- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: L2L IPSEC DNS and DNS Gaurd?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 07:40 AM - edited 02-21-2020 09:34 AM
Hello Folks,
When I establish a L2L tunnel over IPSEC, how can I have access to the other network dns? is it automatic?
and how should the other end define the dns gaurd? so I can't flood their udb port(DOS)?
Thx
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2019 12:02 AM
Hi,
What is DNS Guard?
The DNS guard function inspects and tears down an existing DNS connection associated with a DNS query as soon as the first DNS response message is received and forwarded by the firewall. The firewall also monitors the message exchange to ensure that the transaction ID of the DNS reply matches the transaction ID of the initial DNS query. For the firewall to successfully mitigate cache poisoning attacks, both the initial DNS query and the subsequent non-malicious DNS response will need to transit the firewall. In the unlikely occurrence that the malicious DNS response arrives first and with the correct transaction ID, then the firewall is unable to prevent DNS cache poisoning type attacks.
Enabling DNS guard through either the command line DNS Guard function or DNS application inspection provides preventive controls against DNS cache poisoning attacks. This feature is enabled by default and is available on Cisco ASA, Cisco PIX and Cisco FWSM Firewalls.
https://www.cisco.com/c/en/us/about/security-center/dns-best-practices.html
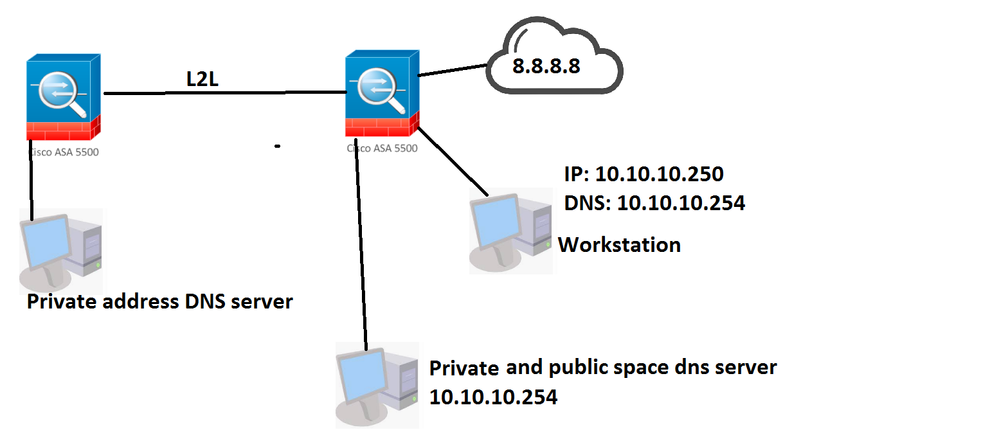
As I am understating your question, you want that end-users queries must be resolved from "Private address DNS server" if that query belongs to specific FQDN or domain and this "Private address DNS server" is seating at another site over the tunnel but you don't want to change DNS server address on the workstations. Is it correct?
If it is correct then no need to do anything on the Cisco ASA, You have to configure "Conditional DNS Forwarding" on the "Private and Public DNS Space" server for specific Domains or FQDNS. Now, If your workstation will send a query for specific DNS resolution that it belongs to "Private address DNS server" then your "Private and Public DNS Space" will auto redirect that query to the "Private address DNS server" and the client will get an answer.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 09:13 AM
If other side not allowed for your connect to internet, your attemtpts will be dropped.
you need to configure split tunnel for your own Internet access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2019 03:09 PM - edited 10-09-2019 10:28 PM
Could you read my question once again? this problem is so important to me
first of I am not asking about internet access, I am asking about their internal dns server, where they might have a local web server that they resolve with and all the host addresses,
second of all I don't even know when you L2L over ipsec to a remote asa(the asa on the left side), how do you access the dns of that network?(how do you(end host) have your own dns for your own network, and send your dns requests for that specific ip range to their DNS.(again this is a tunnel that's being established by our ASA to a remote ASA, and ASA does not send DNS inquiries workstations do). twice nat is the answer you think?
3rd, how does the dns guard works, which prevents from DNS flood attack? I know there is a mechanism on ASA called DNS guard, I just don't know if it's manual?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2019 12:02 AM
Hi,
What is DNS Guard?
The DNS guard function inspects and tears down an existing DNS connection associated with a DNS query as soon as the first DNS response message is received and forwarded by the firewall. The firewall also monitors the message exchange to ensure that the transaction ID of the DNS reply matches the transaction ID of the initial DNS query. For the firewall to successfully mitigate cache poisoning attacks, both the initial DNS query and the subsequent non-malicious DNS response will need to transit the firewall. In the unlikely occurrence that the malicious DNS response arrives first and with the correct transaction ID, then the firewall is unable to prevent DNS cache poisoning type attacks.
Enabling DNS guard through either the command line DNS Guard function or DNS application inspection provides preventive controls against DNS cache poisoning attacks. This feature is enabled by default and is available on Cisco ASA, Cisco PIX and Cisco FWSM Firewalls.
https://www.cisco.com/c/en/us/about/security-center/dns-best-practices.html
As I am understating your question, you want that end-users queries must be resolved from "Private address DNS server" if that query belongs to specific FQDN or domain and this "Private address DNS server" is seating at another site over the tunnel but you don't want to change DNS server address on the workstations. Is it correct?
If it is correct then no need to do anything on the Cisco ASA, You have to configure "Conditional DNS Forwarding" on the "Private and Public DNS Space" server for specific Domains or FQDNS. Now, If your workstation will send a query for specific DNS resolution that it belongs to "Private address DNS server" then your "Private and Public DNS Space" will auto redirect that query to the "Private address DNS server" and the client will get an answer.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2019 12:32 AM
Now your new post with more explanation makes sense? original post asked your DNS will be treated as attacks, it all depends on how other side agreement, to allow to deny.
coming back to your next post, as mentioned Deepak more explanation, you can have your own DNS or you can have DNS forwarder setup, both the case if your path using VPN tunnel, other side need to be allowed your interesting traffic to query DNS and internet traffic, if the contract only access local servers not any other, your required to have your own DNS Setup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2019 01:04 AM - edited 10-10-2019 06:29 AM
if my ASA and the remote ASA, ipsec access-list(crypto map match address) covers the remote side dns server ip subnet, do I still have to open another access list on the other side(Remote) for the DNS port(53)?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide