- Cisco Community
- Technology and Support
- Networking
- Routing
- ACL With Standard List Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022
03:11 AM
- last edited on
08-24-2022
02:13 AM
by
Translator
![]()
Hi there,
I am currently configuring a c888 series router.
I have a Lan network at 192.168.10.0/24 (Native Vlan 1 by default - ETH0-1-2-3).
An interface TO WAN THROUGH DIALER 1, the default route is via this DIALER 1 interface.
I configured a loopback10 interface:
ip address 10.0.0.1 255.255.255.255 !!! (Not real IP is just for example)
Outgoing nat performed:
ip nat inside source list 10 interface Loopback10 overload
I need to access from the outside to a machine which is on the LAN network, IP of the machine: 192.168.10.3/24.
I did port forwarding:
ip nat inside source static tcp 192.168.10.3 443 10.0.0.1 8083 extendable
I now need to filter incoming traffic so that certain public IPs can access this port forwarding:
I configured a standard Access-list 50
access-list 50 permit 99.20.10.63
access-list 50 permit 85.24.20.54
I added this access-list on the VLAN1 interface:
ip address 192.168.10.1 255.255.255.0
ip access-group 50 out
ip nat inside
ip virtual-reassembly in
no autostate
Port forwarding works and filtering by ip too. The problem is that the machine 192.168.10.3/24 cannot access the internet following this configuration while I can ping: ping 8.8.8.8 source vlan1.
Could you help me ?
Thanks
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2022
03:35 AM
- last edited on
08-24-2022
02:23 AM
by
Translator
![]()
I have find the solution :
i have to put my extended access-list in Int DIALER 1 IN:
interface Dialer1
ip access-group 100 in
Extended IP access list 100
10 permit ip host 185.19.225.209 any (199 matches)
20 permit tcp any any established (13 matches)
This work fine. The Lan can Now access ton internet.
Best regards and thank you for very much for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022
03:42 AM
- last edited on
08-24-2022
02:15 AM
by
Translator
![]()
ip access-group 50 IN
<<- apply this ACL in dialer interface not to VLAN 1 interface with direction IN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022
05:12 AM
- last edited on
08-24-2022
12:36 AM
by
Translator
![]()
Hello thank you,
interface Dialer1
mtu 1492
bandwidth 2000
ip address negotiated
ip access-group 50 in
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer idle-timeout 0
dialer-group 1
no cdp enable
ppp authentication chap callin
ppp chap hostname xxxxxxxxxxxx
ppp chap password 0 xxxxxxxxxx
ppp ipcp route default
!
This not Working. Now i Can't access to my forwarding ports and i can't ping to 8.8.8.8.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022 08:49 AM
I will do small lab since the OUT is DHCP dynamic learn then may be we need some trick to make it work.
lab today
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022
08:23 AM
- last edited on
08-24-2022
02:20 AM
by
Translator
![]()
Hello,
Remember that an ACL eliminate all trafic that not match, in the sequential order, and consider there is an implicite
deny any any
at the end of the list (as soon as you put a first line in your ACL).
Your
access-list 50 permit ONLY
the 99.20.10.63 and the 85.24.20.54 network. I think that all others trafics are rejected
Hope this wil help you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022 09:45 AM
There is no real solution for my issue ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022 02:35 PM - edited 08-22-2022 06:37 AM
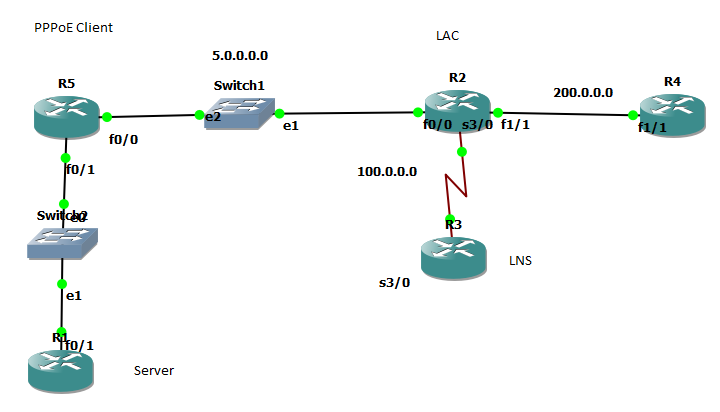
First keep cool,
I make LAB as show above,
the PPPoE cleint have dialer interface and it get IP from Pool in LNS, NOW if I ping from LNS
I need to check which IP address assign to dialer then I can ping it,
in PPPoE client I config static nat and it work the ping is direct to Sever (Router)
Issue here two point
if you use dialer interface IP then it must be know by any one to access Server in LAN
if you use LO then this LO IP must advertise to all other network, hence any one want to access Server use LO and LO will NAT in PPPoE client to LAN Server.
I think this issue not relate so much to ACL than it relate to NAT
You free to ask me any any thing I can apply to my lab or can find to you right answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022
08:00 AM
- last edited on
08-24-2022
02:18 AM
by
Translator
![]()
Keep cool too
Thank you very much but i have the same issue. This is not resolve my issue.
The problem is when i put my
Access-list
to my Vlan interface the Lan Can't access to internet but i Can Ping 8.8.8.8 from the Gateway of the vlan.
there is a rule that I do not know to put in place or add so that flows can pass without external users being able to access my LAN.
allow only ips from this
acccess-lists :
access-list 50 permit 99.20.10.63
access-list 50 permit 85.24.20.54
the LIst access works it blocks the ips which are not in the access lists but it also blocks the LAN for the internet
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022
08:42 AM
- last edited on
08-24-2022
02:21 AM
by
Translator
![]()
ping from the GW because the Packet is generate from Router and ACL will not apply to it.
LAN-PPPoE Client Router -Internet
you want to make LAN access specific IP
<the IP you config in ACL >??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2022
02:02 AM
- last edited on
08-24-2022
02:23 AM
by
Translator
![]()
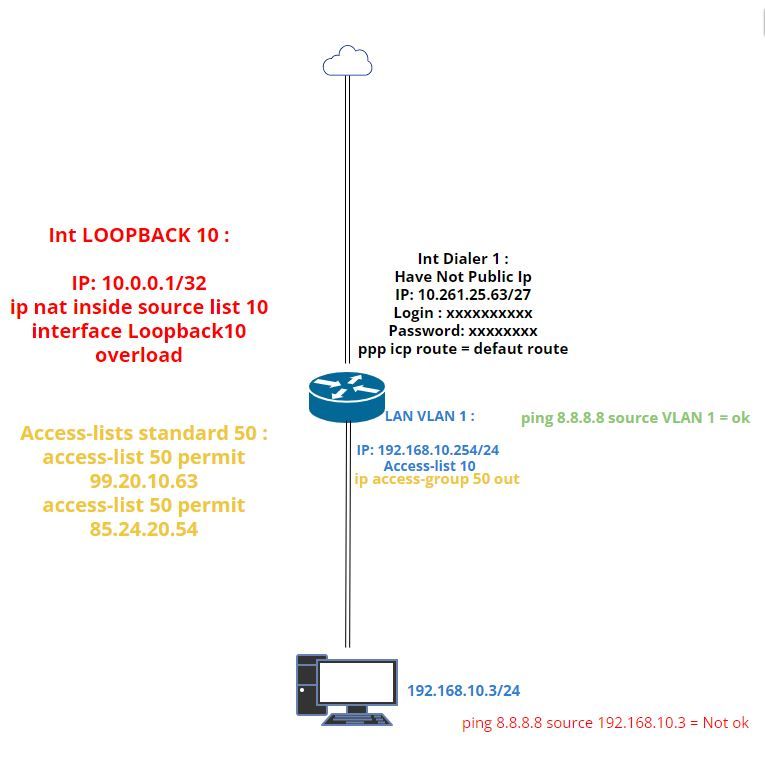
I hope this draw help you,
The ACL works perfectly:
Both ips are allowed to access machine 192.168.10.3/24 and the other ips are denied.
Via this forwarding port :
ip nat inside source static tcp 192.168.10.3 443 10.0.0.1 8083
extendable
The problem is that the acl blocks the flows from the lan to the internet and I can't find a solution to this problem.
Thank you for your patience and valuable help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2022
03:35 AM
- last edited on
08-24-2022
02:23 AM
by
Translator
![]()
I have find the solution :
i have to put my extended access-list in Int DIALER 1 IN:
interface Dialer1
ip access-group 100 in
Extended IP access list 100
10 permit ip host 185.19.225.209 any (199 matches)
20 permit tcp any any established (13 matches)
This work fine. The Lan can Now access ton internet.
Best regards and thank you for very much for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2022
03:15 PM
- last edited on
08-24-2022
02:25 AM
by
Translator
![]()
Hello
try appending the following:
access-list 10 permit 192.168.10.0 0.0.0.255
ip access-list extended 100 permit tcp host 99.20.10.63 8083 host 192.168.10.3 eq 443
ip access-list extended 100 permit tcp host 85.24.20.54 8083 host 192.168.10.3 eq 443
ip access-list extended 100 deny ip host 99.20.10.63 host 192.168.10.3
ip access-list extended 100 deny ip host 85.24.20.54 host 192.168.10.3
ip access-list extended 100 permit ip any any
ip nat inside source list 10 interface dialer1 overload
ip nat inside source static tcp 192.168.10.3 443 <public ip > 8083 extendable
ip route 0.0.0.0 0.0.0.0 dialer1
int dialer1
Description wan
ip access-group 100 in
ip nat outside
int x/x
Description lan
no ip access-group 50 out
ip nat inside
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2022 08:01 AM
Hey
I have try this but its the same issue =(.
Best Regards
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide