- Cisco Community
- Technology and Support
- Security
- Network Security
- CISCO ISE using default deny policy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 07:21 AM
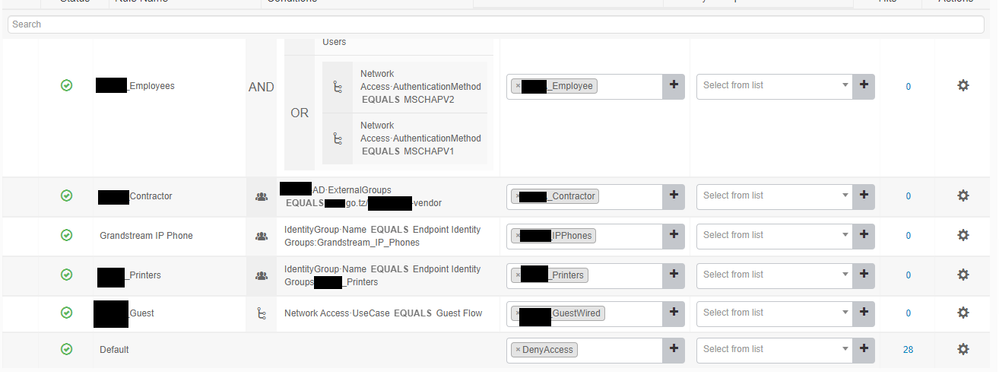
Hello Please help me, my ise policies keep hitting the default deny authorization policy, it was working fine before now i do not know what went wrong.
Please see attached screenshots of my policies and my access lists on the switch,
Extended IP access list ACL-ALLOW
10 permit ip any any
Extended IP access list ACL-WEB-REDIRECT
10 deny udp any eq bootpc any eq bootps
20 deny udp any any eq domain
30 deny ip any host 10.200.222.82
40 permit tcp any any eq www (18584 matches)
50 permit tcp any any eq 443 (13758 matches)
60 deny ip any any
Extended IP access list Auth-Default-ACL-OPEN
10 permit ip any any
Extended IP access list CISCO-CWA-URL-REDIRECT-ACL
100 deny udp any any eq domain
101 deny tcp any any eq domain
102 deny udp any eq bootps any
103 deny udp any any eq bootpc
104 deny udp any eq bootpc any
105 permit tcp any any eq www
Extended IP access list REDIRECT
10 deny udp any eq bootpc any eq bootps
20 deny udp any any eq domain
30 deny ip any host 10.200.222.82
40 permit ip any any
Extended IP access list preauth_ipv4_acl (per-user)
10 permit udp any any eq domain
20 permit tcp any any eq domain
30 permit udp any eq bootps any
40 permit udp any any eq bootpc
50 permit udp any eq bootpc any
60 deny ip any any
IPv6 access list preauth_ipv6_acl (per-user)
permit udp any any eq domain sequence 10
permit tcp any any eq domain sequence 20
permit icmp any any nd-ns sequence 30
permit icmp any any nd-na sequence 40
permit icmp any any router-solicitation sequence 50
permit icmp any any router-advertisement sequence 60
permit icmp any any redirect sequence 70
permit udp any eq 547 any eq 546 sequence 80
permit udp any eq 546 any eq 547 sequence 90
deny ipv6 any any sequence 100
Solved! Go to Solution.
- Labels:
-
Other Network Security Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:47 AM
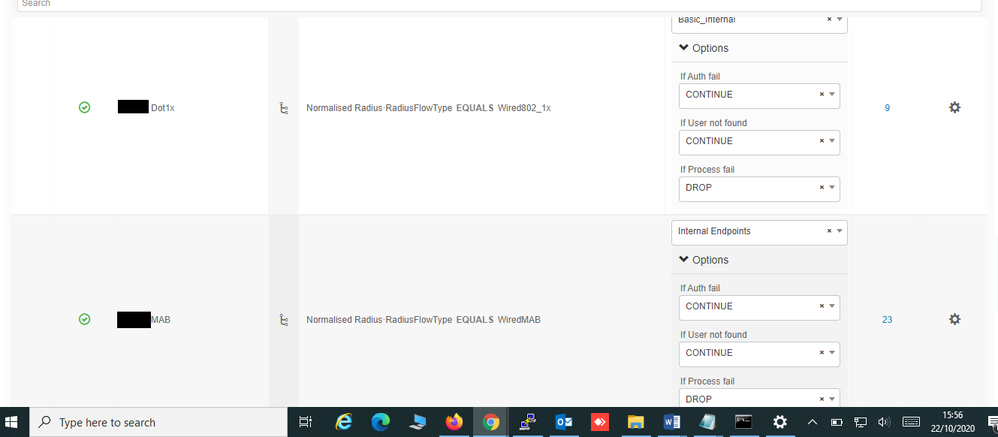
and hit on detials to see the flow for evaluating policies. Basically you
are matching your conditions hence hitting default deny. We can suggest on
this as it depends on your end point and you conditions.
Just follow these steps and you might find what is missing.
**** please remember to rate useful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2020 10:47 AM
and hit on detials to see the flow for evaluating policies. Basically you
are matching your conditions hence hitting default deny. We can suggest on
this as it depends on your end point and you conditions.
Just follow these steps and you might find what is missing.
**** please remember to rate useful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide