Cisco SD-Access 2.1.2.0 continues to empower IT with Accessibility, Reliability and Analytics driven Segmentation
With its latest release, Cisco SD-Access introduces new capabilities and enhancements centered around security, accessibility, and reliability. Before we showcase the latest innovation in 2.1.2, let’s quickly refresh what was delivered in 1.3.3.
Cisco SD-Access 1.3.3 unveiled several notable features providing new automation and security capabilities including Policy extension for IoT, StackWise Virtual (SVL) Support, Layer 2 inter-site communication, and enhancements on Authentication templates & Multicast. With Policy extension for SDA and SVL, customers were able to extend security and automation to IoT devices outside the “carpeted network”, leverage micro-segmentation, and increase reliability & performance to bottleneck areas by virtually stacking switch capacity. Cisco SD-Access 1.3.3 pushed the capability for Distributed Campus even further with Layer 2 inter-site feature & authentication templates extending inter-site communication and enabling site-specific/ global authentication settings configuration.
Cisco SD-Access 2.1.2.0
In this article, we will elaborate on the most notable features offered as part of Cisco SD-Access 2.1.2.0 that will enable you to strengthen your IT infrastructure.
1 C9000 series as Policy Extended Node
Organizations are growing and becoming more complex by the day. With hybrid environments and complex networking infrastructure comprising of IoT devices, legacy and next-generation platforms, there is a glaring need for secure and efficient network operation. Cisco SD-Access allows you to secure your networks, achieve greater visibility, and maintain consistent policies while utilizing your existing infrastructure.
Starting from 2.1.2.0, Catalyst 9000 series as Policy Extended Node extends current Fabric Edge behavior to the extended enterprise and offers
- Group classification providing greater visibility –
- Profiling & Endpoint Analytics aggregates source information to group devices. Group labels assigned based on endpoint type help characterize them and apply appropriate security policies.
- Group-based policy analytics analyses traffic flow and provides insights that form the basis of access policies
- Secure and automated device onboarding solution with central policy automation and management saving time, money & effort required to make manual config changes
Cat9K as Policy extended node also provides flexible deployment options for you to retain existing Layer 2 network policies and extend the connectivity to the fabric and utilize macro-segmentation. You can accommodate your existing network designs and constraints without having to make disruptive changes.
2 IP Directed Broadcast
Being able to turn on computers remotely can be particularly useful for universities or businesses with large networks, where physically turning on all of the computers in a reasonable amount of time may not be feasible. IP Directed Broadcast allows n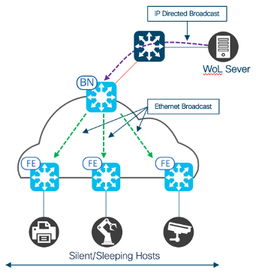 etwork administrators to remotely wake up/ turn on silent hosts, makes administrative tasks such as patch deployment or system maintenance convenient, and decreases overall energy consumption.
etwork administrators to remotely wake up/ turn on silent hosts, makes administrative tasks such as patch deployment or system maintenance convenient, and decreases overall energy consumption.
Up until now, this has been achieved using L2 flooding with the constraint that the WoL server and host must be on the same subnet. However, a usual enterprise deployment may have a server residing in the Data Center and hosts connected to a Fabric edge in an SDA fabric environment. With the 2.1.2 release, IP directed broadcast feature enables the SDA fabric to forward magic packets to hosts from an external domain.
3 StackWise Virtual Support for Catalyst 9400 and 9600 series
Health and Public sectors often require high availability of servers all the time and seek not just port-level redundancy but switch as well. For operational simplicity, customers often connect the endpoints to the core network even though the actual switches are in different locations.
StackWise Vir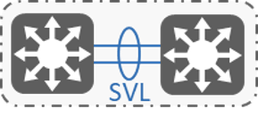 tual (SVL) allows two physical switches to operate as a single logical virtual switch. An election mechanism selects one of the switches to be the SVL Active device and the other switch to be the SVL Standby device. The active switch is responsible for all the management, bridging, routing protocols, and software data path, while the standby switch is ready to take over the role of active.
tual (SVL) allows two physical switches to operate as a single logical virtual switch. An election mechanism selects one of the switches to be the SVL Active device and the other switch to be the SVL Standby device. The active switch is responsible for all the management, bridging, routing protocols, and software data path, while the standby switch is ready to take over the role of active.
Starting from Cisco SD-Access 2.1.2 release, SVL will extend dual-home client connectivity at the edge to Catalyst 9400 & 9600 series
- Allowing two borders in different buildings to act as a single border
- Increasing operational efficiency by having a single control and management plane
- Reducing risk associated with a looped topology
4 Embedded Wireless Support for N+1
Increasing demand for reliable and performant infrastructure has got organizations concerned with eliminating single points of failure and decreasing downtime. High availability in controllers allows you to reduce the downtime of the wireless networks that occurs due to the failure of controllers.
With Cisco SD-Access 2.1.2 release, N+1 High Availability provides redundancy of Wireless LAN Controller (WLC). N+1 HA architecture allows a single WLC to be used as a backup WLC for primary controllers and provides redundancy for WLC across sites/floors or buildings within the fabric site. The primary and secondary WLC’s from different floors, buildings, or fabric sites can act as a backup/secondary for each other.
Implementing high availability for your infrastructure is a useful strategy to reduce the impact of component failures.
5 Multisite Remote Border
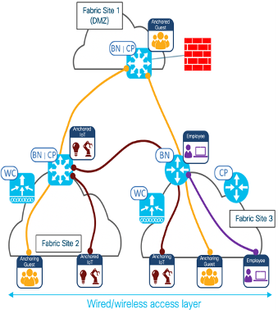 For security in a network environment, it is preferred that certain types of traffic terminates at a specific location irrespective of where it originates. However, since single IP address pools could not be configured across sites, this couldn’t be achieved in a multi-site deployment where traffic from VNs across multiple sites is required to egress the fabric at a particular location.
For security in a network environment, it is preferred that certain types of traffic terminates at a specific location irrespective of where it originates. However, since single IP address pools could not be configured across sites, this couldn’t be achieved in a multi-site deployment where traffic from VNs across multiple sites is required to egress the fabric at a particular location.
Cisco SD-Access’ Multisite Remote Border feature allows the same IP address pool to exist at multiple fabric sites through anchoring the pool to specific border and control plane nodes.
This feature enables multiple fabric sites to use one common external border node and enables a virtual network to be available across multiple sites.
6 IPv6 for SD-Access Wireless on Catalyst WLCs
Due to IPv4 exhaustion, customers are now looking for IPv6 support in all network devices, for scalability, policy compliance, and future-proofing their infrastructure. With 2.1.2, IPv6 support with Cisco SD-Access fabric wireless has been expanded to include Catalyst 9800, 9800-CL, and Embedded Wireless Controllers.
7 FlexConnect Over-the-Top Wireless
With FlexConnect customers were able to control & configure Access Points in a branch or remote office through Wide Area Network without deploying controllers in each office. In this setup, only Fabric-mode APs were able to connect endpoints to SD-Access virtual networks.
Starting from this release, Cisco SD-Access offers FlexConnect OTT which enables you to migrate the wired deployments to SD-Access while retaining your previous wireless FlexConnect design.
Cisco SD-Access 2.1.2 enables you to extend the capabilities of multi-site deployments with L2 fabric service & multisite remote border, increase reliability & availability with SVL support & N+1 HA for WLC and improve accessibility with policy extension and IP directed broadcast. Endpoint and policy analytics further strengthen the drive for better segmentation outcomes.
For more information on the latest innovations,
