- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Re: How to use Duo with Cisco TACACS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to use Duo with Cisco TACACS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2016 02:33 PM
What is the recommend way to configure Duo with Cisco TACACs running on Linux?
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scftplus.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2016 10:43 AM
Hi Al,
Our Sales Engineers have gotten this working before with a Cisco ISE via the following process. Please let us know if this works for you and we can look into making some documentation public in our KB:
-
Log in to the Duo Admin Panel and navigate to Applications.
-
Click Protect an Application and locate RADIUS in the applications list. Click Protect this Application to get your integration key, secret key, and API hostname. See Getting Started for help.
-
Install the Duo Authentication Proxy
-
Configure the Proxy:
[ad_client]
host=1.2.3.4
service_account_username=duoservice
service_account_password=password1
search_dn=cn=Users,dc=example,dc=com
[radius_server_auto]
ikey=■■■■■■■■■■■■■■■■■■■■
■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
api_host=■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=
radius_secret_1=thi■■■■■■■■■■■■■■■■■■■■
client=ad_client
port=1812
failmode=safe -
Start the Proxy by running: net start DuoAuthProxy
-
Login to Cisco ISE
-
Now change your Authentication Policy to use the External Identity Source you created for Duo. This is done under Work Centers > Device Administration > Device Admin Policy Sets.
-
Now configure the network device to talk TACACS+ to the Cisco ISE server. The key thing with the commands is that the authentication timeout for the network device is configured for 60 seconds. The default is 5 seconds.
Run the following:
tacacs-server login-timeout 60
tacacs-server host 10.10.1.1 timeout 60
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2017 08:57 PM
I understand how to configure Diagram 1 but I am having difficulty figuring out how to configure Diagram 2 on the Cisco ISE side. Do you have any documentation you can refer me to?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 07:41 AM
Hey Kirk,
We do not have any tested or supported TACACS documentation, as you’ve found, but we do have an internal guide that may be useful for your circumstances. Please be aware our Support Team will not be able to help you troubleshoot this configuration if you have issues.
Here is the guide for your reference:
Duo-CiscoACSISEGuide.pdf (943.7 KB)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2017 08:44 AM
Thanks for the guide, that looks like it is using the same workflow as Diagram 1. I will continue to use that method till I have more time to look into it, since it is working. Thank you for providing what resources you have available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2017 02:11 PM
With this setup are you able to do multi factor authentication? We use ISE and I am playing around with the auth proxy but I have it before ISE and I have not been able to get it to work. I do see attempts in ISE and there are entries in the auth proxy log. I am getting this in the log [RadiusClient (UDP)] dropping packet from 10.200.1.30:1812 - response packet has invalid authenticator.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2017 03:20 PM
It works great. Basically you use the Duo rule for both 2fa and ad auth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2017 03:36 PM
Would you mind sharing some of your config information? What kind of account do I need to get the AD part working?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-03-2018 08:37 AM
Adding the 60 second timeout wiped out our shared key and broke TACACS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2018 12:38 PM
Any notes on how to use Tacacs+ free Tacacs server with Duo?
http://tacacs.net/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 06:55 AM
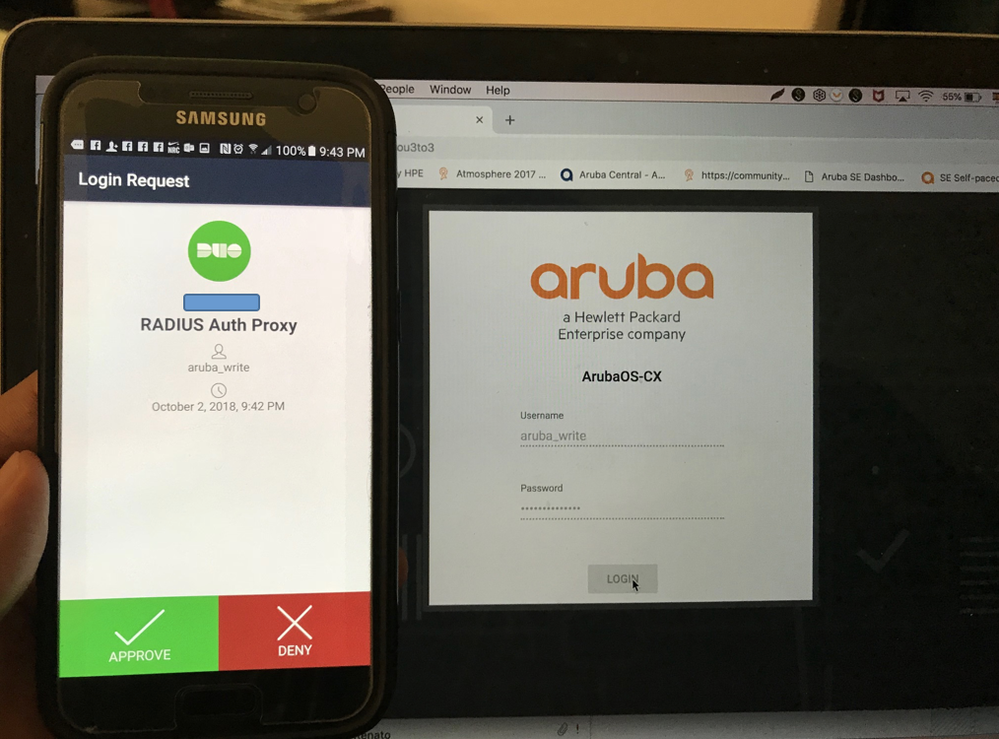
Clearpass can be used, here you will find the details: From zero to demo - Clearpass, DUO and 2FA
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide