- Cisco Community
- Technology and Support
- Security
- Network Security
- FPR1010 FDM NAT / Policy (not working)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
FPR1010 FDM NAT / Policy (not working)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2022 10:55 AM
Hello
So I am having some issues deploying NAT...
My FPR1010 has a WAN (outside) IP 207.108.121.X which has a LAN (inside) 192.168.1.0.
I have NAT on INSIDE for an Internal Network (connected to a SG550) which is 192.168.5.1-192.168.5.55
The 192.168.1.0 (LAN/INSIDE) on FPR1010 has a static IP on SG550 GE1/1 of 192.168.1.2 and the SG 192.168.5.1-192.168.5.55 uses that for a PBR to access Internet, so everything 192.168.5.1-192.168.5.55 communicates with FPR via 192.168.1.2. Why PBR? Cause 192.168.5.56-192.168.5.100 uses different PBR for it's WAN.
Most of this is irrelevant My issue is that a device on 192.168.5.43 (using 192.168.1.2 to access Internet which uses 207.108.121.x for WAN) has an SSH Port 66. I want any device on "outside" to be able to come in and on Port 66 be directed to that 192.168.5.43 Device.
I created a NAT "outside any 66 inside 192.168.5.43 66" as well as a Policy allowing incoming from outside to 192.168.5.43 port 66 but I keep getting a rejection when trying to access it from outside.
I am clearly missing something and for now have no config to show you but maybe these words and description can start a narrative.
I am hoping to not get involved with why PBR, why internal 192.168.5.0 when I have 192.168.1.0 etc. Everything else works fine, I just need this to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2022 02:04 PM
can we see config of PBR ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2022 02:17 PM
I can post it tonight for sure.
Off hand it is :
access list 101 permit ip 192.168.5.0 0.0.0.63 any
access list 102 permit ip 192.168.5.65 0.0.0.63 any
route-map tointernet permit 10
match ip address 101
set ip next-hop 192.168.1.1
route-map tointernet permit 11
match ip address 102
set up next-hop 192.168.2.1
interface vlan
ip policy route-map tointernet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2022 05:00 PM
access-list 102 permit ip 192.168.5.65 0.0.0.63 any (not sure how your subnet, this should be 192.168.5.64/26)
Look at the example Policy-based Routing :
https://integratingit.wordpress.com/2021/04/18/ftd-policy-based-routing/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 12:11 PM
Like I feared, I had written the wrong PBR configuration. That is what I get for trying to remeber.
So anyway, I disabled PBR. I simplified it
192.168.5.0, on the SG500, uses 192.168.1.2 (GE 1/1) to access INTERNET via 0.0.0.0 0.0.0.0 192.168.1.2 route. So nothing else on the SG500 as far as programming.
Which revolves back to my initial issue of somehow I can not get connectivity from OUTSIDE port 66 to HOST 192.168.5.43 via INSIDE 192.168.1.2.
I have done a policy to open that port. I have done NAT from OUTSIDE ANY 66 INSIDE 192.168.5.43 66 and it does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 01:16 PM
please share the config of final PBR and NAT and ACL apply on OUT inside.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 02:20 PM
Well like I said, I no longer have BPR.
Regardless, I shall post my configs for FPR1010 and SG500
Meantime;
FPR
207.108.121.X OUTSIDE (WAN)
192.168.1.0 INSIDE (LAN)
route 0.0.0.0 0.0.0.0 207.108.121.x
route 192.168.5.0 255.255.255.0 192.168.1.2
192.168.1.0, by default with default Policy etc, uses WAN 207.108.121.X for Internet.
SG500
192.168.1.2 GE 1/1
vlan1 192.168.5.0
route 0.0.0.0 0.0.0.0 192.168.1.2
NP PBR
NO Policy/NAT outside of whatever would come standard to the SG500.
From OUTSIDE I want to connect to 207.108.121.x Port 66 which will go through 192.168.1.2 which will communicate with 192.168.5.43 Port 66.
66 will only be used on my whole Network by one Host, 192.168.5.43 (vlan 1 Host on SG), which connects to the Internet VIA 192.168.1.2 (GE 1/1 on SG) which connects to INSIDE on FPR1010 which has a WAN address of 207.108.121.X
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 02:57 PM - edited 04-25-2022 03:23 PM
route 192.168.5.0 255.255.255.0 192.168.1.2 <- FPR reach the subnet 192.168.5.0 using next-hop 192.168.1.2
Note that SG use same next-hop for default route !!
second you need static NAT for 192.168.5.43 port 66 and allow this traffic connection in OUT.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 04:22 PM
Not sure what you are suggesting with comment one. Are you saying I have it right, or that it was wrong? Is the SG next-hop being 192.168.1.2, which is the same for the route 192.168.5.0 255.255.255.0 192.168.1.2 on FPR, correct or wrong?
Default Route;
Name Interface IP Type Networks Gateway IP SLA Monitor Metric Actions 1INSIDE_to_5_Network
inside | IPv4 | 192.168.5.0/24 | 192.168.1.2 | 1 |
Access Control, If it is correct;
SOURCE DESTINATION
Action Zone Networks Ports Zone Networks Ports
Allow Outside_Zone Any 66 Inside_Zone SSH66_HOST 66
Obviously OUTSIDE is the 297.108.121.x, Port is the Port and SSH66_HOST is the 192.168.5.43
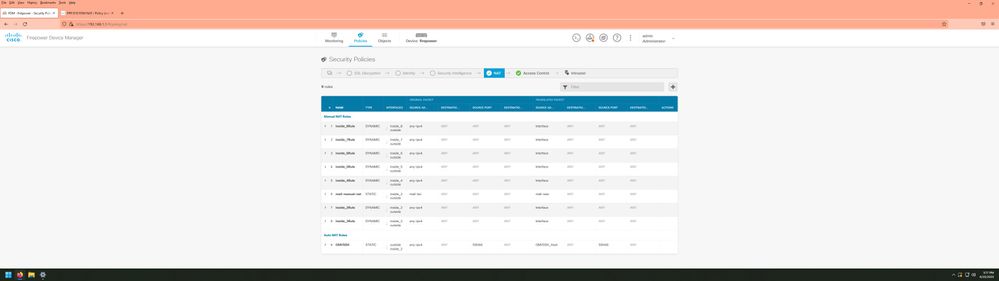
NAT; (is autonat)
Name Type Interfaces Original packet
Translated packet
Actions
OMVSSH
STATIC | outside inside_2 | any-ipv4 | Any | SSH66 | Any | OMVSSH_Host | Any | SSH66 | Any |
Will not connect with this configuration I had done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 04:59 PM - edited 04-25-2022 04:59 PM
Allow Outside_Zone Any 66 Inside_Zone SSH66_HOST 66 <-Outside client will use unknown port to connect to SSH66 with port 66, so change it to any.
For the routing why SG and FPR use same next-hop ??
For NAT can you show me screenshot ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2022 05:23 PM
Well, I guess I have no answer about the route. My thought that for the FPR to communicate with the Network 192.168.5.0 which is not directly associated to the FPR, I had to create a route to tell it that to get to 192.168.5.0 I have to go through 192.168.1.2, it's (FPR) local LAN Network.
For the SG500 being that 192.168.1.2 is in L3 by using an Interface, vlan1 (local LAN on SG) 192.168.5.0 had to have a route to 192.168.1.2 to access the internet.
Was this theory wrong? I mean, I have no issues getting onto the Internet... Or maybe that is the issue, why I can't SSH in.
Hopefully you are able to zoom in on pic, I also added it as an attachment.
I did indeed change "66" to any on the outside coming in. Did not work..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2022 05:46 AM
@TheGoob it's probably a conflict on the NAT rules. Your SSH NAT rule should be above the other NAT rules.
Your current Manual NAT rules should be changed to Auto NAT. Your Auto NAT rule for SSH should be a Manual NAT.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2022 07:30 AM
Morning
I will do this change this evening. May I ask how it is a conflict? I just never know when and where and why to use Auto over Manual.
I have no reason as to why I did each other than keep trying different variations.
By looking at the screenshot, how do you tell that the Manual NAT is causing conflicts without knowing what it is?
I hope that comes across with humility. I truly do not understand how you see that, and wish to learn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2022 05:22 PM - edited 04-26-2022 05:22 PM
I changed the existing MANUL NAT to Auto, and it's functionality still works.
But, when I create MANUAL NAT for the SSH 66, nada.
STATIC | outside inside_2 | any-ipv4 | Any | SSH66 | Any | OMVSSH_Host | Any | SSH66 | Any |
I also did inside_2 outside and reversed everything.. Also, it is "above" other nat rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2022 07:24 AM
Well something is clearly odd. That Manual NAT you told me to change to Auto was a STATIC 1 to 1 NAT. I have multiple WAN Static IP’s x.x.x.182 is man FPR1010 WAN, and x.x.x.182 is Static NAT 192.268.5.55. For fun I added a policy for Port 66 on that device and sure enough I can SSH to it and then from that device I can SSH to the 192.168.5.43.
I am wondering if there is an issue with this; I have made 192.168.5.55 specific to a WAN IP not the FPR main WAN but the 192.168.5.43 is the FPR WAN IP which utilizes the 192.168.1.0 Inside. Should I be creating a NAT to 192.168.1.2 Port 66 then to 192.168.5.43? I know how Auto NAT has source and destination but Manual NAT has source destination then source and destination. Should it be like outside to inside then inside to 192.168.5.43. So, x.x.x.182 to 192.168.1.2 then 192.168.1.2 to 192.168.5.43 or am I overthinking?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide