Hi All,
After completing POCs and providing support to customers for Viptela, I got to know there are many Engineers who are confused about the certificates which need to be signed by the Root CA and also are not sure about the how to get the whitelist (serial.viptela) file that needs to be uploaded on the vManage controller.
This blog talks exactly about the above 2 requirements we have during the intial setup phase of Viptela fabric. Lets start..!
So once the controllers are deployed either on premises or on cloud we need to ensure we have basic IP reachability between the controllers of-course to form the control connections of DTLS/TLS.
After your controllers are ready, next is to add the vbond and vsmart controllers into your vmanage. This can be easily done from the vManage dashboard. Upto this point, I believe most of us are very much comfortable. Now comes the tricky part [Not exactly tricky but its just that we are not aware of it :)]
As we access the dashboard of vManage and are happy to see the controllers present there, we also see the operation state as N/A and certificate serial says "No Certificate Installed"
What Next????!!!!!!
Basically after we are done adding the controllers, to ensure the controllers are able to successfully form control connections among themselves and also with the edge routers, they need to get a signed certificate installed on them. This signed certificate will be used for 2 way authentication along with other parameters to trust one another & form the control connections.
There are 5 different options available for same.
- Automated third-party certificate signing through Symantec/Digicert.
- Manual third-party certificate signing through Symantec/Digicert
- Automated certificate signing through Cisco Systems
- Manual certificate signing through Cisco Systems
- Enterprise Root Certificate Authority (CA)
Option 1 > > Automated third-party certificate signing by Symantec/Digicert.
We can use Symantec/Digicert as Root CA and generate CSR request for the controllers/edge routers. This request can be submitted to Cisco by opening a Cisco TAC and selecting appropriate options. Once the request is approved and certs are signed, vManage will check for the certs at regular time interval configured by us and will install them automatically. In below screenshot time interval is set to 60 mins.
Note - In this method, vManage requires reachability to Symantec server.
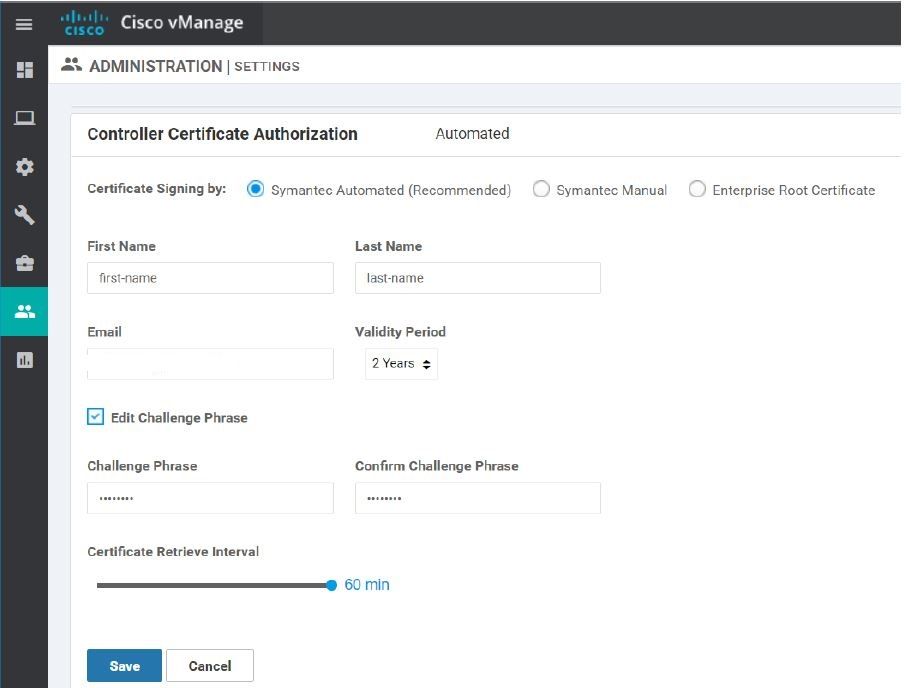
Option 2 > Manual third-party certificate signing through Symantec/Digicert
This option is similar to first one, except we need to manually upload the CSR on the Symantec portal. After which user needs to open Cisco TAC and provide the details. After which certificates will be sent as an attachment on the email provided in the contact information which can be either copy pasted or uploaded.

Option 3 > Automated certificate signing through Cisco Systems
This option is shortest,quickest and completely automated to get the cert signed by Cisco but possible only if the user has access to smart account. One can simply provide the smart account credentials in the vManage dashboard and go to controllers and generate CSR request. This CSR will be directly sent to Cisco and signed after approval. vManage will keep track for signed certs on regular interval configured by the user and will be installed on the respective controllers once available.
Note - In this method, vManage requires reachability to Cisco PnP server.
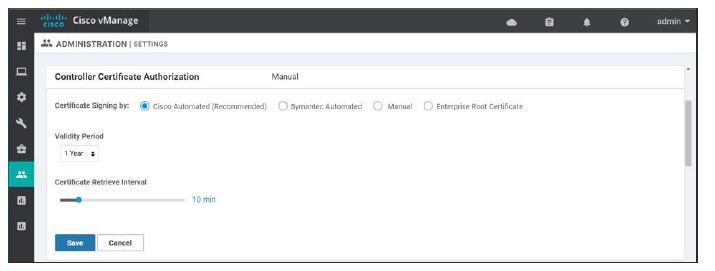
Option 4 > Manual certificate signing through Cisco Systems
One can also get the certificate signed from Cisco via Smart account manually (incase of vManage is isolated from internet & not reachable to Cisco PnP server). To do this, user has to generate the CSR request and paste the content of CSR on PnP portal under certificates > generate certificate tab. Once the content is pasted, provide appropriate name/validity/description and click on submit. Download the signed certificate and install it back on the vManage controller.
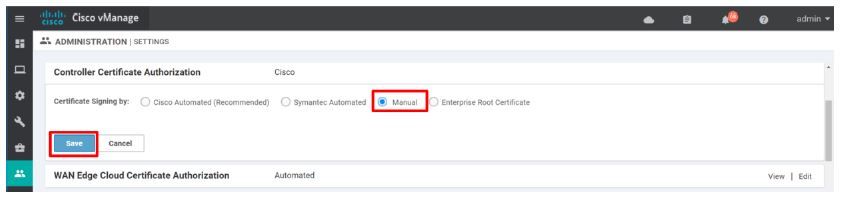
option 5 > Enterprise Root Certificate Authority (CA)
User can also get the certificate signed by the internal Root CA if they have one. For this, one has to first install the Enterprise Root CA chain (.pem) file on the vManage and also have to set the CSR properties manually on the vManage controller. This Root CA Chain will be automatically distributed by vManage to other controllers on the fabric.
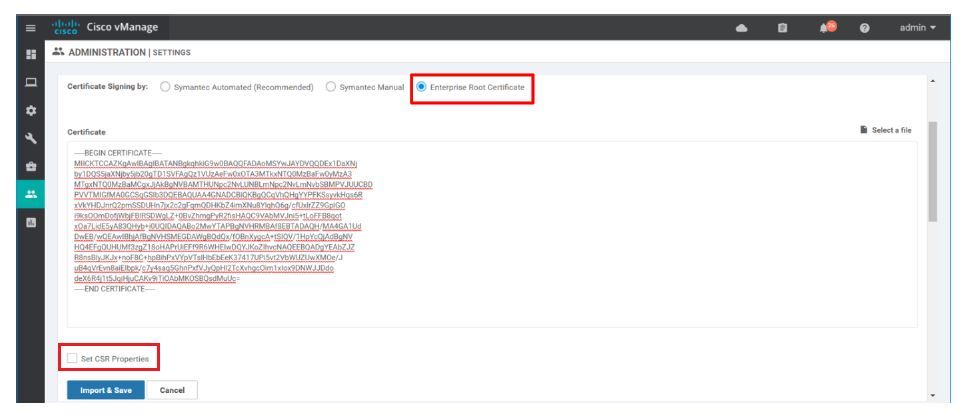
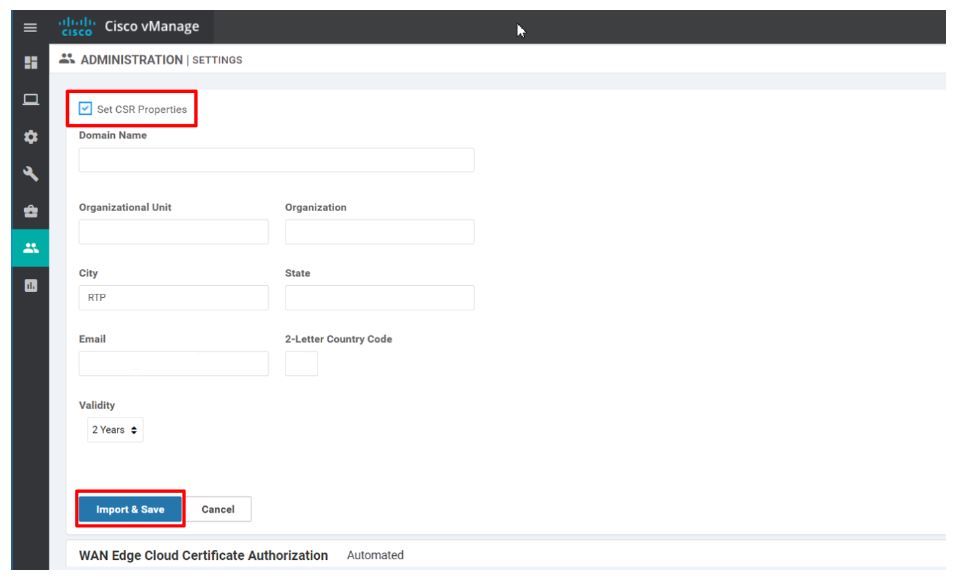
Once user has installed the Root CA chain on the vManage controller, now you can simply generate the CSR request for the controllers/edges, get it signed by your Root CA and install it back on the controller like any other method.
I hope you find this information useful and it helps you in some or the other way. In my next blog, we shall talk about how to get the serial.viptela whitelist for your Network.
Happy Blogging!!!!
Cheers!
Regards,
Rajiv Yadav
