- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD VTI tunnels limit
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2023 03:00 PM
I use FTD (FPR1010) for VTI tunnels to remote sites. When I have 10 tunnels, they are all stable, however, as soon as I add new tunnel it works but flopping periodically. As more new tunnels are added, they flop more frequently. At the same time, the original 10 tunnels are still stable (only new tunnels are flopping). It looks weird to me. Does the FPR1010 have a limit on number of VTI tunnels? Should I switch to the next version (FPR1012) to have more than 10 tunnels (actually I need around 50 tunnels from the FTD)? With ASA 5506 I could have around 25 VTI tunnels without any issue.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2023 11:52 AM
I've found a fix of the problem. For each tunnel with FTD at the far end, I've added a unique Local Identity Configuration Key ID. After that all tunnels are Up and stable. It seems the reason was that IP address of each remote FTD's outside interface behind NAT is the same on all remote FTDs, and each FDT uses this IP address as ID by default. This explains why only one tunnel at a time was up for about 20 seconds until another tunnel with the same ID was coming Up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2023 04:37 PM
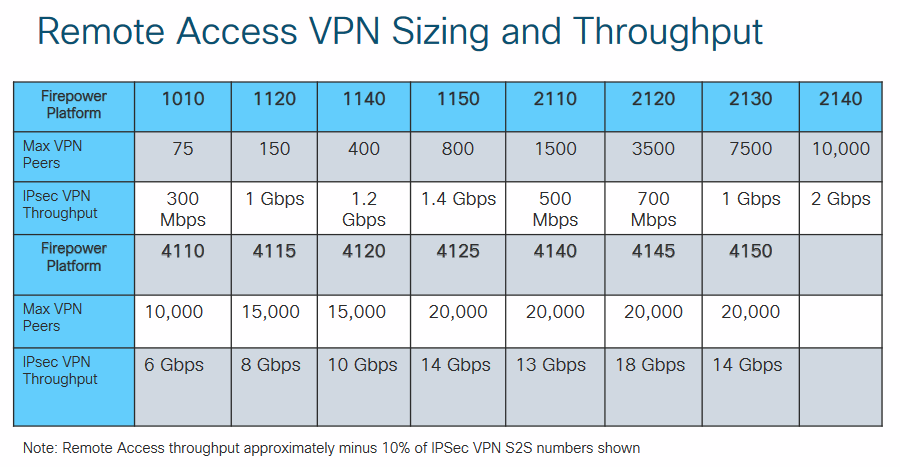
the Firepower 1010 support up to 300 mbps vpn throughput.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2023 02:05 AM - edited 05-19-2023 02:08 AM
You can create up to 100 VTIs per source interface, and a maximum of 1000 VTIs.
you 1010 only support up to 75 vpn tunnel and if you requirement is more then this in that case you might have to consider to upgrade your FTD unit. the way you describe your issue it seems the FTD 1010 can not handel the traffic flow it might doing more cpu processes on the other part (either control plane/mgmt plane) doing the IPS inspection. so yes could be this is the issue. did you check when you had these issues on the vpn what is the processes utlization on the box?
what is the presentation of your Internet line? was it the same internet line you used for the ASA too?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2023 12:49 PM
I've disabled IPS inspection, but it doesn't help. The 10 VTI tunnels work perfect. As soon as I add a new VTI tunnel, it doesn't work stable and also affect one existing VTI tunnel.
Data Plane and System memories are the same as before while Snort memory has increased from 24% to 38%. The Control Plane CPU has increased from 0.3 to 0.7.
BTW, the FTD version is 7.0.1 while FMC version is 7.1.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2023 09:00 AM
Probably I should open a ticket with Cisco TAC on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2023 09:54 AM
I am sure the unit FTD 1010 is definitely capable to support more than 10 VTI. it could be some how software bug playing up with this. But if you have cisco TAC support please open case with them.
Your CPU processor look normal in given circusmstance. worth giving tac a shout on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2023 09:57 AM
It can we look in different direction'
It can that the vti effect fpr routing and effect all other vti.
You say that over 10 vti' disable old vti and enable new vti and see if the fpr show same issue or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2023 09:02 PM
10 VTIs work perfect. As soon as I add the 11th VTI, it doesn't work stable (it stays Up for around 20 seconds and drops). Also, one of the old VTIs stars flopping as soon as the 11th VTI is added. As soon as the 11th VTI is deleted, the original 10 VTIs become stable again.
I'll try to add the 11th VTI and remove one of the original VTIs and see if the new 10 VTIs are stable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2023 09:43 PM
OK, let me provide some updates. It seems FPR1010 doesn't like more than one VTI with FPR1010 on far end. 9 of 10 VTIs are with ASA 5506 on far end with only one VTI with FPR1010 on far end. I've removed all my 9 VTIs with ASA (while keeping one VTI with FPR1010) and added one VTI with FPR1010 on far end. They don't work. New VTI runs for around 20 seconds and drops while the original VTI doesn't come up (it was working before I added new VTI).
My local FRP1010 runs version 7.0.1 while all far end FPR1010 runs version 7.1.0. I'll try to upgrade the local FPR1010 to the version 7.1.0 and check if it helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 01:44 AM
This is very Interesting. 2xFTD 1010 the VTI does not work. Are they managed FTD through FMC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 10:12 AM
Yes, they are all managed by FMCs, separate FMC for each FTD so far.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 02:23 AM
Can I see how you config the VTI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 10:18 AM
Interface IP-Address OK? Method Status Protocol
Tunnel1 x.x.x.x YES CONFIG up up
Tunnel3 x.x.x.x YES CONFIG up up
Tunnel10 x.x.x.x YES CONFIG up up
Tunnel16 x.x.x.x YES CONFIG up up
Tunnel22 x.x.x.x YES CONFIG up up
Tunnel29 x.x.x.x YES CONFIG up up
Tunnel30 x.x.x.x YES CONFIG up up
Tunnel32 x.x.x.x YES CONFIG up up
Tunnel34 x.x.x.x YES CONFIG up up
Tunnel35 x.x.x.x YES CONFIG up up
Tunnel38 x.x.x.x YES CONFIG down down
Tunnel41 x.x.x.x YES CONFIG down down
interface Tunnel35
nameif Jefferson
ip address x.x.x.x 255.255.255.252
tunnel source interface outside
tunnel destination y.y.y.y
tunnel mode ipsec ipv4
tunnel protection ipsec profile FMC_IPSEC_PROFILE_3
!
interface Tunnel41
nameif Baker
ip address 169.254.10.154 255.255.255.252
tunnel source interface outside
tunnel mode ipsec ipv4
#The respective IPSEC tunnel is removed
!
interface Tunnel38
nameif Macon_1
ip address 169.254.10.142 255.255.255.252
tunnel source interface outside
tunnel mode ipsec ipv4
#The respective IPSEC tunnel is removed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 12:22 PM - edited 05-22-2023 12:27 PM
this same major subnet 169.254.10.x 255.255.255.x
check if there is conflict in IP
also this IP is 169.x is used in case of system not get ip from DHCP server, why you use it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2023 12:19 PM
I've upgraded the FTD from version 7.0.1 to 7.1.0, but it doesn't help. The issue is still there.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide