- Cisco Community
- Technology and Support
- Networking
- Routing
- AnyConnect ping is good but http does not work ASA 5520
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 01:06 PM - edited 04-04-2019 01:08 PM
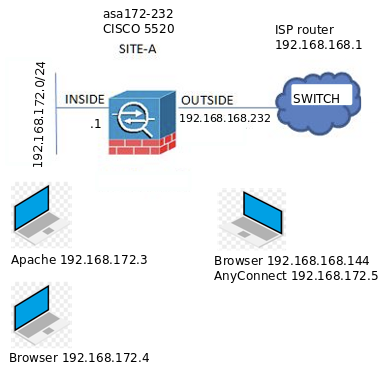
AnyConnect is working but I can't access the web server but ping works. Attached is the full configuration. I had to remove the nat to get it to work.
((( no nat (inside,outside) source static 192.168.172.0_24 192.168.172.0_24 destination static )))
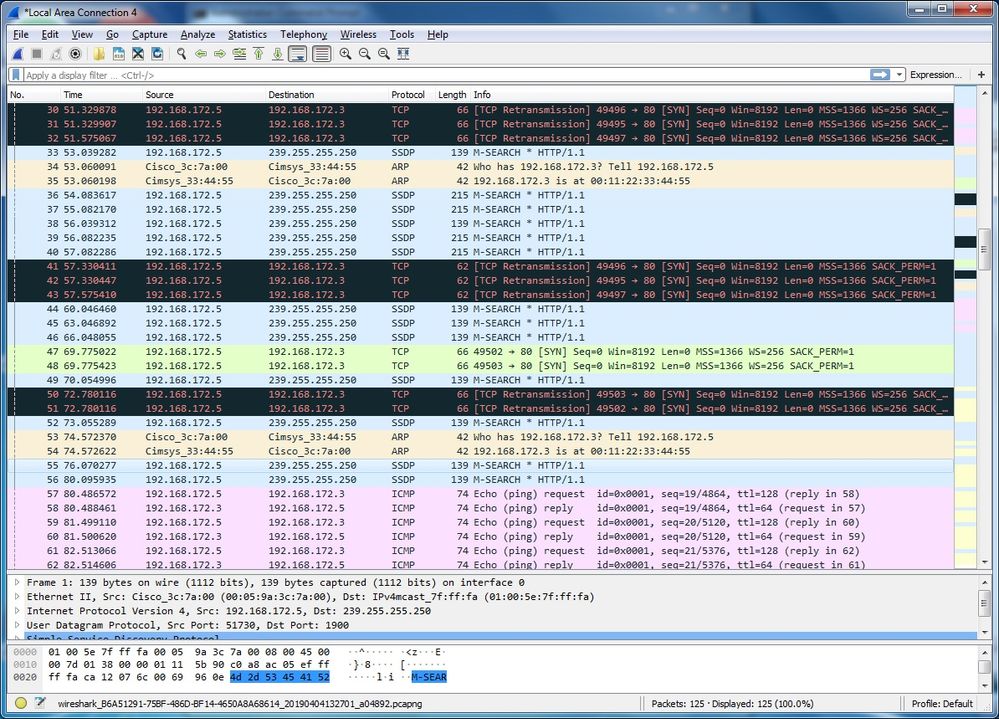
Here us the Wireshark on the client for the ping and http://192.168.172.3:80 (ping is at the bottom)
192.168.172.3<->192.168.172.5
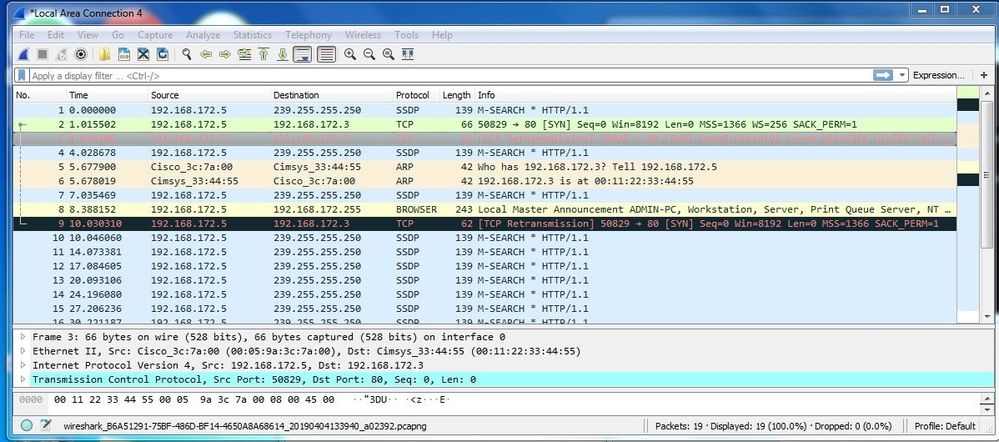
Here is Wireshark for "telnet 192.167.172.3 80" it tries to connect then tries again.
CONFIGURATION - CONFIGURATION - CONFIGURATION - CONFIGURATION - CONFIGURATION -
webvpn
anyconnect image flash:anyconnect-win-4.6.03049-webdeploy-k9.pkg
enable outside
anyconnect enable
sysopt connection permit-vpn
ip local pool VPN_POOL 192.168.172.5-192.168.172.10 mask 255.255.255.0
access-list SPLIT_TUNNEL standard permit 192.168.172.0 255.255.255.0
group-policy ANYCONNECT_POLICY internal
group-policy ANYCONNECT_POLICY attributes
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT_TUNNEL
dns-server value 192.168.168.1
webvpn
anyconnect keep-installer installed
anyconnect ask none default anyconnect
anyconnect dpd-interval client 30
tunnel-group MY_TUNNEL type remote-access
tunnel-group MY_TUNNEL general-attributes
default-group-policy ANYCONNECT_POLICY
address-pool VPN_POOL
exit
tunnel-group MY_TUNNEL webvpn-attributes
group-alias SSL_USERS enable
webvpn
tunnel-group-list enable
username SSL_USER password SSLPassword
username SSL_USER attributes
service-type remote-access
end
**************************************************************************************
Client AnyConnect VPN Client > Statistics > Details > Export (AnyConnect-ExportedStats.txt
Cisco AnyConnect Secure Mobility Client Version 4.6.03049
VPN Stats
Bytes Received: 28837
Bytes Sent: 84930
Compressed Bytes Received: 0
Compressed Bytes Sent: 0
Compressed Packets Received: 0
Compressed Packets Sent: 0
Control Bytes Received: 1603
Control Bytes Sent: 1779
Control Packets Received: 43
Control Packets Sent: 65
Encrypted Bytes Received: 13797
Encrypted Bytes Sent: 129090
Encrypted Packets Received: 65
Encrypted Packets Sent: 694
Inbound Bypassed Packets: 0
Inbound Discarded Packets: 0
Outbound Bypassed Packets: 0
Outbound Discarded Packets: 0
Packets Received: 16
Packets Sent: 623
Session Disconnect: None
Time Connected: 00:11:12
Protocol Info
Active Protocol
Protocol Cipher: DHE_RSA_AES256_SHA
Protocol Compression: None
Protocol State: Connected
Protocol: DTLS
Inactive Protocol
Protocol Cipher: DHE_RSA_AES256_SHA
Protocol Compression: None
Protocol State: Connected
Protocol: TLSv1.0
Tunnel Mode (IPv4): Split Include
Tunnel Mode (IPv6): Drop All Traffic
Dynamic Tunnel Exclusion: None
Dynamic Tunnel Inclusion: None
Routes
Secure Routes
192.168.172.0 24
192.168.168.1 32
Non-tunneled Routes
0.0.0.0 0
Firewall Rules
OS Version
Windows 7 : WinNT 6.1.7601 Service Pack 1
Windows IP Configuration
Host Name . . . . . . . . . . . . : ADMIN-PC
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Local Area Connection 4:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Cisco AnyConnect Secure Mobility Client Virtual Miniport Adapter for Windows x64
Physical Address. . . . . . . . . : 00-05-9A-3C-7A-00
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::9656:3601:37c6:aff6%19(Preferred)
Link-local IPv6 Address . . . . . : fe80::b58a:5504:566f:2e1%19(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.172.5(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : ::
DNS Servers . . . . . . . . . . . : 192.168.168.1
NetBIOS over Tcpip. . . . . . . . : Enabled
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Generic Marvell Yukon 88E8040 PCI-E Fast Ethernet Controller
Physical Address. . . . . . . . . : A4-BA-DB-9E-9B-DC
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::8127:186d:6b35:22cb%11(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.168.144(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Thursday, April 04, 2019 1:17:14 PM
Lease Expires . . . . . . . . . . : Thursday, April 04, 2019 4:34:21 PM
Default Gateway . . . . . . . . . : 192.168.168.1
DHCP Server . . . . . . . . . . . : 192.168.168.1
DHCPv6 IAID . . . . . . . . . . . : 245676763
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-22-D5-9B-C7-A4-BA-DB-9E-9B-DC
DNS Servers . . . . . . . . . . . : 192.168.168.1
NetBIOS over Tcpip. . . . . . . . : Enabled
Tunnel adapter isatap.fios-router.home:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Tunnel adapter Teredo Tunneling Pseudo-Interface:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Teredo Tunneling Pseudo-Interface
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Tunnel adapter isatap.{27727A6C-3A86-41F1-A263-4D585139B6DF}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
===========================================================================
Interface List
19...00 05 9a 3c 7a 00 ......Cisco AnyConnect Secure Mobility Client Virtual Miniport Adapter for Windows x64
11...a4 ba db 9e 9b dc ......Generic Marvell Yukon 88E8040 PCI-E Fast Ethernet Controller
1...........................Software Loopback Interface 1
15...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter
13...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface
14...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #2
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.168.1 192.168.168.144 20
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.168.0 255.255.255.0 On-link 192.168.168.144 276
192.168.168.1 255.255.255.255 On-link 192.168.168.144 21
192.168.168.144 255.255.255.255 On-link 192.168.168.144 276
192.168.168.232 255.255.255.255 On-link 192.168.168.144 21
192.168.168.255 255.255.255.255 On-link 192.168.168.144 276
192.168.172.0 255.255.255.0 On-link 192.168.172.5 257
192.168.172.5 255.255.255.255 On-link 192.168.172.5 257
192.168.172.255 255.255.255.255 On-link 192.168.172.5 257
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.168.144 276
224.0.0.0 240.0.0.0 On-link 192.168.172.5 10000
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.168.144 276
255.255.255.255 255.255.255.255 On-link 192.168.172.5 10000
===========================================================================
Persistent Routes:
None
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
19 21 ::/0 On-link
1 306 ::1/128 On-link
19 276 fe80::/64 On-link
11 276 fe80::8127:186d:6b35:22cb/128
On-link
19 276 fe80::9656:3601:37c6:aff6/128
On-link
19 276 fe80::b58a:5504:566f:2e1/128
On-link
1 306 ff00::/8 On-link
11 276 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
**************************************************************************************
server asa172-232# show vpn-sessiondb detail svc filter name SSL_USER
asa172-232# show vpn-sessiondb detail svc filter name SSL_USER
Session Type: AnyConnect Detailed
Username : SSL_USER Index : 3
Assigned IP : 192.168.172.5 Public IP : 192.168.168.144
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES256 DTLS-Tunnel: (1)none
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)none
Bytes Tx : 15854 Bytes Rx : 400618
Pkts Tx : 20 Pkts Rx : 2538
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : ANYCONNECT_POLICY Tunnel Group : MY_TUNNEL
Login Time : 07:55:18 UTC Thu Apr 4 2019
Duration : 1h:31m:07s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
AnyConnect-Parent Tunnels: 1
SSL-Tunnel Tunnels: 1
DTLS-Tunnel Tunnels: 1
AnyConnect-Parent:
Tunnel ID : 3.1
Public IP : 192.168.168.144
Encryption : none Hashing : none
TCP Src Port : 49373 TCP Dst Port : 443
Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 0 Minutes
Client OS : Windows
Client Type : AnyConnect
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.03049
Bytes Tx : 7627 Bytes Rx : 900
Pkts Tx : 5 Pkts Rx : 1
Pkts Tx Drop : 0 Pkts Rx Drop : 0
SSL-Tunnel:
Tunnel ID : 3.2
Assigned IP : 192.168.172.5 Public IP : 192.168.168.144
Encryption : AES256 Hashing : SHA1
Encapsulation: TLSv1.0 TCP Src Port : 49376
TCP Dst Port : 443 Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 0 Minutes
Client OS : Windows
Client Type : SSL VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.03049
Bytes Tx : 7627 Bytes Rx : 453
Pkts Tx : 5 Pkts Rx : 5
Pkts Tx Drop : 0 Pkts Rx Drop : 0
DTLS-Tunnel:
Tunnel ID : 3.3
Assigned IP : 192.168.172.5 Public IP : 192.168.168.144
Encryption : none Hashing : none
Encapsulation: DTLSv1.0 UDP Src Port : 53356
UDP Dst Port : 443 Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 30 Minutes
Client OS : Windows
Client Type : DTLS VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.6.03049
Bytes Tx : 600 Bytes Rx : 399391
Pkts Tx : 10 Pkts Rx : 2533
Pkts Tx Drop : 0 Pkts Rx Drop : 0
NAC:
Reval Int (T): 0 Seconds Reval Left(T): 0 Seconds
SQ Int (T) : 0 Seconds EoU Age(T) : 5468 Seconds
Hold Left (T): 0 Seconds Posture Token:
Redirect URL :
Solved! Go to Solution.
- Labels:
-
Other Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 02:16 PM
Hello,
the split tunnel ACL does not look right. It needs to specify the network of the inside interface. Instead of:
access-list SPLIT_TUNNEL standard permit 192.168.173.0 255.255.255.0
use
access-list SPLIT_TUNNEL standard permit 192.168.172.0 255.255.255.0
Also, add the words in bold to your NAT exemption:
nat (inside,outside) source static 192.168.172.0_24 192.168.172.0_24 destination static 192.168.173.0_24 192.168.173.0_24 no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 03:45 PM
Hello,
looking at your configuration it seems that your VPN pool is derived from the same network as your inside ?
ip local pool VPN_POOL 192.168.172.5-192.168.172.10 mask 255.255.255.0
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
Typically you would need a NAT exemption from the inside/local network to your VPN pool addresses. This is not possible as both are in the same network. Try and change the VPN pool to something different:
ip local pool VPN_POOL 192.168.173.5-192.168.173.10 mask 255.255.255.0
and then add a network object for the pool, and the NAT exemption:
object network 192.168.173.0_24
subnet 192.168.173.0 255.255.255.0
!
nat (inside,outside) source static 192.168.172.0_24 192.168.172.0_24 destination static 192.168.173.0_24 192.168.173.0_24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 07:47 AM - edited 04-08-2019 09:06 AM
Hi Grorg, Thank you for your recommendation. I entered the configuration that you suggested into the ASA firewall, it went in OK and the AnyConnect client runs OK, but it doesn't work. The ASA firewall that I'm using to get into the enclave is not the default-router used to get to the internet. The AnyConnect client connects but the default-router is blank, like this "Default Gateway . . . . . . .::" How does the client route from the AnyConnect network, 192.1687.173.0, through the ASA outside interface, 192,.168.168.232, to the ASA inside network 192.168.172.0?
When I ping from the client to inside of the AnyConnect connection, the ping goes out the wrong Ethernet Adapter. The main NIC is used, Ethernet adapter Local Area Connection, instead of the AnyConnect NIC, Ethernet adapter Local Area Connection 4? See the following.
Ethernet adapter Local Area Connection 4:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Cisco AnyConnect Secure Mobility Client V
irtual Miniport Adapter for Windows x64
Physical Address. . . . . . . . . : 00-05-9A-3C-7A-00
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::94e7:a99b:49e6:4d41%19(Preferred)
Link-local IPv6 Address . . . . . : fe80::b58a:5504:566f:2e1%19(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.173.5(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : ::
DNS Servers . . . . . . . . . . . : 192.168.168.1
NetBIOS over Tcpip. . . . . . . . : Enabled
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Generic Marvell Yukon 88E8040 PCI-E Fast
Ethernet Controller
Physical Address. . . . . . . . . : A4-BA-DB-9E-9B-DC
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::8127:186d:6b35:22cb%11(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.168.144(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Monday, April 08, 2019 9:45:39 AM
Lease Expires . . . . . . . . . . : Monday, April 08, 2019 1:45:38 PM
Default Gateway . . . . . . . . . : 192.168.168.1
DHCP Server . . . . . . . . . . . : 192.168.168.1
DHCPv6 IAID . . . . . . . . . . . : 245676763
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-22-D5-9B-C7-A4-BA-DB-9E-9B-DC
DNS Servers . . . . . . . . . . . : 192.168.168.1
NetBIOS over Tcpip. . . . . . . . : Enable
The examples that I see on the internet show an ASA doing only Anyconnect. I've got to have the same ASA 1) nat to the internet, 2) build ipsec tunnels to remote customers (ASA-to-ASA), 3) Port Map some inside servers to the outside, 4) get AnyConnect working to get to inside servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 09:37 AM
Hello,
post the current full configuration of your ASA, including the changes you have made...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 10:51 AM - edited 04-08-2019 12:58 PM
Thank you for taking a look :-)
There are now tunnels from the command "sh cry ipsec sa"
Note that I had to remove the overload nat to get anyconnect to work (when I was using the same network for the inside and the anyconnect pool. "nat (inside,outside) after-auto source dynamic any interface" This is the nat that worked with the PAT, L3 tunnels, and the overload nat to the internet.
Here are the NATs that play well with others :-)
asa172-232# sh start | i nat
nat (inside,outside) source static 192.168.172.0_24 192.168.172.0_24 destination static 192.168.180.0_24 192.168.180.0_24 no-proxy-arp route-lookup
nat (inside,outside) static interface service tcp www 8888
nat (inside,outside) static interface service tcp ssh 2222
nat (inside,outside) after-auto source dynamic any interface
asa172-232#
Here is what I added with your recommendations.
webvpn
anyconnect image flash:anyconnect-win-4.6.03049-webdeploy-k9.pkg
enable outside
anyconnect enable
sysopt connection permit-vpn
ip local pool VPN_POOL 192.168.173.5-192.168.173.10 mask 255.255.255.0
access-list SPLIT_TUNNEL standard permit 192.168.173.0 255.255.255.0
group-policy ANYCONNECT_POLICY internal
group-policy ANYCONNECT_POLICY attributes
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT_TUNNEL
dns-server value 192.168.168.1
webvpn
anyconnect keep-installer installed
anyconnect ask none default anyconnect
anyconnect dpd-interval client 30
tunnel-group MY_TUNNEL type remote-access
tunnel-group MY_TUNNEL general-attributes
default-group-policy ANYCONNECT_POLICY
address-pool VPN_POOL
exit
tunnel-group MY_TUNNEL webvpn-attributes
group-alias SSL_USERS enable
webvpn
tunnel-group-list enable
username SSL_USER password SSLPassword
username SSL_USER attributes
service-type remote-access
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 02:16 PM
Hello,
the split tunnel ACL does not look right. It needs to specify the network of the inside interface. Instead of:
access-list SPLIT_TUNNEL standard permit 192.168.173.0 255.255.255.0
use
access-list SPLIT_TUNNEL standard permit 192.168.172.0 255.255.255.0
Also, add the words in bold to your NAT exemption:
nat (inside,outside) source static 192.168.172.0_24 192.168.172.0_24 destination static 192.168.173.0_24 192.168.173.0_24 no-proxy-arp route-lookup
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2019 09:12 AM
WOW it works!!! Everything works - but I haven't tested the L3 tunnel yet. I have to build up another 5505. But NAT overload, PAT outside:8080 to inside:80, VPN Anyconnect all work.
You're the best Georg. Thank you for your time once again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2019 07:52 AM
Georg, I just got an amazing find. Its a 5520 with an SSM-20 module and it is fully configured. Sometimes you get lucky on Craigslist :-) Looking at this configuration makes me feel like a kindergartner :-/ Check it out!!!! I sanitized it so, hopefully, there is no trace to the original owner....Used Cisco ip address for routable IPs. This ASA is really locked down.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide