- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- RV180 port forwarding issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2014 09:06 AM
I wanted to forward a range of ports on a RV180, so I created a service for them, but when I go to the port forwarding page, it seems you have to enter an internal port number, which is a problem, because with a range you don't know what the incoming port was, and also you can't enter a range in the internal port field anyway. In the online help it mentions an option for this:
Forward to Port: Select Same as incoming port if the traffic
should be forwarded to the same port as of the incoming traffic or Specify
Port if the incoming traffic should be sent to one particular port.
Port Number: The port to which incoming traffic should be directed in
case specify port option is chosen.
But this option does not exist in the interface. There is only the internal port field. Surely this is an omission? If you can't forward a port range within a service you create, what's the point of allowing you to create it in the first place?
Solved! Go to Solution.
- Labels:
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 01:15 AM
Hi Matthew,
With RV180 we can have port range forwarding to the LAN. (tested and working)
Please follow this steps :
1. Under Firewall --> Advanced Setting --> Custom Services
2. Add the range of port and choose the Protocol Type (please if you have already single port forwarding in the range port please remove them)
3. Under Firewall --> Access Rules --> add the following rules
4. From WAN to LAN, Action : Always allow, Service : your service, Source:Any, Dnat: Private Server IP, Status : Enable, SAVE
--> Now if we want to check you can go to port forwarding we will see the rule added automatically and in the internal port is EMPTY --> please don't edit the rule of port forwarding otherwhise the router will expect to put the internal address
--> If we want to test (if you have the Router in test envirement and you don't have the server connected in the local) please follow this steps to confirm our configuration
0. Please install wireshark (Packet sniffer)
1. Under Administration --> Diagnostics --> Packet Capture
2. Select LAN and start to capture the traffic
3. From Client outside try to access to access with public IP with different port already configured for Access rule (from the browser publicip:port)
4. Stop the packet captures and downloaded
5. Open it with Wireshark and filter by "tcp.port==xx" you will there is the request coming to the LAN it means the firewall allow those port (xx:port number)
------------------------------
Here is a screenshots from my test : (I redirect range of port 70-80 TCP) to internal IP 192.168.1.100
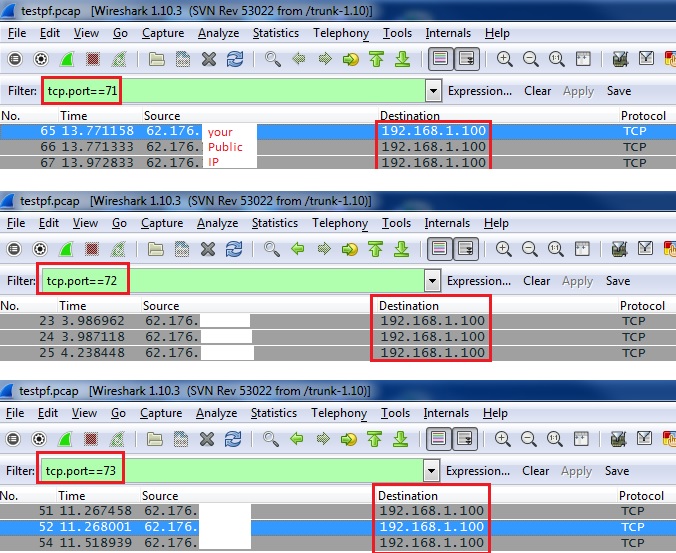
Please Rate this post or Marked as answered to help other Cisco Customers
Greetings
Mehdi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2014 12:14 AM
This seems to be bug CSCuc72086
Description—Port forwarding in regards to port range does not work.
Workaround—Use a single port instead of a port range.
As of firmware 1.0.4.14, this bug seems to remain unresolved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2014 06:46 AM
Just put an RV180 into service. Using the latest firmware (1.0.4.14) we still can't forward a RANGE of ports!!
It is hard to believe that the RV180 has now been on the market for years and Cisco still does not provide support for forwarding a range of ports.
PLEASE GET ON THIS CISCO!!!
This seems to be bug CSCuc72086
Description—Port forwarding in regards to port range does not work.
Workaround—Use a single port instead of a port range.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2014 10:13 PM
I am having this same issue. Did it ever get resolved?
DB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 01:16 AM
Hi Matthew,
With RV180 we can have port range forwarding to the LAN. (tested and working)
Please follow this steps :
1. Under Firewall --> Advanced Setting --> Custom Services
2. Add the range of port and choose the Protocol Type (please if you have already single port forwarding in the range port please remove them)
3. Under Firewall --> Access Rules --> add the following rules
4. From WAN to LAN, Action : Always allow, Service : your service, Source:Any, Dnat: Private Server IP, Status : Enable, SAVE
--> Now if we want to check you can go to port forwarding we will see the rule added automatically and in the internal port is EMPTY --> please don't edit the rule of port forwarding otherwhise the router will expect to put the internal address
--> If we want to test (if you have the Router in test envirement and you don't have the server connected in the local) please follow this steps to confirm our configuration
0. Please install wireshark (Packet sniffer)
1. Under Administration --> Diagnostics --> Packet Capture
2. Select LAN and start to capture the traffic
3. From Client outside try to access to access with public IP with different port already configured for Access rule (from the browser publicip:port)
4. Stop the packet captures and downloaded
5. Open it with Wireshark and filter by "tcp.port==xx" you will there is the request coming to the LAN it means the firewall allow those port (xx:port number)
------------------------------
Here is a screenshots from my test : (I redirect range of port 70-80 TCP) to internal IP 192.168.1.100

Please Rate this post or Marked as answered to help other Cisco Customers
Greetings
Mehdi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 03:55 AM
I have done this several times and also upgraded the firmware. It is still not working for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2015 10:57 AM
What was confusing me is that there are basically 2 related screens which on many routers are only one. If you want to forward a single port and maybe translate it as well, use the port forwarding screen. If you want to forward a range, use access rules. It's working for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 01:15 AM
Hi Matthew,
With RV180 we can have port range forwarding to the LAN. (tested and working)
Please follow this steps :
1. Under Firewall --> Advanced Setting --> Custom Services
2. Add the range of port and choose the Protocol Type (please if you have already single port forwarding in the range port please remove them)
3. Under Firewall --> Access Rules --> add the following rules
4. From WAN to LAN, Action : Always allow, Service : your service, Source:Any, Dnat: Private Server IP, Status : Enable, SAVE
--> Now if we want to check you can go to port forwarding we will see the rule added automatically and in the internal port is EMPTY --> please don't edit the rule of port forwarding otherwhise the router will expect to put the internal address
--> If we want to test (if you have the Router in test envirement and you don't have the server connected in the local) please follow this steps to confirm our configuration
0. Please install wireshark (Packet sniffer)
1. Under Administration --> Diagnostics --> Packet Capture
2. Select LAN and start to capture the traffic
3. From Client outside try to access to access with public IP with different port already configured for Access rule (from the browser publicip:port)
4. Stop the packet captures and downloaded
5. Open it with Wireshark and filter by "tcp.port==xx" you will there is the request coming to the LAN it means the firewall allow those port (xx:port number)
------------------------------
Here is a screenshots from my test : (I redirect range of port 70-80 TCP) to internal IP 192.168.1.100

Please Rate this post or Marked as answered to help other Cisco Customers
Greetings
Mehdi
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2014 01:15 AM
Hi Matthew,
With RV180 we can have port range forwarding to the LAN. (tested and working)
Please follow this steps :
1. Under Firewall --> Advanced Setting --> Custom Services
2. Add the range of port and choose the Protocol Type (please if you have already single port forwarding in the range port please remove them)
3. Under Firewall --> Access Rules --> add the following rules
4. From WAN to LAN, Action : Always allow, Service : your service, Source:Any, Dnat: Private Server IP, Status : Enable, SAVE
--> Now if we want to check you can go to port forwarding we will see the rule added automatically and in the internal port is EMPTY --> please don't edit the rule of port forwarding otherwhise the router will expect to put the internal address
--> If we want to test (if you have the Router in test envirement and you don't have the server connected in the local) please follow this steps to confirm our configuration
0. Please install wireshark (Packet sniffer)
1. Under Administration --> Diagnostics --> Packet Capture
2. Select LAN and start to capture the traffic
3. From Client outside try to access to access with public IP with different port already configured for Access rule (from the browser publicip:port)
4. Stop the packet captures and downloaded
5. Open it with Wireshark and filter by "tcp.port==xx" you will there is the request coming to the LAN it means the firewall allow those port (xx:port number)
------------------------------
Here is a screenshots from my test : (I redirect range of port 70-80 TCP) to internal IP 192.168.1.100

Please Rate this post or Marked as answered to help other Cisco Customers
Greetings
Mehdi
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide