- Cisco Community
- Technology and Support
- Networking
- Routing
- All your incoming traffic to
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2017 11:56 PM - edited 03-05-2019 08:22 AM
Please see the attached layout:
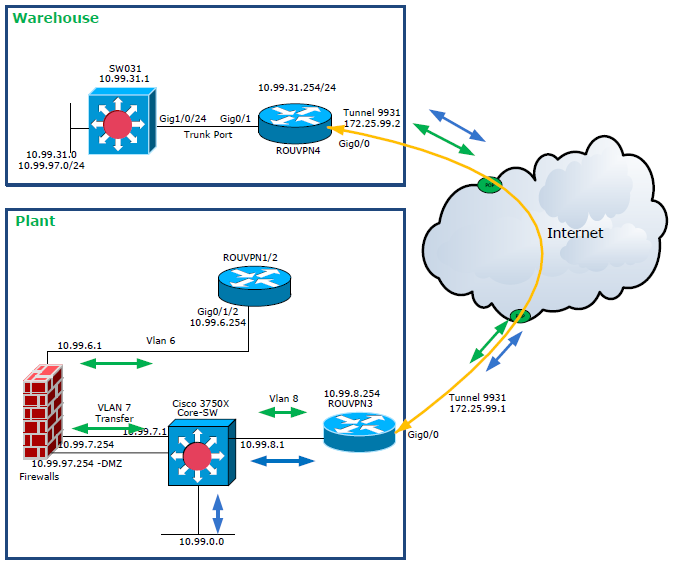
VLAN 97(DMZ) Default Gateway is on Firewall and i want allow whole subnet IP address(10.99.97.0/24) on warehouse via VPN but its not working.(cant ping from firewall.....traffic is not passing via FW)
Please provide me the guidance or solution to do it!!!
Thanks in advance
Solved! Go to Solution.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2017 07:47 AM
I meant to say to replace 10.99.97.x/24 you can use a new subnet, but if you are already using 10.99.31.0/24 there and if it's okay to use that subnet to communicate with DMZ network at site Plant then that's fine too. And it looks like you are using ROUVPN4 as the default gateway for
10.99.31.0/24 network. If you need to create a new network at the warehouse then you will also need to create a new sub-interface at G0/1 of ROUVPN4 as the default-gateway for that new network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 02:12 AM
Hi,
Thanks for the help.
Lets take another network 10.99.32.0/24.... (also created a sub-interface on ROUVPN4 ?)
Current case:
10.99.31.254/24 , 10.99.32.254/24 - on ROUVPN4
10.99.31.1/24 , 10.99.32.1/24, Default Gateway:10.99.31.254 - SW031
Is it ok ?
what should i do now to forward the traffic von 10.99.32.0/24 to DMZ interface of firewall ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 04:32 AM
You mentioned you created a sub-interface under g0/1 (based on the diagram it's a trunk port on router 4) for network 10.99.32.0/24. What's the default gateway for 10.99.32.0/24? is it 10.99.32.254/24? and are you able to ping 10.99.32.254/24 from a host on network 10.99.32.0/24?
Once you have all this working then just make sure that routing is in place whether you are static routing or some dynamic routing protocol. You may have to work with firewall admin to allow this network to pass through the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 04:46 AM
Firewall allowed this network.
yes I created sub-interface(10.55.32.254) on ROUVPN4.
GW in VLAN 32 is 10.99.32.254 and yes i can ping from Host (10.99.32.200) to Default Gateway.
Also configured the static routing on Core-Switch , VPN3 router.
Here is the config of all devices:
Core Switch:
ip route 0.0.0.0 0.0.0.0 10.99.7.254
ip route 10.99.31.0 255.255.255.0 10.99.8.254
ip route 10.99.32.0 255.255.255.0 10.99.8.254
VPN3:
ip route 0.0.0.0 0.0.0.0 10.99.8.1
ip route 10.99.31.0 255.255.255.0 172.25.99.2
ip route 10.99.32.0 255.255.255.0 172.25.99.2
VPN4:
interface FastEthernet0/1.31
encapsulation dot1Q 31
ip address 10.99.31.254 255.255.255.0
!
interface FastEthernet0/1.32
encapsulation dot1Q 32
ip address 10.99.32.254 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 172.25.99.1
SW031:
interface Vlan31
ip address 10.99.31.1 255.255.255.0
!
interface Vlan32
ip address 10.99.32.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.99.31.254
is it correct ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 05:00 AM
Everything seems to be configured fine besides configuration on sw31. Did you try to make it work with current configuration and did it work?
SW031:
interface Vlan31
ip address 10.99.31.1 255.255.255.0
!
interface Vlan32
ip address 10.99.32.1 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.99.31.254
You don't need any of this configuration on SW31. You don't need to create SVIs for vlan 31 and 32 because they already have default gateway configured on router4. Also it doesn't need ip routing enabled and default gateway ip route 0.0.0.0 0.0.0.0 10.99.31.254. On sw31 all you need is a trunk port to router 4 that is already configured and access port for end hosts on vlan 31 and vlan 32.
is it correct ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 05:07 AM
Yes it is working means....from host in warehouse (10.99.32.200) i can ping all Data VLANs in Plant. Same applies to vlan 31.
Now i want that host should not have access to Dat VLANs..instead it must pass the traffic via DMZ interface of FW, which is connected on core switch.
Regarding SW031 Switch:
But then how i will access to this switch ?(I need a IP address of Switch have telnet/ssh access)
I don't need any route or default gateway on SW031 ?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 05:38 AM
Now i want that host should not have access to Dat VLANs..instead it must pass the traffic via DMZ interface of FW, which is connected on core switch.
What's the next hop or gateway from core switch to reach DMZ network?
Regarding SW031 Switch:
But then how i will access to this switch ?(I need a IP address of Switch have telnet/ssh access)
I don't need any route or default gateway on SW031 ?
If you want to use 2 SVIs for management then that's up to you. Lets say you remove svi for vlan 32 and you want to access the switch through telnet using svi for vlan 31 from a host that's on vlan 32, the host on vlan 32 would go to its DG on router 4 and router 4 will route the packet to switch address which is on svi 31 as router 4 is the gateway for both subnets/vlans. But that's up to you if you want to keep it the way the way it is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 05:50 AM
Hi,
Thanks for quick reply.
What's the next hop or gateway from core switch to reach DMZ network?
Core-switch is directly connected to firewall:
1. One interface for DMZ (Vlan 97 - 10.99.97.254)
2. All other LAN (Data vlans) - 10.99.7.254
If you want to use 2 SVIs for management then that's up to you.
I dont need two SVIs, just one (vlan 31) is enough to reach SW031. Just removed the vlan 32 SVI from SW031.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 06:21 AM
All your incoming traffic to site Plant lands at router 3 and it has a default route to core switch 10.99.8.1. So you will need to configure an acl on the core switch and apply it to the interface that has 10.99.8.1 configured on it.
How many vlans/subnets are there that you don't want warehouse network to access? can you summarize them? because with summarization it would be easier to configure ACL unless you only have handful.
Basically you want network 10.99.31.x and 32/24 to have access to 10.99.97.0/24 and deny everything else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 06:27 AM
Plant has many Data vlans (all SVIs are configure don Core switch for these vlans).
1. I want that network 10.99.31.0/24 must access everything in plant.
2. Network 10.99.32.0/24 must access only 10.99.97.0/24
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 06:50 AM
You can configure acl like this:
ip access-list extended 150
permit ip10.99.32.0 0.0.0.255 10.99.97.0 0.0.0.255
deny ip 10.99.32.0 0.0.0.255 any
permit ip any any
int x
ip access-group 150 in
you can either use a name or a number for extended acl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 07:01 AM
I will configure on Core-Swicth and let you know the result..
Question: If i conifgure like this then .....is vlan32 acting as DMZ interface ? As per my understanding we are just forwarding the vlan 32 traffic to vlan 97!!!
What i want is:
My whole traiic of vlan 32 must pass via DMZ interface , How can we achive this:
1. if FW is Default gateway of vlan 32
2. any other method ?
Sorry for my english ..
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 07:03 AM
I wouldn't say that vlan 32 is acting as a DMZ interface because it's not directly connected to the firewall so you are only restricting this vlan to talk to DMZ network at site plant. You are right about forwarding.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 07:06 AM
Thanks.
So what I need to do on firewall to forward the VLAN 32 traffic to outside as we are doing for other DMZ VLANs(97)!!
As you know that VLAN 97 IP is directly configured on firewall......
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2017 08:29 AM
You configured default gateway on router 4 for vlan 32 and that's where vlan 32 terminates, using firewall at another site as a default gateway for vlan 32 wouldn't work because you are traversing other IP networks to reach gateway for vlan 32 and that was the reason we came up with this design. You will have to restrict traffic using ACLs at core switch so vlan 32 can't access anything else besides DMZ network behind the firewall at site plant. Vlan 32 and DMZ networks are behind two separate interfaces on the firewall, and you can't move subnet 32 behind the DMZ interface of firewall at site plant since it's geographically at a different location and reaches site plant through the tunnel.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide