- Cisco Community
- Technology and Support
- Networking
- Routing
- Disaster Recovery - Redundant VPN Tunnels
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2011 09:38 AM - edited 03-04-2019 01:09 PM
Hello all, thanks in advance for your expertise.
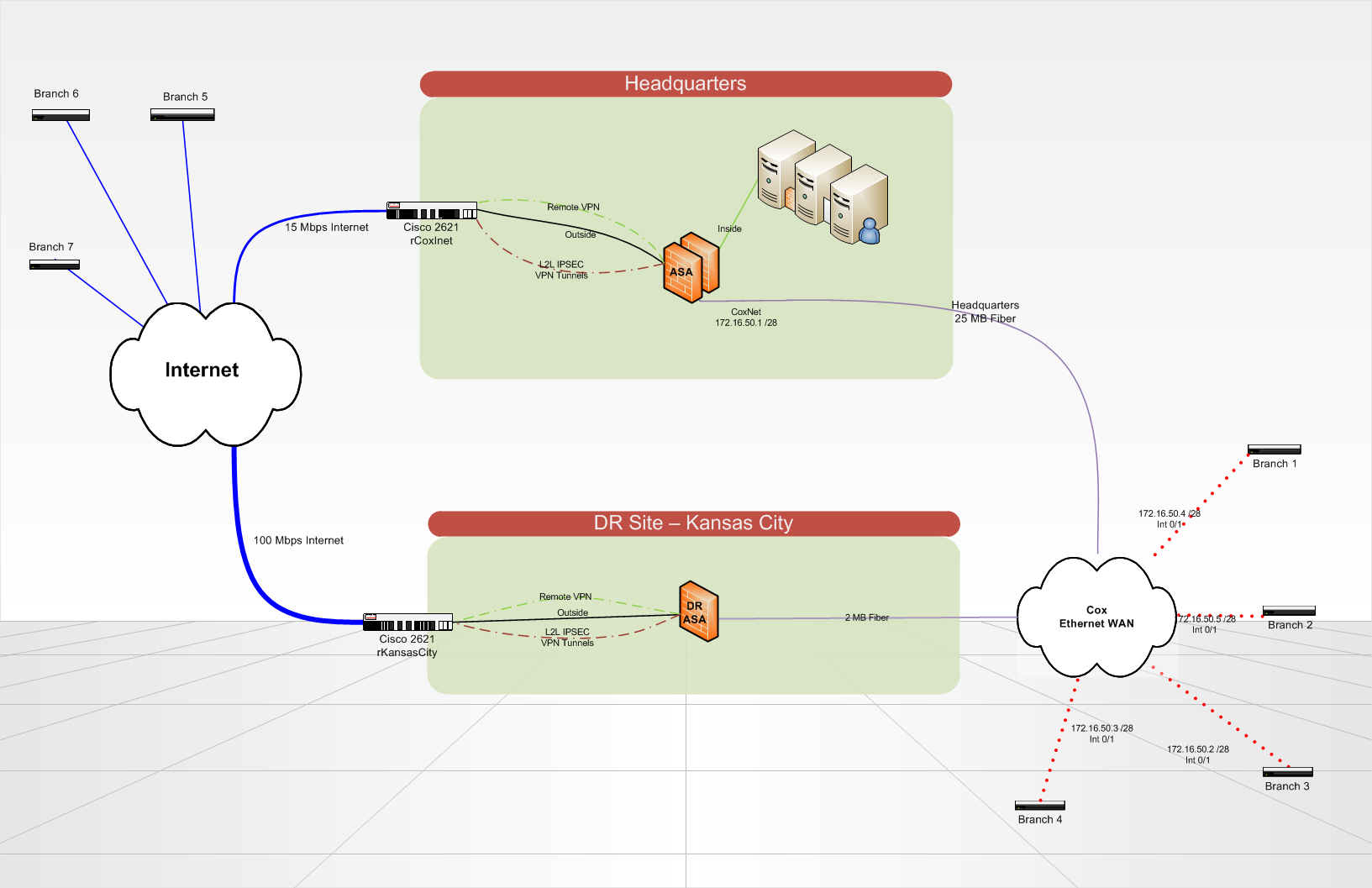
We are setting up a disaster recovery site which will host redundant copies of our servers and critical data in Kansas City. In the case of a disaster, our headquarters site would be totally gone.
Currently we have 7 branch offices that communicate to our HQ via VPN tunnels (either over an Internet circuit, or over a Cox Communications Ethernet WAN circuit). The branch sites each have a 2821 Cisco ISR Router. At the headquarters and at the DR site, we use a Cisco ASA 5510 to terminate the VPN tunnels and do all of our backbone routing. Routing on the ASA and on the branch routers is all static, using a routing protocol would be a nice upgrade in the future..any ideas? We use lan-2-lan IPSEC VPN tunnels, no GRE/VPN is in use because the ASA does not terminate it.
What is the best way to setup my branch routers to automatically or manually fail-over to connect to a different ASA at the DR site?
Also, if my Headquarters site is still up, but either my Internet circuit or the Cox ethernet circuit at the headquarters goes down. How can I re-route all traffic in a loop back to the headquarters over the one good remaining circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 03:45 PM
Hi,
You need to setup two site to site VPN tunnels from the branches to the head quarter and the DR sites with (IP SLA Tracking).
So each branch will trigger a failure of any of it's WAN link dynamically without the need of manuall intervention.
You would also need to setup LAN to LAN IPSec between your HQ and the DR to be used for detouring traffic incase of any Wan failure.
However, from a design approach, I would suggest different way but this depends on your future plan. In any way, the above should be a solution with your current setup.
Regards,
Mohamed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 09:32 AM
Anybody?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 11:33 AM
Research GRE over VPN or DMVPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 11:36 AM
I have and it looks like they are limited to Cisco IOS routers. I am terminating my VPN tunnels at the headquarters and DR site with a Cisco ASA. The ASA does not support GRE over VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 03:45 PM
Hi,
You need to setup two site to site VPN tunnels from the branches to the head quarter and the DR sites with (IP SLA Tracking).
So each branch will trigger a failure of any of it's WAN link dynamically without the need of manuall intervention.
You would also need to setup LAN to LAN IPSec between your HQ and the DR to be used for detouring traffic incase of any Wan failure.
However, from a design approach, I would suggest different way but this depends on your future plan. In any way, the above should be a solution with your current setup.
Regards,
Mohamed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 03:48 PM
Thanks for your reply Mohamed,
I like your plan as well. I think I'll be going that route.
From a design approach, what suggestions would you make? How would you change the design?
Lucas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2011 04:29 PM
Lucas,
There is some limitation in your current design. As well as I wouldn't rely on static routing in my all configuration here.
For example, with the current setup, you can't have a multicast deployed which is one of the main deployment now adage.
What I would do here if it's a choice, is to terminate all wan links on the HQ and DR sites to a WAN routers that supports DMVPN. Or if it's not, then having GRE Tunnels over IPSec from the branches to both hubs.
We have recently designed and implemented similar setup over L3-MPLS-VPN, I had BGP running between my HQ and DR site links with additional tuning to trigger a failure faster than it normally does.
I still have the same firewalls in place providing additional protection to both DMZ and internal users. But this protection is only from the Internet since I have already secured WAN.
Regards,
Mohamed
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
