- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- Basic ACL Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:09 AM
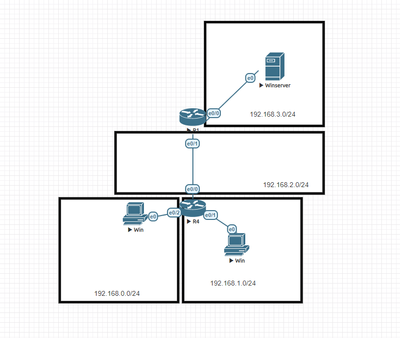
Hello everyone, I have an ACL question. Let's say in a given topology I have the following networks. My goal is i want to prevent telnet traffic to 192.168.3.0/24 network but allow http traffic
I'd put an ACL on the following interface R4 e0/0 such as: ip access-group in
with
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www
access-list 101 permit ip any any
I thought you had to put in a specific deny statement to filter telnet traffic and that access-list 101 permit ip any any would allow telnet to go through anyways since it would match all traffic.
A deny statement such as
access-list 101 deny tcp any 192.168.3.0 0.0.0.255 eq 23
Or would an implicit deny still take care of TCP traffic such as blocking telnet since I just put the ip any any statement to allow ip protocol traffic.
Hopefully this makes sense just trying to check my logic and see where it may be flawed. Also would that change the behavior if i did ip access-group out instead of in ?
Thank you in advance,
Solved! Go to Solution.
- Labels:
-
Access List
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:23 AM - edited 05-01-2021 10:58 AM
Hi,
If you will use only:
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www access-list 101 permit ip any any
Then telent traffic will be allowed because it will match the second statement. To deny only telnet and allow everything else (including HTTP traffic) you should use:
access-list 101 deny tcp any 192.168.3.0 0.0.0.255 eq 23 access-list 101 permit ip any any
If you want to allow only HTTP traffic and deny everything else then you should use
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www
Default deny statement will take care of the rest (you can add it if you want to make it visible in the config). Also, note that www means port 80 so traffic for HTTPs which is port 443 will be denied.
"Also would that change the behavior if i did ip access-group out instead of in ?" yes it would stop working properly because for out router will expect that source and destination is reversed in comparison to "in" for example
when you are using this with "in" command on R4 e0/1 it's ok:
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www
But if you would like to use "out" statement on the same interface then you should use:
access-list 101 permit tcp 192.168.3.0 0.0.0.255 eq www 192.168.0.0 0.0.1.255
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:15 AM
Do you like to allow the only HTTP? then you allow only HTTP rest all automatically deny
Your intention to block telnet and allow rest, then you need to deny and allow rest.
couple of examples :
https://www.cisco.com/c/en/us/support/docs/ip/access-lists/26448-ACLsamples.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:17 AM
Hi @ghofer
If your goal is just to deny telnet traffic then explictly deny telnet, followed by "permit ip any any". Example:-
access-list 101 deny tcp any 192.168.3.0 0.0.0.255 eq 23
access-list 101 permit ip any any
If you had a "permit ip any any" statement as per your initial example, then no implict deny would take place as all traffic is already permitted.
Yes the direction is important, generally traffic is filtered inbound on an interface.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:18 AM
That's what i thought. Someone was trying to tell me different. I thought you had to have the deny statements first and allow everything else. They seemed to be under the impression that ip any any was going to filter telnet because an implicit deny for TCP would take place. I thought without listing the specific deny statement for it then no filtering would take place.
Thank you for the quick reply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:23 AM
Sure it all depends on the use case. how you want to use it ACL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2021 10:23 AM - edited 05-01-2021 10:58 AM
Hi,
If you will use only:
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www access-list 101 permit ip any any
Then telent traffic will be allowed because it will match the second statement. To deny only telnet and allow everything else (including HTTP traffic) you should use:
access-list 101 deny tcp any 192.168.3.0 0.0.0.255 eq 23 access-list 101 permit ip any any
If you want to allow only HTTP traffic and deny everything else then you should use
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www
Default deny statement will take care of the rest (you can add it if you want to make it visible in the config). Also, note that www means port 80 so traffic for HTTPs which is port 443 will be denied.
"Also would that change the behavior if i did ip access-group out instead of in ?" yes it would stop working properly because for out router will expect that source and destination is reversed in comparison to "in" for example
when you are using this with "in" command on R4 e0/1 it's ok:
access-list 101 permit tcp 192.168.0.0 0.0.1.255 192.168.3.0 0.0.0.255 eq www
But if you would like to use "out" statement on the same interface then you should use:
access-list 101 permit tcp 192.168.3.0 0.0.0.255 eq www 192.168.0.0 0.0.1.255
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide