- Cisco Community
- Technology and Support
- Security
- Network Security
- Security Global Forum for ASA and FTD Topics - AMA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Security Global Forum for ASA and FTD Topics - AMA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2021
01:56 PM
- last edited on
01-13-2021
10:12 PM
by
Jimena Saez
![]()
| Español | Português | Français | Русский | 日本語 | 简体中文 |
This event is a chance to discuss about Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) regarding products, management, installation, configuration, implementation, use, and integration with other devices within your network. Learn the best practices to make the most of the advanced firewall settings, as well as the best practices to troubleshoot its common issues. This forum event works well as an introduction for those who are not familiar with the security tools and have recently started using them.
To participate in this event, please use the 
Ask questions from Tuesday, January 12 to Friday, January 22, 2021
 Berenice Guerra Martinez is a Technical Consulting Engineer at the Cisco Global Technical Assistance Center (TAC) for Security - Next Generation Firewall (NGFW). She specializes in Threat Detection, ASA and Firepower configuration and best practices, and Firepower integrations. Berenice has a bachelor’s degree in electronic engineering with a cybersecurity specialization and is a Telecommunications Technician. She holds three different Cisco certifications: CCNA R&S, CyberOps Associate, and DevNet Associate.
Berenice Guerra Martinez is a Technical Consulting Engineer at the Cisco Global Technical Assistance Center (TAC) for Security - Next Generation Firewall (NGFW). She specializes in Threat Detection, ASA and Firepower configuration and best practices, and Firepower integrations. Berenice has a bachelor’s degree in electronic engineering with a cybersecurity specialization and is a Telecommunications Technician. She holds three different Cisco certifications: CCNA R&S, CyberOps Associate, and DevNet Associate. Namit Agarwal is a Technical Marketing Engineer in the Security Business Group. He is based out of Toronto, Canada. He partners closely with our platform product management team and leads critical technical enablement engagements. He joined Cisco in 2009 and has held multiple positions, most recently working as a Technical Leader with the Security CX team in Bangalore, India. In that role, he worked on escalations, led serviceability initiatives for product improvement, and drove engagements with the NGFW sales teams. He is a CCIE n°33795 Security and has experience with multiple Cisco Security solutions such as Cisco Firewalls, IPS, VPN, and Cloud Security.
Namit Agarwal is a Technical Marketing Engineer in the Security Business Group. He is based out of Toronto, Canada. He partners closely with our platform product management team and leads critical technical enablement engagements. He joined Cisco in 2009 and has held multiple positions, most recently working as a Technical Leader with the Security CX team in Bangalore, India. In that role, he worked on escalations, led serviceability initiatives for product improvement, and drove engagements with the NGFW sales teams. He is a CCIE n°33795 Security and has experience with multiple Cisco Security solutions such as Cisco Firewalls, IPS, VPN, and Cloud Security. Ilkin Gasimov is a Technical Consulting Engineer in the Cisco Global TAC for Security - NGFW. He joined the TAC team in 2017 and since then has mainly been focused on supporting Cisco NGFW platforms and on the collaboration with the Cisco Business Unit to contribute to the NGFW product quality improvement. He has also delivered troubleshooting sessions to the partners and customers. Before joining Cisco, he had hands-on experience with the Cisco ASA firewalls in enterprise and mobile networking environments. He holds a CCIE n°54979 Security certification since 2016.
Ilkin Gasimov is a Technical Consulting Engineer in the Cisco Global TAC for Security - NGFW. He joined the TAC team in 2017 and since then has mainly been focused on supporting Cisco NGFW platforms and on the collaboration with the Cisco Business Unit to contribute to the NGFW product quality improvement. He has also delivered troubleshooting sessions to the partners and customers. Before joining Cisco, he had hands-on experience with the Cisco ASA firewalls in enterprise and mobile networking environments. He holds a CCIE n°54979 Security certification since 2016.
For more information, visit the Security Discussions category.
Find further events on Security Events list.
Please be sure to rate the Answers to Questions
- Adaptive Security appliance
- asa
- Berenice Guerra Martinez
- ccie
- ccnp
- Cisco Adaptive Security Appliance
- Cisco HTTS
- cloud security
- CyberOps Associate
- DevNet associate
- discussion
- Enterprise network
- escalade
- event
- firepower
- FirePOWER Threat Defense
- firewall
- forum
- FTD
- Ilkin Gasimov
- integration
- ips
- Namit Argawal
- Next Generation Firewall
- ngfw
- products
- Ricardo Diez Gutierrez Gonzalez
- Security CX
- vpn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2021 05:07 PM
hi,
is multi-instance/multiple context supported in FTD 2100 series? per link below it only mentioned 4100/9300
but per FPR-2100 data sheet in mentioned supported security context. is this running the FTD or ASA OS?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2021 09:22 AM
Multi-instance FTD deployment is supported only in Firepower 4100/9300 series.
The multi-context mode is supported only on ASA applications, not FTD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:11 PM - edited 01-13-2021 12:06 AM
Please teach me how to operate (convert) Firepower running ASA-OS with FTD (FX-OS).
Note: This question is a translation of a post originally posted in Japanese by cja56910tf. The post has been translated to all the languages we have in the community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:29 PM
Could you please clarify the details of this question?
Do you want to convert or migrate ASA to FTD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2021 05:50 PM
I'm running the ASA-OS on the chassis Firepower 1010.
I would like to to operate FX-OS using this chassis continuingly.
It means that I wouldn't like to move the ASA 5500X to Firepower, but I want to convert an ASA running on Firepower to FTD.
Note: This question is a translation of a post originally posted in Japanese by cja56910tf. The post has been translated into all the languages we have in the community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2021 03:21 PM
In order to convert ASA to FTD, you can follow the steps mentioned in the ASA→FTD: Firepower 1000 or 2100 Appliance Mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:13 PM - edited 01-13-2021 12:06 AM
Can you give us an example configuration for profiling devices with the Cisco ASA in conjunction with Cisco ISE for anyConnect connections on the Cisco ASA?
Note: This question is a translation of a post originally posted in Japanese by cja56910tf. The post has been translated to all the languages we have in the community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021
02:28 PM
- last edited on
01-14-2021
02:34 PM
by
Jimena Saez
![]()
Hi,
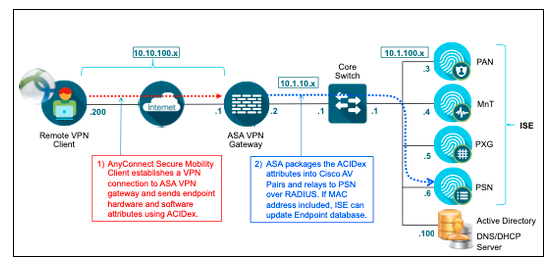
ACIDex attributes are mainly for profiling where is not required a special configuration within the ASA.
AnyConnect Identity Extensions (ACIDex)
Remote Access Virtual Private Network (VPN) clients represent a special use case for the ISE Profiler.
AnyConnect Identity Extensions (ACIDex) is a feature of the Cisco AnyConnect Secure Mobility Client which helps to solve this issue. ACIDex, also referred to as Mobile Posture, allows the AnyConnect VPN client to communicate endpoint attributes to the Cisco Adaptive Security Appliance (ASA) over a remote access VPN connection. The ASA can consume these attributes locally to make policy decisions, but can also relay the attributes in RADIUS to ISE PSNs as Cisco attribute-value (AV) pairs. When ISE receives ACIDex attributes that includes client MAC address(es), the PSN can update the corresponding endpoint in the Profiler database.
ACIDex Example.
Further details in the ISE Profiling Design Guide
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:14 PM - edited 01-13-2021 12:07 AM
Since DDoS attacks may occur from the Internet, we are considering using ASA or Firepower as a DDoS countermeasure device.
Does the machine have such a function in the first place?
Also, if there is a function, it would be helpful if you could teach us about setting examples, parameter values, and tuning points.
Note: This question is a translation of a post originally posted in Japanese by cja56910tf. The post has been translated to all the languages we have in the community
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:44 PM
Firepower 4100/9300 Series appliances support the deployment of Radware vDP in a Service Chain to protect against DDoS attacks.
Please review the following links:
1. Radware DefensePro Service Chain for Firepower Threat Defense Quick Start Guide
2. Firepower 4100/9300 Configuration guide - Chapter: Logical Devices
3. Links in the Radware DefensePro section of the Firepower 9300 Configuration Guides
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2021 11:25 PM
Why I'm not seeing any device in order to generate a Troubleshooting file from my Firepower devices?
Note: This question is a translation of a post originally created in Chinese by alina_xiao , It has been translated by Cisco Community to share the inquiry and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2021 07:09 PM
In order to generate the Troubleshooting file of your firepower devices, navigate in your FMC to System > Health > Monitor > Select Appliance within the list displayed > Generate Troubleshooting Files.
If you do not see any devices listed below you must probably need to click on the pie chart. Will depend on the health status of your devices from where you can click the pie chart portion to display them.
Green - Health status
Yellow – Appliances with some Warnings
Red – Appliances with Errors
Blue – Disabled Appliances
For more details you can go to the next content.
Cisco Video Portal - https://video.cisco.com/video/6155382458001
Cisco Tech Notes - https://www.cisco.com/c/en/us/support/docs/security/sourcefire-defense-center/117663-technote-SourceFire-00.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-13-2021 11:20 PM
Thanks for hosting this event. How can I manage my firepower devices?
Note: This question is a translation of a post originally created in Chinese by W2493455280 , It has been translated by Cisco Community to share the inquiry and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021
06:54 PM
- last edited on
01-14-2021
07:03 PM
by
Yanli Sun
![]()
You have two different options in order to manage your FTD, it can be locally using the Firepower Device Manager (FDM) or through the Firepower Management Center (FMC).
In order to see how to register the FTD within the FMC see next video with further details.
https://video.cisco.com/video/6156204074001
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-14-2021 05:31 AM
Hi team!
How can I take packet captures in the FTD? I’m familiar with the ASA captures however seems that those commands are not supported by the FTD.
Thanks
Note: This question is a translation of a post originally created in Portuguese by Adolfo Suarez. It has been translated by Cisco Community to share the inquiry and its solution in different languages.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide