- Cisco Community
- Technology and Support
- Security
- Network Security
- High Availability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
High Availability
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2011 08:38 AM - edited 03-11-2019 01:44 PM
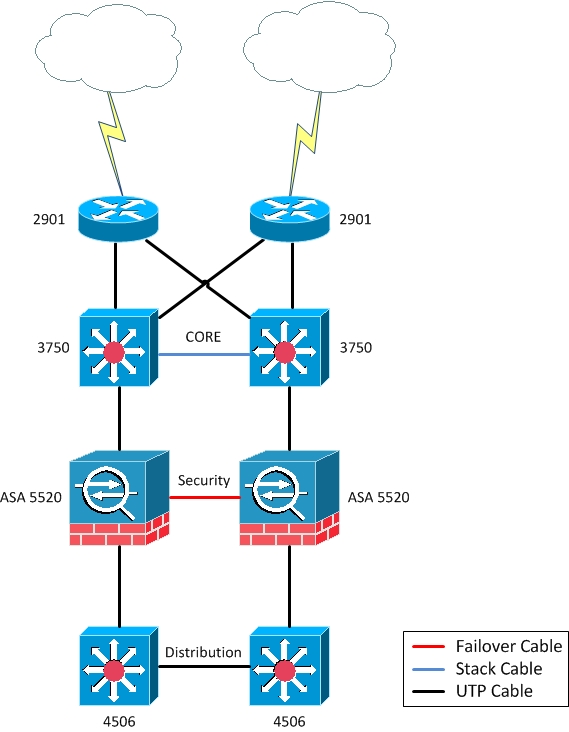
We’re planning to implement a High Availability environment with no one SPOF (topology attached)
The environment consists in:
2- Routers 2901 which will receive internet links
2- Catalyst 3750 acting as a core cause it’ll receive a few more services.
2- ASA 5520 in the security layer.
2- Catalyst 4506 which will be responsible to my distribution layer (server, farm, users and iSCSI).
No problem so far.
We’re going to set up both 4506 working active/active with the protocol GLBP, but the ASA does not work with this protocol (if I’m not wrong), so how can I make the firewall works fine with it?
I mean I need to know which protocol should I use, or what kind of configuration to use, to keep both 4506 working simultaneously.
I have no problem with use other protocols, so if there is someone appropriate to this case I’ll be grateful to know.
Also I don’t need that the both ASA working as Active/Active, but the distribution (4506) must to be.
I’ll appreciate all tips and ideas you guys could supply.
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2011 02:23 PM
When you are using GLBP you must be careful, or your trunks may have much more traffic than you anticipated!
Also, why is it necessery to have Active/Active 4500, when you will have only one active FW?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2011 02:46 PM
Hi Mile,
Thanks for the answer!
I need both 4500 active/active cause i'm going to have a server with 4 nics and i'll connect 2 in each 4500 if one of then be in standby i'll lose two nics and how i'll use vmware in this server, two nics i'll be not enough. The same thing happens to the storage, I have just one nic for which SP, so the throuput won’t be enough nether.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2011 05:00 PM
You should use all 4 NICs, that is not in question, but think about this...
You have SW1 and SW2 (your core switches).
You configure GLBP.
Host on SW1 sends ARP request. Since it is round robin, SW1 that is Virtual Active Forwarder, it can calculate to send VMAC of AVG (which is SW2), and you have your FW connected to SW1, so your traffic flow would be:
Host - > broadcast ARP, then Host connected to SW1 will send IP packets destined for VMAC of SW2, that will return the same traffic over trunk back to SW1 so it can over firewall...
It's a bit messy... And that is why I do not like GLBP...
On the other hand, you will have just 1 Gb port connecting your SW with firewall, so that is highest amount of traffic that can be transported either way.
I presume that most of the traffic will not go through firewall, because if it does, there is nothing much we can do.
If most of traffic will stay at pair of 4500, I would create two VLANs, and then just configure SPT and HSRP (or VRRP) to have Sw1 default gateway for one VLAN, and SW2 as default gateway for second VLAN.
So, for the traffic going to servers, 4500 will route them internally, wherever they are coming from.
For outgoing traffic, one VLAN will use SW1 as default gateway (SW1 locally connected hosts+SW2 hosts over trunk), SAN VLAN will use SW2 (SW2 locally, hosts connected to SW1 over trunk)…
Altogether, you don’t get anything fancy, and bandwidth utilized is about the same, just this is a bit neater ••J
On firewall side, you can use standard ASA Active/Passive configuration,
Configure ASA VLAN on switches, use /29 IP addresses and that’s it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2011 02:46 PM
Do you have any better idea?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
