- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: 4500X PBR problem on SVIs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
4500X PBR problem on SVIs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2018 07:55 AM - edited 03-05-2019 10:53 AM
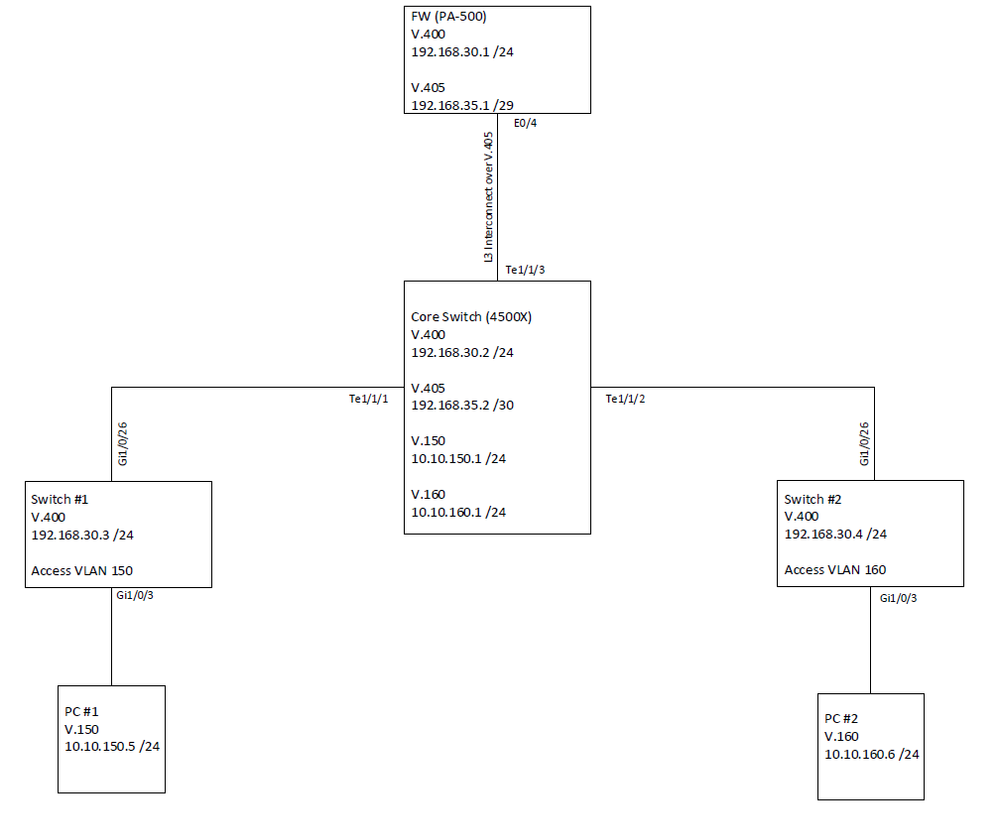
I have been trying to get PBR to work on a 4500x running entservices for the last few days in my lab before deploying into production. However, I am having problems getting PBR to work on the SVIs; local PBR is working as desired on the core. I did however get PBR to function properly on a 3750x running ipservcies. Below is the general setup:
I just noticed the subnet on the firewall for V405 and V405 on the core are marked as different subnets. I verified this in the config and both are /29. I just mismarked the diagram. (9-19-2018)
Vlan 400: MGT Plane for all switches
Vlan 405: L3 Interconnect between core and firewall
Vlan 150: User subnet 10.10.150.0 /24
Vlan 160: User subnet 10.10.160.0 /24
Desired traffic flow:
All traffic coming from any user IP address directed to a switch IP on vlan 400 needs to go through the firewall first. In addition, all traffic originated on vlan 400 such as syslog, ping and ntp need to go through the firewall; this part functions properly as the local PBR route-map on the core directs traffic from the core's vlan 400 to the firewall. Additionally the access layer switches direct their traffic to their default gateway of 192.168.30.1 (Firewall sub-interface).
Here is the PBR configuration that worked as intended on a 3750x but not a 4500x:
-----------------------------------------------
access-list 130 permit ip any 192.168.30.0 0.0.0.255
access-list 135 permit ip 192.168.30.0 0.0.0.255 any
route-map pcnm permit 300
match ip address 130
set ip next-hop 192.168.35.1
exit
route-map local permit 300
match ip address 135
set ip next-hop 192.168.30.1
exit
interface vlan 150
ip policy route-map pcnm
exit
interface vlan 160
ip policy route-map pcnm
exit
ip local policy route-map local
-----------------------------------------------
When issuing a show route-map I see matches on both policies. To help troubleshoot I issued a 'debug ip policy' on the core and received the following results:
Test1:
Ping from PBR-Core to PC#1: Traffic is routed through the firewall as expected
*Aug 30 15:52:41.361 MST: IP: s=192.168.30.2 (local), d=10.10.150.5, len 100, policy match route map local, item 300, permit
*Aug 30 15:52:41.361 MST: IP: s=192.168.30.2 (local), d=10.10.150.5 (Vlan400), len 100, policy routed local to Vlan400 192.168.30.1
*Aug 30 15:52:41.364 MST: IP: s=192.168.30.2 (local), d=10.10.150.5, len 100, policy match route map local, item 300, permit
Test2:
Ping from PC#1 to PBR-Core: Traffic is routed laterally and does not go through firewall; however PBR-Core sends ICMP reply back through firewall which is expected. What is not seen is a policy match for PC#1 (10.10.150.5) to PBR-Core (192.168.30.2). This traffic is defined in access list 130 but for some reason the inbound traffic on interface 150 does not check against the route-map.
*Aug 30 15:55:23.659 MST: IP: s=192.168.30.2 (local), d=10.10.150.5, len 60, policy match route map local, item 300, permit
*Aug 30 15:55:23.659 MST: IP: s=192.168.30.2 (local), d=10.10.150.5 (Vlan400), len 60, policy routed local to Vlan400 192.168.30.1
Test3:
Ping from PC#1 to Switch#1: No log appears on the PBR-Core showing inbound traffic against the route-map. However, the traffic is observed on the firewall and traffic to and from Switch#1 to PC#1 behave as desired.
What am I missing? My money is on one simple command that's needed on the 4500x. Thanks in advance.
- Labels:
-
LAN Switching
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 10:13 AM
Ok that makes sense.
Can you post the switch configs so we can see exactly what is setup.
Bear in mind with hardware switches that you do not always see hits on the acls so it is not always the best way to verify PBR.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 01:12 PM
Well I was hoping to find a way to attach this rather than paste it but I don't see a way. Here is the config for the switches:
---------------------------
Core Switch
---------------------------
no service pad
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
service compress-config
!
hostname PBR-Core
!
boot-start-marker
boot system bootflash:/cat4500e-universalk9.SPA.03.08.06.E.152-4.E6.bin
boot-end-marker
!
!
vrf definition mgmtVrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
logging buffered 4096
enable secret 5 **********
!
username !admin secret 5 ****************
no aaa new-model
clock timezone MDT -7 0
clock summer-time MST recurring
!
switch virtual domain 10
switch mode virtual
switch 1 priority 150
mac-address use-virtual
!
!
no ip source-route
no ip cef optimize neighbor resolution
!
ip domain-name pcn.local
!
!
vtp domain pcn.local
vtp mode transparent
!
!
!
power redundancy-mode redundant
!
mac access-list extended VSL-BPDU
permit any 0180.c200.0000 0000.0000.0003
mac access-list extended VSL-CDP
permit any host 0100.0ccc.cccc
mac access-list extended VSL-DOT1x
permit any any 0x888E
mac access-list extended VSL-GARP
permit any host 0180.c200.0020
mac access-list extended VSL-LLDP
permit any host 0180.c200.000e
mac access-list extended VSL-MGMT
permit any 0022.bdcd.d200 0000.0000.00ff
permit 0022.bdcd.d200 0000.0000.00ff any
mac access-list extended VSL-SSTP
permit any host 0100.0ccc.cccd
archive
log config
logging enable
logging size 200
notify syslog contenttype plaintext
hidekeys
!
spanning-tree mode rapid-pvst
spanning-tree portfast edge default
spanning-tree portfast edge bpduguard default
spanning-tree extend system-id
!
redundancy
mode sso
!
vlan internal allocation policy ascending
!
vlan 150
name V150
!
vlan 160
name V160
!
vlan 400
name V400
!
vlan 405
name V405
!
vlan 888
name HONEYPOT
!
vlan 931
name NATIVE
!
!
class-map match-any VSL-MGMT-PACKETS
match access-group name VSL-MGMT
class-map match-any VSL-DATA-PACKETS
match any
class-map match-any VSL-L2-CONTROL-PACKETS
match access-group name VSL-DOT1x
match access-group name VSL-BPDU
match access-group name VSL-CDP
match access-group name VSL-LLDP
match access-group name VSL-SSTP
match access-group name VSL-GARP
class-map match-any VSL-L3-CONTROL-PACKETS
match access-group name VSL-IPV4-ROUTING
match access-group name VSL-BFD
match access-group name VSL-DHCP-CLIENT-TO-SERVER
match access-group name VSL-DHCP-SERVER-TO-CLIENT
match access-group name VSL-DHCP-SERVER-TO-SERVER
match access-group name VSL-IPV6-ROUTING
class-map match-any VSL-MULTIMEDIA-TRAFFIC
match dscp af41
match dscp af42
match dscp af43
match dscp af31
match dscp af32
match dscp af33
match dscp af21
match dscp af22
match dscp af23
class-map match-any VSL-VOICE-VIDEO-TRAFFIC
match dscp ef
match dscp cs4
match dscp cs5
class-map match-any VSL-SIGNALING-NETWORK-MGMT
match dscp cs2
match dscp cs3
match dscp cs6
match dscp cs7
!
policy-map VSL-Queuing-Policy
class VSL-MGMT-PACKETS
bandwidth percent 5
class VSL-L2-CONTROL-PACKETS
bandwidth percent 5
class VSL-L3-CONTROL-PACKETS
bandwidth percent 5
class VSL-VOICE-VIDEO-TRAFFIC
bandwidth percent 30
class VSL-SIGNALING-NETWORK-MGMT
bandwidth percent 10
class VSL-MULTIMEDIA-TRAFFIC
bandwidth percent 20
class VSL-DATA-PACKETS
bandwidth percent 20
class class-default
bandwidth percent 5
!
!
!
interface Port-channel1
description "VSL Link from Switch 1"
switchport
switchport mode trunk
switchport nonegotiate
switch virtual link 1
!
interface Port-channel2
description "VSL Link from Switch 2"
switchport
switchport mode trunk
switchport nonegotiate
switch virtual link 2
!
interface TenGigabitEthernet1/1/1
description "Link to SW1"
switchport access vlan 888
switchport trunk allowed vlan 150,300,400
switchport trunk native vlan 931
switchport mode trunk
!
interface TenGigabitEthernet1/1/2
description "Link to Sw2"
switchport access vlan 888
switchport trunk allowed vlan 160,300,400
switchport trunk native vlan 931
switchport mode trunk
!
interface TenGigabitEthernet1/1/3
description "Link to FW"
switchport access vlan 888
switchport mode trunk
!
!
!
!
interface TenGigabitEthernet1/1/29
description ***VSL Link - Port-channel 1***
switchport mode trunk
switchport nonegotiate
no lldp transmit
no lldp receive
no cdp enable
channel-group 1 mode on
service-policy output VSL-Queuing-Policy
!
interface TenGigabitEthernet1/1/30
description "Dual-Active Detection"
dual-active fast-hello
!
interface TenGigabitEthernet1/1/31
description ***VSL Link - Port-channel 1***
switchport mode trunk
switchport nonegotiate
no lldp transmit
no lldp receive
no cdp enable
channel-group 1 mode on
service-policy output VSL-Queuing-Policy
!
interface TenGigabitEthernet1/1/32
description "Dual-Active Detection"
dual-active fast-hello
!
interface TenGigabitEthernet2/1/29
description ***VSL Link - Port-channel 2***
switchport mode trunk
switchport nonegotiate
no lldp transmit
no lldp receive
no cdp enable
channel-group 2 mode on
service-policy output VSL-Queuing-Policy
!
interface TenGigabitEthernet2/1/30
description "Dual-Active Detection"
dual-active fast-hello
!
interface TenGigabitEthernet2/1/31
description ***VSL Link - Port-channel 2***
switchport mode trunk
switchport nonegotiate
no lldp transmit
no lldp receive
no cdp enable
channel-group 2 mode on
service-policy output VSL-Queuing-Policy
!
interface TenGigabitEthernet2/1/32
description "Dual-Active Detection"
dual-active fast-hello
interface Vlan1
no ip address
!
interface Vlan150
ip address 10.10.150.1 255.255.255.0
ip policy route-map pcnm
!
interface Vlan160
ip address 10.10.160.1 255.255.255.0
ip policy route-map pcnm
!
interface Vlan400
ip address 192.168.30.2 255.255.255.0
!
interface Vlan405
ip address 192.168.35.2 255.255.255.248
!
ip local policy route-map local
ip default-gateway 192.168.30.1
no ip forward-protocol nd
no ip forward-protocol udp tftp
no ip forward-protocol udp nameserver
no ip forward-protocol udp domain
no ip forward-protocol udp time
no ip forward-protocol udp netbios-ns
no ip forward-protocol udp netbios-dgm
no ip forward-protocol udp tacacs
no ip http server
no ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 192.168.35.1
ip ssh time-out 10
!
ip access-list extended VSL-BFD
permit udp any any eq 3784
ip access-list extended VSL-DHCP-CLIENT-TO-SERVER
permit udp any eq bootpc any eq bootps
ip access-list extended VSL-DHCP-SERVER-TO-CLIENT
permit udp any eq bootps any eq bootpc
ip access-list extended VSL-DHCP-SERVER-TO-SERVER
permit udp any eq bootps any eq bootps
ip access-list extended VSL-IPV4-ROUTING
permit ip any 224.0.0.0 0.0.0.255
!
ip sla enable reaction-alerts
logging trap notifications
logging source-interface Vlan300
logging host ***
logging host ***
access-list * remark "SNMP RO Access"
access-list * permit *
access-list * deny any log
access-list * remark "VTY Access List"
access-list * permit *
access-list * deny any log
access-list * remark "NTP Server Access List"
access-list * permit *
access-list * deny any log
access-list 115 permit ip 10.10.150.0 0.0.0.255 192.168.30.0 0.0.0.255
access-list 130 permit ip any 192.168.30.0 0.0.0.255
access-list 135 permit ip 192.168.30.0 0.0.0.255 any
!
route-map pcnm permit 300
match ip address 115 130
set ip next-hop 192.168.35.1
!
route-map local permit 300
match ip address 135
set ip next-hop 192.168.30.1
!
ipv6 access-list VSL-IPV6-ROUTING
permit ipv6 any FF02::/124
!
no vstack
line con 0
session-timeout 10
timeout login response 15
logging synchronous
transport preferred none
stopbits 1
line vty 0 4
session-timeout 10
access-class * in
timeout login response 15
logging synchronous
login
transport input ssh
line vty 5 15
session-timeout 10
access-class * in
timeout login response 15
logging synchronous
login
transport input ssh
!
!
module provision switch 1
chassis-type 72 base-mac 006B.F156.9A00
slot 1 slot-type 402 base-mac 006B.F156.9A00
!
module provision switch 2
chassis-type 72 base-mac B838.6121.D748
slot 1 slot-type 402 base-mac B838.6121.D748
slot 2 slot-type 400 base-mac 4C4E.358C.F858
!
ntp access-group peer *
ntp server *
ntp server * prefer
!
end
PBR-Core#
------------------------------------------------------------
Switch #1 (Switch 2 is configured the same expect for IP and name)
------------------------------------------------------------
no service pad
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
!
hostname Switch-1
!
boot-start-marker
boot-end-marker
!
no logging console
!
no aaa new-model
clock timezone MDT -7 0
clock summer-time MST recurring
switch 1 provision ws-c2960x-24td-l
!
!
!
no ip source-route
!
!
ip domain-name pcn.local
vtp domain PCN.LOCAL
vtp mode transparent
!
!
!
!
archive
log config
logging enable
logging size 200
notify syslog contenttype plaintext
hidekeys
!
spanning-tree mode rapid-pvst
spanning-tree portfast edge default
spanning-tree portfast edge bpduguard default
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
vlan 150
name V150
!
vlan 400
name V400
!
vlan 888
name HONEYPOT
!
vlan 931
name NATIVE
!
!
!
!
interface FastEthernet0
no ip address
!
interface GigabitEthernet1/0/1
switchport access vlan 121
switchport mode access
spanning-tree portfast edge
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
description "V150 Access"
switchport access vlan 150
spanning-tree portfast edge
!
!
!
!
interface GigabitEthernet1/0/26
switchport access vlan 888
switchport trunk allowed vlan 150,400
switchport trunk native vlan 931
switchport mode trunk
!
interface TenGigabitEthernet1/0/1
!
interface TenGigabitEthernet1/0/2
!
interface Vlan1
no ip address
shutdown
!
interface Vlan400
ip address 192.168.30.3 255.255.255.0
!
ip default-gateway 192.168.30.1
no ip http server
no ip http secure-server
!
ip ssh time-out 10
ip ssh source-interface Vlan400
!
logging trap notifications
logging source-interface Vlan400
logging host *
logging host *
!
no vstack
!
line con 0
line vty 5 15
!
!
end
Switch-1#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 01:19 PM - edited 09-19-2018 01:29 PM
Here is a screen capture of a ping test from PC#1 to Switch #1 and Switch #2 according to the firewall logs (Image 1). As you can see the source information and destinations are in the correct order along with the application. There was no output from the Core when I used the 'debug ip policy' command.
(Image 1)
Next is a ping test from PC#1 to the Core switch (Image 2 & 3). With this test I got hits on the Core using the 'debug ip policy' but only for the return traffic from the Core to PC#1. Notice the firewall log source and destination zones are backwards along with the incorrect application. To me shows that the ping from PC#1 to the core is going laterally rather than going through the firewall as desired.
(Image 2)
(Image 3)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2018 12:10 PM
Bumping. I'm about to deploy another network with the similar architecture and need to get this problem figured out. I do remember that on the 3750X I had to modify the SDM template but was unable to find the same commands on the 4500X. Is there a way to modify the template?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2018 07:41 AM
can you share the output of the following command show sdm prefer
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2018 06:59 AM
Doesn't look like that command is available on the 4500X.
-Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2018 12:21 PM
Bumping in the hopes we can find a solution.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide