- Cisco Community
- Technology and Support
- Networking
- Routing
- Assymmetric routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Assymmetric routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2013 08:00 AM - edited 03-04-2019 07:21 PM
Hi
I am designing a SSL-VPN solution, hope you will help me in solving out this puzzle •J.
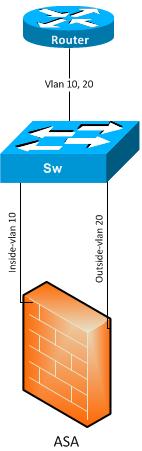
Network diagram below.
Description
Router1 is connected to a switch with trunk port vlan 10 and 20. Vlan 10 is for inside traffic whereas vlan 20 is for outside traffic.
ASA port gig 0/0 is untagged to vlan 10 (inside)
ASA port gig 0/1 is untagged to vlan 20 (outside)
VPN clients are terminating on ASA port 0/1 (outside) interface.
Configuration:
Static Route on ASA:
Default route: next hop to outside interface
Internal network: next hop to inside interface
Static Routes on Router01
VPN IP pool towards inside.
Problem :
The problem I am facing here is with TCP return traffic destined to VPN clients. When TCP syn comes from VPN Client for an outside address, ASA box forwards the traffic towards outside interface using default route. While for the return TCP traffic (SYN ACK) from an outside address, Router forwards TCP return traffic towards inside interface of ASA. Which ASA ignores in the end as it never expect syn ack from inside interface. Seems like ASA box don’t like transmit and receive traffic on different interface.
Should I go with to seperate Routers i.e. inside / outside router. Could someone help me sort out this problem ?
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2013 08:34 AM
Apparnetly, the Internet is terminated on the router. Correct? Does router have default route on itself?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-21-2013 10:17 AM
Actually behind the router is a big ospf cloud that is not show n here. So the inside and outside traffic goes via this router.
Thanks
Umair
Sent from Cisco Technical Support Android App
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2013 07:33 AM
With a separate router for inside/outside you'll still have same problem.
Apparnelty, you're not NATTing all the VPN client traffic to an internal space. NATing all VPN client traffic to internal addresses would make all Internet bound traffic to go through normal Internal route. Alternately, your clients should send only the traffic for internal machines to the tunnel.
This firewall should be positioned in-line to where ever Internet traffic/link is.
HTH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2013 08:07 AM
Hi Rais,
yes there is no NATting. just consider as the IP pools having public IP address.
Could you please expand on where you said inline to internet traffic ?
Regards,
Umair
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2013 11:32 AM
Usually firewalls are placed right where the internet connection is. Something like:
Internet----firewall or router-------internal network
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide