- Cisco Community
- Technology and Support
- Networking
- Routing
- Confused about route-maps, prefix-lists, acl's, and distribution-lists
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Confused about route-maps, prefix-lists, acl's, and distribution-lists
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-15-2021 10:53 AM - edited 01-15-2021 10:55 AM
So before I start, I am currently CCNA certified and working on CCNP. I understand this much...
- prefix-lists and access-lists are used to collect a pool of IP's or subnets to compare and contrast from
- route-maps and distribution-lists look to those prefix-lists and access-lists or other criteria to make a decision on how to handle those pools of IP's, whether to permit them, forward them, block them from entering the AS or routing table.
- distribution-lists only affect the IP routing table, not the AS topology information, meaning if R1, a DR in an OSPF topology within area 0 were using a distribution-list to block network 192.168.5.0/24 - it would only block it from R1's routing table (show ip route) rather than the OSPF topology (show ip ospf topology) so 192.168.5.0/24 would still propogate to other routers ospf topology and ip routing table if there were no additional filters preventing it from doing so.
- As for route-maps - they can do alot of stuff from what I'm gathering, blocking or permitting traffic is only one of them, they can also redistribute traffic along another path using a next-hop argument. Anyway though, in this context, a route-map would block the network from the entire AS if its implemented on a ASBR.
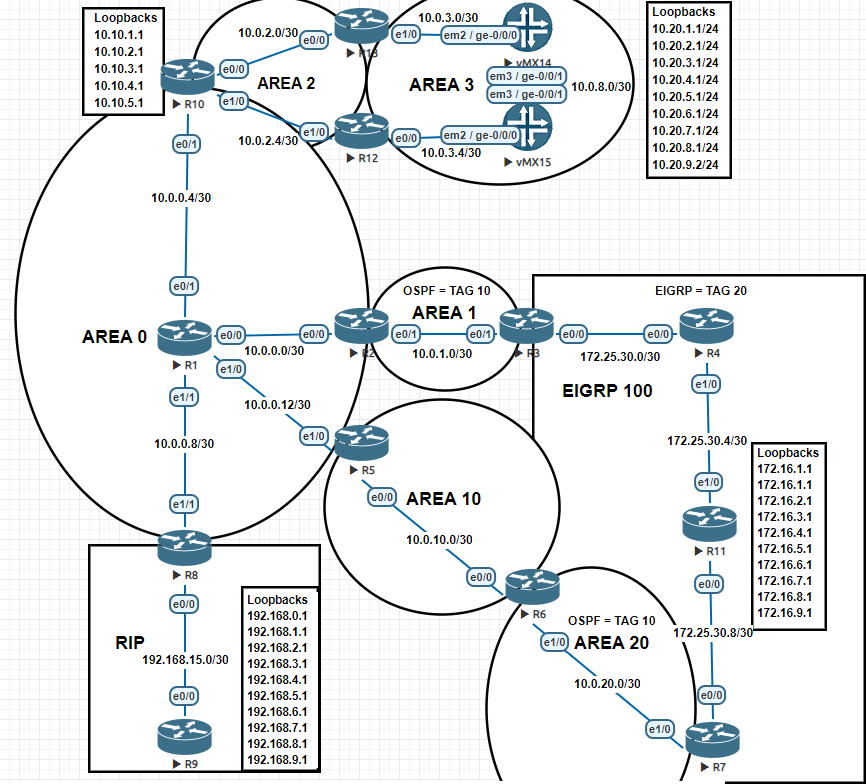
Now what I'm having difficulty with are the actual uses of ip-prefix lists or acl's with route-maps and the most effective way to use them. Lets say for example I wanted to redistribute OSPF to EIGRP and there were two ASBR's for the same AS's and I want to tag traffic to ensure that there are no loops...
R3 is between EIGRP 100 and OSPF 1 Area 1
R3 and R7 are ASBR's between OSPF 1 and EIGRP 100
R5 & R6 have virtual-link configured to give R7 access to Area 0
So now the question.. ..what would be the most effective way to...
Block IP's 10.20.0.0 thru 10.20.5.255 from entering the EIGRP routing table with the least amount of commands?
This is what I did on R3 and R7
ip prefix-list OSPF_Filter deny 10.20.0.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.1.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.5.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.2.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.3.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.4.0/24 le 32 ip prefix-list OSPF_Filter deny 10.20.5.0/24 le 32 ip prefix-list OSPF_Filter permit 0.0.0.0/0 le 32 route-map OSPF-EIGRP permit 5 set tag 20 match ip address prefix-list OSPF_Filter route-map OSPF-EIGRP deny 10 match tag 10 route-map EIGRP-OSPF permit 5 set tag 10 route-map EIGRP-OSPF deny 10 match tag 20 router eigrp 100 redistribute ospf 1 metric 10000 100 255 1 1500 route-map OSPF-EIGRP router ospf 1 redistribute eigrp 100 subnets route-map EIGRP-OSPF
Are the tags set correctly above?
I can't help but feel that this approach was very cumbersome and there should be an easier way to approach it with less statements or through summarization. Problem is if I summarize that route in the prefix-list I end up with a 10.20.0.0/28 which will also block unintended networks.
- Can you use route summaries in prefix-lists to block out everything in the summarized route?
- Can you modify the ge / le qualifiers in this example to only include 10.20.0.0 thru 10.20.5.255?
- What would happen if my prefix-list instead permitted the routes and denied 0.0.0.0/0 le 32 (is that even necessary, this should be implicitly denied right?) If I did that, how would I implement it on the route-map to block the IP's permitted in the prefix-list? Would this be appropriate or would it block out all routes? Would the below be appropiate? If not, what would be best to filter those nodes out from the EIGRP routing table while keeping it in this syntax (with the prefix-lists permitting).
ip prefix-list OSPF_Filter permit 10.20.0.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.1.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.5.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.2.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.3.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.4.0/24 le 32 ip prefix-list OSPF_Filter permit 10.20.5.0/24 le 32 ip prefix-list OSPF_Filter deny 0.0.0.0/0 le 32 route-map OSPF-EIGRP permit 5 set tag 20 route-map OSPF-EIGRP deny 10 match tag 10 match ip address prefix-list OSPF_Filter route-map EIGRP-OSPF permit 5 set tag 10 route-map EIGRP-OSPF deny 10 match tag 20
- Labels:
-
Other Routing
-
Routing Protocols
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-16-2021 07:55 AM
Hello @MikeAW2010 ,
a lot of questions indeed.
First of all, for OSPF topology to work you will need virtual links between R10 and R12 and between R10 and R13.
Coming to your questions the following notes apply:
a ) Are the tags set correctly above?
in your first config example they are.
b) I can't help but feel that this approach was very cumbersome and there should be an easier way to approach it with less statements or through summarization. Problem is if I summarize that route in the prefix-list I end up with a 10.20.0.0/28 which will also block unintended networks.
The approach is correct as you noted if you have used a single line prefix-list using 10.20.0.0/21 you could stop redistribution of other component routes.
c) Can you use route summaries in prefix-lists to block out everything in the summarized route?
Yes using
ip prefix-list OSPF_Filter deny 10.20.0.0/22 le 32
ip prefix-list OSPF_Filter deny 10.20.5.0/24 le 32
ip prefix-list OSPF_Filter permit 0.0.0.0/0 le 32
d) Can you modify the ge / le qualifiers in this example to only include 10.20.0.0 thru 10.20.5.255?
No, all you can find is to use base block 10.20.0,0/22 as described above
e)
if you want to use a prefix-list that permits the prefixes to be denied the prefix-list has to be invoked within a route-map clause with action deny.
But you need a specific rouute-map clause for this that cannot be combined with the other one denying routes with tag 10.
so you would need
no
no route-map OSPF-EIGRP permit 5
route-map OSPF-EIGRP deny 10
match address prefix-list OSPF-FILTER
route-map OSPF-EIGRP deny 20
match tag 10
route-map OSPF-EIGRP permit 30
set tag 20
because the order of operations is very important
you first deny unwanted OSPF routes
you then deny routes already redistributed
finally you permit everything else
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-17-2021 12:41 AM
Thanks a ton.
Here is another question. In what circumstances would you prefer prefix-lists over access-lists or vice versa?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2021 12:24 AM
Hello @MikeAW2010 ,
for route filtering prefix-lists are to be preferred as they have been introduced for this specific purpose.
Being a specialized tool prefix-lists allows to express complex requirements that would be difficult or impossible to express with standard IP ACL and even with extended IP ACLs
ip prefix-list EXAMPLE permit 10.100.0.0/16 ge 18 le 27
this means allows all component prefixes of 10.100.0.0/16 with a prefix-length between 18 and 27 inclusive.
Prefix-lists are also more efficient.
To be noted that only BGP allowed to use IP extended ACLs for route filtering but it would be difficult to write an IP extended ACL equivalent to the prefix-list reported above.
For user traffic filtering and for route-maps used for PBR IP ACLs have to be used.
Hope to help
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide