- Cisco Community
- Technology and Support
- Networking
- Routing
- area 0 authentication message-digest
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
area 0 authentication message-digest
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 06:38 AM
when to use command"area 0 authentication message-digest"
- Labels:
-
Other Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 06:42 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 07:26 AM - edited 02-28-2023 07:34 AM
Hello,
You can apply authentication type 2 different ways in OSPFv2. In the global routing config or on the interface.
The area 0 authentication message-digest command is used in global routing to tell the router that every interface in Area 0 (or whichever area you specify) needs to be using MD5 authentication. You would apply a similar command on the interface if you only wanted select interfaces to participate in authentication. You still need to apply the message digest password on the interface only.
Sample configuration:
router ospf 1
area 0 authentication message-digest <- specified MD5 authentication is used for all interfaces in Area 0.
R1(config)#Interface g0/0
R1(config-if)#ip ospf message-digest-key 5 md5 cisco <-applies password to interface
or you could do both on the interface which limits authentication to this interface only:
R1(config)#Interface g0/0
R1(config-if)#ip ospf authentication message-digest <-specifies type of authentication to be used for interface only
R1(config-if)#ip ospf message-digest-key 5 md5 cisco <- must specify key number and password - must match on other side
If you use the global router command you'll need to put a password on all interfaces in the area specified in the Area command and also put the same authentication on the remote end for adjacency to form.
Hope that helps
-David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 08:58 AM
I was going to "cancel" this reply - because it's so out-of-date, but posting anyway, in case anyone ends up needing to support such out-ot-date Cisco devices. I.e. What's a valid config now, might not also be valid on older equipment.
Dave, OSPF may have changed since I've actively used it, and/or my memory is faulty, but I recall (?) even to use interface to interface authentication, area authentication had to be configured (the latter, though, as you note, had to be configured, the same, for all routers in that area).
(NB: just checked, at least my memory is not [totally, this time] faulty, OSPF interface authentication, no longer needing area authentication, started in 12.0[8]. [Laugh - and I remember when 12.0 was so new and shiny; with new features and new bugs, vs. v11.])
I also (strongly) recall, when using an authenticated area, we did NOT have to configure passwords on interfaces we didn't want them on (other side, though, had to also not use password). I.e. we configured passwords on Ethernet LAN interfaces, where someone could rather easily, attach something to, but generally didn't bother with non-Ethernet WAN interfaces.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 09:17 AM - edited 02-28-2023 09:22 AM
Hey Joseph
You are correct in that a password isn't "required" and only authentication type has to match, but then that defeats the authentication piece of configuring it in the first place (in my opinion).
Area authentication does not need to be the same on every router - but as mentioned above if you configure Area authentication on lets say R1 - then every router connecting to R1 in Area 0 needs the same authentication...but it can be configured on the interface connecting to R1 in Area 0 and not the entire Area. (sounds kind of confusing even me reading it back)
If you configure authentication on the interface (with both commands of choosing the type and then configuring the password) then Area authentication is not needed.
But lets say you want authentication on all Area 0 interfaces current and any future ones. You would configure Area 0 authentication in global router mode, so when you configured a new interface in Area 0 you would just need to configure the password (or lack thereof as mentioned) instead of password and authentication type. It just "reduces" commands needed.
Thinking in terms of the CCIE test I hope to pass one day (laugh) and getting a question to configure OSPF authentication using the least amount of commands possible:
Configuring Area authentication and then configuring a password on 2 interfaces would be 3 lines of configuration. Meanwhile configuring authentication type and then configuring a password on those same 2 interfaces would be 4 commands. Obviously its useful the more interfaces you have.....not so much when its only a couple.
-or configure MD5 authentication for the whole area except this interface, configure it as plaintext.
(as you can tell the rabbit hole runs deep here)
Also note as I am sure you're aware that interface config takes precedence. So if MD5 is configured for the Area in global mode and SHA is configured on the interface....SHA wins.
-David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 10:20 AM - edited 02-28-2023 10:23 AM
You are correct in that a password isn't "required" and only authentication type has to match, but then that defeats the authentication piece of configuring it in the first place (in my opinion).
Defeating purpose of configurating authentication, yes and no. As I described, we were only concerned about Ethernet interfaces, especially in small branches offices, where network devices weren't in a locked closet. Those we wanted to add an additional level of security, to preclude someone jacking in a PC, running OSPF, doing who knows what.
Again, at that time, could not do interface authentication, alone, had to enable it first on all the area's routers. Effectively, we now had a per interface authentication usage, or not, choice.
Laugh - consider why interface, alone, authentication is supported. I.e. provides an interface by interface choice without first needing to convert a large production OSPF area's authentication mode, which, is much fun, as routers will not form adjacency until they at least agree on area authentication mode.
Area authentication does not need to be the same on every router - but as mentioned above if you configure Area authentication on lets say R1 - then every router connecting to R1 in Area 0 needs the same authentication...but it can be configured on the interface connecting to R1 in Area 0 and not the entire Area. (sounds kind of confusing even me reading it back)
Well I agree, what you wrote is confusing.
Dang - made me "research" this new fangled interface only authentication. ; )
Found in https://www.cisco.com/c/en/us/support/docs/ip/open-shortest-path-first-ospf/13697-25.html
Note: The area authentication command in the configuration enables authentications for all the interfaces of the router in a particular area. You can also use the ip ospf authentication command under the interface to configure plain text authentication for the interface. This command can be used if a different authentication method or no authentication method is configured under the area to which the interface belongs. It overrides the authentication method configured for the area. This is useful if different interfaces that belong to the same area need to use different authentication methods
Note: The area authentication message-digest command in this configuration enables authentications for all of the router interfaces in a particular area. You can also use the ip ospf authentication message-digest command under the interface to configure MD5 authentication for the specific interface. This command can be used if a different authentication method or no authentication method is configured under the area to which the interface belongs. It overrides the authentication method configured for the area. This is useful if different interfaces that belong to the same area need to use different authentication methods.
My understanding is enabling authentication for the area (within OSPF routing section), and authentication methods (e.g. plain text, MD5, etc.) are two different things.
Some of Cisco's OSPF authentication documentation, for the area, still make it clear all area routers need to agree they are, or are not, in an authenticated area. (I.e. like area number, adjacency cannot happen unless specific area setting agree.)
If I'm understanding the above notes correctly, you might not be able to mix and match routers, within the same area, if they have area authentication activation, or not, settings, but you can, at the interface, mix and match authentication methods or also use per interface authentication, even when it's not activated for the area (again, I think even in this latter case, all area routers would need area authentication to NOT be enabled, i.e. all area routers configured alike).
Dave, you thoughts or comments?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 11:19 AM - edited 02-28-2023 11:20 AM
Joseph,
First let me say I enjoy this constructive discussion as I have to dig to make sure what I said "off the cuff" was accurate as you are also doing your homework. I have made a PT lab that I have attached. Just in case you cant open it or don't have PT I will pout it in here best I can. If area authentication is enabled (plaintext or MD5) it doesn't have to be the same throughout the Area. If its a key chain/SHA authentication configuration, I believe that's interface only as the updated OSPFv2 standard just uses that (check).
Global router mode Commands:
area 0 authentication <- enables plaintext area authentication
area 0 message-digest <- enabled MD5 authentication in the area
R1
interface GigabitEthernet0/0/0
ip address 192.168.12.1 255.255.255.0
ip ospf authentication message-digest <- Overrides plaintext with MD5
ip ospf message-digest-key 5 md5 cisco <- MD5 password to R2
!
interface GigabitEthernet0/0/1
ip address 192.168.13.1 255.255.255.0
ip ospf authentication-key cisco <-plaintext PW for interface to R3
!
router ospf 1
log-adjacency-changes
area 0 authentication <-enabled plaintext for area 0
network 0.0.0.0 255.255.255.255 area 0
!
R2
interface GigabitEthernet0/0/0
ip address 192.168.12.2 255.255.255.0
ip ospf message-digest-key 5 md5 cisco
!
interface GigabitEthernet0/0/1
ip address 192.168.23.2 255.255.255.0
ip ospf authentication null <- dont use any authentication on this interface to R3
!
router ospf 1
log-adjacency-changes
area 0 authentication message-digest <- enable MD5 authentication for Area 0
network 0.0.0.0 255.255.255.255 area 0
!
R3
interface GigabitEthernet0/0/0
ip address 192.168.23.3 255.255.255.0
ip ospf authentication null <- dont use any authentication on this interface to R2
!
interface GigabitEthernet0/0/1
ip address 192.168.13.3 255.255.255.0
ip ospf authentication <-enabled plaintext for interface to R1
ip ospf authentication-key cisco <-plaintext PW for interface to R1
!
router ospf 1
log-adjacency-changes
network 0.0.0.0 255.255.255.255 area 0
no area authentication command configured on R3 - just interface commands
!
As you can see all routers form an adjacency and share OSPF routes without issue (I can send those snips as well if you cant open the PT file). So it seems its much more streamlined for upgrades and like you said differing authentication methods per neighbor.
Thanks for the lab practice
-David
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 11:39 AM
That's great, but, don't trust PT to be accurate.
If you can do similar on something using real IOS images, that would be ideal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 12:36 PM
I share your sentiment and can do the same thing in Eve-NG and CML (done before practicing labbing). Unfortunately I am at work but will be more than happy to provide the same setup in both once I am off either tonight or tomorrow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
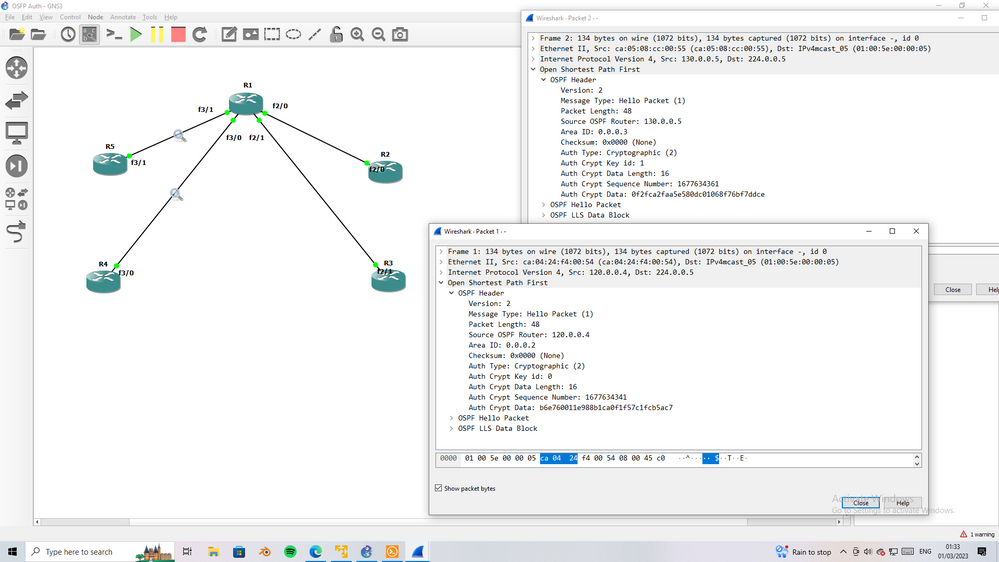
02-28-2023 02:40 PM - edited 02-28-2023 02:43 PM
interface FastEthernet3/1
ip address 130.0.0.1 255.255.255.0
ip ospf message-digest-key 1 md5 R5
duplex auto
speed auto
!
!
router ospf 100
log-adjacency-changes
area 0 authentication
area 1 authentication
area 2 authentication message-digest
area 3 authentication message-digest
network 100.0.0.0 0.0.0.255 area 0
network 110.0.0.0 0.0.0.255 area 1
network 120.0.0.0 0.0.0.255 area 2 <<- R4
network 130.0.0.0 0.0.0.255 area 3 <<- R5
I config four area in R and then assign area with different auth method
finally I use key under SOME interface,
when we config auth, the key ID is 0 which is default and it apply to all interface in that area except when we override this default by assign key for md5 under specific interface, here I config the key under the interface toward R5
the result you can see in OSPF hello message check the header you will see the key ID the router use for specific interface.
below wireshark capture
R1-R4 md5 auth with default key
R1-R5 md5 auth with key config under interface
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
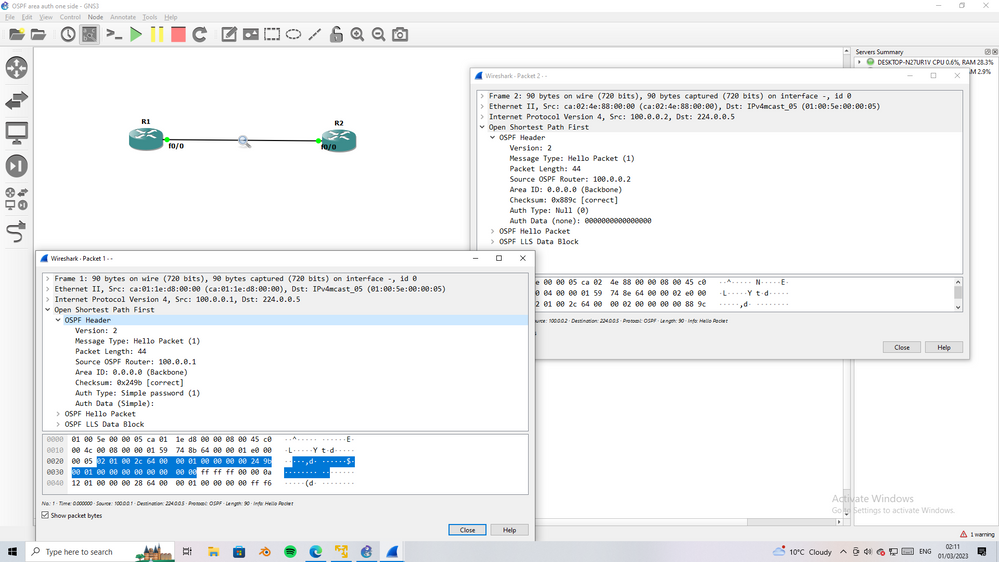
02-28-2023 03:03 PM - edited 02-28-2023 03:06 PM
Kool, but, unsure it answers the question, can two OSPF routers, in the same area, establish an adjacency if one router has area authentication defined (any kind defined for area in OSPF router section) and the other router has no area authentication defined (any kind defined for area in OSPF router section)?
E.g.:
R1
interface e0
ip address 192.168.1.1 255.255.255.0
router ospf 10
area 1 authentication
network 192.168.1.0 0.0.0.255 area 1
R2
interface e0
ip address 192.168.1.2 255.255.255.0 area 1
router ospf 10
network 192.168.1.0 0.0.0.255
I.e. will OSPF adjacency come up between R1 and R2 on e0<>e0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 03:14 PM
I try it and NO
because the hello us auth and other router can not accpet it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 03:27 PM - edited 02-28-2023 03:37 PM
That's what I expected to happen (Dave you expected what MHM just did to work, correct?), but would you please also try:
R1
interface e0ip address 192.168.1.1 255.255.255.0ip ospf authentication-key cisco
router ospf 10area 1 authenticationnetwork 192.168.1.0 0.0.0.255 area 1
R2
interface e0ip address 192.168.1.2 255.255.255.0ip ospf authentication-key cisco
router ospf 10network 192.168.1.0 0.0.0.255 area 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 03:27 PM - edited 02-28-2023 03:27 PM
You would still have to configure authentication on R2 e0/0 interface for it to come up.
@MHM Cisco World what happens when you put the command on R2s e0/0 interface
R2(config-if)#ip ospf authenticationWhile keeping Area authentication on R1. It should work.
As @Joseph W. Doherty mentioned you can configure authentication without a password. As long as the link between routers needing to peer agrees on the authentication type (0, 1 or 2) it should function normally as I understand it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 03:35 PM
Oops, my bad (thanks Dave), so next to try would be:
R1
interface e0
ip address 192.168.1.1 255.255.255.0
router ospf 10
area 1 authentication
network 192.168.1.0 0.0.0.255 area 1
R2
interface e0
ip address 192.168.1.2 255.255.255.0
ip ospf authentication
router ospf 10
network 192.168.1.0 0.0.0.255 area 1
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide