- Cisco Community
- Technology and Support
- Security
- Network Security
- The way this is most commonly
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Dual ASA Dual ISP failover configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2014 07:54 AM - edited 03-11-2019 09:10 PM
Hello,
I inherited a network with two Cisco ASA 5540's, one connected to the primary ISP and the other connected to the backup ISP. Each ASA has a connection to three switches on the three remaining interfaces. See the diagram below for more details.
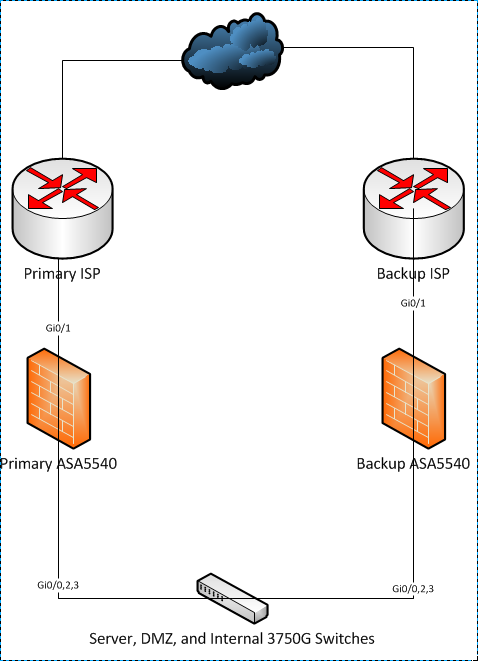
As I found out yesterday when our primary circuit went down, the manual failover procedure that the previous admin implemented does not work. I believe he set it up using OSPF, but I am not that familiar with it and I was not able to get it to work properly. I am looking to resolve this and implement failover in a simpler matter, but I'm not quite a network expert and I don't know where to start. Do I want Active/Active, Active/Standby, or is there another method to set this up?
Our ISPs don't support BGP, which is fine IMO. In the event of a failover, I don't mind having to change DNS records for in-bound stuff. I just want a way to be able to easily failover to the backup ISP. Anyone have any suggestions of where to start with this? Thanks
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2014 08:21 AM
Can you describe the way the manual failover should work?
Is there any failover currently configured between the firewalls?
Is the OSPF on the firewalls?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2014 10:40 AM
The manual procedure works by shutting down the outside interface on the production firewall. There is then a route set to point to the secondary firewall (10.255.255.27)
Perimeter# sh route | inc 0.0.0.0
Gateway of last resort is 10.255.255.27 to network 0.0.0.0
O*E2 0.0.0.0 0.0.0.0 [110/20] via 10.255.255.27, 0:00:27, internal
I see OSPF on the firewalls:
Primary
router ospf 1
router-id 10.1.0.1
network 10.255.255.8 255.255.255.248 area 1
network 10.255.255.16 255.255.255.248 area 3
network 10.255.255.24 255.255.255.248 area 0
log-adj-changes
redistribute connected subnets
default-information originate
Secondary
router ospf 1
router-id 10.1.0.94
network 10.255.255.8 255.255.255.248 area 1
network 10.255.255.16 255.255.255.248 area 3
network 10.255.255.24 255.255.255.248 area 0
network 10.255.255.92 255.255.255.252 area 2
log-adj-changes
redistribute connected subnets
default-information originate metric 20
and on my switches:
Server switch
router ospf 1
router-id 10.1.0.53
log-adjacency-changes
redistribute connected subnets
network 10.255.255.8 0.0.0.3 area 1
network 10.255.255.40 0.0.0.3 area 1
internal switch
router ospf 1
router-id 10.1.0.17
log-adjacency-changes
redistribute static subnets
network 10.255.255.24 0.0.0.7 area 0
I'm just not really sure what any of this means...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2014 11:45 AM
i don't know that the ospf configs mean anything for failover, but the idea of ospf is that if you lose a router (or firewall if it is running ospf), you have a good route to any needed destination using the remaining routers.
Failover is designed to make sure you have a good path outside in case you lose a firewall.
If your firewalls are configured such that each traffic moving interface across both firewalls is on the same subnet, you can use active-standby failover. In my experience, this requires a router to be placed between your firewalls and the ISP router, which would allow your outside interfaces to be placed on the same subnet.
I haven't had a chance to run active-active, but the idea there is more load balancing.
The link below will help with setting up failover.
The link below will help explain how OSPF works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2014 08:29 AM
The way this is most commonly done is by having the two ASAs (assuming single context) in an Active-Standby HA pair. Each ASA has two outside interfaces (they could be subinterfaces on a trunk if your physical interfaces are otherwise spoken for). One of the outside interfaces goes to ISP A and one to ISP B. It is usually best to make those connections via a switch as most ISPs only give you a single physical interface.
You then set a static default route (with tracking option) to ISP A. You set a second static default route (with a higher admin distance) to ISP B. You use them in conjunction with an IP sla operation that tests reachability of some upstream resource (a remote site, public DNS etc.). If the isp sla fails, the tracking option in the first default route causes it to be removed and the ASAs start sending all outbound traffic via the second ISP.
Cisco has an old (but still relevant) configuration guide showing this in detail. Link
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


