- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: RV325 Login Issue After Upgrading to 1.4.2.15
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV325 Login Issue After Upgrading to 1.4.2.15
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-16-2017 06:00 PM - edited 03-21-2019 10:55 AM
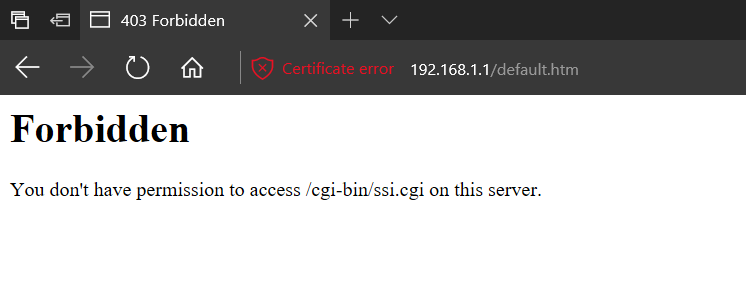
I am receiving a "403 Forbidden" error after upgrading my RV325 from firmware 1.3.2.02 to 1.4.2.15. It happens when I navigate to the admin web interface and enter the correct credentials to login. I have tried power cycling the router without success. The full error is:
Forbidden
You don't have permission to access /cgi-bin/ssi.cgi on this server.
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2018 12:43 PM
Well, it's working now for what I need so I'll have to see if it's also stable.
I'm hoping cisco won't let this router down. Again, it's my first experience
with this small router and was expecting something better... I cannot even
believe they released such a bad firmware which, if tested, couldn't even
pass the smell test.
Anyway, finger crossed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2018 03:09 PM - edited 01-29-2018 03:29 PM
Not good either (v1.3.2.02).
The vpn part of the RV325 (cli2gw / easyvpn) is unstable (client device - iphone/ios11).
Every time I connect with the iphone to the router, the iphone looses the vpn connection in few minutes (~20 mins) after witch, most of the times, the router refuses to establish any new connection.
The only solution I found is to reboot the vpn router, which is bad by definition.
Very disappointed with this device/firmware/support so far.
It's simply unstable which means not reliable which means wasted money and time.
PS: same iphone with openvpn client installed and connected to an ASUS router (Merlin firmware) on the same network of the RV325, it does not loose the connection for days (yes, 72+ hours).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 09:09 AM - edited 01-30-2018 01:39 PM
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2018 09:14 AM - edited 01-30-2018 02:01 PM
EasyVPN failure and corresponding router logs:
# SUCCESSFULL AUTHENTICATION:
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===? #1: [Tunnel Authorize Fail] RC5_R16_B64_CBC is not enabled for this connection. Attribute OAKLEY_HASH_ALGORITHM
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===? #1: [Tunnel Authorize Fail] MODP_2048 is not enabled for this connection. Attribute OAKLEY_GROUP_DESCRIPTION
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===? #1: [Tunnel Authorize Fail] DES_CBC is not enabled for this connection. Attribute OAKLEY_HASH_ALGORITHM
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===? #1: [Tunnel Authorize Fail] CAST_CBC is not enabled for this connection. Attribute OAKLEY_HASH_ALGORITHM
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===? #1: [Tunnel Authorize Fail] no acceptable Oakley Transform
2018-01-30, 16:10:23 VPN Log [grpips0][1] 0.0.0.0/0=== ...123.123.123.123===?: [Tunnel Disconnected] grpips0 instance with peer 123.123.123.123 {isakmp=#0/ipsec=#0}
2018-01-30, 16:10:23 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===? #2: [Tunnel Authorize Fail] received Hash Payload does not match computed value
2018-01-30, 16:10:23 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===? #2: [Tunnel Established] ISAKMP SA established
2018-01-30, 16:10:38 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===? #2: [Tunnel Established] received XAUTH ack, established
2018-01-30, 16:10:38 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===172.16.100.101/32 #2: [Tunnel Established] sent ModeCfg reply, established
2018-01-30, 16:10:39 VPN Log [grpips0]: cmd=up-client peer=123.123.123.123 peer_client=172.16.100.101/32 peer_client_net=172.16.100.101 peer_client_mask=255.255.255.255
2018-01-30, 16:10:39 VPN Log ip route add 172.16.100.101/32 via 128.178.43.1 dev eth1 metric 35
2018-01-30, 16:10:39 VPN Log iptables -t nat -I vpn -d 172.16.100.101/32 -j ACCEPT
2018-01-30, 16:10:39 VPN Log iptables -t nat -I vpn -s 172.16.100.101/32 -j ACCEPT
2018-01-30, 16:10:39 VPN Log iptables -t nat -I vpn_postrouting -d 172.16.100.101/32 -j ACCEPT
2018-01-30, 16:10:39 VPN Log iptables -t nat -I vpn_postrouting -o eth0 -s 172.16.100.101/32 -j ACCEPT
2018-01-30, 16:10:39 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===172.16.100.101/32 #3: [Tunnel Established] IPsec SA established {ESP=>0x00296d73 < 0xc96bd859 NATOA=0.0.0.0}
# CLIENT LOOSES CONNECTION:
2018-01-30, 16:58:26 VPN Log [grpips0][3] 0.0.0.0/0=== ...123.123.123.123===? #4: [Tunnel Authorize Fail] received Hash Payload does not match computed value
2018-01-30, 16:58:26 VPN Log [grpips0][3] 0.0.0.0/0=== ...123.123.123.123===? #4: [Tunnel Established] ISAKMP SA established
2018-01-30, 17:00:55 VPN Log [grpips0][3] 0.0.0.0/0=== ...123.123.123.123===?: [Tunnel Disconnected] grpips0 instance with peer 123.123.123.123 {isakmp=#0/ipsec=#0}
2018-01-30, 17:01:04 VPN Log [grpips0][2] 0.0.0.0/0=== ...123.123.123.123===172.16.100.101/32 #3: [Tunnel Negotiation Fail] DPD: Could not find newest phase 1 state
# ROUTER REFUSES NEW VPN CONNECTIONS (ios11 stuck with "connecting..." message):
2018-01-30, 17:02:28 VPN Log [grpips0][15] 0.0.0.0/0=== ...123.123.123.123===? #5: [Tunnel Established] received XAUTH ack, established
2018-01-30, 17:02:28 VPN Log [grpips0][15] 0.0.0.0/0=== ...123.123.123.123===? #5: [Tunnel Established] sent ModeCfg reply, established
2018-01-30, 17:02:45 VPN Log [grpips0][15] 0.0.0.0/0=== ...123.123.123.123===?: [Tunnel Disconnected] grpips0 instance with peer 123.123.123.123 {isakmp=#0/ipsec=#0}
We need a working firmware for this router:
*) easyvpn unstable
*) load balancing unstable
*) vlans do break access to management web interface (what the heck is this!)
an entire comunity has filed reports about these problems.
This router is currently useless for production environments, it should not even be sold!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2018 04:36 PM - edited 02-01-2018 04:51 PM
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2018 02:31 AM
I have two VLANs and both were enabled for device management. I signed into the RV320 using the other VLAN, disabled device management through the VLAN that was giving me trouble, saved, and then reenabled device management on the same VLAN and saved. That fixed the problem for me.
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide