmz/27, Translated: a1-smartpay-inside/27, a1-smartpay-dmz/27
41 (belpak) to (ghu) source dynamic vpn-client-net 192.168.223.4 destination static tpro-cloud-nets tpro-cloud-nets
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.19.0/24, Translated: 192.168.223.4/32
Destination - Origin: tpro-inside/27, Translated: tpro-inside/27
42 (ghu) to (bft) source dynamic stylesoftvpnpool interface destination static paritet-host paritet-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: 172.17.176.0/24, Translated: 10.1.11.30/30
Destination - Origin: 10.9.1.2/32, Translated: 10.9.1.2/32
43 (inside) to (bft) source static 192.168.111.244 interface destination static bft-network bft-network service tcp80 tcp45423
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.244/32, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
Service - Origin: tcp source eq www , Translated: tcp source eq 45423
44 (inside) to (bft) source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
translate_hits = 2, untranslate_hits = 2
Source - Origin: 192.168.111.250/32, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
Service - Origin: tcp source eq 3389 , Translated: tcp source eq 65123
45 (inside) to (bft) source static 192.168.111.16 192.168.20.100 destination static 172.22.147.51 172.22.147.51 service tcp7777 tcp4102 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.16/32, Translated: 192.168.20.100/32
Destination - Origin: 172.22.147.51/32, Translated: 172.22.147.51/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 4102
46 (inside) to (bft) source static 192.168.111.2 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts service ftp21 ftp21 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.2/32, Translated: 192.168.20.100/32
Destination - Origin: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32, Translated: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32
Service - Origin: tcp source eq ftp , Translated: tcp source eq ftp
47 (inside) to (bft) source static 192.168.111.250 192.168.23.100 destination static 192.168.24.100 192.168.24.100 service tcp3389 tcp65123 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.250/32, Translated: 192.168.23.100/32
Destination - Origin: 192.168.24.100/32, Translated: 192.168.24.100/32
Service - Origin: tcp source eq 3389 , Translated: tcp source eq 65123
48 (inside) to (belpak) source static 192.168.111.2 192.168.182.1 destination static DM_INLINE_NETWORK_5 DM_INLINE_NETWORK_5 service tcp80 tcp8097 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.2/32, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.119/32, 172.16.128.68/32, Translated: 172.16.128.119/32, 172.16.128.68/32
Service - Origin: tcp source eq www , Translated: tcp source eq 8097
49 (inside) to (belpak) source static 192.168.111.2 192.168.182.1 destination static DM_INLINE_NETWORK_6 DM_INLINE_NETWORK_6 service tcp7777 tcp9777 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.2/32, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.119/32, 172.16.128.68/32, Translated: 172.16.128.119/32, 172.16.128.68/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 9777
50 (inside) to (belpak) source static 192.168.111.234 82.209.233.253 service tcp80 tcp80
translate_hits = 45, untranslate_hits = 45
Source - Origin: 192.168.111.234/32, Translated: 82.209.233.253/32
Service - Origin: tcp source eq www , Translated: tcp source eq www
51 (inside) to (belpak) source static 192.168.111.234 82.209.233.253 service tcp8008 tcp8008
translate_hits = 2, untranslate_hits = 2
Source - Origin: 192.168.111.234/32, Translated: 82.209.233.253/32
Service - Origin: tcp source eq 8008 , Translated: tcp source eq 8008
52 (inside) to (ghu) source static 192.168.111.250 interface service tcp3389 tcp65123 no-proxy-arp
translate_hits = 3, untranslate_hits = 0
Source - Origin: 192.168.111.250/32, Translated: ghu.bs/27
Service - Origin: tcp source eq 3389 , Translated: tcp source eq 65123
53 (inside) to (belpak) source static 192.168.111.250 interface service tcp3389 tcp65123
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.250/32, Translated: 82.209.233.250/29
Service - Origin: tcp source eq 3389 , Translated: tcp source eq 65123
54 (inside) to (belpak) source static 192.168.111.2 belpack.work.bs service ftp21 ftp21
translate_hits = 122, untranslate_hits = 1901
Source - Origin: 192.168.111.2/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq ftp , Translated: tcp source eq ftp
55 (inside) to (belpak) source static 192.168.111.2 belpack.work.bs service ssh22 ssh22
translate_hits = 1023, untranslate_hits = 1087
Source - Origin: 192.168.111.2/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq ssh , Translated: tcp source eq ssh
56 (inside) to (belpak) source static 192.168.111.115 belpack.stand.bs service tcp6001 tcp6001 inactive description hsm1.boil
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.115/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 6001 , Translated: tcp source eq 6001
57 (inside) to (belpak) source static 192.168.111.16 belpack.stand.bs service tcp7777 tcp7777 description ohs stand
translate_hits = 64, untranslate_hits = 67
Source - Origin: 192.168.111.16/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 7777
58 (inside) to (belpak) source static 192.168.111.43 belpack.work.bs service tcp1521 tcp55443 description ticketpro for test module
translate_hits = 14, untranslate_hits = 15
Source - Origin: 192.168.111.43/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq sqlnet , Translated: tcp source eq 55443
59 (inside) to (belpak) source static 192.168.111.43 belpack.work.bs service tcp80 tcp80
translate_hits = 222, untranslate_hits = 240
Source - Origin: 192.168.111.43/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq www , Translated: tcp source eq www
60 (inside) to (belpak) source static 192.168.111.43 belpack.work.bs service tcp443 tcp443
translate_hits = 4980, untranslate_hits = 8665
Source - Origin: 192.168.111.43/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq https , Translated: tcp source eq https
61 (inside) to (ghu) source static 192.168.111.2 interface service ftp21 ftp21 no-proxy-arp
translate_hits = 65, untranslate_hits = 6
Source - Origin: 192.168.111.2/32, Translated: ghu.bs/27
Service - Origin: tcp source eq ftp , Translated: tcp source eq ftp
62 (inside) to (ghu) source static 192.168.111.23 interface service tcp1521 tcp45421 no-proxy-arp
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.23/32, Translated: ghu.bs/27
Service - Origin: tcp source eq sqlnet , Translated: tcp source eq 45421
63 (inside) to (belpak) source static 192.168.111.100 belpack.stand.bs service tcp1194 tcp27512
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.100/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 1194 , Translated: tcp source eq 27512
64 (inside) to (belpak) source static 192.168.111.102 belpack.stand.bs service tcp1194 tcp27256
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.102/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 1194 , Translated: tcp source eq 27256
65 (inside) to (belpak) source static 172.16.177.220 belpack.work.bs service tcp8080 tcp9988 description parking ords
translate_hits = 22270, untranslate_hits = 42847
Source - Origin: 172.16.177.220/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq 8080 , Translated: tcp source eq 9988
66 (inside) to (belpak) source static 172.16.177.220 belpack.work.bs service tcp1521 tcp44251 description parking sqlnet
translate_hits = 7, untranslate_hits = 7
Source - Origin: 172.16.177.220/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq sqlnet , Translated: tcp source eq 44251
67 (inside) to (belpak) source static 192.168.111.73 belpack.work.bs service tcp7999 tcp7999
translate_hits = 10194, untranslate_hits = 16046
Source - Origin: 192.168.111.73/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq 7999 , Translated: tcp source eq 7999
68 (inside) to (belpak) source static 192.168.111.73 belpack.work.bs service tcp7990 tcp7990
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.73/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq 7990 , Translated: tcp source eq 7990
69 (inside) to (belpak) source static 192.168.111.44 belpack.stand.bs service tcp1194 tcp27128 description ahramovich
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.44/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 1194 , Translated: tcp source eq 27128
70 (inside) to (belpak) source static 172.16.177.221 82.209.233.254 service tcp80 tcp80
translate_hits = 67, untranslate_hits = 74
Source - Origin: 172.16.177.221/32, Translated: 82.209.233.254/32
Service - Origin: tcp source eq www , Translated: tcp source eq www
71 (inside) to (belpak) source static 172.16.177.221 82.209.233.254 service tcp443 tcp443
translate_hits = 26, untranslate_hits = 32
Source - Origin: 172.16.177.221/32, Translated: 82.209.233.254/32
Service - Origin: tcp source eq https , Translated: tcp source eq https
72 (inside) to (belpak) source static 172.16.177.223 belpack.work.bs service tcp8081 tcp8081
translate_hits = 65, untranslate_hits = 73
Source - Origin: 172.16.177.223/32, Translated: 82.209.233.251/32
Service - Origin: tcp source eq 8081 , Translated: tcp source eq 8081
73 (inside) to (belpak) source static 192.168.111.224 belpack.stand.bs service tcp42000 tcp42000
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.224/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 42000 , Translated: tcp source eq 42000
74 (inside) to (belpak) source static 192.168.111.224 belpack.stand.bs service tcp42001 tcp42001
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.224/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 42001 , Translated: tcp source eq 42001
75 (inside) to (belpak) source static 192.168.111.205 belpack.stand.bs service tcp7777 tcp17777 description BSNET-107 for boil
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.205/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 17777
76 (inside) to (belpak) source static 192.168.111.206 belpack.stand.bs service tcp7777 tcp27777 description BSNET-107 for boil
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.206/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 27777
77 (inside) to (belpak) source static 172.16.177.50 belpack.stand.bs service tcp7777 tcp37777 description BSNET-107 for boil
translate_hits = 2, untranslate_hits = 2
Source - Origin: 172.16.177.50/32, Translated: 82.209.233.252/32
Service - Origin: tcp source eq 7777 , Translated: tcp source eq 37777
78 (inside) to (ghu) source dynamic bs-nets-inside 192.168.181.22 destination static boil-stand boil-stand
translate_hits = 1, untranslate_hits = 5
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.181.22/32
Destination - Origin: 10.93.1.24/32, Translated: 10.93.1.24/32
79 (inside) to (belpak) source dynamic bs-nets-inside 192.168.181.22 destination static boil-stand boil-stand
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.181.22/32
Destination - Origin: 10.93.1.24/32, Translated: 10.93.1.24/32
80 (inside) to (belpak) source dynamic bs-nets-inside 172.17.125.100 destination static parimatch-ipsec-host parimatch-ipsec-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 172.17.125.100/32
Destination - Origin: 172.31.255.1/32, Translated: 172.31.255.1/32
81 (inside) to (belpak) source dynamic bs-nets-inside 192.168.21.100 destination static trustbank-ipsec-host trustbank-ipsec-host
translate_hits = 16, untranslate_hits = 17
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.21.100/32
Destination - Origin: 212.98.162.139/32, Translated: 212.98.162.139/32
82 (inside) to (bft) source dynamic bs-nets-inside 192.168.20.100 destination static bgpb-ipsec-hosts bgpb-ipsec-hosts
translate_hits = 49, untranslate_hits = 49
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.20.100/32
Destination - Origin: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32, Translated: 172.22.147.10/32, 172.22.147.50/32, 172.22.147.51/32, 172.22.147.5/32
bgpb-ipsec-net/24, 172.22.147.38/32, 172.22.147.2/32, 172.22.147.45/32
172.22.133.15/32, 192.168.77.15/32
83 (inside) to (bft) source dynamic bs-nets-inside 192.168.21.100 destination static trustbank-ipsec-host trustbank-ipsec-host
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.21.100/32
Destination - Origin: 212.98.162.139/32, Translated: 212.98.162.139/32
84 (inside) to (belpak) source dynamic bs-nets-inside 192.168.129.100 destination static DM_INLINE_NETWORK_10 DM_INLINE_NETWORK_10
translate_hits = 9, untranslate_hits = 9
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.129.100/32
Destination - Origin: vtb-bank-stand/32, 10.7.7.65/32, 10.7.7.66/32, Translated: vtb-bank-stand/32, 10.7.7.65/32, 10.7.7.66/32
85 (inside) to (belpak) source dynamic bs-nets-inside 172.27.143.33 destination static multicarta-ipsec-net multicarta-ipsec-net
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 172.27.143.33/32
Destination - Origin: 172.22.22.0/24, Translated: 172.22.22.0/24
86 (inside) to (bft) source dynamic bs-nets-inside 192.168.142.1 destination static bta-bank-hosts bta-bank-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.142.1/32
Destination - Origin: 192.168.14.11/32, 192.168.14.4/32, 192.168.4.64/32, 192.168.5.224/32, Translated: 192.168.14.11/32, 192.168.14.4/32, 192.168.4.64/32, 192.168.5.224/32
87 (inside) to (belpak) source dynamic dkv-users 192.168.133.1 destination static dkv-network dkv-network
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.102/32, 192.168.111.110/32, 192.168.111.16/32, 192.168.111.23/32
192.168.111.240/32, 192.168.111.250/32, Translated: 192.168.133.1/32
Destination - Origin: 192.168.233.32/27, Translated: 192.168.233.32/27
88 (inside) to (bft) source dynamic bs-nets-inside 192.168.130.100 destination static life-smsc life-smsc
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.130.100/32
Destination - Origin: 81.30.80.42/32, Translated: 81.30.80.42/32
89 (inside) to (bft) source dynamic bs-nets-inside interface destination static bft-network bft-network
translate_hits = 17010, untranslate_hits = 63293
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
90 (inside) to (ghu) source dynamic bs-nets-inside 192.168.111.1 destination static datacenter-dmz-ipsec-net datacenter-dmz-ipsec-net
translate_hits = 87, untranslate_hits = 87
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.111.1/32
Destination - Origin: 192.168.4.0/24, Translated: 192.168.4.0/24
91 (inside) to (belpak) source dynamic bs-nets-inside 192.168.152.1 destination static parking-grodno401 parking-grodno401
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.152.1/32
Destination - Origin: 172.18.152.0/28, Translated: 172.18.152.0/28
92 (inside) to (belpak) source dynamic bs-nets-inside 172.17.221.100 destination static parking-mogilev7601 parking-mogilev7601
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 172.17.221.100/32
Destination - Origin: 192.168.200.0/24, Translated: 192.168.200.0/24
93 (inside) to (belpak) source dynamic bs-nets-inside 192.168.182.1 destination static belapb-ipsec-hosts belapb-ipsec-hosts
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.182.1/32
Destination - Origin: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32, Translated: 172.16.128.117/32, 172.16.128.119/32, 172.16.128.68/32, 172.16.62.20/32
94 (inside) to (belpak) source dynamic bs-nets-inside 192.168.22.1 destination static bps-ipsec-net bps-ipsec-net
translate_hits = 0, untranslate_hits = 0
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.22.1/32
Destination - Origin: 172.30.71.0/24, Translated: 172.30.71.0/24
95 (inside) to (ghu) source dynamic bs-nets-inside 192.168.222.2 destination static a1-ipay-ipsec-nets a1-ipay-ipsec-nets
translate_hits = 20, untranslate_hits = 20
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, Translated: 192.168.222.2/32
Destination - Origin: a1-ipay-border/27, a1-ipay-ipsec-dmz/27, Translated: a1-ipay-border/27, a1-ipay-ipsec-dmz/27
96 (inside) to (ghu) source dynamic allowed-to-a1 192.168.223.3 destination static a1-smartpay a1-smartpay
translate_hits = 0, untranslate_hits = 0
Source - Origin: d.vyrvich/32, George_Wifi/32, 192.168.111.2/32, George_Lan/32
192.168.111.50/32, 172.16.177.106/32, 192.168.111.90/32, 192.168.111.101/32
192.168.111.102/32, 192.168.111.250/32, Translated: 192.168.223.3/32
Destination - Origin: a1-smartpay-inside/27, a1-smartpay-dmz/27, Translated: a1-smartpay-inside/27, a1-smartpay-dmz/27
97 (inside) to (ghu) source dynamic allowed-to-tpro-cloud 192.168.223.4 destination static tpro-cloud-nets tpro-cloud-nets
translate_hits = 0, untranslate_hits = 0
Source - Origin: George_Wifi/32, 192.168.111.250/32, 192.168.111.2/32, George_Lan/32
192.168.111.50/32, 192.168.111.90/32, Translated: 192.168.223.4/32
Destination - Origin: tpro-inside/27, Translated: tpro-inside/27
98 (inside) to (belpak) source dynamic DM_INLINE_NETWORK_7 interface description Dynamic outgoing NAT
translate_hits = 148882, untranslate_hits = 1620
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, 172.16.189.0/24, Translated: 82.209.233.250/29
99 (inside) to (ghu) source dynamic DM_INLINE_NETWORK_8 interface description Dynamic outgoing NAT
translate_hits = 3186, untranslate_hits = 1
Source - Origin: vpn-client-netwotk/24, ipay-network/24, 172.16.154.0/24, inside-network/24
bs-users-network/24, interlink-nework/24, 172.16.189.0/24, Translated: ghu.bs/27And 'show asp drop' after cleaning and test:
bs-asa5506x# show asp drop Frame drop: Flow is denied by configured rule (acl-drop) 9 First TCP packet not SYN (tcp-not-syn) 12 TCP failed 3 way handshake (tcp-3whs-failed) 1 TCP RST/FIN out of order (tcp-rstfin-ooo) 1 Connection to PAT address without pre-existing xlate (nat-no-xlate-to-pat-pool) 24 Last clearing: 19:20:21 AST Mar 5 2020 by yura Flow drop: Last clearing: 19:20:21 AST Mar 5 2020 by yura
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 11:14 AM
why you are confusing your self. let me explain you. In your ASA configuration you mentioned this
43 (inside) to (bft) source static 192.168.111.244 interface destination static bft-network bft-network service tcp80 tcp45423
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.111.244/32, Translated: 10.1.11.30/30
Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8
This mean if your packet coming from inside interface static with ip address 192.168.111.244 (real) change this to interface bft ip address (mapped) which is 10.1.11.30 (this is ASA bft interface address) with destination static bft-network 10.0.0.0/8 (mapped) to 10.0.0.0/8 (real).
!
remember nat work like this nat(iniside,outside) real mapped dest mapped real.
!
now problem is in your packet tracer you alway put your destin network as ip address of firewall. you have to put some other address like 10.1.11.29.
bs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.29 65123 detailed
this above will work.
but this will not work as ASA is not listening on port 65123
bs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.30 65123 detailed
!
to see what port ASA is listening command is
!
show asp table socket
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2020 09:29 PM
@Sheraz.Salim wrote:why you are confusing your self. let me explain you. In your ASA configuration you mentioned this
43 (inside) to (bft) source static 192.168.111.244 interface destination static bft-network bft-network service tcp80 tcp45423 translate_hits = 0, untranslate_hits = 0 Source - Origin: 192.168.111.244/32, Translated: 10.1.11.30/30 Destination - Origin: 10.0.0.0/8, Translated: 10.0.0.0/8This mean if your packet coming from inside interface static with ip address 192.168.111.244 (real) change this to interface bft ip address (mapped) which is 10.1.11.30 (this is ASA bft interface address) with destination static bft-network 10.0.0.0/8 (mapped) to 10.0.0.0/8 (real).
!
remember nat work like this nat(iniside,outside) real mapped dest mapped real.
!
now problem is in your packet tracer you alway put your destin network as ip address of firewall. you have to put some other address like 10.1.11.29.
bs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.29 65123 detailedthis above will work.
but this will not work as ASA is not listening on port 65123
bs-asa5506x# packet-tracer input inside tcp 192.168.111.250 3389 10.1.11.30 65123 detailed
!
to see what port ASA is listening command is
!
show asp table socket
Hm, I created this NAT entry through ASDM without 'Disable proxy ARP on egress interface' option, but tried with as well without luck.
I don't understand how PAT should look like =| The same entries toward my outside interfaces work well..
Currently only rule #47 works as expected (192.168.23.100 is cryptotrafix to my test S2S IPSec), but the same rule #45 for example toward IPSec to my partner doesn't work (encrypted traffic comes, but doesn't return into IPSec).
So, I have two problems with my ASA related to interface 'bft':
1. I can't make ASA listen PAT on interface bft (rules #43 and #44)
2. Not all PAT enties through 'bft' inerface to my IPSec work as expected (#47 works, but #45 and #46 don't).
'show asp table socket' interesting command. Thank you very much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-06-2020 02:14 AM - edited 03-06-2020 03:41 AM
I'd like to add something.
I have one more ASA5506-X (ver. 9.8(2)20) connected to this network (10.0.0.0) and I have the same issue there (can't PAT to 'bft' interface any service), but
there are two additional IP addresses (10.52.31.190 and 10.52.31.194) routed to 'bft' interface from bft-network ISP, and I can PAT to this IP addresses any port easily, though I don't see these PAT entries in 'show asp table socket'
I don't understand what I'm doing wrong? =(( I had no such issues on my previous Cisco devices (ASA5510, 5505, PIX515E and router 891).
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide