- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: You need to have the complete
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2016 08:19 AM - edited 03-12-2019 12:32 AM
folks
I'm hoping you can help me with a query
I'm setting up a site to site vpn between an ASA and a palo alto, I've set it up and tested ok using a PSK but I now need to migrate it to using certificates instead of the PSK
I have defined the trustpoint and bound my identity cert and the issuer cert (the identity cert is issued by an enterprise authority) to the trustpoint
my problem is that when I test the vpn phase 1 fails and the asa complains that the peer's certificate is
CRYPTO_PKI(Cert Lookup) issuer="cn=x.x.x.x" serial number=xxxxxxxxxxx aaaaaaaa | w.....?%......
00 00 2e | ...
CRYPTO_PKI: Invalid cert
a debug crypto ikev1 127 complains that there is a Certificate Validation Failed
both my and the peer's certificates have been issued by the enterprise authority though they have different common names , the crypto policy is set for rsa-sig authentication and the tunnel group is pointing to the trustpoint
do I need to define a trustpoint and load the intermediate certificate too? (the intermediate issued the enterprise certificate)
thanks to anyone taking the time to have a look
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2016 09:39 AM
I've only ever done this on the ASA with asdm. If I understand it correctly, If you are using an intermediate CA you must add the Root CA certificate as well. It does not need to be on the same trust point. It just needs to be local.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2016 01:46 PM
You need to have the complete certificate chain on the ASA. Otherwise it can't validate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2016 04:34 AM
I agree with Phillip. You must have the entire chain imported on the ASA. The Root CA, and if you are using a subordinate CA for issuing must be imported as a CA certificate. The Identity certificate will be used during authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2016 05:32 AM
folks
thanks for all your replies, its greatly appreciated
i currently have the identity certificate and enterprise associated with the same trustpoint
are you telling me I need to have the intermediate and root certificates also loaded onto the ASA
if so, do I need to create a new trustpoint for the root and a new one for the intermediate?
I was sure I read that the ASA only needs the identity and issuing certificates, I've had a look but can't see any guides for installing certificate chains so I'd be grateful if you can point me in the right direction
thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2016 09:39 AM
I've only ever done this on the ASA with asdm. If I understand it correctly, If you are using an intermediate CA you must add the Root CA certificate as well. It does not need to be on the same trust point. It just needs to be local.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2016 09:59 AM
andre
i've got it working again
there were several issues that caused me problems
i created two new trustpoints and dropped the intermediate and root certificates into them
I had left out the trustpoint from the crypto map, once I got these added it started working
interestingly I was working from an example in the cisco asa all in one next gen firewall book and while it mentions adding in the identity and issuing certs it doesn't touch on the intermediate or root certs
thanks for all your help and patience
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2024 01:27 AM
@Philip D'Ath hi Philip,
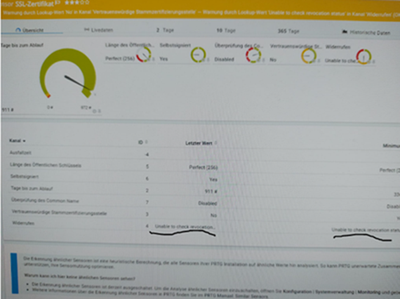
I have an SSL certificate alarm from PRTG that correctly highlights the "Unable to check revocation status"
with <sh crypto ca certificates> I can see that the issuing or root certificate authority or the root certificate authority is available to be queried.
I can also see the certificate via Cisco ASDM
>Configuration>VPN remote access>Certificate management>CA certificates.
I don't understand why I've been getting this alarm for a week on 3 of the 20 ASA firewalls.
I use the following command on the firewall in the CLI and if I import a firewall rule from the firewall and then perform a deployment, the parameter is overwritten: ssl trustp-point My_trustpoint
conf t
dynamic-access-policy-confi activate
vpn-addr-assign local reuse-delay 0
no ssl trust-point <My_trustpoint>
I don't understand why (CSM) Cisco Security Manager keeps deleting the last command line and unfortunately, I haven't found the corner of the CSM where this is configured....
This is probably the reason why messages appear in the prtg, because the verified certificate authority is not the right one or it is, by default, self-signed certificates on firewalls.
Unfortunately, our chain is not routed to the Internet". Unable to resolve the domain name" is the message I received from ssllabs.com.
Is there a way to validate or compare my parameters?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2016 11:26 PM
Could you run us through the steps you took to import the certificate to the ASA please.
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2017 05:34 AM
marius
apologies but i've only seen your query now
i created the trustpoint as normal but used the enrolment terminal command
i imported the the CA certificate using the crypto pki authenticate [TRUSTPOINT] name and pasted the certificate in from notepad
i generated the csr with the crypto pki enroll [TRUSTPOINT] name command and then imported the certificate with the crypto pki import [TRUSTPOINT] name command after copying it from notepad
you can view the certificates with the command show crypto ca certificates [TRUSTPOINT] name
hope this helps and again, apologies
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide