- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- How to SDA Host Onboarding with ISE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-19-2020 04:48 AM - edited 02-25-2020 07:49 AM
Introduction
Host Onboarding is the term used when connecting an endpoint (hosts , IOT , Other devices) to the fabric , and can be accomplished in a couple of ways.
One option is the "static" approach as oppose to the dynamic and secure approach using Identity Services Engine (ISE) based on Authentication and Authorization.
With this approach we dynamically assign the endpoint to a VN as well as assigning it a Scalable Group Tag (SGT) providing us with Macro and Micro Segmentation.
In this document we will provide a step by step example how to Onboard an endpoint to the fabric using ISE.
This document assumes you have a fabric already up and running with VNs, IP Pools, SGTs, and AAA settings in place. This document will not focus on these steps.
Requirements
- When writing this doc the following was used.
DNAC 1.3.1.4
ISE 2.6 Patch 1 - Cisco DNA Center with ISE integration
How To Cisco DNA Center ISE Integration - VNs, SGTs, IP Pools, Authentication Template
Cisco DNA Center Deployment Steps
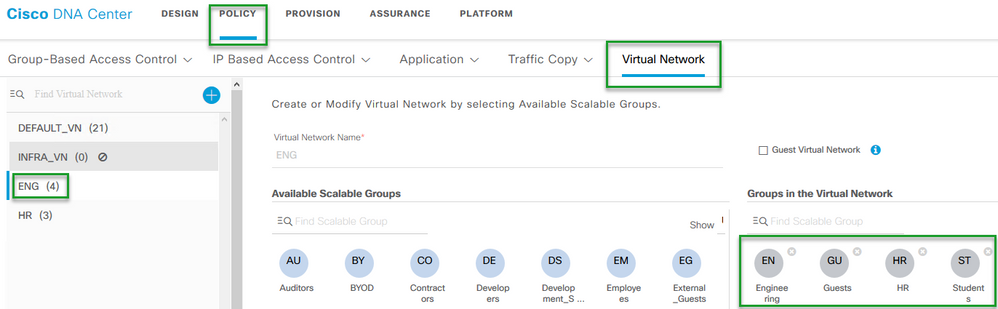
- Create the VN . This will be achieved under Policy > Virtual Network
In this example we have we created a VN named "ENG" - Assign SGTs
In this example we have added a few SGTs - Engineering, Guests, HR, Students
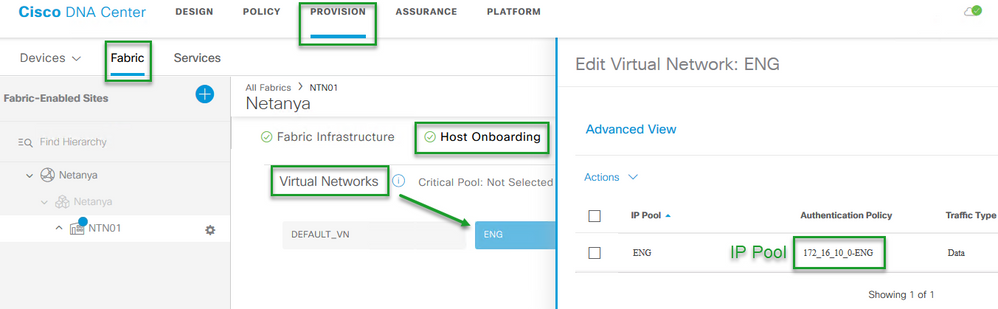
- Navigate to Provision > Fabric and choose the Fabric you created , Then choose "Host Onboarding"
You will see the VN that was created in previous steps
Assign IP pool to VN
We have reserved an IP pool of 172.16.10.0 and assigned it to "ENG" VN
NOTE:When adding the IP Pool to VN it is important to understand the significance of the name created by SDA and why there is an option to actually modify that name. This is out of the scope of this document but you can find the explanation in the following document:
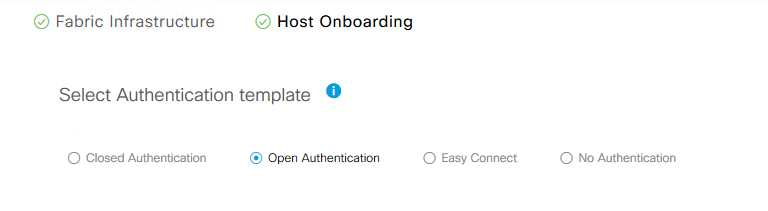
SDA-Access Authentication Policy Naming Best Practice - The Authentication Template chosen in this example is "Open Authentication" which is in the upper part of "Host Onboarding".
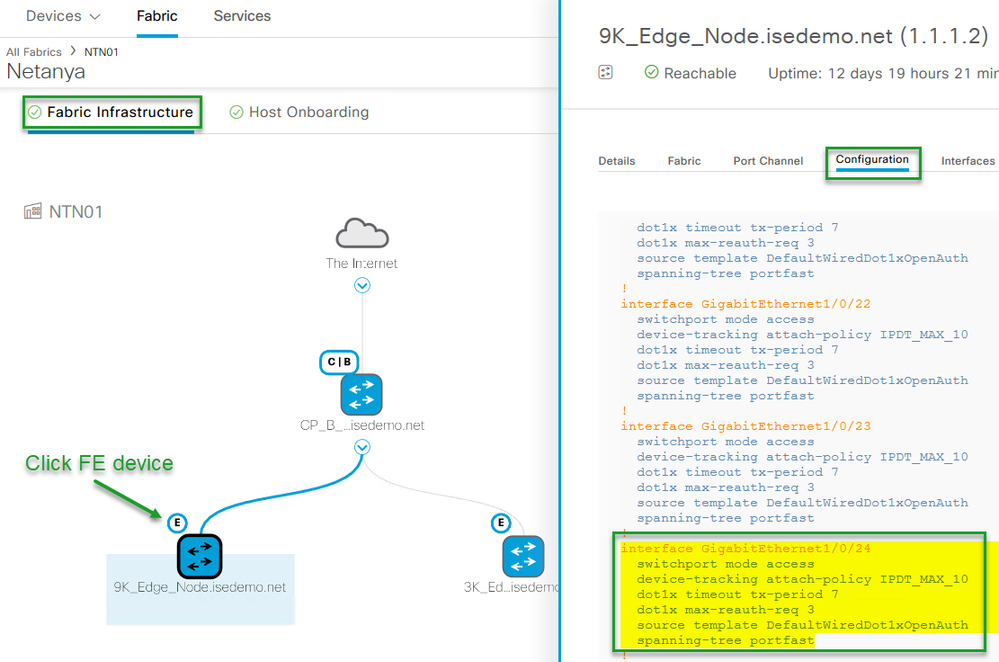
To check the actual configuration the template applies at the port level we can navigate in Cisco DNA Center to
Fabric Infrastructure , and click on the Fabric Edge device at which time a slide in window will appear with information regarding the specific Edge device. Click on "Configuration" to see the device configuration.
The Cisco DNA Center section is complete and in this next section will show the steps needed in ISE to accomplish dynamic Onboarding.
ISE Deployment Steps
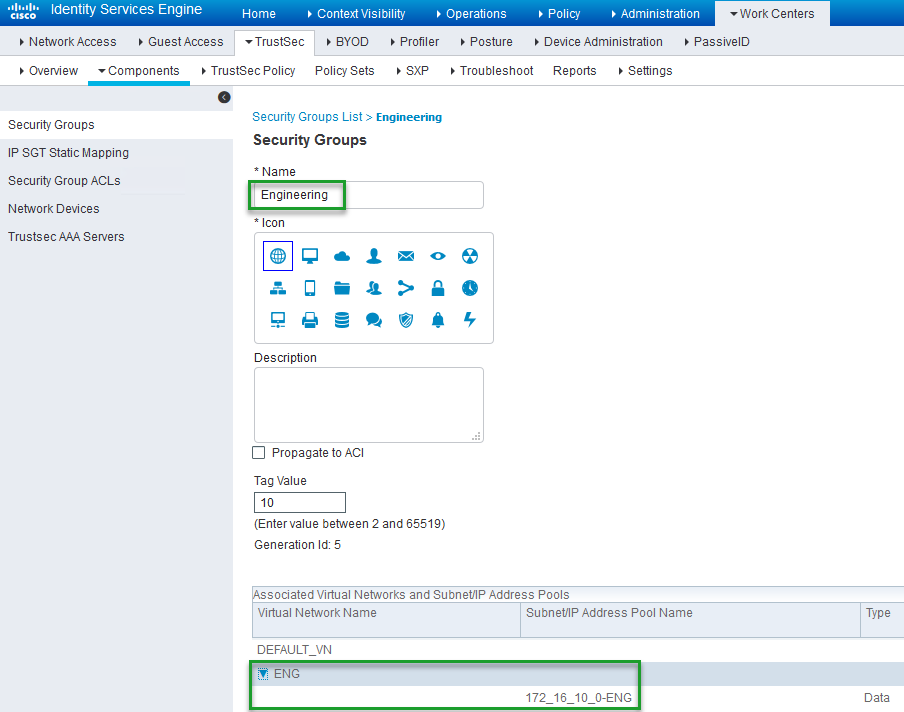
The way ISE interprets and views the VN and the IP Pool assigned to it , is by binding it to the SGT that was assigned to the VN, This can be seen in the diagram below under SGT "Engineering".
So lets take a quick look of the steps that were taken ,
- We created the VN (ENG)
- We assigned the SGTs to the VN (HR, Engineering, Guests, Students)
- We assigned an IP pool to VN (172_16_10_0-ENG)
So if for example we were to take a look at the SGT "Engineering" in ISE , we would see the VN "ENG" and the address pool that we assigned to it in Cisco DNA Center.
Navigate to Work Centers > TrustSec > Components > Security Groups (which is on the left hand side) and click on SGT "Engineering"
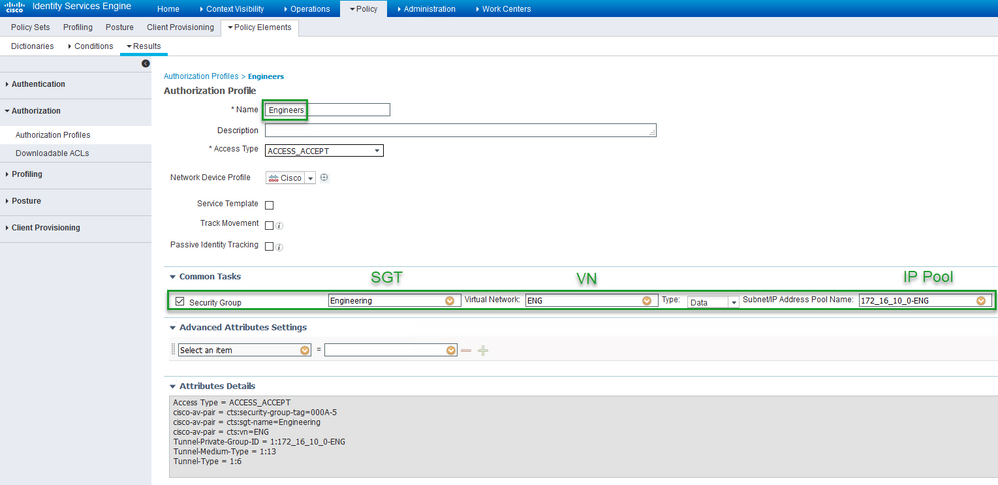
The next step is to create the "Authorization Profile" which is the Authorization that is applied once the endpoint is Authenticated and meets that Authorization Conditions.
- In ISE Navigate to Policy > Policy Elements > Results > Authorization (left hand side) > Authorization Profiles
- Click "Add"
- Will Name it "Engineers"
- Under "Common Tasks" we will check mark "Security Group"
- In the first field of "Security Group" we will choose the SGT "Engineering"
- Once the SGT is chosen an additional field will appear which is the VN field , We will chose VN "ENG"
- As soon as we choose the VN "ENG" the last field will appear , which is the "Subnet/IP Address Pool Name" at this stage we will choose the IP Pool Name "172_16_10_0-ENG" (Note:You may have multiple IP Pools in a single VN)
Your Authorization Profile should look like this.
We can now create the Authorization Policy and apply the Authorization Profile we created above (also known as the Rule)
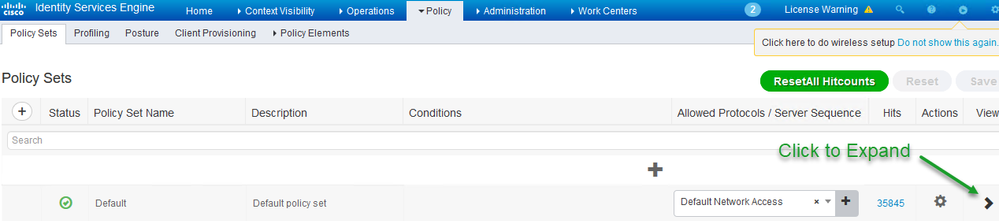
Note: We will not cover the Authentication Policy and we will use default Policy Set
- Navigate to Policy > Policy Sets and choose the "Default" just under it by clicking the arrow on the right hand side which will expand the Policy Set
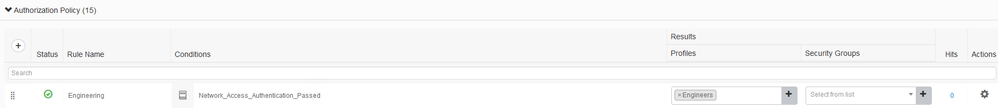
Click on "Authorization Policy" Policy to expand and create a new Authorization Policy Named "Engineering"
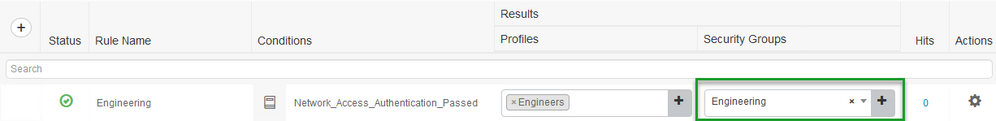
Your Authorization Policy should look like this:
Notice the "Security Groups" field is empty , this is because we already applied the SGT in the Authorization Profile so there is no reason to add it here.
But what if you did not want to assign an SGT to the endpoint and still have it assigned a VN ?
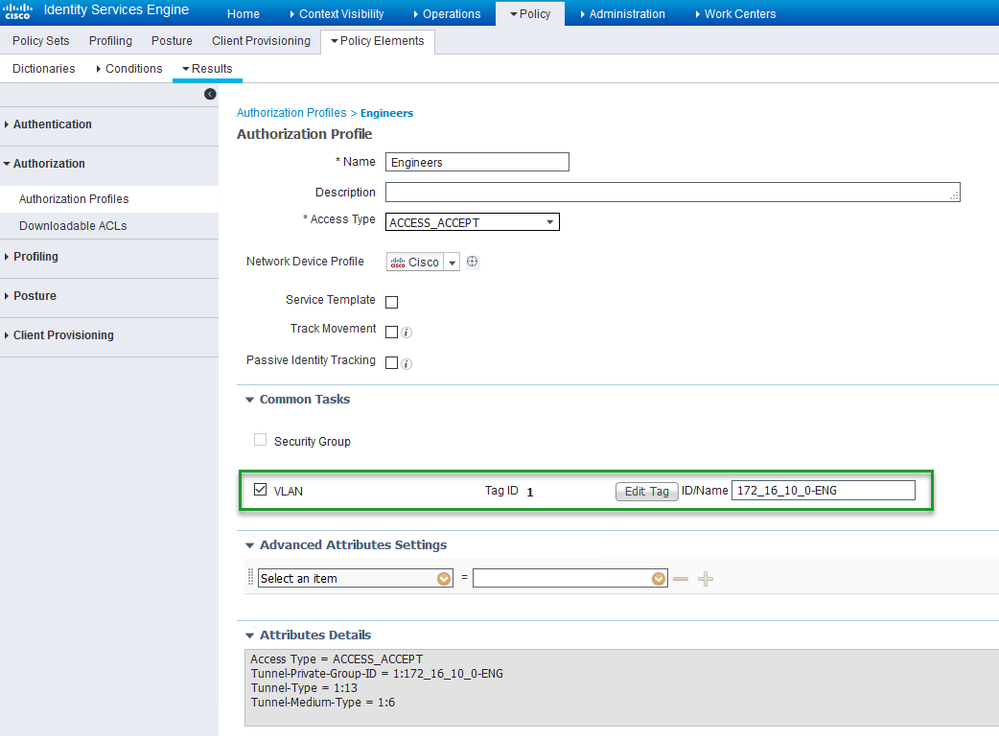
In this case you would use the "VLAN" option under "Common Tasks" in the Authorization Profile we previously created (Engineers) instead of "Security Group"
Which should look like this:
Make sure to enter the VN name correctly otherwise it will not work , best practice is to copy the VN name from the SGT section and paste it in the field.
You can then use that same Authorization Policy we created previously and if later you wish to start assigning an SGT while Onboarding the endpoint you can choose it from the "Security Groups" field in the Authorization Policy:
In this document you have learned how to dynamically assign a VN (Macro Segmentation) and an SGT (Micro Segmentation) while Onboarding an endpoint based on an Authorization Policy.
If you have any questions regarding this particular Document or would like to see other walk throughs that extend beyond this topic please let us know on our community page SD-Access Community
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How does this SGT/VN information get translated into VLAN ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@NAGISWAREN2 The VLAN is pushed in the Authorization Profile named "Engineers" as per the second to last screenshot above.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
So in ISE , I will create many authorization profile and each one include the specific parameters (VN name, SGT name , Pool name) and this parameters should match the names in the DNA
If i have Authorization profile 1 VN ENG SGT HR Pool name 172.16.1.1_HR
Authorization profile 2 VN ENG SGT Engineer Pool name 172.17.1.1_ENG
My question now
In the host Onboarding , If i have the two ports and there is 802.1x configuration but i need the first port when it successful authentication , take the authorization profile 1 and the second port take the authorization profile 2
so How the port know which authorization profile will use , If there is command under the port point to the name of the authorization profile to check it with ISE ?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: