- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: 802.1x not working. PC can't get IP Address from DHCP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 03:22 AM - edited 05-28-2020 03:51 AM
Hello,
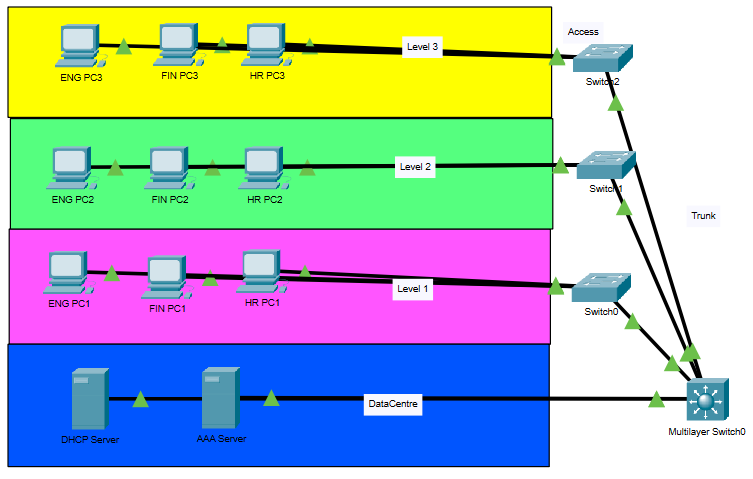
I am trying to get my AAA Server working with a DHCP Server on the same VLAN2 configured and assigned to a Layer 3 Multilayer Switch ports (g1/0/1-2) respectively. 3 Different Layer 2 switch are connected to the Layer 3 Multilayer Switch.
The layer 3 switch is configured with 5 VLAN, VLAN 123 (Engineering), VLAN 124 (Finance), VLAN 125 (HR), VLAN 2 (DHCP+AAA-Server) and VLAN99 (TRUNK NATIVE VLAN to the Layer 2 switch)
Routing
I managed to configure the DHCP server and host connected to Layer 2 switch on thier levels are able to receive their correct IP address from the DHCP server. I have issued to ip helper-address on the vlans so that they are able to receive DHCP message only from the DHCP Server.
I have included a packet tracer file which I have done.I can neither ping the PC or Multilayer Switch from the Level Switch (Switch0-2)
Solved! Go to Solution.
- Labels:
-
Catalyst Switch
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2020 02:22 PM - edited 06-12-2020 02:29 PM
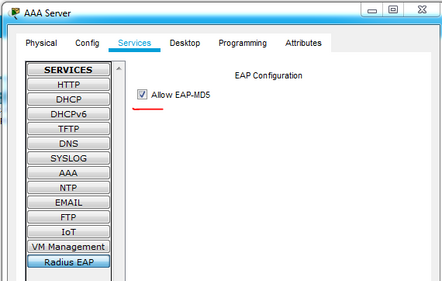
I don't know if you got it working but what we missed was check in box on AAA Radius EAP server plus small adjustments like IP of interface vlan 2 on Switch0 so that it can ping both servers. changed hostname Switch0 to SW1 and added Sw1 authentication info in AAA. see attached files
Regards, ML
**Please Rate All Helpful Responses **
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 08:35 AM - edited 05-28-2020 08:41 AM
Looks good; couple things: L2 switches should have manually assigned IPs for management access purpose from reserved IT Vlan subnet. Your L2 switches have the same IP of 192.168.0.1, all 3, for interface vlan 1. Of course, There should be no 2 devices with same IP on network anywhere inside the company.
Also, L3 sw does not have interface vlan1 up nor has IP assigned. Assuming that your IT department is on vlan 1 and in 192.168.0.1/24, once u add /change IPs , switches will be able to ping.
Using vlan 1 is not good idea for security; so u may want to change IT dept vlan to vlan 99.
Normally Regular PCs should not be able to ping L2/L3 switches anyway; such PC should be only designated IT PC to admin and mange switches/routers.
Regards, ML
**Please Rate All Helpful Responses **
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 08:58 AM - edited 05-28-2020 09:06 AM
Do check the attachment
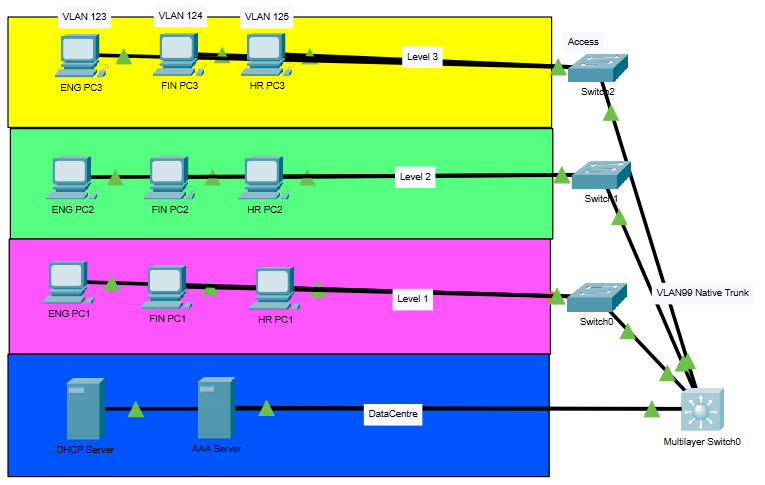
I have updated accordingly the Native VLAN now is VLAN99 on Switch0 and MLS. I have also set the SVI interface for VLAN 99 ip address to 192.168.99.11 at Switch0 and 192.168.99.1 the at MLS.
I am still not sure why I am unable to reach the other VLAN interface IP addresses or the PCs when I ping HR1 PC, DHCP and AAA server.
show run on Switch0
Building configuration...
Current configuration : 1822 bytes ! version 15.0 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname Switch ! ! ! ! ! aaa new-model ! aaa authentication dot1x default group radius ! ! ! ! ! ! ! dot1x system-auth-control spanning-tree mode pvst spanning-tree extend system-id ! interface FastEthernet0/1 switchport access vlan 125 switchport mode access authentication port-control auto dot1x pae authenticator ! interface FastEthernet0/2 switchport access vlan 124 switchport mode access ! interface FastEthernet0/3 switchport access vlan 123 switchport mode access ! interface FastEthernet0/4 shutdown ! interface FastEthernet0/5 shutdown ! interface FastEthernet0/6 shutdown ! interface FastEthernet0/7 shutdown ! interface FastEthernet0/8 shutdown ! interface FastEthernet0/9 shutdown ! interface FastEthernet0/10 shutdown ! interface FastEthernet0/11 shutdown ! interface FastEthernet0/12 shutdown ! interface FastEthernet0/13 shutdown ! interface FastEthernet0/14 shutdown ! interface FastEthernet0/15 shutdown ! interface FastEthernet0/16 shutdown ! interface FastEthernet0/17 shutdown ! interface FastEthernet0/18 shutdown ! interface FastEthernet0/19 shutdown ! interface FastEthernet0/20 shutdown ! interface FastEthernet0/21 shutdown ! interface FastEthernet0/22 shutdown ! interface FastEthernet0/23 shutdown ! interface FastEthernet0/24 shutdown ! interface GigabitEthernet0/1 switchport trunk native vlan 99 switchport mode trunk ! interface GigabitEthernet0/2 shutdown ! interface Vlan1 ip address 192.168.0.1 255.255.255.0 ! interface Vlan99 mac-address 000c.855d.7b01 ip address 192.168.99.11 255.255.255.0 ! radius-server host 192.168.2.12 auth-port 1645 key cisco ! ! ! line con 0 login ! line vty 0 4 line vty 5 15 ! ! ! ! end |
show run on MLS
Building configuration...
Current configuration : 2624 bytes ! version 16.3.2 no service timestamps log datetime msec no service timestamps debug datetime msec no service password-encryption ! hostname Switch ! ! ! ! ! ! ! no ip cef ip routing ! no ipv6 cef ! ! ! ! ! ! ! ! ! ! ! ! ! ! spanning-tree mode pvst ! ! ! ! ! ! interface GigabitEthernet1/0/1 switchport access vlan 2 switchport mode access switchport nonegotiate ! interface GigabitEthernet1/0/2 switchport access vlan 2 switchport mode access switchport nonegotiate ! interface GigabitEthernet1/0/3 switchport trunk native vlan 99 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/4 switchport trunk native vlan 99 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/5 switchport trunk native vlan 99 switchport trunk encapsulation dot1q switchport mode trunk ! interface GigabitEthernet1/0/6 ! interface GigabitEthernet1/0/7 shutdown ! interface GigabitEthernet1/0/8 shutdown ! interface GigabitEthernet1/0/9 shutdown ! interface GigabitEthernet1/0/10 shutdown ! interface GigabitEthernet1/0/11 shutdown ! interface GigabitEthernet1/0/12 shutdown ! interface GigabitEthernet1/0/13 shutdown ! interface GigabitEthernet1/0/14 shutdown ! interface GigabitEthernet1/0/15 shutdown ! interface GigabitEthernet1/0/16 shutdown ! interface GigabitEthernet1/0/17 shutdown ! interface GigabitEthernet1/0/18 shutdown ! interface GigabitEthernet1/0/19 shutdown ! interface GigabitEthernet1/0/20 shutdown ! interface GigabitEthernet1/0/21 shutdown ! interface GigabitEthernet1/0/22 shutdown ! interface GigabitEthernet1/0/23 shutdown ! interface GigabitEthernet1/0/24 shutdown ! interface GigabitEthernet1/1/1 shutdown ! interface GigabitEthernet1/1/2 shutdown ! interface GigabitEthernet1/1/3 shutdown ! interface GigabitEthernet1/1/4 shutdown ! interface Vlan1 no ip address ! interface Vlan2 mac-address 00d0.ba75.ec01 ip address 192.168.2.1 255.255.255.0 ! interface Vlan99 mac-address 00d0.ba75.ec05 ip address 192.168.99.1 255.255.255.0 ! interface Vlan123 mac-address 00d0.ba75.ec02 ip address 192.168.123.1 255.255.255.0 ip helper-address 192.168.2.11 ip helper-address 192.168.2.12 ! interface Vlan124 mac-address 00d0.ba75.ec03 ip address 192.168.124.1 255.255.255.0 ip helper-address 192.168.2.11 ip helper-address 192.168.2.12 ! interface Vlan125 mac-address 00d0.ba75.ec04 ip address 192.168.125.1 255.255.255.0 ip helper-address 192.168.2.11 ip helper-address 192.168.2.12 ! ip classless ! ip flow-export version 9 ! ! ! ! ! ! ! ! line con 0 ! line aux 0 ! line vty 0 4 login ! ! ! ! end |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 10:45 PM
not sure what you are tying to do and whether is possible in PT; Port-based AAA authentication for PCs?
as far as I know PT can do console and telnet access via AAA.
I take a look later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 11:47 PM - edited 05-28-2020 11:48 PM
Hi what I am trying to do is be able to get a IP address from the DHCP Server but my lab work requires to implement the AAA Server for authentication purposes for the PC to get an IP from the DHCP server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2020 05:56 PM
I currently have layer 2 switch doing native trunking on vlan 99 to the layer 3 switch is that okay? should I not use the vlan that I used to do native trunking for the IT department remote management? I can't seem to get 802.1x working on the access switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 12:07 AM
Hello,
I have opened your file. Which IP address can you not ping from which IP address ?
Source IP --> Destination IP
?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 02:33 AM - edited 05-29-2020 03:11 AM
I'm not clear what you are trying to say? I am using VLANs here. I can't ping the Layer 3 Switch, Servers and PCs from the Layer 2 Switch. Also I cannot ping Layer 2 Switch from the Servers, Layer 3 switch and the host devices. I have re-did my packet tracer file again. Perhaps you might want to take a look.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 08:09 AM
all 3 L2 switches have exactly same IP address on vlan 1; they should have unique; L2 usually have 1 SVI up; not both vlan 1 and vlan 99. PT bug here; I would use vlan 99 but vlan 1 is ok.
L2 switches are missing ip default-gateway 192.168.x.x (vlan 99 or int vlan 1 of L3)
L3 sw does not have IP on vlan 1.
once you fix those issues above, you get pings ok.
The issue is 802.1x for PCs, which I am not sure works in PT but I check. Pcs are getting IPs without authentication 802.1x but not with 802.1x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 10:42 PM
Hi Martin,
Yes I set an IP address on the respective Department vlan interface of Layer 2 Switches and managed to ping them to the PCs, DHCP Server and AAA server IP address but 802.1x indeed is still not working which is quite odd.
I set 802.1x authentication for PC access ports only and not the trunk links but not sure why The PC are unable to get their IP addresses from the DHCP server like you said.
From my understanding we should set 802.1x on ports where PCs are going to be connected and not trunk ports/links which.
How strange that I can get IP address without 802.1x but not with 802.1x
I hope someone can enlighten me on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2020 11:45 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2020 02:22 PM - edited 06-12-2020 02:29 PM
I don't know if you got it working but what we missed was check in box on AAA Radius EAP server plus small adjustments like IP of interface vlan 2 on Switch0 so that it can ping both servers. changed hostname Switch0 to SW1 and added Sw1 authentication info in AAA. see attached files
Regards, ML
**Please Rate All Helpful Responses **
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide