- Cisco Community
- Technology and Support
- Security
- Other Security Subjects
- Multi Site-Site VPNs question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:10 AM
Hi Guys,
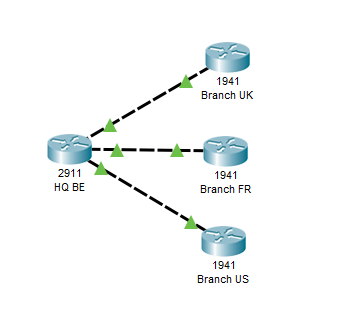
So I'm working on a proof concept in PT and learning a lot on the way! I just have a question regarding site-site VPNs, Is it at all possible to have a router at the HQ configured with multiple tunnels to various branches? (see image)
I know that the image depicts the branches being connected to the HQ on separate IP interfaces, but obviously in the real-world it would all be happening over a single interface on the HQ site, the internet connection of course. The problem is I know there is a limit of a single crypto map on a single interface...
Any ideas?
Thanks in advance for any advice!
Solved! Go to Solution.
- Labels:
-
Other Security Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:35 AM
Something like:
crypto map CRYPTO 10 ipsec-isakmp crypto map CRYPTO 10 match address FOO-01 crypto map CRYPTO 10 set peer 1.1.1.2 crypto map CRYPTO 10 set transform-set BAR-01 crypto map CRYPTO 20 ipsec-isakmp crypto map CRYPTO 20 match address FOO-02 crypto map CRYPTO 20 set peer 2.2.2.3 crypto map CRYPTO 20 set transform-set BAR-01 crypto map CRYPTO 30 ipsec-isakmp crypto map CRYPTO 30 match address FOO-03 crypto map CRYPTO 30 set peer 3.3.3.4 crypto map CRYPTO 30 set transform-set BAR-01 crypto map CRYPTO interface outside
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:20 AM
Hi there,
Yes, it is pretty stand configuration to have multiple VPNs terminated on a single interface. As you mention this would be achieved using a single crypto map with multiple sequences/ peers defined.
You should be able to mock it up in PT. Add a switch in bewteen all of the routers and have their 'outside' interfaces connected to a common subnet.
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:25 AM
Thanks for the reply, I figured there'd be a way to do this with a single crypto map...
Would you be able to provide a quick / simple example for how to configure "A single crypto map with multiple sequences / peers defined", is it done in a similar way to an ACL with multiple permit / denies?
Thanks,
Yanni
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:35 AM
Something like:
crypto map CRYPTO 10 ipsec-isakmp crypto map CRYPTO 10 match address FOO-01 crypto map CRYPTO 10 set peer 1.1.1.2 crypto map CRYPTO 10 set transform-set BAR-01 crypto map CRYPTO 20 ipsec-isakmp crypto map CRYPTO 20 match address FOO-02 crypto map CRYPTO 20 set peer 2.2.2.3 crypto map CRYPTO 20 set transform-set BAR-01 crypto map CRYPTO 30 ipsec-isakmp crypto map CRYPTO 30 match address FOO-03 crypto map CRYPTO 30 set peer 3.3.3.4 crypto map CRYPTO 30 set transform-set BAR-01 crypto map CRYPTO interface outside
cheers,
Seb.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 04:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 03:31 AM
You just change the sequence number. So you can have a single crypto map with 4 VPNs for example.
crypto map cm-cryptomap 100 ipsec-isakmp
...
crypto map cm-cryptomap 101 ipsec-isakmp
...
crypto map cm-cryptomap 102 ipsec-isakmp
...
crypto map cm-cryptomap 103 ipsec-isakmp
...
If these are routes and are all your own sites I would tend to use DMVPN/iWAN instead. Even using DVTI tunnel interfaces is likely to be easier. Using crypto maps seems so "old school" now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 04:03 AM
Thanks for the advice, I'll definitely research DMVPN for future consideration!
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-09-2019 04:10 AM
I'd agree with Phillip and go for DMVPN type solution using multiple Tunnel interfaces with IPSEC protection for each P2P (assuming that the remote peers dont want or dont have reachability with each other. You're going to get more flexibility with regards to routing, no encryption domain definition, etc....
ie..
!
interface Tunnel0
tunnel protection ipsec profile P2P-PROFILE
!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide