- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Nexus L3 Design with Firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Nexus L3 Design with Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 03:13 AM - edited 03-03-2019 06:52 AM
Hello
I have a question with regards L3 design on a Nexus 7k talking to a pair of active/passive pair of firewalls. The main issue being the stateful nature of the firewall means that it will not accept asymmetric traffic flow. I have referred to this document and see the preferred option in figure 53
However as I said it is necessary for the traffic to enter and exit the firewall on the same interface. Therefore this option is not acceptable. Figure 59 shows a topology which would work, but I am concerned over the on going operational support of having this extra link between the 7K, if someone doesn't understand it's purpose and adds the routing VLAN across the peer-link in the future I can see the whole thing coming tumbling down.
To this end I have come up with another solution, which employs an external L2 switch to provide the "external" adjacency between the two 7k's, so I am not using the peer link for this purpose, and also allows the traffic flow to the firewalls to be symmetrical. A very simple diagram is shown below.
.
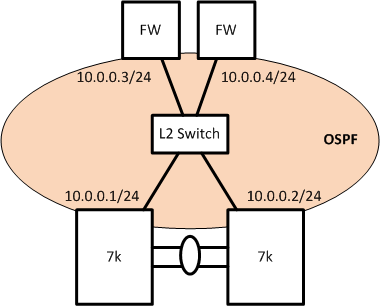
Can anybody tell me why this isn't a support configuration, or indeed ideally if it is a supported configuration?
Thanks in advance
Martin
- Labels:
-
Other Networking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 06:43 AM
This link has a good explanation of the issues involved.
See Diagram# 3B. This also recommends an inter-switch non-vPC link.
http://bradhedlund.com/2010/12/16/routing-over-nexus-7000-vpc-peer-link-yes-and-no/
A couple of disadvantages of your topology:
- The L2 switch now becomes a single point of failure. If it is fails then:
- Connectivity between the firewalls are lost.
- Connectivity from the N7Ks to the firewalls are lost.
- The N7Ks have several HA features built in such as dual supervisors, redundant power supplies, hitless IOS upgrades etc. In order to replicate these features on an equivalent L2 switch would be very expensive.
- Deploying another L2 switch is more expensive than deploying a couple of fibre SPFs for a non-VPC inter-switch link.
Don't forget to rate all posts that are helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 06:59 AM
Look what you can do add a 3750 stack of two switched for redundancy multi home the uplink of the switch to both N7K peers using vPC
Connect you firewalls to the 3750 stack and use l2 Vlans only in this switch as desired
Keep the layer 3 gateway service at the n7k using hsrp
Use static routing from the firewalls to point to the relevant hsrp VIP in the n7k of each Vlan
From n7k also use static routing to point to the active ip of the clusters firewalls as required
This simplify your design and also keep the redundancy level of device and traffic path as well
Hope this help
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 07:15 AM
@marwanshawi
Thanks for this, off course I meant a resilient L2 switch like a 3750X or even two L2 switches connected together, since they will only have L3 ports from both the Firewall and Nexus connected there would be no loop.
You state the preference for static routes to simplfy the design but the requirement I have is to run OSPF on the firewall, I can't see any issue with doing this, but are you saying this is a problem or a potential problem?
@Sean
As a side note, which I should have mentioned earlier, the firewall only has 1G interfaces so I believe I could get something cheap enough and still resilient to do this job. Although I agree it's unlikely to be as cheap as a couple of SFP and some fibres!
Thanks
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 09:05 AM
The problem is that ospf peering might happen over the vpc peer link and this is not supported design
Other options here is
use a separate l3 link as a point to point l3 for ospf peering between nexus switches
Or use none vpc Vlan over the vpc peer link for the ospf peering but the first option better and simpler
Hope this help
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 09:24 AM
Sorry I'm confused by why you would say it would use the peer link. If the interfaces to the L2 switch we configured as routed interfaces there would be no opportunity for OSPF to use the peer link
So I mean like this...
7Kswitch# config t
7Kswitch(config)# interface ethernet 2/1.10
7Kswitch(config-subif)# ip address 10.0.0.1/24
7Kswitch(config-subif)# encapsulation dot1Q 10
7Kswitch(config-subif)# ip router ospf 10 area 0.0.0.15
Hence my entire query.
Thanks
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2012 01:19 AM
Let's us know if your questions were answered !
Sent from Cisco Technical Support iPhone App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-03-2013 02:23 AM
Hi
Well my question wasn't really answered, I was just told to look at the information I already had.
Thanks
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2012 10:12 AM
I would recommend you to use the access switch in l2 only
And use l3 routing recommendations above also you can referee to the link posted in another post for l3 peering using dynamic routing in a vpc domain
Sent from Cisco Technical Support iPhone App
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
