- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Redirect traffic to FP but ignore the interface?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Redirect traffic to FP but ignore the interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 05:39 AM
Hello
On my ASA I have three interfaces Inside, Guest, Outside. I am redirecting all (barring few Servers) traffic to FP for inspection. In my Access Policy, as you can see from attachment, I have only selected traffic going from Inside to Outside, ignoring Guest interface.
What happens here? I know traffic from Guest is being redirected to FP as I can see some allow / deny logs on FP for Guest network. Somebody said, and I quote "If you don't include an interface in ACP, it's traffic won't be inspected but still subjected to some rules such as URL blocks etc" This does not make sense to me, can somebody please explain?
What difference does it make if I also include Guest interface in ACP?
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2019 12:44 PM
I dont no, if i understand you correct :) but i try to explain few fundamental which clear your concepts. I guess you are redirecting all traffic/selected traffic from ASA cli config for SFR module. with exception of your Server IP addresses. one can ask how to flow of traffic work for SFR with ASA.
there are some pre-requiste in order to fine tune the firepower to meet you requirments. first you need to understand the flow of traffic in SFR.
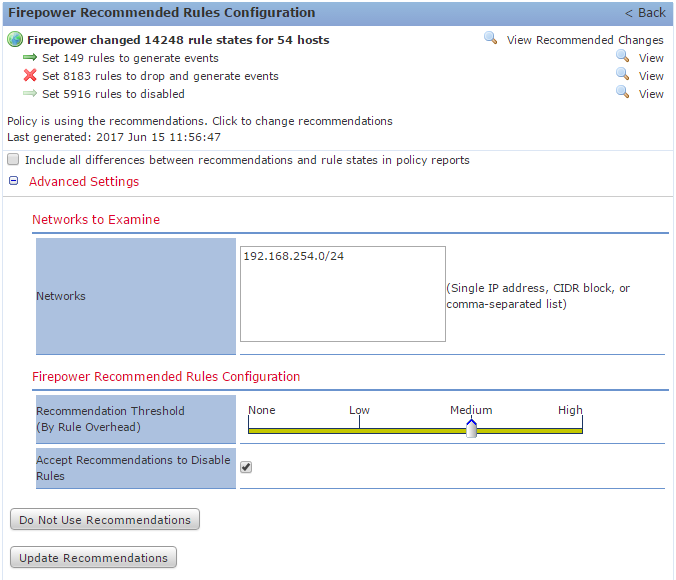
if you see the flow of traffic it will make sense to you. i shall skip explaination. in order to acheive the max use of SFR you have to define your network discovery host/subnet/application. by default its 0.0.0.0 which you dont want to set this as default to profile/gathere system informaiton of devices from your outside network e.g google.com/youtube.com etc. once you have define the network discovery, than go to your intrustion policy, you will see some option to use called "Firepower recommanded rules" this is something dont remember the accurte what it called the name. what you could do is you can define your interested subnet which you want them to inspect.
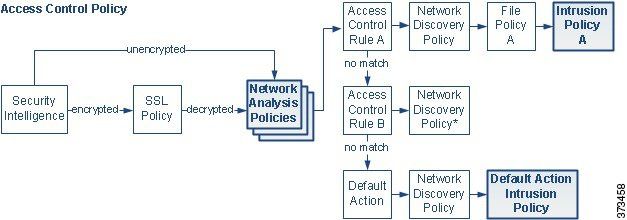
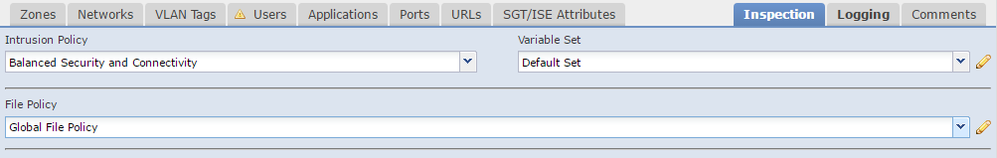
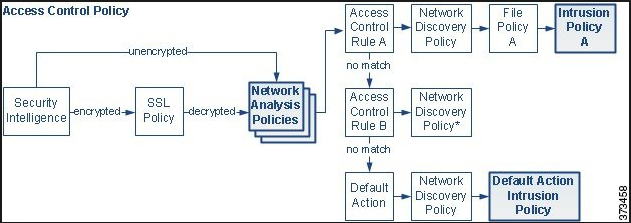
now coming to your ACP. you have define the Inside and outside. so what will happen is your traffic going from inside to outside will have intrustion inspection if you see the below picture intrustion policy is using the Balanced Security and Connectivity. you can define your own intrustion policy too and once define you can map it to below intrustion policy.
now if case if you did not define the intrustion policy like above one than in this case the default action will in. other thing you need to be aware is Variable set. you can fine tune them according to your needs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2019 08:05 AM
Thanks for your response. It does make sense to me but I will eloborate.
Suppose, I am redirecting traffic from 10.1.1.0/24 (inside Interface) and Guest (10.1.2.0/24) to FMC but in the ACP, I do not select Guest, only Inside to Outside.
What happens to traffic originating from Guest Interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2019 08:46 AM
Hi,
If your default action in ACP is BLOCK ALL TRAFFIC, your guest traffic will get blocked.
If your default action in ACP is BALANCED & SECURITY, your guest traffic will get inspected as per the policy.
check the ACP what is the default action you have set. All the traffic that is not specified in acp rule will get the default action.
Hope This Helps
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2019 11:19 AM
in that case, your default ACP rule will come in action. however, it would be better if you mapped this GUEST interface and subnet in FMC. the other thing you have to remember is to fine tune your network discovery policy, your intrustion policy too.
below is the flow of packet flow in Firepower make your self familiar with it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide