- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Creating an ACL to block access to some servers but not all
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 01:39 AM - edited 03-05-2019 11:02 AM
Hey guys, this is my first question in this community!
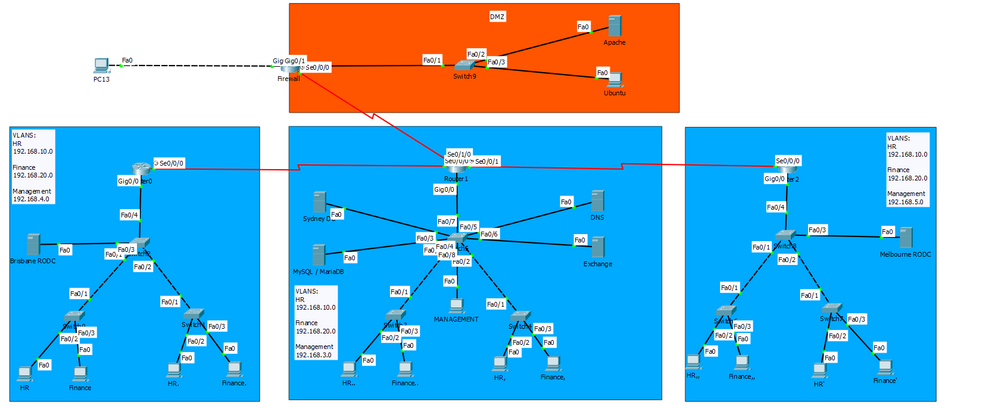
I need to create an ACL that blocks access to Sydney DC, and DNS servers but allow access to MySQL, Exchange and Apache. The traffic is coming IN from PC13 (in the top left of the image).
I've been stuck on this for days.
PC13 IP: 192.168.7.2
Sydney DC: 192.168.3.2
MySQL: 192.168.3.3
DNS: 192.168.3.4
Exchange: 192.168.3.5
Apache: 192.168.6.3
Thanks for any help guys, it is hugely appreciated!
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
WAN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 01:46 AM
Hello,
the below should work:
access-list 101 deny ip host 192.168.7.2 host 192.168.3.2
access-list 101 deny ip host 192.168.7.2 host 192.168.3.4
access-list 101 permit ip host 192.168.7.2 host 192.168.3.3
access-list 101 permit ip host 192.168.7.2 host 192.168.3.5
access-list 101 permit ip host 192.168.7.2 host 192.168.6.3
!
interface GigabitEthernet0/1
ip access-group 101 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 01:46 AM
Hello,
the below should work:
access-list 101 deny ip host 192.168.7.2 host 192.168.3.2
access-list 101 deny ip host 192.168.7.2 host 192.168.3.4
access-list 101 permit ip host 192.168.7.2 host 192.168.3.3
access-list 101 permit ip host 192.168.7.2 host 192.168.3.5
access-list 101 permit ip host 192.168.7.2 host 192.168.6.3
!
interface GigabitEthernet0/1
ip access-group 101 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 03:07 AM
Should I be applying this ACL on my Firewall (Router) ?
Thankyou!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 03:20 AM
Just a hint, the answer you selected would prevent the PC13 from going to the rest of network so it will go only the one permitted ones
access-list 101 permit ip host 192.168.7.2 host 192.168.3.3
access-list 101 permit ip host 192.168.7.2 host 192.168.3.5
access-list 101 permit ip host 192.168.7.2 host 192.168.6.3
!
anything else will not be reachable to it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 11:31 AM - edited 11-04-2018 11:32 AM
Hello
@bobIT wrote:
Hi, thankyou so much for your response!
Should I be applying this ACL on my Firewall (Router) ?
Thankyou!
Is this actually a real firewall or a router acting as a firewall? - Either way it looks like from your topology PC13 is connecting to this firewall/router.
However it wouldn't just be the case of applying an acl to an interface because Firewalls or Routers running ios firewalls have different ways of applying access control lists, So can you confirm on what security device PC13 is connecting to?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2018 05:37 AM
Yes the firewall is actually just a router simulating a firewall. My apologies for not clarifying in the op
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2018 11:24 AM
Hello
@bobIT wrote:
Hi!
Yes the firewall is actually just a router simulating a firewall. My apologies for not clarifying in the op
So then it wont just be a matter of applying a acl to an interface if your ruining zbfw?
Can you confirm how you have the ios fw setup?
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2018 01:47 AM
try this
ip access-list extended NO-PC13
deny ip host 192.168.7.2 host 192.168.3.4
deny ip host 192.168.7.2 host 192.168.3.2
permit ip any any
Apply on router serial inbound direction.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide