- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Firepower with AnyConnect's cannot access share drives
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 01:12 PM
I am new to Firepower devices trying to deploy a new Firepower 1140 ONLY USING FDM, NO FMC...
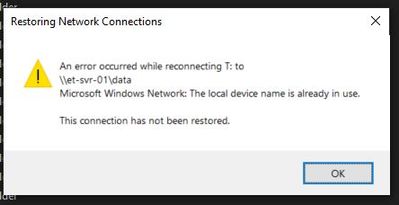
I have VPN AnyConnect set up with our internal server verifying users. User verification works, you get access to internal network from the outside on VPN. Once in I cannot get to any Share Drives I get: (error occurred while reconnecting, The local device name is already in use) See pic bellow.
Second issue is cannot ping any inside network device including the Server that verified the user logging in.
Last is internet connection is slow when using the VPN
Any advice is appreciated and I am willing to share config information to get this resolved. Again NOT USING FMC..
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 03:01 PM
@00u18jg7x27DHjRMh5d7 this command is correct. Check out the line starting Phase 7, it confirms the nat rule matched. Which is your problem, it is translating the traffic behind the ftd interface.
As i said above create the nat exemption rule above the dynamic rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 01:24 PM
@00u18jg7x27DHjRMh5d7 do you have a nat exemption rule to ensure the traffic is not unintentionally translated?
Do you have the internal dns servers configured so the vpn users can resolve the internal names?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 01:34 PM
I do its on the same server that verifies credentials, I also added it as DNS server in the VPN configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 01:37 PM - edited 01-06-2022 01:40 PM
@00u18jg7x27DHjRMh5d7 what about nat exemption rules though?
From the cli run "show nat detail" and provide the output
Run packet-tracer from the CLI to simulate the RAVPN traffic and provide the output.
I assume you've also created the relevant rules in the Access Control Policy, permitting the traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 01:55 PM
See Bellow for output, let me know if I need to run another command
Thank You,
WH01-FP-1# sho nat detail
Manual NAT Policies Implicit (Section 0)
1 (nlp_int_tap) to (inside) source static nlp_server__http_0.0.0.0_intf17 interface destination static 0_0.0.0.0_21 0_0.0.0.0_21 service tcp https https
translate_hits = 1211, untranslate_hits = 1431
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
Destination - Origin: 0.0.0.0/0, Translated: 0.0.0.0/0
Service - Protocol: tcp Real: https Mapped: https
2 (nlp_int_tap) to (inside) source static nlp_server__ssh_0.0.0.0_intf17 interface destination static 0_0.0.0.0_20 0_0.0.0.0_20 service tcp ssh ssh
translate_hits = 2, untranslate_hits = 2
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
Destination - Origin: 0.0.0.0/0, Translated: 0.0.0.0/0
Service - Protocol: tcp Real: ssh Mapped: ssh
3 (nlp_int_tap) to (inside) source static nlp_server__ssh_::_intf17 interface ipv6 destination static 0_::_19 0_::_19 service tcp ssh ssh
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
Destination - Origin: ::/0, Translated: ::/0
Service - Protocol: tcp Real: ssh Mapped: ssh
4 (nlp_int_tap) to (inside) source dynamic nlp_client_0_0.0.0.0_6proto22_intf17 interface destination static nlp_client_0_ipv4_28 nlp_client_0_ipv4_28 service nlp_client_0_6svc22_27 nlp_client_0_6svc22_27
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
Destination - Origin: 0.0.0.0/0, Translated: 0.0.0.0/0
Service - Origin: tcp destination eq ssh , Translated: tcp destination eq ssh
5 (nlp_int_tap) to (inside) source dynamic nlp_client_0_ipv6_::_6proto22_intf17 interface ipv6 destination static nlp_client_0_ipv6_26 nlp_client_0_ipv6_26 service nlp_client_0_6svc22_25 nlp_client_0_6svc22_25
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
Destination - Origin: ::/0, Translated: ::/0
Service - Origin: tcp destination eq ssh , Translated: tcp destination eq ssh
Manual NAT Policies (Section 1)
1 (inside) to (outside) source dynamic any-ipv4 interface
translate_hits = 1, untranslate_hits = 0
Source - Origin: 0.0.0.0/0, Translated: x.x.174.155/29
2 (any) to (outside) source dynamic any-ipv4 interface
translate_hits = 73, untranslate_hits = 2
Source - Origin: 0.0.0.0/0, Translated: x.x.174.155/29
3 (outside) to (inside) source static VPN_Network Inside_Network destination static IPv4-Private-192.168.0.0-16 Inside_Network no-proxy-arp
translate_hits = 1232, untranslate_hits = 0
Source - Origin: 192.168.101.0/24, Translated: 192.168.1.0/24
Destination - Origin: 192.168.0.0/16, Translated: 192.168.1.0/24
Auto NAT Policies (Section 2)
1 (nlp_int_tap) to (outside) source dynamic nlp_client_0_intf10 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: x.x.174.155/29
2 (nlp_int_tap) to (vlan50) source dynamic nlp_client_0_intf11 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.50.5/24
3 (nlp_int_tap) to (vlan70) source dynamic nlp_client_0_intf12 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.70.5/24
4 (nlp_int_tap) to (vlan80) source dynamic nlp_client_0_intf13 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.80.5/24
5 (nlp_int_tap) to (vlan90) source dynamic nlp_client_0_intf14 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.90.5/24
6 (nlp_int_tap) to (valn100) source dynamic nlp_client_0_intf15 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.100.5/24
7 (nlp_int_tap) to (vlan120) source dynamic nlp_client_0_intf16 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.120.5/24
8 (nlp_int_tap) to (inside) source dynamic nlp_client_0_intf17 interface
translate_hits = 4995, untranslate_hits = 453
Source - Origin: 169.254.1.3/32, Translated: 192.168.1.1/24
9 (nlp_int_tap) to (diagnostic) source dynamic nlp_client_0_intf2 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 0.0.0.0/32
10 (nlp_int_tap) to (vlan10) source dynamic nlp_client_0_intf3 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.10.5/24
11 (nlp_int_tap) to (vlan150) source dynamic nlp_client_0_intf4 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.150.5/24
12 (nlp_int_tap) to (vlan30) source dynamic nlp_client_0_intf5 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.30.5/24
13 (nlp_int_tap) to (outside_frontier) source dynamic nlp_client_0_intf6 interface
translate_hits = 210, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: x.x.x.125/24
14 (nlp_int_tap) to (vlan20) source dynamic nlp_client_0_intf7 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.20.5/24
15 (nlp_int_tap) to (vlan40) source dynamic nlp_client_0_intf8 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.40.5/24
16 (nlp_int_tap) to (vlan60) source dynamic nlp_client_0_intf9 interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 169.254.1.3/32, Translated: 192.168.60.5/24
17 (outside) to (inside) source dynamic AIX interface
translate_hits = 0, untranslate_hits = 0
Source - Origin: 192.168.1.228/32, Translated: 192.168.1.1/24
18 (outside) to (inside) source dynamic ET-SVR interface
translate_hits = 1, untranslate_hits = 0
Source - Origin: 192.168.1.248/32, Translated: 192.168.1.1/24
19 (nlp_int_tap) to (outside) source dynamic nlp_client_0_ipv6_intf10 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
20 (nlp_int_tap) to (vlan50) source dynamic nlp_client_0_ipv6_intf11 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
21 (nlp_int_tap) to (vlan70) source dynamic nlp_client_0_ipv6_intf12 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
22 (nlp_int_tap) to (vlan80) source dynamic nlp_client_0_ipv6_intf13 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
23 (nlp_int_tap) to (vlan90) source dynamic nlp_client_0_ipv6_intf14 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
24 (nlp_int_tap) to (valn100) source dynamic nlp_client_0_ipv6_intf15 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
25 (nlp_int_tap) to (vlan120) source dynamic nlp_client_0_ipv6_intf16 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
26 (nlp_int_tap) to (inside) source dynamic nlp_client_0_ipv6_intf17 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
27 (nlp_int_tap) to (diagnostic) source dynamic nlp_client_0_ipv6_intf2 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
28 (nlp_int_tap) to (vlan10) source dynamic nlp_client_0_ipv6_intf3 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
29 (nlp_int_tap) to (vlan150) source dynamic nlp_client_0_ipv6_intf4 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
30 (nlp_int_tap) to (vlan30) source dynamic nlp_client_0_ipv6_intf5 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
31 (nlp_int_tap) to (outside_frontier) source dynamic nlp_client_0_ipv6_intf6 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
32 (nlp_int_tap) to (vlan20) source dynamic nlp_client_0_ipv6_intf7 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
33 (nlp_int_tap) to (vlan40) source dynamic nlp_client_0_ipv6_intf8 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
34 (nlp_int_tap) to (vlan60) source dynamic nlp_client_0_ipv6_intf9 interface ipv6
translate_hits = 0, untranslate_hits = 0
Source - Origin: fd00:0:0:1::3/128, Translated:
WH01-FP-1# packet-tracer input inside tcp 192.168.1.238 3000 8.8.8.8 80
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.1.22 using egress ifc inside(vrfid:0)
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group NGFW_ONBOX_ACL global
access-list NGFW_ONBOX_ACL advanced permit object-group |acSvcg-268435462 ifc inside object any-ipv4 ifc inside object any-ipv4 rule-id 268435462
access-list NGFW_ONBOX_ACL remark rule-id 268435462: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 268435462: L5 RULE: Inside_2_Inside
object-group service |acSvcg-268435462
service-object ip
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 865913, packet dispatched to next module
Phase: 8
Type: EXTERNAL-INSPECT
Subtype:
Result: ALLOW
Config:
Additional Information:
Application: 'SNORT Inspect'
Phase: 9
Type: SNORT
Subtype:
Result: ALLOW
Config:
Additional Information:
Snort Trace:
00:00:00:00:00:00 -> E0:69:BA:02:BF:25 0800
192.168.1.238:3000 -> 8.8.8.8:80 proto 6 AS=0 ID=5 GR=1-1
Packet 1525582: TCP ******S*, 01/06-21:45:16.476583, seq 1091216897, dsize 0
Session: new snort session
AppID: service: (0), client: (0), payload: (0), misc: (0)
Firewall: trust/fastpath rule, id 268435462, allow
Policies: Network 0, Inspection 0, Detection 2
Verdict: pass
Snort Verdict: (pass-packet) allow this packet
Phase: 10
Type: INPUT-ROUTE-LOOKUP-FROM-OUTPUT-ROUTE-LOOKUP
Subtype: Resolve Preferred Egress interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.1.22 using egress ifc inside(vrfid:0)
Phase: 11
Type: ADJACENCY-LOOKUP
Subtype: Resolve Nexthop IP address to MAC
Result: ALLOW
Config:
Additional Information:
Found adjacency entry for Next-hop 192.168.1.22 on interface inside
Adjacency :Active
MAC address e069.ba78.e847 hits 8706 reference 3
Result:
input-interface: inside(vrfid:0)
input-status: up
input-line-status: up
output-interface: inside(vrfid:0)
output-status: up
output-line-status: up
Action: allow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 02:14 PM - edited 01-06-2022 02:15 PM
@00u18jg7x27DHjRMh5d7 you need to sort out your nat rules out. Traffic from outside vpn networks to the inside networks should not be translated. This rule has to be above the dynamic nat rule from inside to outside.
That packet tracer output does not simulate the ravpn traffic and does not confirm what nat or acp rules were matched.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 02:29 PM
So I need to have Inside to Outside NAT rule for the VPN?
I added another trace at the bottom if it helps, not sure if its the correct direction of travel.
Thank You,
WH01-FP-1# packet-tracer input outside icmp 192.168.1.238 8 0 8.8.8.8 detailed
Phase: 1
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.1.22 using egress ifc inside(vrfid:0)
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group NGFW_ONBOX_ACL global
access-list NGFW_ONBOX_ACL advanced permit ip any any rule-id 1 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 1: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 1: L7 RULE: DefaultActionRule
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Forward Flow based lookup yields rule:
in id=0x145fb19cad50, priority=12, domain=permit, deny=false
hits=502, user_data=0x145f9d7ec900, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145faf907b30, priority=0, domain=nat-per-session, deny=true
hits=752629, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fba7ca110, priority=0, domain=inspect-ip-options, deny=true
hits=22320, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 5
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
class-map inspection_default
match default-inspection-traffic
policy-map global_policy
class inspection_default
inspect icmp
service-policy global_policy global
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fb1875a40, priority=70, domain=inspect-icmp, deny=false
hits=308, user_data=0x145fb9ee9010, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 6
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fb187cdc0, priority=70, domain=inspect-icmp-error, deny=false
hits=308, user_data=0x145fb9ee9b70, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip/id=0.0.0.0, mask=0.0.0.0, icmp-type=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, icmp-code=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 7
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fbe17e0d0, priority=13, domain=ipsec-tunnel-flow, deny=true
hits=22056, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 8
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
nat (inside,outside) source dynamic any-ipv4 interface
Additional Information:
Forward Flow based lookup yields rule:
out id=0x145fb9d151e0, priority=6, domain=nat-reverse, deny=false
hits=20790, user_data=0x145fb9d113e0, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=inside(vrfid:0)
Result:
input-interface: outside(vrfid:0)
input-status: up
input-line-status: up
output-interface: inside(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000056444aa88854 flow (NA)/NA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 02:34 PM
@00u18jg7x27DHjRMh5d7 from inside to outside between the inside networks and the vpn network, which is on the outside.
That packet tracer still does not simulate ravpn traffic, you'd want the destination to be your server on the inside.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 02:55 PM
See bellow If this is not the correct command please give me the correct one to show RAVPN Traffic
WH01-FP-1# packet-tracer input outside tcp 192.168.1.238 80 192.168.101.1 4443$
WARNING: Bypass-checks and decrypted options are conflicting
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fbd1b7e40, priority=1, domain=permit, deny=false
hits=186, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=outside, output_ifc=any
Phase: 2
Type: INPUT-ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
Found next-hop 192.168.1.22 using egress ifc inside(vrfid:0)
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group NGFW_ONBOX_ACL global
access-list NGFW_ONBOX_ACL advanced permit ip any any rule-id 1 event-log both
access-list NGFW_ONBOX_ACL remark rule-id 1: ACCESS POLICY: NGFW_Access_Policy
access-list NGFW_ONBOX_ACL remark rule-id 1: L7 RULE: DefaultActionRule
Additional Information:
This packet will be sent to snort for additional processing where a verdict will be reached
Forward Flow based lookup yields rule:
in id=0x145fbce82970, priority=12, domain=permit, deny=false
hits=15, user_data=0x145f9d7ed080, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, ifc=any, vlan=0, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 4
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145faf904430, priority=0, domain=nat-per-session, deny=false
hits=565456, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=any, output_ifc=any
Phase: 5
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fb2a74ce0, priority=0, domain=inspect-ip-options, deny=true
hits=43, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 6
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x145fb1a04890, priority=13, domain=ipsec-tunnel-flow, deny=true
hits=45, user_data=0x0, cs_id=0x0, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=any
Phase: 7
Type: NAT
Subtype: rpf-check
Result: DROP
Config:
nat (inside,outside) source dynamic any-ipv4 interface
Additional Information:
Forward Flow based lookup yields rule:
out id=0x145fb5e234c0, priority=6, domain=nat-reverse, deny=false
hits=1, user_data=0x145fb5e21a80, cs_id=0x0, use_real_addr, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0, nsg_id=none
input_ifc=outside(vrfid:0), output_ifc=inside(vrfid:0)
Result:
input-interface: outside(vrfid:0)
input-status: up
input-line-status: up
output-interface: inside(vrfid:0)
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule, Drop-location: frame 0x000056444aa88854 flow (NA)/NA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 03:01 PM
@00u18jg7x27DHjRMh5d7 this command is correct. Check out the line starting Phase 7, it confirms the nat rule matched. Which is your problem, it is translating the traffic behind the ftd interface.
As i said above create the nat exemption rule above the dynamic rule.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide