- Cisco Community
- Technology and Support
- Networking
- Routing
- Cisco 2811 Routing between two Eth if. using GRE Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco 2811 Routing between two Eth if. using GRE Tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 12:29 AM - edited 03-04-2019 08:35 PM
Hello Forum,
I have established a VPN IPSec GRE tunnel to my counterparty. It's up and stable. Logged into the cisco router, I can make a telnet to a
server on Cpty-Side with
cisco2811# telnet 90.1.2.101 10170 /source-interface FastEthernet0/1
Trying 90.162.253.101, 10170 … Open
But I need the connection on another computer in my private Network (192.168.100.49). There is a Java Software that needs to connect to a server
within the network of the counterparty. Telnet from 192.168.100.49 to above address returns with time-out error.
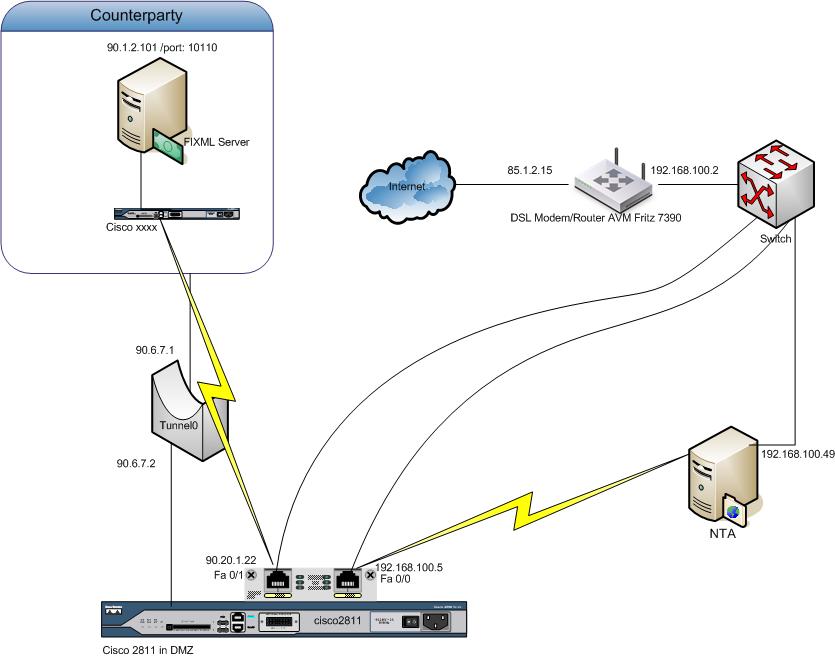
I've got the following information from Cpty:
|> Any connections attempts to FIX services should be sourced from the 90.20.1.0/24 network.
Additionally, my techn. Acct.Mgr. @Cpty says: If we get a request, we check if its came from 90.20.1.22 (my Fa0/1 address), otherwise it will
be rejected.
In fact the ip network 90.20.1.0/24 is not my network, it is an external company (BskyB) owned network. So I would assume I cannot change my
internal network address schema to their network schema.
Here my actual and funtionally config
interface Tunnel0
description To Cpty
ip address 90.6.7.2 255.255.255.0
tunnel source 192.168.100.5
tunnel destination 193.2.7.6
!
interface FastEthernet0/0
description Facing LAN
ip address 85.1.2.15 255.255.255.0 secondary
ip address 192.168.100.5 255.255.255.0
crypto map dbs
!
interface FastEthernet0/1
description MIC Member Lan
ip address 90.20.1.22 255.255.255.0
With this config the initial connection is up and running
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 192.168.100.5 YES manual up up
FastEthernet0/1 90.20.1.22 YES NVRAM up up
Tunnel0 90.6.7.2 YES NVRAM up up
Tunnel1 90.20.1.22 YES unset up up
Tunnel2 90.20.1.22 YES unset up up
cisco2811#show crypto session
Crypto session current status
Interface: FastEthernet0/0
Session status: UP-ACTIVE
Peer: 193.2.7.6 port 500
IKE SA: local 192.168.100.5/500 remote 193.2.7.6/500 Active
IPSEC FLOW: permit 47 host 192.168.100.5 host 193.2.7.6
Active SAs: 2, origin: crypto map
The ip route command shows many routes
cisco2811#show ip route
…cut...
Gateway of last resort is 192.168.100.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.100.2 10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
…cut…
D 90.15.2.0/24 [90/26881024] via 90.61.76.1, 00:21:35, Tunnel0
D 90.16.2.0/24 [90/26881024] via 90.61.76.1, 00:21:35, Tunnel0
C 90.20.1.0/24 is directly connected, FastEthernet0/1
L 90.20.1.22/32 is directly connected, FastEthernet0/1
192.168.100.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.100.0/24 is directly connected, FastEthernet0/0
L 192.168.100.5/32 is directly connected, FastEthernet0/0
…cut...
And I want to reach 90.16.2.101 on port 10170. On my 192.168.100.49, I set 192.168.100.5 as the default gateway but that was not enough.
Thus, I need IMHO something like: ip route all incoming traffic from FastEthernet0/0 with request to 90.* / 193.* --forward-to--> FastEthernet0/1
(like in the example
cisco2811#telnet 90.162.253.101 10170 /source-interface FastEthernet0/1
Trying 90.162.253.101, 10170 … Open
)
As I tried with: ip route 90.16.2.0 255.255.255.0 FastEthernet0/1
I lost even my telnet connection on board of the cisco. After deleting, I was again capable telnet from the cisco2811 console.
Or need I some kind of NATting with Fa0/0 and Fa0/1??
Please, take into account that my ADSL Router already performs NAT for my network. And the cisco is in the DMZ.
Thanks in advance.
Regards,
Celal
PS: For more in depth information about my network infrastructure or previous problem, please read
http://www.dslreports.com/forum/r28460073-Config-Review-requested-VPN-with-Cisco-behind-a-DSL-Router
There, I described earlier my problem with the establishing the tunnel (which is solved).
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-30-2013 12:34 AM
If they check source address, you would need NAT.
And that will make everything more complicated.
I recommend that you talk to the ownerof the company (the one that pays) so that he commands the other people to relax checks, re-organizer network, and make things works easy and smoothj without tricks.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide