- Cisco Community
- Technology and Support
- Security
- Network Security
- Thank you . Much appreciated.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Spam feed in Security Intelligence
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2016 11:55 PM - edited 03-12-2019 06:03 AM
I use firepower v.5.4.1 on ASA 5516. I see huge amout of malware comming via mail (smtp connection). Almost every malware detection is only retrospective. It means malware reached customer mail servers and maybe users mail-boxes too. IP addresses of senders of malware messages (.zip files) are all listed as spam senders in senderbase.org or other anti-spam lists.
Firepower Security Intelligence has feed and one of the category is Spam. But there is only 32k of ip addresses. I see some match and block on this list, but majority of malware from spam IP senders passed and is detected only hours or days later by retrospective.
Could somebody suggest me reliable spam list (list of spammers IP addresses) which can be used as 3rd party list and can be downloaded as custom list? Or event better: is there any feed (not only static list) which can be used as Firepower Security Intelligence object?
- Labels:
-
NGIPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2016 03:08 AM
Hi,
As of now, we just have the static list in security intelligence but if you are observing
some spam ip's being bypassed, you can open a TAC case so that we can investigate it further
and have the feed updated on our end.
Rate if it helps.
Thanks,
Ankita
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 12:19 AM
Static list is not a problem. But it's poor content. Cisco owns intelligence sources (senderbase.org, ironport's source ....), but on firepower spam list is like a joke. Firepower services get passed hundreds of malware files (as it later marks as retrospective) and all of IPaddr of senders is listed on senderbase.org with poor mail reputation.
This is big confusion for customer: every morning opens firepower console and get list of passed malware, received from known malware senders.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-15-2016 11:12 AM
I have good experience with the Security Intel feeds. In addition, i added the Cisco Talos, feed, too. In addition, we have our own internal Security Analysts intel feed. No issues, so far. Good metrics and reporting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2016 11:07 PM
Could you be more specific, please? Where I can find theese feeds and how can I use it in Firepower.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2016 11:18 PM
Hello ,
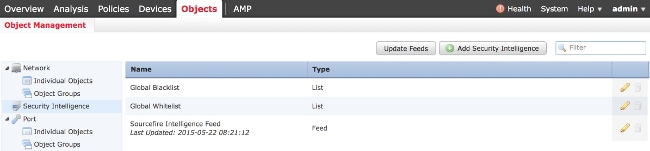
In order to update the Security Intelligence Feed, choose Objects > Object Management. Choose the Security Intelligence option from the left panel, and click Update Feeds. If you want to update your custom feed or you want to create a custom list, click Add Security Intelligence.
Rate if this post helps you
Regards
Jetsy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-17-2016 11:23 PM
As I wrote in my opening post, I use this buit-in feed. But these are poor. Because I receive tens of malware file per day. From IP addresses, which are known to Cisco (senderbase.org) as malware senders, but not included in built-in feeds. I am looking for third party feed to include to firepower which will contain IP's from senderbase.org (or similar) database.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2016 09:23 AM
Would you please be so kind to elaborate (for a Snort newbie) where do you check all of that stuff . I'm also interested in what happens with spam and if there is something we can do about it .
Much appreciated. Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2016 12:31 AM
Hi,
You can check the spam static list under /var/sf/si_urldownload and if you do
cat of the uuid , you will see the list of url or ip's in the list.
You can follow the document to have better understanding :
http://www.cisco.com/c/en/us/td/docs/security/firesight/541/user-guide/FireSIGHT-System-UserGuide-v5401/AC-Events.html
Rate if it helps.
Thanks,
Ankita
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2016 07:24 AM
Thank you . Much appreciated.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide