- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Community Ask Me Anything - Secure Remote Workers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Community Ask Me Anything - Secure Remote Workers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2020
10:10 PM
- last edited on
03-24-2020
10:06 AM
by
Monica Lluis
![]()
You can ask your question on your own language:
| Español | Português | Français | Русский | 日本語 | 简体中文 |
Here’s your chance to discuss Cisco Secure Remote Working technologies such as AnyConnect, ASA, FTD, Duo, and Umbrella. In this session, the experts will answer questions about emergency licenses, design, configuration, and troubleshooting. Our experts span more than 12 time zones. Also, we’ll be translating the session into multiple languages to provide you with the best experience possible.
This forum event works well as an introduction for those who are not familiar with these security solutions and/or have recently started using them.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Friday, March 20 to Friday, April 3, 2020

 Jonny Noble leads the Technical Marketing team for Cloud Security at Cisco, with expertise in Cisco Umbrella and surrounding technologies. For more than 20 years, Jonny has obtained experience in customer-facing disciplines for global hi-tech organizations. He also has rich experience in presenting breakout sessions and proctoring labs at Cisco Live events along with representing Cisco at numerous customer and partner events, trade shows, and exhibitions. Jonny holds degrees in Electronics, Sociology, a Business MBA, and is CISSP certified.
Jonny Noble leads the Technical Marketing team for Cloud Security at Cisco, with expertise in Cisco Umbrella and surrounding technologies. For more than 20 years, Jonny has obtained experience in customer-facing disciplines for global hi-tech organizations. He also has rich experience in presenting breakout sessions and proctoring labs at Cisco Live events along with representing Cisco at numerous customer and partner events, trade shows, and exhibitions. Jonny holds degrees in Electronics, Sociology, a Business MBA, and is CISSP certified.
 Aditya Ganjoo is a Technical Marketing Engineer in Bangalore, India. He has been working with Cisco for the past seven years in Security domains such as Firewall, VPN and AAA. Aditya has delivered trainings on ASA and VPN technologies. He holds a Bachelor's degree in Information Technology. Additionally, he is a CCIE in Security (CCIE#58938). He has been a consistent contributor on Cisco Support Community and has delivered multiple sessions at Cisco Live.
Aditya Ganjoo is a Technical Marketing Engineer in Bangalore, India. He has been working with Cisco for the past seven years in Security domains such as Firewall, VPN and AAA. Aditya has delivered trainings on ASA and VPN technologies. He holds a Bachelor's degree in Information Technology. Additionally, he is a CCIE in Security (CCIE#58938). He has been a consistent contributor on Cisco Support Community and has delivered multiple sessions at Cisco Live.
By posting a question on this event you're giving permission to be translated in all languages we have in the community.
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 04:18 AM
Hi,
Can you share the output of show run group-policy <policy-name>?
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2020 09:37 PM
Hi,
Here is my sh run group policy
1)
group-policy it-test internal
group-policy it-test attributes
dns-server value 192.168.1.100
vpn-idle-timeout 20
vpn-tunnel-protocol ikev1 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value it-test-acl
default-domain value test.local
address-pools value it-test-pool
2 )group-policy it-test2 internal
group-policy it-test2 attributes
wins-server none
dns-server value 192.168.1.100
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value it-test2-acl
default-domain value test.local
split-dns value test.local test.com
split-tunnel-all-dns disable
address-pools value it-test2-Pool
Tried the below also after removing "split-tunnel-all-dns disable" but did not help .
3 )group-policy it-test2 internal
group-policy it-test2 attributes
wins-server none
dns-server value 192.168.1.100
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value it-test2-acl
default-domain value test.local
split-dns value test.local test.comsplit-tunnel-all-dns disable
address-pools value it-test2-Pool
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 12:11 AM
Please disable/remove the tunnel-all split dns config and keep the split-dns values, also ensure that the DNS servers (IP) is a part of the split tunnel ACL.
To confirm the DNS lookups (if they are going through Anyconnect) you can use Wireshark, start a capture on the machine and check on which adapter the DNS requests go out to.
Please share the output of ipconfig /all from the test machine and the captures if possible.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 02:32 AM
Please disable/remove the tunnel-all split dns config and keep the split-dns values, also ensure that the DNS servers (IP) is a part of the split tunnel ACL.
disabled and full subnet is (192.168.1.0/24 ) is part of split tunnel acl
To confirm the DNS lookups (if they are going through Anyconnect) you can use Wireshark, start a capture on the machine and check on which adapter the DNS requests go out to.
yes it is going through any connect
Please share the output of ipconfig /all from the test machine and the captures if possible.
attached
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 04:22 AM
Standard query response, Server failure
You told that it works fine when you are not on Anyconnect.
If possible please share captures for the working one.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 06:14 AM
Thanks for the reply .
What I mean by it is working when I am on anyconnect , If I remove "split-dns value test.com " it is going to public dns ( ISP) through physical adapter and public ip address .
and the internal dns server working from our local lan ( I can share the packet capture soon )
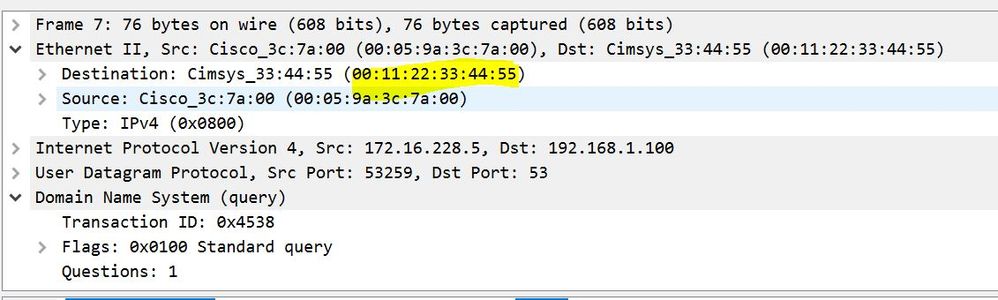
And can you tell me why the anyconnect mac address is shown as 00:11:22:33:44:55
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 07:13 AM
MAC address for AC is 0-05-9A-3C-7A-00.
"AnyConnect driver does not interfere with the native DNS resolver. Therefore, DNS resolution is performed based on the order of network adapters where AnyConnect is always the preferred adapter when VPN is connected. Moreover, a DNS query is first sent via the tunnel and if it does not get resolved, the resolver attempts to resolve it via public interface. The split-include access-list includes the subnet which covers the Tunnel DNS server(s). To start with AnyConnect 4.2, host routes for the Tunnel DNS server(s) are automatically added as split-include networks (secure routes) by the AnyConnect client, and therefore the split-include access-list no longer requires explicit addition of the tunnel DNS server subnet."
I think this is happening in your case.
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 07:34 AM
Thanks for the reply ,
I have removed the subnet from acl , but it is giving the same issue .
From the wireshark capture analysis , the dns query is responding with an error ?
When you say "The MAC address is for the Destination IP, your next hop."
It could be the ASA firewall interface ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2020 08:12 AM
Regards,
Aditya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 05:08 AM
Hello all, I have several questions:
1. Am I correct in understanding that webvpn customization (i.e. the webvpn home page) and AnyConnect customization (messages, languages etc.) are not currently supported when using Firepower Threat Defense (FTD) device as the headend? (either FMC-managed or FDM/CDO-managed)
2. Basic posture checking like we are able to do with ASA and DAP/Hostscan is not currently an option with FTD alone (i.e. we must refer to an external solution like ISE) - correct?
3. For DAP/Hostscan with ASA, does it require AnyConnect Premium and is it supported on ASAv platform models?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 05:44 AM
Hi Marvin,
- That is correct. Clientless WebVPN and AnyConnect customization are not supported today on FTD.
- You will need to use ISE Posture for client posture assessment today on FTD.
- ASA with DAP requires the Apex license (previously the Premium license) and is supported on ASAv models.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 06:04 AM
Thanks Divya,
One followup - a couple of us have tried getting DAP going on ASAv and ran into problems. Please see this thread:
https://community.cisco.com/t5/vpn/asa-virtual-unable-to-activate-hostscan/td-p/4044100
Is that something you can answer here or should we open a TAC case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 06:20 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 06:22 AM
Updated on the post you mentioned too.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 07:19 AM - edited 03-24-2020 10:09 AM
Thanks @Divya Nair and @Aditya Ganjoo !
To fill in readers here, bumping the memory to run the ASAv as an ASAv10 (vs. ASAv5) model fixes the inability to add in hostscan which is necessary to use DAP.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide