- Cisco Community
- Technology and Support
- Security
- Network Security
- Problem with a Cisco ASA 5510
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2010 11:07 AM - edited 03-11-2019 12:21 PM
Hello,
I post this message because I encounter a problem with my Cisco ASA
Quick Schema:
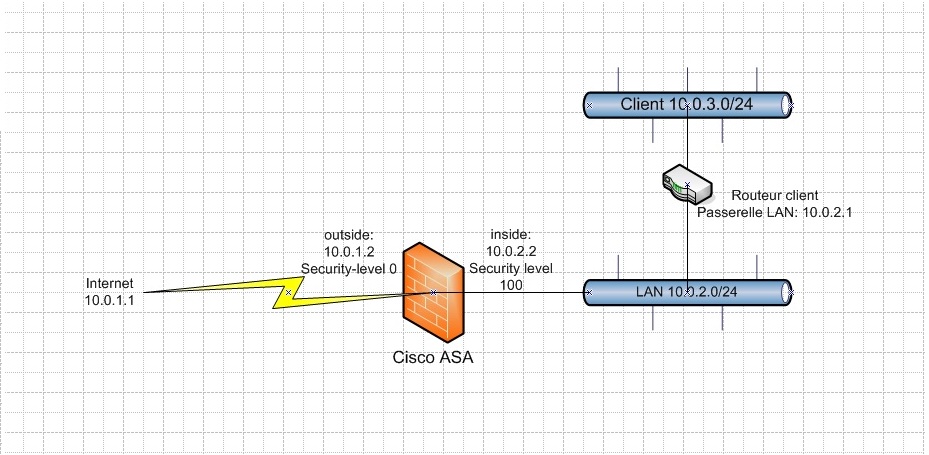
Plan:
The network 10.0.2.0 must have access to:
- Internet via the interface 10.0.1.1
- Client network 10.0.3.0 via a Citrix connection
Internet access:
- NAT rule:
global (outside) 1 interface
nat (inside) 1 10.0.2.0 255.255.255.0
- Default route:
Outside route 0.0.0.0 0.0.0.0 10.0.1 1 1
Network Access Client:
- Added the way to the client network that has no IP interface on the FW:
route inside 10.0.3.0 255.255.255.0 10.0.2.1 1
- Order same-security-traffic permit intra-interface to enter and exit from the same interface.
- Adding a NAT Exempt to join the client:
Access-list extended permit ip 10.0.2.0 IN_NAT_0 10.0.3.0 255.255.255.0 255.255.255.0
I'm not sure that this rule is necessary ...
Result:
From the LAN 10.0.2.0, I go on internet with NAT rule but i can't connect to the network client 10.0.3.0.
For info:
- NAT for the client network is managed by the client router.
- When I add the route10.0.3.0 255.255.255.0 10.0.2.1 directly on client PC, il doesn't pass through the firewall and it works.
So, there is a problem with my FW config.
Logs:
Errors: portmap translation creation failed for udp src inside: 10.0.2.10 / X dst inside: 10.0.3.X / X
I don't understand the link with my problem...
Config ASA:
I reset the config and i have not others config on the FW
Questions?
Should I add specific commands to access a network that is not directly connected to the FW from a network who is?
Normally, with the command same-security-traffic permit intra-interface, you can enter and exit through the same interface...
Thank you in advance for your help and sorry for my poor english!
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2010 09:43 AM
Hey glad to know that. Please mark this as answered if all is done.
Cheers,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2010 11:12 AM
Hello,
Traffic from 10.0.2.0/24 to 10.0.3.0/24 should not go through the ASA (both are Inside from the ASA perspective).
However, if your setup mandates to communicate both networks through the ASA, try this:
same-security-traffic permit intra-interface
static (in,in) 10.0.2.0 10.0.2.0 netmask 255.255.255.0
static (in,in) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
Make sure if there's an ACL applied to the inside interface that is permitting this traffic.
Let us know.
Federico.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2010 03:01 PM
Thanks for your help!
I test tomorrow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 01:48 AM
Hi,
I had the commands below:
same-security-traffic permit intra-interface
static (in,in) 10.0.2.0 10.0.2.0 netmask 255.255.255.0
static (in,in) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
And a ACL for testing:
access-list ACLINSIDE_IN extended permit ip any any
But I still have the problem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 02:26 AM
I post the config for more details:
ASA Version 8.2(3)
!
!
interface Ethernet0/0
no nameif
no security-level
no ip address
!
interface Ethernet0/0.705
vlan 705
nameif inside
security-level 100
ip address 10.0.2.2 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 10.0.1.2 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 10.0.4.0 255.255.255.0
management-only
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list ACLOUTSIDE_IN extended permit ip any host 10.0.1.10
access-list ACLINSIDE_IN extended permit ip any any
access-list IN_NAT0 remark NAT exempt 10.0.3.0
access-list IN_NAT0 extended permit ip 10.0.3.0 255.252.0.0 10.0.2.0 255.255.255.0
access-list IN_NAT0 extended permit ip 10.0.2.0 255.255.255.0 10.0.3.0 255.255.252.0
pager lines 24
logging enable
logging asdm informational
logging host outside X.X.X.X
mtu management 1500
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-634-53.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list IN_NAT0
nat (inside) 1 10.0.2.0 255.255.255.0
static (inside,outside) 10.0.1.10 10.0.2.10 netmask 255.255.255.255
access-group ACLINSIDE_IN in interface inside
access-group ACLOUTSIDE_IN in interface outside
route outside 0.0.0.0 0.0.0.0 10.0.1.1 1
route management X.X.X.X 255.255.255.255 X.X.X.X 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
ssh timeout 5
console timeout 0
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
username admin password d/N8a6sCspr9dLCz encrypted privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:94cd9ffbc575d2a8acd49ee109e6b1ca
: end
Thanks for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 06:45 AM
Hi Francois,
Config looks ok to me. Post the output of the following command:
packet-tracer input inside icmp 10.0.2.10 8 0 10.0.3.10 detail
This should give us a better idea of what's going wrong. I suppose you are still seeing the portmap translation errors.
Cheers,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 08:15 AM
I post the output of the following comand:
packet-tracer input inside icmp 10.0.2.10 8 0 10.0.3.10 detail
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd74189b8, priority=1, domain=permit, deny=false
hits=522199, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
static (inside,inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
match ip inside 10.0.3.0 255.255.255.0 inside any
static translation to 10.0.3.0
translate_hits = 0, untranslate_hits = 1
Additional Information:
NAT divert to egress interface inside
Untranslate 10.0.3.0/0 to 10.0.3.0/0 using netmask 255.255.255.0
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ACLINSIDE_IN in interface inside
access-list ACLINSIDE_IN extended permit ip any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd8074fb8, priority=12, domain=permit, deny=false
hits=21446, user_data=0xd64581c0, cs_id=0x0, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd741aec0, priority=0, domain=inspect-ip-options, deny=true
hits=41873, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 5
Type: INSPECT
Subtype: np-inspect
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd741ab38, priority=66, domain=inspect-icmp-error, deny=false
hits=2024, user_data=0xd7654958, cs_id=0x0, use_real_addr, flags=0x0, protocol=1
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 6
Type: NAT
Subtype:
Result: ALLOW
Config:
static (inside,inside) 10.0.2.0 10.0.2.0 netmask 255.255.255.0
match ip inside 10.0.2.0 255.255.255.0 inside any
static translation to 10.2.2.0
translate_hits = 1, untranslate_hits = 1089
Additional Information:
Static translate 10.0.2.0 /0 to 10.0.2.0/0 using netmask 255.255.255.0
Forward Flow based lookup yields rule:
in id=0xd754a088, priority=5, domain=nat, deny=false
hits=2, user_data=0xd76a17d8, cs_id=0x0, flags=0x0, protocol=0
src ip=10.0.2.0, mask=255.255.255.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 7
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (inside,outside) 10.0.1.10 10.0.2.10 netmask 255.255.255.255
match ip inside host 10.0.2.10 outside any
static translation to 10.0.1.10
translate_hits = 1046, untranslate_hits = 105
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd81111a8, priority=5, domain=host, deny=false
hits=1130, user_data=0xd7419798, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=10.0.2.10, mask=255.255.255.255, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 8
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
static (inside,inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
match ip inside 10.0.3.0 255.255.255.0 inside any
static translation to 10.0.3.0
translate_hits = 0, untranslate_hits = 1
Additional Information:
Forward Flow based lookup yields rule:
out id=0xd5b50ad8, priority=5, domain=nat-reverse, deny=false
hits=1, user_data=0xd76d9e00, cs_id=0x0, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=10.0.3.0, mask=255.255.255.0, port=0, dscp=0x0
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 40017, packet dispatched to next module
Module information for forward flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: inside
output-status: up
output-line-status: up
Action: allow
For your information, I don't have any message "portmap translation..." since I add:
- static (inside,inside) 10.0.2.0 10.0.2.0 netmask 255.255.255.0
- static (inside,inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
- access-list ACLINSIDE_IN extended permit ip any any
But I have this "level 6" messages when I try a connection to 10.0.3.X from 10.0.2.10
built inbound UDP connection X for inside:10.0.2.10/X (10.0.2.10/X) to inside:10.0.3.X/X(10.0.3.X/X)
teardown UDP connection X for inside:10.0.2.10/X to inside:10.0.3.X/X/X duration 0:00:00 bytes ...
.....
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2010 08:26 AM
Hi Francois,
Hmmm. So i think now the issue is with how U-turning works with firewalls. In our case, when we send a packet from 10.0.2.x to 10.0.3.x, the original packet goes through the ASA but the return packet goes directly to the 10.0.2.x host bypassing the firewall.
Hence, the ASA sees only one direction of traffic and hence will drop all subsequent packets from 10.0.2.x destined to 10.0.3.x.
What kind of UDP traffic are you passing between 10.0.2.x and 10.0.3.x, If it's DNS, remove the "inspect dns" that may be present under "global_policy".
If TCP traffic is also going to pass between 10.0.2.x to 10.0.3.x, you will need to create tcp state bypass config and also disable seq number randomization. please follow the below document:
https://supportforums.cisco.com/docs/DOC-13728
In addition to
set connection advanced-options tcp-state-bypass
you will also need
set connection random-seq disable
try this out and let me know how it goes!!
Cheers,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2010 05:43 AM
Hi
Thanks Prapanch for your response and the link.
The first solution below works:
Configuring NAT for both subnets:
static (inside,inside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0 norandom nailed
static (inside,inside) 172.16.10.0 172.16.10.0 netmask 255.255.255.0 norandom nailed
Adding the nailed option to the static command causes TCP state tracking and sequence checking to be skipped for the connection. More info can be found here:
However, I would like use the second solution with TCP_STATE_BYPASS and class-map creation who is more secure.
But this solution doesn't works, I still have dropped TCP connections.
- I created a class-map "TCP_STATE_BYPASS"
- I match access-list TCP_STATE_BYPASS (access-list TCP_STATE_BYPASS extended permit ip 10.0.2.0 255.255.255.0 10.0.3.0 255.255.255.0
- I created a policy-map "inside_policy" and I added the class-map
- On the policy-map I added the commands:
set connection random-sequence-number disable
set connection advanced-options tcp-state-bypass
- Finally, I linked the policy-map to the service-policy and the service-policy to the interface "inside"
But I still have the policy-map global_policy enabled on all the interfaces.
Is this a problem? I understand that a service-policy on an interface was priorituy on the global_policy
Config:
class-map TCP_STATE_BYPASS
match access-list TCP_STATE_BYPASS
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map inside_policy
class TCP_STATE_BYPASS
set connection random-sequence-number disable
set connection advanced-options tcp-state-bypass
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
service-policy inside_policy interface Inside
Thanks in advance for your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2010 06:47 AM
Hi,
Can you post the packet-tracer here:
packet-tracer input inside tcp 10.0.2.10 1234 10.0.3.10 80 det
Also, just to clarify, the config does look good. @ servicepolocies should not cause an issue. But in our case, you can apply the calss-map for tcp state bypass to global_policy" itself like below:
policy-map global_policy
class TCP_STATE_BYPASS
set connection random-sequence-number disable
set connection advanced-options tcp-state-bypass
In this case, you can remove the service-policy from the inside interface. What version ar you running on the ASA?
Cheers,
Prapanch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2010 06:52 AM
Fancois,
Can we address this problem a little different? The right way to fix this issue is as follows:
When 10.0.2.0/24 and 10.0.3.0/24 want to talk with each other, these packets should not come to the firewall. The router should be able to do the routing and these packets should not arrive on the firewall. Is this not possible in your network?
If the GW configured on the clients in the 10.0.2.0/24 are pointing to the firewall, then we need to swap the IP addresses between the ASA and the router and give the router the IP address or the firewall and vice versa.
The router should only have a default route pointing to the firewall for any route it does not know.
-KS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2010 07:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2010 02:38 PM
If I were you, I would track the folks who manage the router and get this think configured the right way.
Besides that like Prapanch says tcp state bypass is another option. All tcp packets will be treated like udp packets.
-KS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2010 01:13 AM
Hi,
The version of the ASA is 8.23 (asa823-k8.bin) and it's a base license.
I applied the class-map for tcp state bypass to global_policy but I still have the issue.
access-list TCP_STATE_BYPASS extended permit ip 10.0.2.0 255.255.255.0 10.0.3.0 255.255.255.0
class-map TCP_STATE_BYPASS
match access-list TCP_STATE_BYPASS
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class TCP_STATE_BYPASS
set connection random-sequence-number disable
set connection advanced-options tcp-state-bypass
!
service-policy global_policy global
I don't know very well MPF witch class-map so I think I'll use the solution with nail option and failover timeout...
For information, I post the output for the command: packet-tracer input inside tcp 10.0.2.10 1234 10.0.3.10 80 det
Phase: 1
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
static (Inside,Inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
match ip Inside 10.0.3.0 255.255.255.0 Inside any
static translation to 10.0.3.0
translate_hits = 0, untranslate_hits = 24
Additional Information:
NAT divert to egress interface Inside
Untranslate 10.0.3.0/0 to 10.0.3.0/0 using netmask 255.255.255.0
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group ACL_Inside_IN in interface Inside
access-list ACL_Inside_IN extended permit ip any any
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd7d35db8, priority=12, domain=permit, deny=false
hits=1157, user_data=0xd64581c0, cs_id=0x0, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd741aec0, priority=0, domain=inspect-ip-options, deny=true
hits=49334, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
static (Inside,Inside) 10.0.2.0 10.0.2.0 netmask 255.255.255.0
match ip Inside 10.0.2.0 255.255.255.0 Inside any
static translation to 10.0.2.0
translate_hits = 24, untranslate_hits = 4368
Additional Information:
Static translate 10.0.2.0/0 to 10.0.2.0/0 using netmask 255.255.255.0
Forward Flow based lookup yields rule:
in id=0xd7625540, priority=5, domain=nat, deny=false
hits=24, user_data=0xd7d000f0, cs_id=0x0, flags=0x0, protocol=0
src ip=10.0.2.0, mask=255.255.255.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 5
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (Inside,Outside) 10.0.1.10. 10.0.2.10 netmask 255.255.255.255
match ip Inside host 10.0.2.10 Outside any
static translation to 10.68.226.9
translate_hits = 3325, untranslate_hits = 385
Additional Information:
Forward Flow based lookup yields rule:
in id=0xd81111a8, priority=5, domain=host, deny=false
hits=4396, user_data=0xd7419798, cs_id=0x0, reverse, flags=0x0, protocol =0
src ip=10.0.2.10, mask=255.255.255.255, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 6
Type: NAT
Subtype: rpf-check
Result: ALLOW
Config:
static (Inside,Inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
match ip Inside 10.0.3.0 255.255.255.0 Inside any
static translation to 10.0.3.0
translate_hits = 0, untranslate_hits = 24
Additional Information:
Forward Flow based lookup yields rule:
out id=0xd8103678, priority=5, domain=nat-reverse, deny=false
hits=24, user_data=0xd7d44800, cs_id=0x0, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=10.0.3.0, mask=255.255.255.0, port=0, dscp=0x0
Phase: 7
Type: NAT
Subtype: host-limits
Result: ALLOW
Config:
static (Inside,Inside) 10.0.3.0 10.0.3.0 netmask 255.255.255.0
match ip Inside 10.0.3.0 255.255.255.0 Inside any
static translation to 10.0.3.0
translate_hits = 0, untranslate_hits = 24
Additional Information:
Reverse Flow based lookup yields rule:
in id=0xd8103710, priority=5, domain=host, deny=false
hits=34, user_data=0xd7d44800, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=10.0.3.0, mask=255.255.255.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0xd741aec0, priority=0, domain=inspect-ip-options, deny=true
hits=49336, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip=0.0.0.0, mask=0.0.0.0, port=0
dst ip=0.0.0.0, mask=0.0.0.0, port=0, dscp=0x0
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 45678, packet dispatched to next module
Module information for forward flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Module information for reverse flow ...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Result:
input-interface: Inside
input-status: up
input-line-status: up
output-interface: Inside
output-status: up
output-line-status: up
Action: allow
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2010 08:38 AM
Hi,
Finally, it works with class-map and policy-map.
I made a mistake with the ACL TCP_STATE_BYPASS (bad network).
Thank you all for your help!
Regards
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

