- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cisco FTDv on ESXI8
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco FTDv on ESXI8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 01:39 AM
Hello!
I instlled FTDv (7.3.1-19) on ESXI 8.
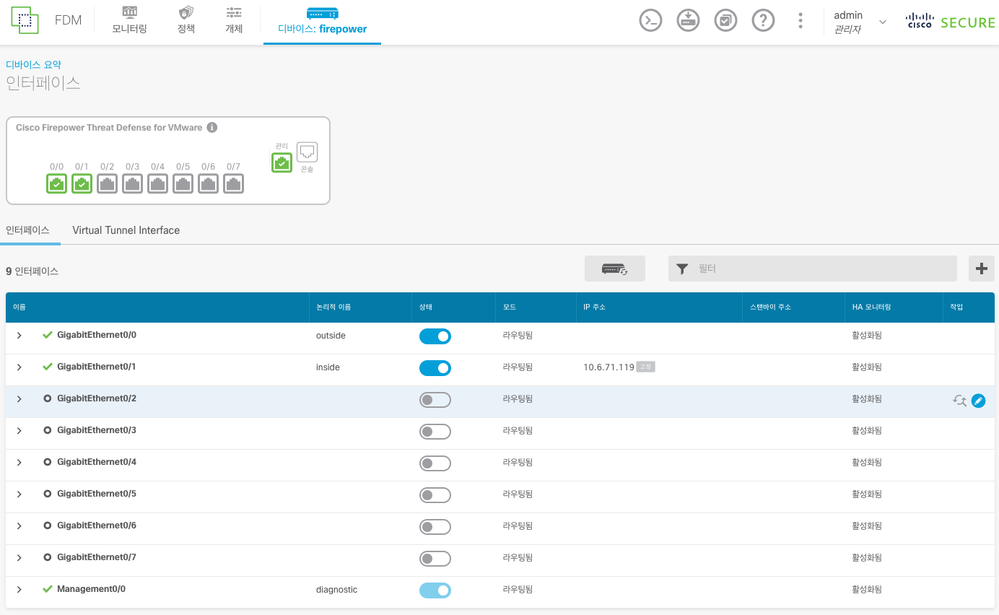
All interfaces down, instead Managemet. On ESXI it configured as VMXNET3.
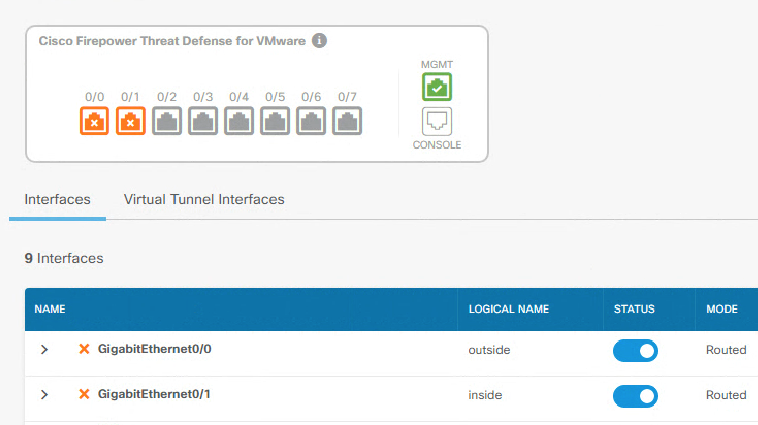
On ESXI side its attach and connected, but on FTDv side its in DOWN status!
> show interface ip brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 192.168.10.114 YES CONFIG down down
GigabitEthernet0/1 unassigned YES DHCP down down
GigabitEthernet0/2 unassigned YES unset administratively down down
GigabitEthernet0/3 unassigned YES unset administratively down down
GigabitEthernet0/4 unassigned YES unset administratively down down
GigabitEthernet0/5 unassigned YES unset administratively down down
GigabitEthernet0/6 unassigned YES unset administratively down down
GigabitEthernet0/7 unassigned YES unset administratively down down
Internal-Control0/0 127.0.1.1 YES unset up up
Internal-Control0/1 unassigned YES unset up up
Internal-Data0/0 unassigned YES unset down down
Internal-Data0/0 unassigned YES unset up up
Internal-Data0/1 169.254.1.1 YES unset up up
Internal-Data0/2 unassigned YES unset up up
Management0/0 unassigned YES unset down down
Does anybody solve this promlem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 02:15 AM
@Alexey Leshko I assume you deployed the policy to the FTD once you enabled the data interfaces?
The release notes for FTD 7.3 only states that VMware vSphere/VMware ESXi 6.5, 6.7, or 7.0 is supported. I would imagine ESX 8.0 is not currently supported, perhaps log a call with TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 02:29 AM
Hi! Thank you for reply!
I known about what ESXI8 is unsupported and search for solution this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 06:31 AM
As @Rob Ingram noted, ESXi 8 is not currently supported (even with the upcoming FTD 7.4). Not only is it not supported (= not tested and verified), but it also does not work - same symptoms as you observed.
I have verified with TAC and raised an enhancement (ENH) bug for this feature. CSCwe44306 applies (not currently publicly viewable).
I was able to get it to work in my lab by building a nested ESXi 7 hypervisor on my ESXi 8 server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 07:08 AM
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2023 03:42 AM
Thanks for Clarification - Just installed ESXi 8 and I was hit by this. Guess stick to ESXi 7 for now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2023 12:56 PM
There is workaround:
After you deploy the OVA, remove all 10 network interfaces from the VM configuration and recreate them as 10 x E1000 interfaces. This will make the interfaces work on ESXI 8. The problem seems to be related to the vmxnet3 drivers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2023 06:56 AM
@OliverFueckert46911 thanks for the tip! I confirmed that worked for me in my lab.
I just had to make sure I accounted for the different mapping of FTDv interfaces when using E1000 vs. vmxnet3 type.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2023 05:33 AM - edited 12-11-2023 05:34 AM
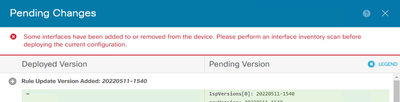
After recreating new interfaces with E1000, I believe you might have faced this error during deployment. How did you resolved?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2023 12:41 PM
You can re-read the interfaces from the devices page. I don't have an instance running right now, so can't show you a screenshot.
best regards,
Oliver.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2024 09:25 PM
It shouldn't be outside of the vendor's coverage, but it works well in my environment. Working normally on vSphere 8.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2024 05:02 AM
I just wanted to add a data point on this topic. I had an FTDv/FMCv that was on 7.2.4 with ESXi 8 U2. Like everyone else the ports were in a down state. I tried deleting all 10 NICs and recreating them as E1000 NICs but that placed all the NICs including the management port into a downstate. After reverting to the latest snapshot and rebooting the FTDv I gained control of the device again. Just for kicks, I updated the FMC and FTD to 7.4.1 and the NICs came back in an upstate with the vmxnet3 type.
I am not saying this is the magic bullet, but the latest release worked for me.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide