- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- DUO SSO with ASA and DAP policies
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DUO SSO with ASA and DAP policies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2023 04:28 AM
Hi All
We are being forced by DUO to move away from our current LDAP method to SSO for MFA on the Cisco ASA.
Previously we had AD as the authentication method, then the secondary Auth pointed to DUO using LDAP, this worked fine and all the dynamic access policies were OK.
Now we have moved to DUO SSO and the DAP polices no longer work, in the new connection profile we created following DUO's guide, it doesn't have anything in for the secondary auth.
My question is, how will the ASA know where to pull the group attributes for the user in to apply the DAP policies with the new SSO method.
How do we solve this?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2023 06:24 AM
You have a few options...
Option 1: Use SAML for authentication (authN) but then also use LDAP for authorization (authZ)
In the connection profile you can point just the Authorization config item to an LDAP server. Someone from Cisco's sales org posted a video about this config here: https://www.youtube.com/watch?v=Ku0mvU9XS94
Option 2: Use Duo SSO generic SAML app to pass group info in the SAML response
It is possible to have Duo SSO send group information from your AD authentication source in the SAML response to the ASA. Unfortunately, our named Cisco ASA SAML application (https://duo.com/docs/sso-ciscoasa) doesn't include support for this.
Today, the best way to accomplish sending group info from AD via Duo SSO is to switch from that named Cisco ASA SAML application to our generic SAML app (https://duo.com/docs/sso-generic) and configure that Duo generic SAML app to send the group info you need from AD.
This will require reconfiguration at the ASA to update the SAML config on the ASA as the SAML entity ID, metadata, etc will change. You will also need to manually type in more information about the ASA service provider in Duo than you did during your original setup of SSO.
This is definitely something Duo Support can help you with 1:1.
Option 3: Don't use Duo SSO
While moving to Duo SSO provides the richest authentication experience for your users and permits use of our more advanced posture and risk-based auth features, it isn't your only option here. Just want to mention that you could also have migrated your LDAPS config to RADIUS via an on-prem Authentication Proxy, and added Duo RADIUS secondary auth after your existing AD primay auth AAA server. However, this configuration does not provide any way for users to experience the web-based Duo authentication prompt.
If you wish to use Duo in a configuration with a similar authentication scheme as you had before, where the ASA is able to pull the group info via your AD AAA server and Duo is the secondary authentication server, and you are happy with a automatic Duo push experience for your users, here are those instructions: https://duo.com/docs/ciscoasa-radius-duo-only
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2023 06:41 AM
Hi There
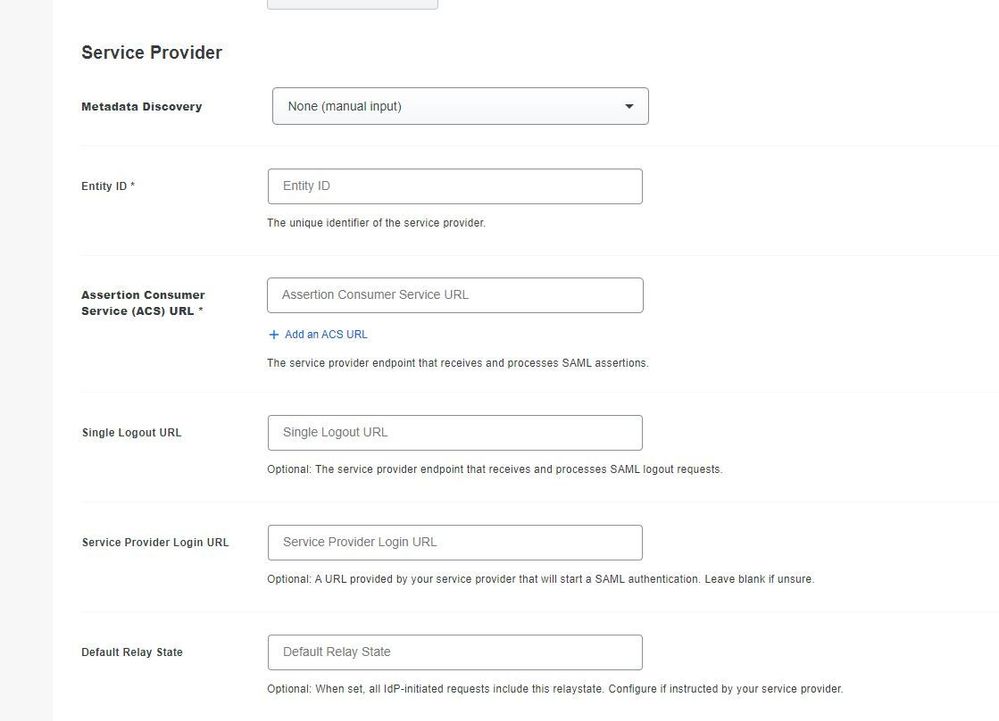
Has anyone set up the Generic SAML SSO on Duo instead of the ASA App which does not pass group info? We use Azure as the Idp.
There are some fields on there, shown below, I am not sure what we populate in them? should this be from Azure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2023 02:03 PM
Those field values should come from the ASA's SAML metadata. With the named Duo ASA SSO application (which doesn't send the groups) we can populated the values based on the base URL and tunnel group name provided.
Looks like the command to show the metadata on the ASA is show saml metadata <idpname>. after you complete the SSO Server config on the ASA from here. The output of that show command should contain the Entity ID, ACS, etc. for your ASA device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2023 10:12 AM
We send AD group info via on On-Prem IdP send group info to Duo via the SAML connector and take advantage of the Bridge Attributes within the Duo Admin Panel. You have to do some funky RegEx gymnastics on the IdP side but it is possible.
Note: Have have Duo Proxies on Prem as well.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide