- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: BGP outbound traffic engineering in multi-homed network with 2 ISP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
BGP outbound traffic engineering in multi-homed network with 2 ISP's
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 06:56 AM - edited 02-22-2023 06:57 AM
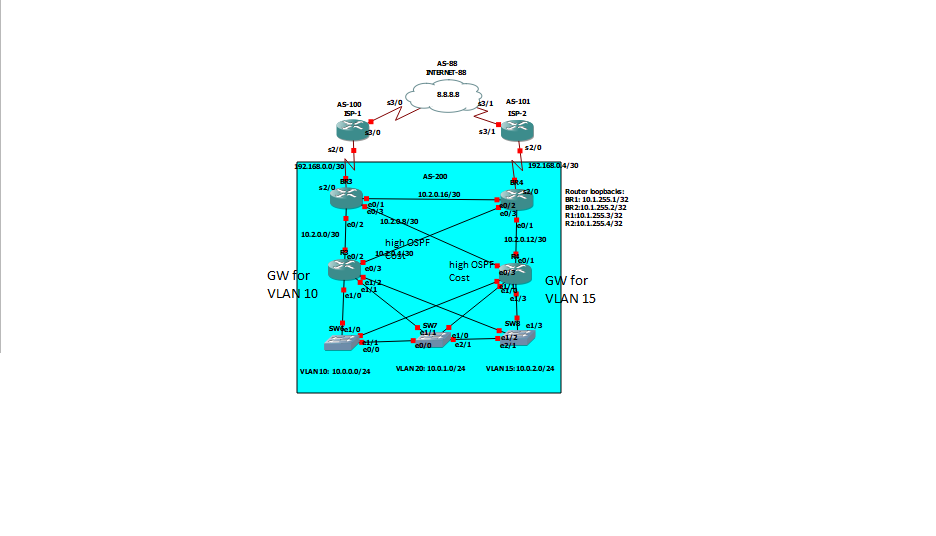
Hello, everyone! I have network with switches at access layer and 3 host networks, 2 core routers , 2 border routers , that have iBGP connection with each other and ospf with other 2 core routers, also each of them connected to 2 different ISP’s with eBGP. Border routers get only default routes from ISP’s. My task is to make load-sharing between those ISP's. For inbound traffic everything is clear - just use as-path prepend, but I want to split also outbound traffic from access layer host networks, for example 2 networks use 1st ISP connection and other 1 network uses 2nd ISP connection. If one connection fails , then all networks that use failed ISP will use another ISP. I want to know how to do it only with BGP. It may be some kind of PBR , but without next-hop attribute because that solucion will not be flexible(if link between border routers goes down - all load-sharing mechanism stops working) and also I don't want to use ip sla.
It is possibe to use vrf for that to make separate BGP instances for all host networks and then use weight or local preference for them, but it has bad scalability and again I just want to know how to do it with pure BGP. Below you can see BGP configurations of border routers. Thanks for your help!
BR3:
router ospf 1; router-id 10.1.255.2; redistribute bgp 200 subnets; passive-interface Ethernet0/2; default-information originate; router bgp 200; bgp router-id 10.1.255.2; bgp log-neighbor-changes; network 10.0.0.0 mask 255.255.255.0; network 10.0.1.0 mask 255.255.255.0; network 10.0.2.0 mask 255.255.255.0; neighbor 10.1.255.1 remote-as 200; neighbor 10.1.255.1 update-source Loopback0; neighbor 10.1.255.1 next-hop-self; neighbor 192.168.0.6 remote-as 101; maximum-paths 4;
BR4:
router ospf 1; router-id 10.1.255.1; redistribute bgp 200 subnets; passive-interface Ethernet0/1; default-information originate; router bgp 200; bgp router-id 10.1.255.1; bgp log-neighbor-changes; network 10.0.0.0 mask 255.255.255.0; network 10.0.1.0 mask 255.255.255.0; network 10.0.2.0 mask 255.255.255.0; neighbor 10.1.255.2 remote-as 200; neighbor 10.1.255.2 update-source Loopback0; neighbor 10.1.255.2 next-hop-self; neighbor 192.168.0.2 remote-as 100; maximum-paths 4;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 07:28 AM
Might you just OSPF ECMP from each core router to each of your BGP border routers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 08:02 AM - edited 02-22-2023 04:02 PM
Sorry my previous reply was for outbound control for inbound traffic.
inbound control for outbound traffic that hard since you received only defualt route from isp.
But I have one idea but I must sure before share it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 02:32 PM - edited 02-22-2023 02:34 PM
Hello
@Igor06032003 wrote:
but I want to split also outbound traffic from access layer host networks, for example 2 networks use 1st ISP connection and other 1 network uses 2nd ISP connection. If one connection fails , then all networks that use failed ISP will use another ISP. I want to know how to do it only with BGP.
I just want to know how to do it with pure BGP. Below you can see BGP configurations of border routers. Thanks for your help!
You can accommodate this by using the Local Preference attribute, based certain received prefixes from either ISP, thus selecting alternate paths, if a link to either ISP fails then, those prefixes from the failed ISP will be withdrawn and the backup ISP path will be selected.
I see also you have bgp multipath enabled however this at present will not work, due to the fact your two ebgp peerings are towards differing ASNs ,for multipath to succeed the bgp AS SET path needs to be identical unless that is you relax this rule with the following:
router bgp 200
bgp bestpath as-path multipath-relax
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 03:41 PM
"I see also you have bgp multipath enabled however this at present will not work, due to the fact your two ebgp peerings are towards differing ASNs ,for multipath to succeed the bgp AS SET path needs to be identical unless that is you relax this rule with the following:"
I'm far from being proficient in BGP, but for eBGP multipath to work, same AS or different ASs, wouldn't the BGP router need links to both ISPs (unless we get into, possibly, eBGP multihop)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 03:59 PM
When I originally replied, a) I couldn't "see" attachment (using my phone) (can now, on my PC) and b) did I did not read your OP thoroughly enough, i.e. your focus on wanting to do this load sharing just using BGP and prefer a BGP path by source network (i.e. manually directed load sharing).
Now that I believe I better understand what your requirements are, beyond just load sharing your two WAN links for your LAN networks, as I noted in my reply to Paul's post, I don't consider myself proficient in BGP, so, unfortunately, don't believe I could help your manually traffic engineer your BGP to obtain your load sharing goals.
If Paul and MHM cannot help you, you might seek out, and @ reference some of our other VIPs, especially those that also appear proficient in BGP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2023 04:54 PM
first start from bottom,
config HSRP group
make R3 GW active for VLAN 10
make R4 GW active for VLAN 15
then change the OSPF cost for the cross connect link to be high than direct connect between R3/R4 and edge routes
this make R3/R4 prefer the direct connect Edge router than cross connect one.
when edge router receive the packet it will forward because BGP criteria prefer weights path.
that it.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2023 09:37 AM - edited 02-23-2023 09:37 AM
Thank you for suggestion, but I see 1 disadvantage of such configuration. For example we need VLAN 15 network sent through ISP 2 and if link between BR4 and R4 goes down - that traffic will go through ISP 1 even if link to ISP 2 from BR4 is still operational. The question now is how to configure BGP , so when traffic from VLAN 15 comes to BR3 - it then will go to BR4 and to ISP 2 accordingly and at the same time VLAN 10 traffic will go to its "primary" ISP 1 from BR3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2023 11:56 AM
""The question now is how to configure BGP ""
you mention how to config BGP the BGP is stop in edge route
what make the solution more difficult is you receive only default route.
then default route will inject into OSPF and OSPF can not separate the next-hop for each default route.
I have one more idea I will share here also
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 08:19 AM
BTW, is using just BGP really, really required?
What end result do you what to accomplish? Is the how it's accomplished as important as the end result?
Reason I ask these questions, I've seen proposed designs where some traffic has to go this way while other traffic needs to go that way, and when I ask why, the answer might be some traffic is more critical than other traffic (which is not unusual). But, if so, using QoS might be a better approach.
One simple issue I bring up, if some traffic is more important, and so you direct different kinds of traffic to different paths, what happens when one path fails? Not only do you lose that path's bandwidth, but now all traffic ends up on remaining path.
With QoS, you better guarantee more important traffic gets preferred handling, regardless of which path it takes.
A real-world example, to which I was personally involved, a large international company I was working for, wanted all remote sites to have dual WAN paths (and redundant hardware), as it was considered business critical that a site didn't drop totally off-line due to some single point of failure.
Great goal, but also great cost for dual international leased lines. So, to reduce WAN costs, leased lines were replaced by frame-relay, then by ATM and then by VPN MPLS. But all the private network WAN technologies were often much more expensive than an Internet connection.
So, for "less" important sites, VPN across Internet was used to replace one of the private WAN links.
But, with that, a new design goal was: "important" traffic should still use private WAN link, "less" important traffic should use Internet VPN.
After about a year or two, our international HQ figured out some way to route different traffic types across different paths.
In the meantime, in our regional HQ, we deployed identical QoS, across both private WAN and VPN Internet, and let traffic use either path. For all practical purposes, we got same results regardless of path (even running VoIP on both).
When international HQ finally came up with the kinds of traffic routing solution, and I showed them over a year of no problem actual operational results, including dealing with link failures, and asked, what happens when your "important" path fails, it was decided to use the QoS approach, everywhere. (Oh, and since Internet VPN worked so well, it was used more often as second WAN link.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2023 02:58 AM
I can't see how bgp could be used to solve this. Each router will use destination IP to route packets. If you want source IP then you have to use PBR. I think @MHM Cisco World have give you the easiest way to accomplish the goal for normal situations. Also, what @Joseph W. Doherty have pointed out, what is the goal? Is it really important that both ISP links is used when there is a failure? Or can you live with the fact that one link is unused when there is a failure. In my opinion, the failure of one link is not something that happens to often, unless there is long haul fiber. It is more common that a router crashes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide