- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Unable to SSH to ASA 5525-X
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 01:27 AM
Hi,
I have four admin users on my ASA all with level 15 access but not of them are able to SSH to my device.
I have checked SSH settings and it is allowed.
Is there anything I could have overlooked? I'm sure this has worked in the past as the device is over 5 years old.
Thanks in advance.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:53 AM
I believe you are missing RSA keys, which are mandatory for SSH. Try with 'crypto key generate rsa modulus 2048', and try SSH after.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 01:53 AM
Hi @BeckyBoo123
Are the users even prompted to authenticate?
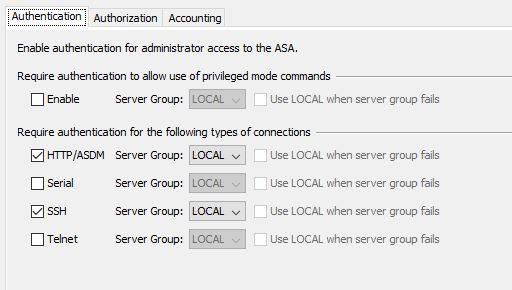
If not it could be you are connecting from a network/IP address that is not permitted to SSH to the ASA. See this really old guide
See the section of the guide "Configuration with ASDM 6.x" - step number 6. From here you need to define the networks/ip addresses permitted to connect to the ASA using ssh.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 02:19 AM
Hi @Rob Ingram
Thank you for the swift reply!
No, no authentication prompt at all is being received. Just says "Server unexpectedly closed network connection".
I've checked the settings that you mentioned and all looks good.
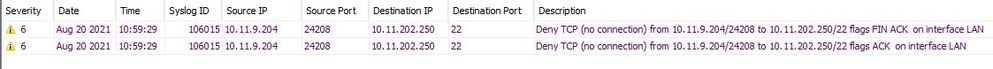
I am also seeing the following message when I try to connect:
%ASA-6-106015: Deny TCP (no connection) from IP_address/port to IP_address/port flags tcp_flags on interface interface_name. The ASA discarded a TCP packet that has no associated connection in the ASA connection table. The ASA looks for a SYN flag in the packet, which indicates a request to establish a new connection. If the SYN flag is not set, and there is no existing connection, the ASA discards the packet.
A quick Google of this error seems rather complex.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 02:32 AM
ASA-6-106015: Deny TCP (no connection) from IP_address/port to IP_address/port flags tcp_flags on interface interface_name.
Looks for me this is Routing issue. what is your client IP address ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:05 AM
I think you may be right. My client IP is 10.11.9.204 and that appears in the log entry.
I am unable to SSH to the device from where I am to check if the lines you asked about are present.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:17 AM
Is this only device, you need to find any other device with different IP can able to SSH, or we need to get in to Console to pull the information.
Note : i saw ASDM picture, are you able to use ASDM ? (from the IP mentioned ?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:42 AM
@balaji.bandi I have just tried to connect from another device (which is actually on the same network) and that too fails.
Yes I am able to access everything on the ASDM from my IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 03:56 AM
Hi @BeckyBoo123,
Could you please check the output (from console) of the 'show asp table socket'? We expect to see that device is listening on TCP/22?
Please also check the outputs:
- 'show run ssh', which should display SSH configuration
- 'show run aaa', to confirm authentication for SSH is configured
- 'show crypto key mypubkey rsa', to confirm that your SSH keys are present
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:27 AM
@Milos_Jovanovic Sorry but the ASA is physically in a different location. I cannot console in at the moment. That may be the only option I have though if I can't get to the bottom of it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:34 AM
From ASDM (not sure what version you have ) - you can use tools --> command line intercce you can issue the commands people requested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:40 AM
@balaji.bandi @Milos_Jovanovic
Sorry I forgot I could do that!
Result of the command: "show run ssh" ssh stricthostkeycheck ssh 10.0.0.0 255.0.0.0 LAN ssh timeout 60 ssh key-exchange group dh-group14-sha1 Result of the command: "show run aaa" aaa authentication http console LOCAL aaa authentication ssh console LOCAL Result of the command: "show crypto key mypubkey rsa" The command has been sent to the device
Hmm, does this mean my key is missing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:53 AM
I believe you are missing RSA keys, which are mandatory for SSH. Try with 'crypto key generate rsa modulus 2048', and try SSH after.
BR,
Milos
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 04:55 AM
Result of the command: "show crypto key mypubkey rsa"
Looks like a catch here, may be since you mentioned it was working several years and broken, worth re-key
or take show run (output and check)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 05:08 AM
@Milos_Jovanovic @balaji.bandi @Rob Ingram
I recreated the key and all works perfectly now!
Thank you all do much, I probably should have tested that first.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2021 05:15 AM
Glad to know our suggestion helped here , we mark as resolved.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide