- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Re: iBGP into OSPF
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2018 05:48 AM - edited 03-03-2019 08:51 AM
Hi,
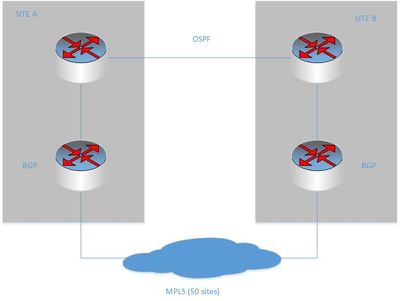
we have two core sites (OSPF) & 50 satellite sites (MPLS BGP)
I want to redistribute the BGP into OSPF so if the BGP router at site A (default data site) goes down, traffic from the MPLS will reach site A via site B (see attached pdf)
Now if I go to enter "bgp redistribute-internal" it has in brackets (dangerous) next to it which is quite alarming to say the least.
Is this just because there is the potential for BGP to dynamically inject networks eg by misconfiguration etc into the OSPF routes?
The MPLS network is a closed network although it is run by our ISP and our external access is via routers at site A & B.
So, is there any danger of redistributing BGP & OSPF to each other in this instance?
Solved! Go to Solution.
- Labels:
-
Other Networking
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2018 12:06 PM
It may be a little easier if Siates A & B were the same AS, but I assume you are already peering with the MPLS provider with Site A being AS 65000 and Site B being 65001. Here's an example below. It probably needs some tweaking and may be not be 100%, but it should give you an idea on how to accomplish things.
SITE A
!
router bgp 65000
neighbor 10.1.1.2 remote-as 65001
neighbor 10.1.1.2 description SITE_B
neighbor 1.1.1.1 remote-as 65555
neighbor 1.1.1.1 description MLPS_SITE_A
!
address-family ipv4
neighbor 10.1.1.2 activate
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 weight 100 (Prefer MPLS routes to remotes)
neighbor 1.1.1.1 route-map Prepend-Site-B out (Prepend Site B's routes)
neighbor 1.1.1.1 filter-list 5 out (Advertise only Site A & Bs routes)
neighbor 1.1.1.1 filter-list 10 in (Don't want to see Site B's AS)
neighbor 1.1.1.1 activate
network 10.10.10.0 mask 255.255.255.0 (Site A network)
!
!
!
ip as-path access-list 1 permit ^65001$
!
!
route-map Prepend-Site-B permit 10
match as-path 1
set as-path prepend 65000 65000 65000
!
!
ip as-path access-list 5 permit ^$
ip as-path access-list 5 permit ^65001$
!
!
ip as-path access-list 10 deny _65001$
ip as-path access-list 10 permit any
!
!
======================================================
SITE B
!
router bgp 65001
neighbor 10.1.1.1 remote-as 65000
neighbor 10.1.1.1 description SITE_B
neighbor 2.2.2.2 remote-as 65555
neighbor 2.2.2.2 description MLPS_SITE_B
!
address-family ipv4
neighbor 10.1.1.1 activate
neighbor 2.2.2.2 weight 100 (Prefer MPLS routes to remotes)
neighbor 2.2.2.2 route-map Prepend-Site-A out (Prepend Site A's routes)
neighbor 2.2.2.2 filter-list 6 out (Advertise only Site A & Bs routes)
neighbor 2.2.2.2 filter-list 20 in (Don't want to see Site A's AS)
neighbor 2.2.2.2 activate
network 20.20.20.0 mask 255.255.255.0 (Site B network)
!
!
ip as-path access-list 2 permit ^65000$
!
!
route-map Prepend-Site-A permit 10
match as-path 2
set as-path prepend 65001 65001 65001
!
!
!
ip as-path access-list 6 permit ^$
ip as-path access-list 6 permit ^65000$
!
!
!
ip as-path access-list 20 deny _65000$
ip as-path access-list 20 permit any
!
!
Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 04:09 AM
Hello,
Do the BGP routers at both sites advertise the same networks to the MPLS cloud, and how do the OSPF routers learn of the MPLS routes?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 08:56 AM
All four routers are configured with OSPF.
Each BGP router only advertises the networks behind it eg SITE A 10.1.1.0/24 & SITE B 10.1.2.0/24
SITE A communicates with SITE B with the dedicated link.
The routing between the OSPF routers is currently done statically but I would like to remove the static routes and advertise the BGP routes into the OSPF routes and vice versa so that the network can handle an outage at either of the BGP routers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 09:33 AM
The redistribution should work, it would probably be best to do it with route-maps and as metric type 1 routes. That's not to say there is the chance for sub-optimal routing.
However, doing IBGP on all four routers may be a better solution in that it allows greater flexibility and control of routing using BGP route weighting, local pref, etc.
Hope this makes sense and is of some help.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 09:51 AM
I was under the impression that you shouldn't use any BGP for internal routing and that OSPF/EIGRP are the preferred routing for this. The top two routers are the core sites and the BGP routers were only installed so that they could communicate with the private MPLS sites.
Now, if it's alright to use iBGP like this, it probably would simplify the whole thing for sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 10:08 AM
I agree with your assessment and the practice of having the BGP routers strictly for peering with the MPLS provider. However, the connectivity and topology described make the current static routes cumbersome and the need to either redistribute BGP into OSPF or run IBGP on all four routers. In the end one must ask is there much of a difference between redistributing BGP into OSPF or simply IBGP peering? In either case, proper filtering and controls allow only the needed advertisements as well as routing preferences, especially in the case of IBGP.
Also, if there was direct connectivity between the two BGP routers so that they could peer directly without having to go across the OSPF domain, redistribution or IBGP may not be needed at all. Might be some sticking points, but something to consider.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 10:43 AM - edited 07-31-2018 10:44 AM
Wow. Very valid points which I agree with too. If you try and "bgp redistribute-internal", Cisco mark it with (Dangerous!) which sets alarm bells ringing and the only reason I can think of that is due to the danger of rogue networks etc being introduced via BGP?
I didn't even consider the last point and the two BGP routers can communicate with each other via the direct link. Would it just be simply a case of entering another neighbor statement into each? The looking at the weights etc so that route is only used as a last resort?
We've only ever peered to the ISP routers and not to each other.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 11:22 AM
So I'm under the impression that the BGP routes from the MPLS provider are only your remote site networks and not Internet routes. If that's not the case, then things are a bit more complex. However, with proper filtering and controls it could still be done. Just not optimal from a security perspective.
Aside from that, if my original understanding was valid, if the BGP routers were to peer directly they would need a direct link. That is because if they peered across the OSPF domain, if there was a routing change, the OSPF only routers would not be aware and a routing loop would occur. That is why the suggestion to do IBGP with all four routers so all would be on the same page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 11:57 AM - edited 07-31-2018 12:01 PM
Yes, that is correct. Our internet breakouts are from both sites via FW's (not shown on image) but connected to the core switches (top left and right)
So the remote sites are private and have no breakout. We could do away with the OSPF although we do use it to inject our other remote sites (IPSEC) routes into the core but nothing that can't be overcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2018 12:17 PM
Keep in mind BGP relies on an IGP so it would probably be best to keep the OSPF. For example, if site A needed to go out the site B BGP router, it would rely on an internal route. I might be over simplifying it, but that's the basic premise. Also, if you were to do BGP with the four routers it would need to be a full mesh, in other words, each router would IBGP peer with each of the three other routers.
If you keep the OSPF, run IBGP between all four routers in the diagram and only allow the remote site routes to be advertised to the two other "inside" routers, you should be OK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2018 01:36 AM - edited 08-05-2018 01:38 AM
HI,
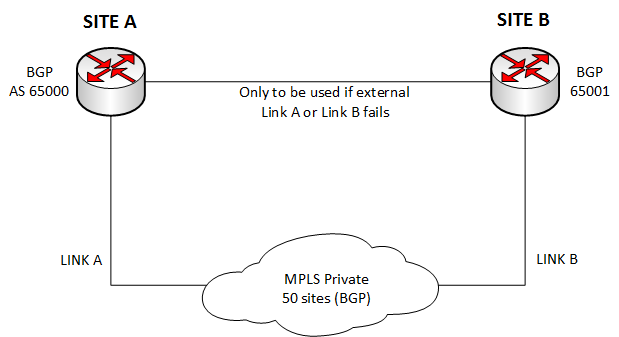
I really liked the idea of actually connecting the 2 BGP routers together using the 1gb link. Makes perfect sense.
How would you prevent traffic using the SITE A to SITE B link in normal use? I know you could use weights/local preference eg I know if i used a weight at SITE A, all traffic would flow to SITE A from the other sites but I wouldn't want SITE B to go directly to SITE A via PtP link.
We also have servers at SITE B which should not be reached by remote sites via SITE A BGP (in normal use)
Basically the PtP link between site A & B should only come into play if SITE A or SITE B external links fail.
Otherwise traffic should flow into SITE A or SITE B direct from the remote sites.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2018 04:27 AM
You influence the outgoing traffic from Site A & B using weights. Incoming you influence the MPLS provider using AS path prepending where as Site A advertises its routes normally and advertises the Site B routes with additional AS hops added (3 would do it) and the reverse at Site B for the Site A routes.
So sites A & B would be the preferred path for the respective sites outgoing and incoming. In the event of a provider link failure at a site, the alternate site would be the backup path.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2018 05:32 AM
Hi Chris,
you do make it sound simple which shows the level you are at. Poor old me is a fair bit below so if there's a chance you could go over it in a little more detail eg example, it would really be appreciated.
Your suggestions so far have really changed the way I was looking at the whole thing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2018 12:06 PM
It may be a little easier if Siates A & B were the same AS, but I assume you are already peering with the MPLS provider with Site A being AS 65000 and Site B being 65001. Here's an example below. It probably needs some tweaking and may be not be 100%, but it should give you an idea on how to accomplish things.
SITE A
!
router bgp 65000
neighbor 10.1.1.2 remote-as 65001
neighbor 10.1.1.2 description SITE_B
neighbor 1.1.1.1 remote-as 65555
neighbor 1.1.1.1 description MLPS_SITE_A
!
address-family ipv4
neighbor 10.1.1.2 activate
neighbor 1.1.1.1 activate
neighbor 1.1.1.1 weight 100 (Prefer MPLS routes to remotes)
neighbor 1.1.1.1 route-map Prepend-Site-B out (Prepend Site B's routes)
neighbor 1.1.1.1 filter-list 5 out (Advertise only Site A & Bs routes)
neighbor 1.1.1.1 filter-list 10 in (Don't want to see Site B's AS)
neighbor 1.1.1.1 activate
network 10.10.10.0 mask 255.255.255.0 (Site A network)
!
!
!
ip as-path access-list 1 permit ^65001$
!
!
route-map Prepend-Site-B permit 10
match as-path 1
set as-path prepend 65000 65000 65000
!
!
ip as-path access-list 5 permit ^$
ip as-path access-list 5 permit ^65001$
!
!
ip as-path access-list 10 deny _65001$
ip as-path access-list 10 permit any
!
!
======================================================
SITE B
!
router bgp 65001
neighbor 10.1.1.1 remote-as 65000
neighbor 10.1.1.1 description SITE_B
neighbor 2.2.2.2 remote-as 65555
neighbor 2.2.2.2 description MLPS_SITE_B
!
address-family ipv4
neighbor 10.1.1.1 activate
neighbor 2.2.2.2 weight 100 (Prefer MPLS routes to remotes)
neighbor 2.2.2.2 route-map Prepend-Site-A out (Prepend Site A's routes)
neighbor 2.2.2.2 filter-list 6 out (Advertise only Site A & Bs routes)
neighbor 2.2.2.2 filter-list 20 in (Don't want to see Site A's AS)
neighbor 2.2.2.2 activate
network 20.20.20.0 mask 255.255.255.0 (Site B network)
!
!
ip as-path access-list 2 permit ^65000$
!
!
route-map Prepend-Site-A permit 10
match as-path 2
set as-path prepend 65001 65001 65001
!
!
!
ip as-path access-list 6 permit ^$
ip as-path access-list 6 permit ^65000$
!
!
!
ip as-path access-list 20 deny _65000$
ip as-path access-list 20 permit any
!
!
Hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2018 01:21 PM
Superb Chris. Many thanks for your help with this. Really appreciated.
Louis
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide