- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: Cisco RV-325 Access Rules are not restricting Port Forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco RV-325 Access Rules are not restricting Port Forwarding
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2020 05:19 AM - edited 09-18-2020 05:43 AM
There are a couple older postings (https://community.cisco.com/t5/small-business-routers/port-forwarding-on-rv320-bypasses-firewall-rules/td-p/2601764) on this subject which I have not found to be useful today.
I have an RV325 Cisco Small Business router, Firmware Version:v1.5.1.11 (2020-05-28, 21:27:51).
I'm having problems understand and/or implementing Access rules for transferring WAN2 traffic for a specific port to an internal device/server.
- If I create a Service for TCP port 9999 going to port 9999 and then create an Access Rule using that Service to send any WAN2 traffic arriving with that port number to internal address 10.0.0.50. For that configuration, no traffic reaches the device at 10.0.0.50.
- if I also create a Forwarding rule using the same Service to the same device address (10.0.0.50), it works. But the port 9999 traffic is not being restricted to only WAN2, it also works from WAN1!! It appears that the Access Rule is being ignored.
- I have found some older references which suggest that one needs a DENY rule, right after the ALLOW Access Rule, which specifies ANY instead of WAN2. I've tried that without success.
Can anyone comment on what I'm doing wrong or how to solve this problem?
Thanks....RDK
- Labels:
-
Routers
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2020 01:46 AM
same here, the router firewall is a shame on Cisco; access rule and port forwarding is unreliable. Trying to bypass the firewall using DMZ also give another headache here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 01:51 AM
Hello Athanz,
We are sorry to hear about your bad experience with the product. Can you please explain in more details how did you configure the firewall (bypass it) and used the DMZ host? Access to the DMZ host from the Internet can be restricted through the Firewall.
Configuration guides of how to configure RV325 access rules and DMZ are available in the following links:
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 01:32 AM
Hello,
Your configuration should work fine and you have to have a Deny rule in place which deny all traffic except WAN2 reaching your internal address. Can you please share/send your forwarding and access rules configs so we can double-check if all is configured correctly?
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2020 08:13 AM
Martin...I'd be happy to send screen shots of those items. I'm a bit out-of-pocket right now without access to the rv-325, but should be able to get to this in a couple days....RDK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2020 10:34 PM - edited 09-26-2020 11:13 PM
Martin...This is a summary of the information in the attached Word document. The figures are also in that document. Thank you for any assistance you might have in this matter....RDK
Notes on my issues with Firewall Access Rules and Forwarding Rules
Scenario 1: Access Rule allowing Swann System service to device at 10.0.1.12
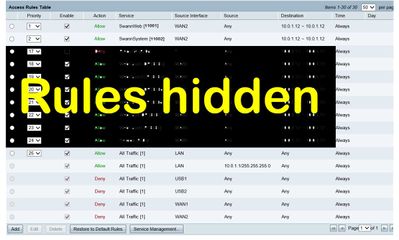
a..Figure 1 shows the Access Rule page, with extra rules blocked out.
Figure 1
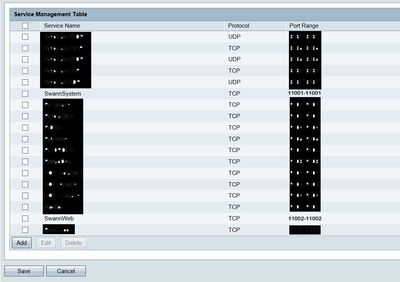
b..Figure 2 shows the Services page with extra services blocked out.
Figure 2
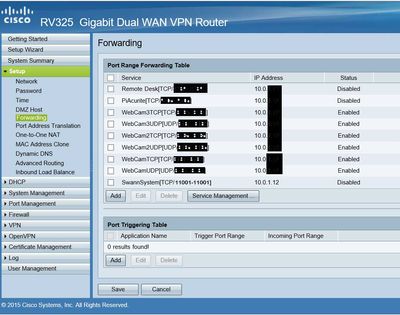
C..Figure 3 shows the “Forwarding” rules page with the Swann System rule disabled
Figure 3
Result: No traffic reaches the device at 10.0.1.12
Scenario 2: Forwarding rule only
a..Disable the Access Rule for Swann System in figure 1.
b..Enable the Swann System rule in Figure 3 (“Forwarding” rules page)
Result WAN2 traffic for this port reaches the device at 10.0.1.12. BUT, WAN1 traffic for this port also reaches the device at 10.0.1.12. There is no source screening which is expected since the Access Rule is not active
Scenario 3: Forwarding rule and access rules enabled
a..Access rule as shown in Figure 1
b..Enable the Swann System rule in Figure 3.
Result WAN2 traffic for this port reaches the device at 10.0.1.12. BUT, WAN1 traffic for this port also reaches the device at 10.0.1.12. There appears to be no source screening by the Access Rule.
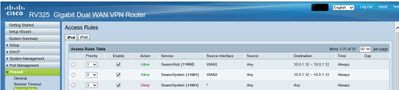
Scenario 4: Add a “deny” rule in the Access rules list which denies all traffic for the Swann System service to all other device
addresses
a..Modify The Access list table as shown in Figure 4
Figure 4
b..Enable the Swann System rule in Figure 3.
Result: No traffic reaches the device at 10.0.1.12
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2020 05:45 AM
Martin Aleksandrov....Have you had time to look into my RV-325 issue? Thanks...RDK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 01:09 AM
OK, It would appear that Martin is no longer interested in my problem
Can anyone help me with this issue?...RDK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 02:47 AM - edited 10-08-2020 02:50 AM
Hello RDK,
Apologies for my delayed response.
1. You must have port forwarding set up in either case. The problem with the RV32x is on the port forwarding settings you don't have the option to choose the source interface whether is WAN1, WAN2 or USB (like it is on the new 160/260/340 series) so this is the reason you will get the connection from WAN1 and WAN2. The other odd is that seemingly the RV32x does not create automatically access rule for the already configured port forwarding rule. Have you seen if when create the port forwarding you also get an access rule auto-configured on your RV access rules table?
2. My suggestion is to configure the port forwarding rules for your SwannWeb and SwannSystem services (like in figure 3) and if you don't have the access rules created automatically then set them up (like in figure 1) choosing the desired source WAN port you will be getting the connections (in your case WAN2). Then create another two deny rules for SwannWeb and SwannSystem services only with source interface WAN1 and destination 10.0.1.12 (not any).
Hope this will help.
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 06:09 AM
Martin....Many thanks for getting back to me. I have quickly tried your suggestion #2 and it seems to work. I will do further testing with other Forwarding rules later before I declare this the "Solution". I do not see any "Auto generated" access rules for any of my Forwarding rules. But, will verify that when I do more testing...RDK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-08-2020 06:52 AM
Hi there,
Nice to hear the things are going in the right direction and work fine. Basically, the issue comes from how the port forwarding is implemented and correlates with the FW access rules.
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2020 12:02 AM
Martin.....Your suggestions are working
For the PAT issue:
- I clicked on the PAT to create a new rule for Remote Desktop access. The default port is 3389 which I do not want to expose.
- I created a new Service, RDT2, which passes TCP port 11003 to 3389.
- Then I created the PAT rule using RDT2 service from the dropdown and pointed it to the internal computer address.
I tested this and it worked from WAN2 and I assume it would also work from WAN1.
Then I went to the Firewall Access Rules and tried to create a rule pair like I did for a Forwarding rule. However, I do not see the RDT2 service in the dropdown, thus I can not create a rule for my PAT. Am I missing something?
Thanks....Rob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2020 09:37 PM
Hello Rob,
The Service Management is used by both Firewall rules and PAT so once the service is being created it must appear for an option in the access rules and PAT. Try to recreate the RDT2 service, i.e. delete, save the config (if possible restart the RV) then create again the RDT2 service and see if this will fix the problem.
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-12-2020 04:57 AM
Martin....Here is a summary of many tries and reboots as I attempted to follow your suggestions. Not sure what I did differently last time to get the figures into my reply, oh well. You can view the whole with figures in the Word doc....RDK
Problem setting up Port Address Translation-Access Rules on RV-325
Note, I have tried this process several time with numerous router reboots, but the same results
1. Click on Setup and then Port Address Translation (PAT) from the RV-325 menu:
Figure 1
If I click on the dropdown to select a service, I get this display. Note the last entry “Dummy2”;
Figure 2
2. Now click on the Service Management button and note that this only shows the default rules, none of the Forwarding rules and not the “Dummy2” rule!
Figure 3
3. Click on the Add button and add as shown below and then Save
Figure 4
Save will return to the PAT page, Figure 1 in step 1 above.
4. Click on Add and then the dropdown. Note we see the default rules, no Forwarding rules and two PAT rules. The Dummy2 rule is left over from a previous attempt to configure PAT and cannot be deleted as it does not appear in the Service Management list. Rebooting the router has no effect
Figure 5
5. Select the RDT4 service, add the device address 10.0.1.11. and then Save.
Figure 6
6. Now from the RV-325 menu select Firewall and Access Rules. Note it only shows the default rules and the Forwarding rules(most blacked out). No PAT rules!! Thus, no Access rule could be created?
Figure 7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2020 11:13 PM
Martin...Have you had time to look into my PAT and Access Rule issue?.....RDK
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide