- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Cisco IPSEC - Ubiquity USG
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco IPSEC - Ubiquity USG
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2019 10:54 PM
Hey Guys,
Can you please help me troubleshoot this?
I'm trying to setup IPSEC tunnel between Cisco 887VAMG2 (LAB) and Ubiquity USG.
crypto isakmp policy 10 encr aes hash md5 authentication pre-share group 14 lifetime 28800 crypto isakmp key XXXXXX address USG_IP crypto ipsec transform-set SET esp-aes esp-md5-hmac mode tunnel crypto map MAP 10 ipsec-isakmp set peer USG_IP set transform-set SET match address VPN set security-association lifetime seconds 3600 ip access-list extended VPN permit ip 192.168.90.0 0.0.0.255 192.168.2.0 0.0.0.255 int Di1 crypto map MAP
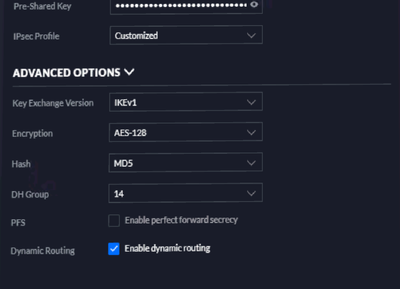
The USG interface is a bit simple and I can't figure out what P2 I need, below is the best I could find from Google:
My first question is which Interface should I apply policy map to?
Dialer, Physical Interface (Switchport), Vlan that is assigned to the interface?
Can you please tell from my debug why P2 is failing?
Dec 14 17:49:28.584 aesdt: ISAKMP-PAK: (2002):received packet from USG_IP dport 500 sport 500 Global (R) QM_IDLE
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):set new node -1952708874 to QM_IDLE
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):processing HASH payload. message ID = 2342258422
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):processing SA payload. message ID = 2342258422
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):Checking IPSec proposal 0
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):transform 1, ESP_AES
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): attributes in transform:
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): key length is 128
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): authenticator is HMAC-MD5
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): encaps is 1 (Tunnel)
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): SA life type in seconds
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002): SA life duration (basic) of 3600
Dec 14 17:49:28.584 aesdt: ISAKMP: (2002):atts are acceptable.
Dec 14 17:49:28.584 aesdt: ISAKMP-ERROR: (2002):IPSec policy invalidated proposal with error 32
Dec 14 17:49:28.588 aesdt: ISAKMP-ERROR: (2002):phase 2 SA policy not acceptable! (local CISCO_IP remote USG_IP)
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):set new node -503979134 to QM_IDLE
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):Sending NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 2321697552, message ID = 3790988162
Dec 14 17:49:28.588 aesdt: ISAKMP-PAK: (2002):sending packet to USG_IP my_port 500 peer_port 500 (R) QM_IDLE
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):Sending an IKE IPv4 Packet.
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):purging node -503979134
Dec 14 17:49:28.588 aesdt: ISAKMP-ERROR: (2002):deleting node -1952708874 error TRUE reason "QM rejected"
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):Node 2342258422, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Dec 14 17:49:28.588 aesdt: ISAKMP: (2002):Old State = IKE_QM_READY New State = IKE_QM_READY
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 12:16 AM
Hello,
post the full configuration of the Cisco. The crypto map needs to be applied to the Dialer, that looks good. The problem is most likely with the access list. Do you have the VPN traffic exempt from NAT ? Also, make sure that on the Ubiquity side, you have specified 192.168.90.0/24 under the 'Remote Subnets'. The thread below contains a GUI shot that is a bit more extensive...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 04:52 AM
Hey Mate,
Thank you! I've attached a slightly edited version.
Just as FYI, I've set up DMVP ( As part of studies), isakmp policy 1.
Cisco LAN: 192.168.90.0/24
USG LAN: 192.168.2.0/24
HOSTNAME#show run version 15.7 no service pad service tcp-keepalives-in service tcp-keepalives-out service timestamps debug datetime msec localtime show-timezone service timestamps log datetime msec localtime show-timezone service password-encryption ! hostname HOSTNAME ! boot-start-marker boot system flash:c880data-universalk9-mz.157-3.M5.bin boot system flash:c880data-universalk9-mz.157-3.M4a.bin boot-end-marker ! ! security passwords min-length 6 logging buffered 65536 ! no aaa new-model clock timezone aest 10 0 clock summer-time aesdt recurring 1 Sun Oct 2:00 1 Sun Apr 2:00 ! ! ! ! ! ! ! no ip source-route ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ip flow-cache timeout inactive 10 ip flow-cache timeout active 5 no ip bootp server ip domain name HOSTNAME ip name-server 1.1.1.1 ip name-server 1.0.0.1 ip multicast-routing ip cef login on-failure log login on-success log no ipv6 cef ! ! ! ! vtp mode transparent ! ! ! ! ! controller VDSL 0 ! controller Cellular 0 ! vlan 5 name Untagged_NBN ! track 1 ip sla 1 reachability ! track 2 ip sla 2 reachability ! track 3 ip sla 3 reachability ! ip tcp ecn ip tcp selective-ack ! ! ! ! crypto isakmp policy 1 encr 3des hash md5 authentication pre-share group 2 ! crypto isakmp policy 10 encr aes hash md5 authentication pre-share group 14 lifetime 28800 ! crypto isakmp key XXXXXXXX address USG_IP crypto isakmp key XXXXXXXX address 0.0.0.0 ! ! crypto ipsec transform-set TS esp-3des esp-md5-hmac mode tunnel crypto ipsec transform-set SET esp-aes esp-md5-hmac mode tunnel ! ! crypto ipsec profile protect-gre set security-association lifetime seconds 86400 set transform-set TS ! ! crypto map MAP 10 ipsec-isakmp set peer USG_IP set transform-set SET match address VPN ! ! ! ! ! interface Loopback0 ip address 10.10.10.10 255.255.255.255 no ip redirects no ip unreachables no ip proxy-arp ! interface Loopback5 ip address 1.1.1.1 255.255.255.255 ! interface Tunnel0 description mGRE - DMVPN Tunnel ip address 172.15.0.1 255.255.0.0 no ip redirects ip nhrp authentication XXXXXXXX ip nhrp network-id 1 tunnel source 1.1.1.1 tunnel mode gre multipoint tunnel protection ipsec profile protect-gre ! ! interface FastEthernet0 description WAN Link - Untagged NBN switchport access vlan 5 no ip address no cdp enable pppoe enable group global pppoe-client dial-pool-number 1 ! interface Vlan1 description LAN-Network ip address 192.168.90.1 255.255.255.0 no ip redirects no ip unreachables no ip proxy-arp ip flow monitor NetFlow input ip flow monitor NetFlow output ip flow ingress ip flow egress ip nat inside ip virtual-reassembly in ! interface Vlan2 ip address 192.168.10.1 255.255.255.0 ip flow monitor NetFlow input ip flow monitor NetFlow output ip flow ingress no autostate ! interface Vlan3 ip address 172.16.0.1 255.255.0.0 ip flow monitor NetFlow input ip flow monitor NetFlow output ip flow ingress no autostate ! interface Vlan5 no ip address ip flow monitor NetFlow input ip flow monitor NetFlow output ip flow ingress ip nat outside ip virtual-reassembly in ip tcp adjust-mss 1452 pppoe enable group global pppoe-client dial-pool-number 1 ! interface Dialer1 description WAN Link mtu 1492 ip address negotiated no ip proxy-arp ip flow ingress ip flow egress ip nat outside ip virtual-reassembly in encapsulation ppp ip tcp adjust-mss 1360 dialer pool 1 dialer idle-timeout 0 dialer persistent dialer-group 1 no cdp enable ppp authentication chap callin ppp chap hostname XXXXXXXX ppp chap password XXXXXXXX ppp ipcp route default crypto map MAP ! ! ! ip nat inside source list NAT interface Dialer1 overload ip route 0.0.0.0 0.0.0.0 Dialer1 ip ssh time-out 60 ip ssh source-interface Loopback0 ip ssh version 2 ! ip access-list extended NAT deny ip 192.168.90.0 0.0.0.255 192.168.2.0 0.0.0.255 permit ip 192.168.90.0 0.0.0.255 any ! ip access-list extended NTP permit ip host 203.193.193.11 any permit ip host 180.92.210.11 any deny ip any any ! ip access-list extended VPN
permit ip 192.168.90.0 0.0.0.255 192.168.2.0 0.0.0.255 ! kron occurrence Backup at 23:00 Sun recurring policy-list Config_Backup ! kron policy-list Config_Backup cli show run | redirect tftp://192.168.90.2/HOSTNAME-confg ! ! control-plane ! ! line con 0 exec-timeout 30 0 logging synchronous login local no modem enable line aux 0 line 3 script dialer hspa-R7 no exec line vty 0 4 access-class Remote_Access in exec-timeout 30 0 logging synchronous login local length 0 transport input ssh ! ntp access-group peer NTP ntp access-group serve NTP ntp server 203.193.193.11 ntp server 180.92.210.11 ! end
Latest Debug
Dec 14 23:48:13.426 aesdt: ISAKMP-PAK: (0):received packet from UNIFI_IP dport 500 sport 500 Global (N) NEW SA
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):Created a peer struct for UNIFI_IP, peer port 500
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):New peer created peer = 0x8DBC6D0C peer_handle = 0x80000225
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):Locking peer struct 0x8DBC6D0C, refcount 1 for crypto_isakmp_process_block
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):local port 500, remote port 500
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):insert sa successfully sa = 8BB70B28
Dec 14 23:48:13.426 aesdt: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Old State = IKE_READY New State = IKE_R_MM1
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing SA payload. message ID = 0
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 215 mismatch
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID is XAUTH
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID is DPD
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID is NAT-T v2
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):found peer pre-shared key matching UNIFI_IP
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):local preshared key found
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Scanning profiles for xauth ...
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Checking ISAKMP transform 1 against priority 1 policy
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): encryption AES-CBC
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): keylength of 128
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): hash MD5
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): default group 14
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): auth pre-share
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): life type in seconds
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): life duration (basic) of 28800
Dec 14 23:48:13.430 aesdt: ISAKMP-ERROR: (0):Encryption algorithm offered does not match policy!
Dec 14 23:48:13.430 aesdt: ISAKMP-ERROR: (0):atts are not acceptable. Next payload is 0
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Checking ISAKMP transform 1 against priority 10 policy
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): encryption AES-CBC
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): keylength of 128
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): hash MD5
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): default group 14
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): auth pre-share
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): life type in seconds
Dec 14 23:48:13.430 aesdt: ISAKMP: (0): life duration (basic) of 28800
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):atts are acceptable. Next payload is 0
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Acceptable atts:actual life: 28800
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Acceptable atts:life: 0
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Basic life_in_seconds:28800
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Returning Actual lifetime: 28800
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):Started lifetime timer: 28800.
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 215 mismatch
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):vendor ID is XAUTH
Dec 14 23:48:13.430 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):vendor ID is DPD
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 69 mismatch
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):vendor ID is NAT-T RFC 3947
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):processing vendor id payload
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):vendor ID seems Unity/DPD but major 123 mismatch
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):vendor ID is NAT-T v2
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM1
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):constructed NAT-T vendor-rfc3947 ID
Dec 14 23:48:13.434 aesdt: ISAKMP-PAK: (0):sending packet to UNIFI_IP my_port 500 peer_port 500 (R) MM_SA_SETUP
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):Sending an IKE IPv4 Packet.
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Dec 14 23:48:13.434 aesdt: ISAKMP: (0):Old State = IKE_R_MM1 New State = IKE_R_MM2
Dec 14 23:48:14.033 aesdt: ISAKMP-PAK: (0):received packet from UNIFI_IP dport 500 sport 500 Global (R) MM_SA_SETUP
Dec 14 23:48:14.033 aesdt: ISAKMP: (0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Dec 14 23:48:14.033 aesdt: ISAKMP: (0):Old State = IKE_R_MM2 New State = IKE_R_MM3
Dec 14 23:48:14.033 aesdt: ISAKMP: (0):processing KE payload. message ID = 0
Dec 14 23:48:14.373 aesdt: ISAKMP: (0):processing NONCE payload. message ID = 0
Dec 14 23:48:14.373 aesdt: ISAKMP: (0):found peer pre-shared key matching UNIFI_IP
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):received payload type 20
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):His hash no match - this node outside NAT
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):received payload type 20
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):No NAT Found for self or peer
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Dec 14 23:48:14.373 aesdt: ISAKMP: (2006):Old State = IKE_R_MM3 New State = IKE_R_MM3
Dec 14 23:48:14.377 aesdt: ISAKMP-PAK: (2006):sending packet to UNIFI_IP my_port 500 peer_port 500 (R) MM_KEY_EXCH
Dec 14 23:48:14.377 aesdt: ISAKMP: (2006):Sending an IKE IPv4 Packet.
Dec 14 23:48:14.377 aesdt: ISAKMP: (2006):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Dec 14 23:48:14.377 aesdt: ISAKMP: (2006):Old State = IKE_R_MM3 New State = IKE_R_MM4
Dec 14 23:48:14.921 aesdt: ISAKMP-PAK: (2006):received packet from UNIFI_IP dport 500 sport 500 Global (R) MM_KEY_EXCH
Dec 14 23:48:14.921 aesdt: ISAKMP: (2006):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Dec 14 23:48:14.921 aesdt: ISAKMP: (2006):Old State = IKE_R_MM4 New State = IKE_R_MM5
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):processing ID payload. message ID = 0
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):ID payload
next-payload : 8
type : 1
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006): address : UNIFI_IP
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006): protocol : 0
port : 0
length : 12
Dec 14 23:48:14.925 aesdt: ISAKMP: (0):peer matches *none* of the profiles
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):processing HASH payload. message ID = 0
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 0x8BB70B28
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):SA authentication status:
authenticated
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):SA has been authenticated with UNIFI_IP
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):SA authentication status:
authenticated
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):Process initial contact,
bring down existing phase 1 and 2 SA's with local *CISCO_IP* remote UNIFI_IP remote port 500
Dec 14 23:48:14.925 aesdt: ISAKMP: (0):Trying to insert a peer *CISCO_IP*/UNIFI_IP/500/,
Dec 14 23:48:14.925 aesdt: ISAKMP: (0): and inserted successfully 8DBC6D0C.
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):Old State = IKE_R_MM5 New State = IKE_R_MM5
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):SA is doing
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):pre-shared key authentication using id type ID_IPV4_ADDR
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):ID payload
next-payload : 8
type : 1
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006): address : *CISCO_IP*
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006): protocol : 17
port : 500
length : 12
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):Total payload length: 12
Dec 14 23:48:14.925 aesdt: ISAKMP-PAK: (2006):sending packet to UNIFI_IP my_port 500 peer_port 500 (R) MM_KEY_EXCH
Dec 14 23:48:14.925 aesdt: ISAKMP: (2006):Sending an IKE IPv4 Packet.
Dec 14 23:48:14.929 aesdt: ISAKMP: (2006):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Dec 14 23:48:14.929 aesdt: ISAKMP: (2006):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
Dec 14 23:48:14.929 aesdt: ISAKMP: (2006):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Dec 14 23:48:14.929 aesdt: ISAKMP: (2006):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Dec 14 23:48:14.953 aesdt: ISAKMP-PAK: (2006):received packet from UNIFI_IP dport 500 sport 500 Global (R) QM_IDLE
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):set new node 1114197406 to QM_IDLE
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):processing HASH payload. message ID = 1114197406
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):processing SA payload. message ID = 1114197406
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):Checking IPSec proposal 0
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):transform 1, ESP_AES
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): attributes in transform:
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): key length is 128
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): authenticator is HMAC-MD5
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): encaps is 1 (Tunnel)
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): SA life type in seconds
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006): SA life duration (basic) of 3600
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):atts are acceptable.
Dec 14 23:48:14.953 aesdt: ISAKMP-ERROR: (2006):IPSec policy invalidated proposal with error 32
Dec 14 23:48:14.953 aesdt: ISAKMP-ERROR: (2006):phase 2 SA policy not acceptable! (local *CISCO_IP* remote UNIFI_IP)
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):set new node -366060285 to QM_IDLE
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):Sending NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 2321697552, message ID = 3928907011
Dec 14 23:48:14.953 aesdt: ISAKMP-PAK: (2006):sending packet to UNIFI_IP my_port 500 peer_port 500 (R) QM_IDLE
Dec 14 23:48:14.953 aesdt: ISAKMP: (2006):Sending an IKE IPv4 Packet.
Dec 14 23:48:14.957 aesdt: ISAKMP: (2006):purging node -366060285
Dec 14 23:48:14.957 aesdt: ISAKMP-ERROR: (2006):deleting node 1114197406 error TRUE reason "QM rejected"
Dec 14 23:48:14.957 aesdt: ISAKMP: (2006):Node 1114197406, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Dec 14 23:48:14.957 aesdt: ISAKMP: (2006):Old State = IKE_QM_READY New State = IKE_QM_READY
Dec 14 23:49:04.954 aesdt: ISAKMP: (2006):purging node 1114197406
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 05:21 AM
Hello,
you now have mixed both the SVTI and the crypto map together in one configuration, which makes it hard to tell what is using what. Try and clean it up so just the VTI remains.
Also, use this transform set:
crypto ipsec transform-set SET esp-3des esp-md5-hmac
mode tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 12:20 PM
Hey Mate,
I've removed the config for tunnels but, I'm seeing this.
Is my issue NAT related?
.Dec 15 07:13:59.576 aesdt: ISAKMP: (0):processing KE payload. message ID = 0
.Dec 15 07:13:59.792 aesdt: ISAKMP: (0):processing NONCE payload. message ID = 0
.Dec 15 07:13:59.792 aesdt: ISAKMP: (0):found peer pre-shared key matching XXXX
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):received payload type 20
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):His hash no match - this node outside NAT
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):received payload type 20
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):No NAT Found for self or peer
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
.Dec 15 07:13:59.792 aesdt: ISAKMP: (2008):Old State = IKE_R_MM3 New State = IKE_R_MM3
.Dec 15 07:16:46.807 aesdt: ISAKMP-ERROR: (2008):IPSec policy invalidated proposal with error 32
.Dec 15 07:16:46.807 aesdt: ISAKMP-ERROR: (2008):phase 2 SA policy not acceptable! (local XXXX remote XXXX)
.Dec 15 07:16:46.807 aesdt: ISAKMP: (2008):set new node 778644462 to QM_IDLE
.Dec 15 07:16:46.807 aesdt: ISAKMP: (2008):Sending NOTIFY PROPOSAL_NOT_CHOSEN protocol 3
spi 2321697552, message ID = 778644462
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 12:37 PM
Hello,
post your current configuration again...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 12:52 PM
Hello,
actually, you need to decide first what you want to configure: a DMVPN (hub or spoke), an SVTI, or a legacy crypto map site to site VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 01:53 PM - edited 12-14-2019 01:54 PM
Sorry just for clarification, the DMVPN was already there prior to me trying to setup IPSEC. It's from my previous studies, and I've removed it all together now.
version 15.7 no service pad service tcp-keepalives-in service tcp-keepalives-out service timestamps debug datetime msec localtime show-timezone service timestamps log datetime msec localtime show-timezone service password-encryption ! hostname XXXXXXX ! boot-start-marker boot system flash:c880data-universalk9-mz.157-3.M5.bin boot system flash:c880data-universalk9-mz.157-3.M4a.bin boot-end-marker ! ! security passwords min-length 6 logging buffered 65536 ! no aaa new-model clock timezone aest 10 0 clock summer-time aesdt recurring 1 Sun Oct 2:00 1 Sun Apr 2:00 ! ! ! ! ! ! ! no ip source-route ! ! ! ! ! ! ! ! ! ! ! ip flow-cache timeout inactive 10 ip flow-cache timeout active 5 no ip bootp server ip domain name XXXXXXX ip name-server 1.1.1.1 ip name-server 1.0.0.1 ip multicast-routing ip cef login on-failure log login on-success log no ipv6 cef ! ! ! ! vtp mode transparent ! ! ! ! ! controller VDSL 0 ! controller Cellular 0 ! vlan 5 name Untagged_NBN ! ! ip tcp ecn ip tcp selective-ack ! ! ! ! crypto isakmp policy 10 encr aes hash md5 authentication pre-share group 14 lifetime 28800 crypto isakmp key XXXXXXX address X.X.X.X ! ! crypto ipsec transform-set SET esp-aes esp-md5-hmac mode tunnel ! ! ! crypto map MAP 10 ipsec-isakmp set peer X.X.X.X set transform-set SET match address VPN ! ! ! ! ! interface Loopback0 ip address 10.10.10.10 255.255.255.255 no ip redirects no ip unreachables no ip proxy-arp ! interface Loopback5 ip address 1.1.1.1 255.255.255.255 ! interface Ethernet0 description VDSL Eth0 no ip address shutdown ! interface ATM0 description ADSL Link no ip address no ip redirects no ip proxy-arp shutdown no atm ilmi-keepalive pvc 8/35 vbr-nrt 650 650 encapsulation aal5mux ppp dialer dialer pool-member 1 ! ! interface FastEthernet0 description WAN Link - Untagged NBN switchport access vlan 5 no ip address no cdp enable pppoe enable group global pppoe-client dial-pool-number 1 crypto map MAP ! interface FastEthernet1 description RaspberryPi no ip address ! interface FastEthernet2 description Fortigate_100D no ip address ! interface FastEthernet3 description WS-C3560-48PS no ip address ! interface Cellular0 no ip address encapsulation slip dialer in-band dialer string hspa-R7 ! interface Vlan1 description LAN-Network ip address 192.168.90.1 255.255.255.0 no ip redirects no ip unreachables no ip proxy-arp ip nat inside ip virtual-reassembly in ! interface Vlan2 ip address 192.168.10.1 255.255.255.0 no autostate ! interface Vlan3 ip address 172.16.0.1 255.255.0.0 no autostate ! interface Vlan5 no ip address ip nat outside ip virtual-reassembly in ip tcp adjust-mss 1452 pppoe enable group global pppoe-client dial-pool-number 1 ! interface Dialer1 description WAN Link mtu 1492 ip address negotiated no ip proxy-arp ip nat outside ip virtual-reassembly in encapsulation ppp ip tcp adjust-mss 1360 dialer pool 1 dialer idle-timeout 0 dialer persistent dialer-group 1 no cdp enable ppp authentication chap callin ppp chap hostname XXXXXXX ppp chap password XXXXXXX ppp ipcp route default
crypto map MAP ! ! router eigrp 1 network 171.16.0.0 network 192.168.10.0 network 192.168.90.0 passive-interface FastEthernet0 passive-interface Dialer1 ! router ospf 2 router-id 192.168.2.1 redistribute bgp 1 subnets tag 90 passive-interface Dialer1 passive-interface FastEthernet0 network 0.0.0.0 255.255.255.255 area 0 ! router bgp 1 bgp log-neighbor-changes network 1.1.1.1 network 10.10.10.10 mask 255.255.255.255 network 172.16.0.0 network 192.168.8.0 network 192.168.10.0 neighbor 192.168.90.5 remote-as 3 neighbor 192.168.90.6 remote-as 2 ! ip forward-protocol nd no ip http server no ip http secure-server ! ip flow-capture packet-length ip flow-capture icmp ip flow-capture mac-addresses ip flow-top-talkers top 50 sort-by bytes ! ip nat inside source list NAT interface Dialer1 overload ip route 0.0.0.0 0.0.0.0 Dialer1 ip ssh time-out 60 ip ssh source-interface Loopback0 ip ssh version 2 ! ip access-list extended NAT deny ip 192.168.90.0 0.0.0.255 192.168.2.0 0.0.0.255 permit ip 192.168.90.0 0.0.0.255 any ip access-list extended NTP permit ip host 203.193.193.11 any permit ip host 180.92.210.11 any deny ip any any ip access-list extended VPN permit ip 192.168.90.0 0.0.0.255 0.0.0.0 255.255.255.0 ! ! logging trap debugging logging facility syslog ipv6 ioam timestamp ! line con 0 exec-timeout 30 0 logging synchronous login local no modem enable line aux 0 line 3 script dialer hspa-R7 no exec line vty 0 4 access-class Remote_Access in exec-timeout 30 0 logging synchronous login local length 0 transport input ssh ! ntp access-group peer NTP ntp access-group serve NTP ntp server 203.193.193.11 ntp server 180.92.210.11 ! end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 02:51 PM
Hello,
which physical interface is connected to your ISP ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 02:57 PM
interface FastEthernet0
It's this :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2019 04:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2019 12:04 AM
Hello,
so it is working now with the last configuration you have posted ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide