- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA cannot ping outside through NAT on border router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2018 08:47 PM - edited 03-05-2019 10:07 AM
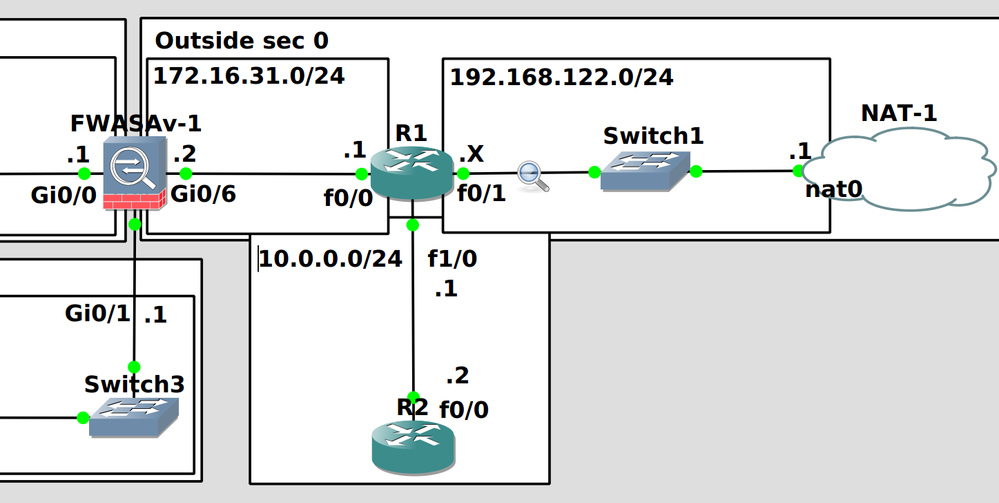
I have the following topology below, in GNS3. Basically, the cloud NAT-1 is the Internet, R1 is my border router with NAT and FWASAv-1 was supposed to be able to access the Internet, but can't. I created that other leg with R2 to test the NAT, and to my surprise, that one works fine. Here is the relevant config:
R1
R1#sh run
!
interface FastEthernet0/0 ip address 172.16.31.1 255.255.255.0 ip nat inside ip virtual-reassembly duplex auto speed auto ! interface FastEthernet0/1 ip address dhcp ip nat outside ip virtual-reassembly duplex auto speed auto ! interface FastEthernet1/0 ip address 10.0.0.1 255.255.255.0 ip nat inside ip virtual-reassembly duplex auto speed auto ! ip nat inside source list 10 interface FastEthernet0/1 overload ! access-list 10 permit any
R1#sh ip int brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 172.16.31.1 YES NVRAM up up
FastEthernet0/1 192.168.122.106 YES DHCP up up
FastEthernet1/0 10.0.0.1 YES NVRAM up up
NVI0 172.16.31.1 YES unset up up
! -- I don't know what that NVI0 is
R1#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 192.168.122.1 to network 0.0.0.0
C 192.168.122.0/24 is directly connected, FastEthernet0/1
172.16.0.0/24 is subnetted, 1 subnets
C 172.16.31.0 is directly connected, FastEthernet0/0
10.0.0.0/24 is subnetted, 1 subnets
C 10.0.0.0 is directly connected, FastEthernet1/0
S* 0.0.0.0/0 [254/0] via 192.168.122.1
R1#ping 192.168.122.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.122.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/15/40 ms
R1#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/20/32 ms
R2
R2#sh run
!
ip name-server 192.168.122.1
!
interface FastEthernet0/0
ip address 10.0.0.2 255.255.255.0
duplex auto
speed auto
!
ip route 0.0.0.0 0.0.0.0 10.0.0.1
!
R2#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 10.0.0.1 to network 0.0.0.0
10.0.0.0/24 is subnetted, 1 subnets
C 10.0.0.0 is directly connected, FastEthernet0/0
S* 0.0.0.0/0 [1/0] via 10.0.0.1
R2#ping 10.0.0.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/13/24 ms
R2#ping 192.168.122.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.122.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 24/28/32 ms
R2#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 36/46/56 ms
FWASAv-1
ASAv1# sh run ip ! interface GigabitEthernet0/0 nameif inside security-level 100 ip address 172.16.0.1 255.255.255.0 ! interface GigabitEthernet0/1 nameif dmz security-level 50 ip address 172.16.10.1 255.255.255.0 ! interface GigabitEthernet0/6 nameif outside security-level 0 ip address 172.16.31.2 255.255.255.0 ! ASAv1# sh run route route outside 0.0.0.0 0.0.0.0 172.16.31.1 1 ! --- I don't know what those deny below are for ASAv1# sh run xlate xlate per-session deny tcp any4 any4 xlate per-session deny tcp any4 any6 xlate per-session deny tcp any6 any4 xlate per-session deny tcp any6 any6 xlate per-session deny udp any4 any4 eq domain xlate per-session deny udp any4 any6 eq domain xlate per-session deny udp any6 any4 eq domain xlate per-session deny udp any6 any6 eq domain ! ASAv1# ping 192.168.122.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.122.1, timeout is 2 seconds: ????? Success rate is 0 percent (0/5) ASAv1# ping 8.8.8.8 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: ????? Success rate is 0 percent (0/5) ASAv1# ping 172.16.31.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.31.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 10/10/10 ms
debug in R1 (debug ip nat)
! When successfully pinging 8.8.8.8 from R1 *Mar 1 01:38:32.039: mapping pointer available mapping:0 *Mar 1 01:38:32.039: NAT: [0] Allocated Port for 10.0.0.2 -> 192.168.122.106: wanted 21 got 21 *Mar 1 01:38:32.043: NAT: i: icmp (10.0.0.2, 21) -> (8.8.8.8, 21) [86] *Mar 1 01:38:32.043: NAT: s=10.0.0.2->192.168.122.106, d=8.8.8.8 [86] *Mar 1 01:38:32.075: NAT: o: icmp (8.8.8.8, 21) -> (192.168.122.106, 21) [35052] *Mar 1 01:38:32.075: NAT: s=8.8.8.8, d=192.168.122.106->10.0.0.2 [35052] *Mar 1 01:38:32.095: NAT: i: icmp (10.0.0.2, 21) -> (8.8.8.8, 21) [87] *Mar 1 01:38:32.095: NAT: s=10.0.0.2->192.168.122.106, d=8.8.8.8 [87] *Mar 1 01:38:32.127: NAT: o: icmp (8.8.8.8, 21) -> (192.168.122.106, 21) [35081] *Mar 1 01:38:32.127: NAT: s=8.8.8.8, d=192.168.122.106->10.0.0.2 [35081] *Mar 1 01:38:32.131: NAT: i: icmp (10.0.0.2, 21) -> (8.8.8.8, 21) [88] *Mar 1 01:38:32.131: NAT: s=10.0.0.2->192.168.122.106, d=8.8.8.8 [88] *Mar 1 01:38:32.167: NAT: o: icmp (8.8.8.8, 21) -> (192.168.122.106, 21) [35115] *Mar 1 01:38:32.167: NAT: s=8.8.8.8, d=192.168.122.106->10.0.0.2 [35115] *Mar 1 01:38:32.187: NAT: i: icmp (10.0.0.2, 21) -> (8.8.8.8, 21) [89] *Mar 1 01:38:32.187: NAT: s=10.0.0.2->192.168.122.106, d=8.8.8.8 [89] *Mar 1 01:38:32.215: NAT: o: icmp (8.8.8.8, 21) -> (192.168.122.106, 21) [35153] *Mar 1 01:38:32.215: NAT: s=8.8.8.8, d=192.168.122.106->10.0.0.2 [35153] *Mar 1 01:38:32.223: NAT: i: icmp (10.0.0.2, 21) -> (8.8.8.8, 21) [90] *Mar 1 01:38:32.227: NAT: s=10.0.0.2->192.168.122.106, d=8.8.8.8 [90] *Mar 1 01:38:32.255: NAT: o: icmp (8.8.8.8, 21) -> (192.168.122.106, 21) [35187] *Mar 1 01:38:32.255: NAT: s=8.8.8.8, d=192.168.122.106->10.0.0.2 [35187] ! When pinging 8.8.8.8 from ASAv and failing *Mar 1 01:39:59.387: mapping pointer available mapping:0 *Mar 1 01:39:59.387: NAT: [0] Allocated Port for 172.16.31.2 -> 192.168.122.106: wanted 56364 got 56364 *Mar 1 01:39:59.391: NAT*: i: icmp (172.16.31.2, 56364) -> (8.8.8.8, 56364) [7968] *Mar 1 01:39:59.391: NAT*: i: icmp (172.16.31.2, 56364) -> (8.8.8.8, 56364) [7968] *Mar 1 01:39:59.391: NAT*: s=172.16.31.2->192.168.122.106, d=8.8.8.8 [7968] R1# *Mar 1 01:40:01.415: mapping pointer available mapping:0 *Mar 1 01:40:01.415: NAT: [0] Allocated Port for 172.16.31.2 -> 192.168.122.106: wanted 56365 got 56365 *Mar 1 01:40:01.415: NAT*: i: icmp (172.16.31.2, 56365) -> (8.8.8.8, 56365) [15738] *Mar 1 01:40:01.419: NAT*: i: icmp (172.16.31.2, 56365) -> (8.8.8.8, 56365) [15738] *Mar 1 01:40:01.419: NAT*: s=172.16.31.2->192.168.122.106, d=8.8.8.8 [15738] R1# *Mar 1 01:40:03.399: mapping pointer available mapping:0 *Mar 1 01:40:03.399: NAT: [0] Allocated Port for 172.16.31.2 -> 192.168.122.106: wanted 56366 got 56366 *Mar 1 01:40:03.399: NAT*: i: icmp (172.16.31.2, 56366) -> (8.8.8.8, 56366) [22464] *Mar 1 01:40:03.403: NAT*: i: icmp (172.16.31.2, 56366) -> (8.8.8.8, 56366) [22464] *Mar 1 01:40:03.403: NAT*: s=172.16.31.2->192.168.122.106, d=8.8.8.8 [22464] R1# *Mar 1 01:40:05.403: mapping pointer available mapping:0 *Mar 1 01:40:05.403: NAT: [0] Allocated Port for 172.16.31.2 -> 192.168.122.106: wanted 56367 got 56367 *Mar 1 01:40:05.403: NAT*: i: icmp (172.16.31.2, 56367) -> (8.8.8.8, 56367) [29396] *Mar 1 01:40:05.407: NAT*: i: icmp (172.16.31.2, 56367) -> (8.8.8.8, 56367) [29396] *Mar 1 01:40:05.407: NAT*: s=172.16.31.2->192.168.122.106, d=8.8.8.8 [29396] R1# *Mar 1 01:40:07.407: mapping pointer available mapping:0 *Mar 1 01:40:07.407: NAT: [0] Allocated Port for 172.16.31.2 -> 192.168.122.106: wanted 56368 got 56368 *Mar 1 01:40:07.407: NAT*: i: icmp (172.16.31.2, 56368) -> (8.8.8.8, 56368) [2676] *Mar 1 01:40:07.411: NAT*: i: icmp (172.16.31.2, 56368) -> (8.8.8.8, 56368) [2676] *Mar 1 01:40:07.411: NAT*: s=172.16.31.2->192.168.122.106, d=8.8.8.8 [2676]
I also captured traffic between R1 and Switch1. When ping comes from R2, packets show up there already translated. When pinged from ASA, no icmp packets show up there.
Is it something in ASA? I don't know what else to do. I can provide more configurations, debug, what not.
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2018 01:49 PM
Hello,
on a side note, and looking at your topology, are you using the IOSv appliance for the routers ? I think the ASAv and IOS routers in GNS are not working well together, you need to use the IOSv appliance.
I have attached the topology I am using in GNS3, with the exact same configs you have posted, and I can ping 8.8.8.8 from the ASA (outside interface)...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2018 01:36 AM
Hello
fws by default provide a way to proxy from one network to another nowadays they are statefull meaning they monitor connections from inside your network to outside or vice versa if they are allowed to but usually only connections initiated from inside to outside are allowed
so ypur inside interface security level 100
will allow traffic out or outside interface security level 0 but not the other way around
NVI is a nat virtual interface used in domain-less nat - it created automatically when when nat is enabled ( domain or domainless) but my understanding it’s only used in domainless nat ( ip nat enable ) so no need for ip nat inside - ip nat outside
in your case regards your topology can a few things are not correct
1) you don’t have nat enabled on the asa and as the rtr that’s is attached to the Asa’s outside interface isn’t aware of the Asa’s internal networks then connectivity will fail
so ether enable nat on the asa or add some static routes in rtr 1 to make it aware of the asa internal networks
2) also you nat acl on rtr 1 should not use any any but be specific about what networks need to be translated as this can put a unwarranted load on the router and also could result in network issues
res
paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2018 07:50 PM
Hello Paul,
So, traffic is not going through the ASA (yet). I'm trying to use the ASA outside interface as source.
As you can see in the debug, the source address for the ASA ping is in fact the one from the outside interface, which is directly connected to R1, so no need for static routes. My understanding is that traffic should go through R1, which would NAT it to the Internet, as it is happening with R2.
So, my traffic is not coming from ASA inside interface, it is being originated in ASA outside interface. It looks like R1 is being selective and only NATing R2 traffic. I know I am missing something, I'm just not sure what.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2018 07:02 AM
Hello,
I am pretty sure this is a bug in GNS3. In VIRL, ping works right away, without a default route or any 'icmp permit' statements on the ASA. The default configuration just has 'icmp inspect' in the global policy, and I am not sure even that is required.
I have tried about everything in GNS3, but I couldn't get it to work either. Some threads suggest to turn off CPU throttling in the Advanced settings of the ASAv template, you might want to give that a try...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2018 10:00 AM - edited 03-20-2018 11:09 AM
Hello
I am quite sure this isnt a bug, Now initiating a ping from the ASA FW itself without any NAT applied on the ASA FW or RTR1 should succeed in a reply from 8.8.8.8 providing you have the correct routing inplace
However as you have NAT applied to RTR1 then this problem could be due to the way the NAT order of operation occurs between the two nat domains ( inside/outside) in legacy nat
Would be interesting to see if you used domain-less NAT ( NVI) instead of legacy nat and retested your ping from the ASA
RTR1
remove ip nat inside/outside from your interfaces and apply ip nat enable
no ip nat inside source list 1 interface fa0/1 overload
no access-list 1
access-list 100 ip permit 172.16.31.0 0.0.0.255 any
access-list 100 ip permit 10.0.0.0 0.0.0.255 any
ip nat source list 100 interface fa0/1 overload
ip route 9.0.0.0 0 0.0.0.0 f0/1 dhcp
res
Paul
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2018 07:16 PM
Hello Paul,
I must have NAT on R1 so I can "PAT" traffic out, since that PAT interface is the only known address by the NAT node. Otherwise, with routing only, if traffic comes from the inside interface-connected network, that source IP will not have a returning path.
As Georg pointed out, it was something to do with GNS3 and how it virtualizes devices now (I replied below). But thanks a lot for responding... you guys helped a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2018 01:49 PM
Hello,
on a side note, and looking at your topology, are you using the IOSv appliance for the routers ? I think the ASAv and IOS routers in GNS are not working well together, you need to use the IOSv appliance.
I have attached the topology I am using in GNS3, with the exact same configs you have posted, and I can ping 8.8.8.8 from the ASA (outside interface)...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2018 07:09 PM - edited 04-05-2018 07:18 PM
Oh my, I can't believe that. I redid my topology with the IOSv image and now ASA can reach outside, and so my intranet on the inside network from ASA point of view. I can't believe dynamips has gone down hill like that, so now every piece of device in GNS3 must be virtualized with KVM or docker.
Thank you for your heads up.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide