- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Duo SSO integration for Cisco vManage
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Duo SSO integration for Cisco vManage
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-08-2023 09:02 AM - edited 08-08-2023 09:03 AM
Has anyone implemented this integration with Duo SSO?
We use Duo's SAML connector with our on Prem IdP. I didn't see "Cisco vManage" as a protected application so I might just have to do a "Generic SAML Service Provider".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2023 09:21 PM
Hi
Sure! You can use Duo SSO - Generic SAML Service Provider and Cisco SD-WAN Security Configuration Guide
Now, there are a few caveats to this configuration that were spotted by some of our Senior Engineers, so I will share their findings:
As the vManage uses Group Membership of the user logging in via SSO to grant rights in vManage so the group membership must be passed via the "Groups" attribute and cannot contain extra text (like the full LDAP path you would get from AD).
There are a few pre-built groups in vManage, you can leverage those in your AD and sync them to Duo or create your own.
* If there is no group match, the user will be logged in with read-only privileges. There is no need to create a user first in vManage, any SAML authenticated user will be allowed in with either read-only or whichever privileges are assigned by their group.( enable Permitted Groups option in Duo and add only those groups of admins that must have this access to avoid undesired users)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-09-2023 09:25 PM - edited 08-09-2023 09:28 PM
About the Service Provider section in Duo… special attention to ACS and logout URL, make sure they include port 443 and login and logout in each parameter. You can take this info from the “download metadata option from the Manage configuration , but they should look like this:
Assertion Consumer Service = https://<ip address of vManage>:443/samlLoginResponse
Single Logout URL = https://<ip address of vManage>:443/samlLogoutResponse
NameID format = urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
Map attributes
|
IdP Attribute |
SAML Response Attribute |
|
<Username> |
Username |
Role attributes - the role names and group names will depend on your specific setup. The Service Provider's Role names must match the group names you wish to use in vManage (Administration > Manage Users > User Groups)
Attribute name: Groups
|
Service Provider's Role |
Duo groups |
|
vmanage_admins |
vmanage_admins |
|
vmanage_readonly |
vmanage_readonly |
Add all applicable roles you may be using.
Save this configuration and download the SAML metadata XML
+++
Now, we are going to upload the saved file in the Vmanage....
Before uploading :
- Open the Metadata XML file in your favorite text editor - this is to prevent an error when logging out of vManage
- At the bottom of the XML, find the two "md:SingleSignOnService" lines
- Copy those, paste them and rename the pasted values
- md: from SingleSignOnService to SingleLogoutService
- Location: from https://xxxx/sso to https://xxxx/slo
- The change should look something like:
- Save the XML file and be ready to upload to vMange
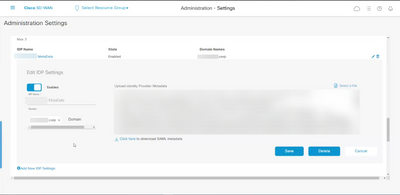
Cisco vManage Setup:
- In vManage, click Administration > Settings
- Look for Identify Provider Settings > Edit
- Click Enabled
- Upload (or copy/paste the text from) the XML Metadata file downloaded, and subsequently edited, from the Duo Admin panel
- Click Save
- Test by logging into to the admin interface by navigating to the vManage URL as normal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2023 07:49 AM - edited 08-14-2023 07:49 AM
Thanks so much for spending the time to write out all this. I'm making a change today for this I'll let you know the outcome!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2023 08:22 AM
You are welcome! Hope it was helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2023 01:25 PM
So the integration was unsuccessful, here are some of the things we ran into...so if you and the Engineer could guide us in the right direction it will be greatly appreciated. I'll try to give you as much info as I can along with letting our Duo reps know as well.
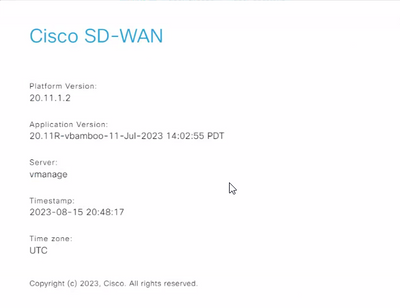
Cisco SD-WAN version (screenshot below)
Duo SSO / SAML Identity Provider:
I've setup the Protected app as a "Generic SAML Service Provider"
Assertion Consumer Service = https://<ip address of vManage>:443/samlLoginResponse
Single Logout URL = https://<ip address of vManage>:443/samlLogoutResponse
We just used the DNS names instead of IP addresses.
NameID format SAML:I. 1 : nameid-format: emailAddress
NameID attribute <Email Address>
Map attruibutes - this will be our custom claim we are using with our SAML IdP. UserName is another we are using for this.
On the Cisco SD-WAN vManage side, we shared our metadata to our Network Team and they uploaded it.
After added it has to Duo Central as an application and even tried as a bookmark, was still unsuccessful on logging in.
Checking our SAML tickets it's sending the right values along with the correct group claim it's expecting "netadmin" & "network_operations". Even with us being in the associated with those groups.
The Main Issue we are having:
We are having to pre-create users within vManage for this to work and having to add our domain.corp as well. After that has been done then users are able to login but that sort of defeats the purpose out of SSO / Groups Claims though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2023 08:40 PM
hi there! sorry for the delay getting back to you... Did you guys modified metadata before uploading it to the vmanage??
This part:
Before uploading to vmanage :
- Open the Metadata XML file from*Duo in your favorite text editor - this is to prevent an error when logging out of vManage-
- You need to go basically to the bottom of the text and locate these lines: "md:SingleSignOnService" (there are 2)
- Copy those, paste them and rename the pasted values ( Literally, just copy and paste just right after the lines)
- Once you have paste the, we are going to modify them... so substitute the next 2 sections that says :
*md: from SingleSignOnService to SingleLogoutService
and
*Location: from https://xxxx/sso to https://xxxx/slo
As you see we do this to specify the logout URLs .. It would not work with this..
one this has been modified, we save it and keep it to be uploaded later on in the vmanage metadata section.
I would delete and disable the current metadata y uploaded it again.
Let me know if that was the issue...
Good luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2023 07:12 AM
Yep, I edited the file before sending it to the network team to upload the metadata.
Just a side note for a possible feature request: If the data is filled out in the "Single Logout URL" field within the Protected app on Duo, then when exporting the metadata shouldn't those values be in the metadata? And not having to manually edit the metadata?
Also, having an import metadata feature within Duo SSO for a protected app would be amazing!
Anyways, just an update, we did end up getting this to work, sort of....
It prompts us with this login first, guessing it's because it can handle multiple IdP's? And that's why?
We have to enter our upn / samaccountname @domain.blahblah THEN it will direct us to vManage, wish there was a way to bypass it, but it works. And I appreciate your help very very much so!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide