- Cisco Community
- Technology and Support
- Networking
- Routing
- GRE/IPSEC: NAT configuration ´route-map´ not available PT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GRE/IPSEC: NAT configuration ´route-map´ not available PT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 03:31 PM
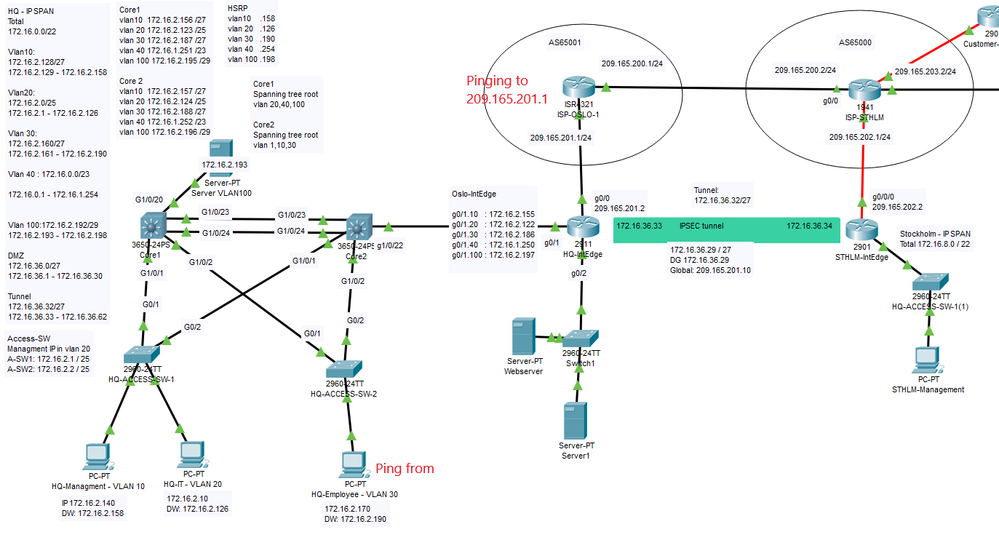
Hi, Could someone help me to understand where it goes wrong with my ping from Local Net to Public? The IPs are beeing transformed via NAT but it won't come back in so I guess there's an issue with my ACLs. I recently set up IPSec so did a few changes to my ACLs. From what I read it could be that I should use a ```route-map nonat``` but that command doesn't seem to exist in PT
!HQ-IntEdge ! crypto isakmp policy 1 encr aes authentication pre-share group 5 ! crypto isakmp key petter address 209.165.202.2 ! ! ! crypto ipsec transform-set HQ-STHLM esp-aes esp-sha-hmac ! crypto map HQ-STHLM_MAP 10 ipsec-isakmp set peer 209.165.202.2 set pfs group5 set security-association lifetime seconds 900 set transform-set HQ-STHLM match address 101 ! ! interface Tunnel0 ip address 172.16.36.33 255.255.255.224 mtu 1476 tunnel source GigabitEthernet0/0 tunnel destination 209.165.202.2 ! interface GigabitEthernet0/0 ip address 209.165.201.2 255.255.255.0 ip access-group INBOUND in ip nat outside duplex auto speed auto crypto map HQ-STHLM_MAP ! ip nat inside source list NAT_ACL interface GigabitEthernet0/0 overload ip nat inside source static 172.16.36.29 209.165.201.3 ip nat inside source static tcp 172.16.36.28 80 209.209.201.2 80 ! ip access-list extended INBOUND permit ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255 permit icmp host 209.165.202.2 host 209.165.201.2 permit udp host 209.165.202.2 host 209.165.201.2 eq isakmp permit esp host 209.165.202.2 host 209.165.201.2 permit ahp host 209.165.202.2 host 209.165.201.2 deny ip any any access-list 101 permit ip 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255 access-list 101 permit ip any any access-list 101 permit gre 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255 ip access-list extended NAT_ACL deny ip 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255 permit ip 172.16.0.0 0.0.3.255 any ! !STHLM-IntEdge ! crypto isakmp policy 1 encr aes authentication pre-share group 5 ! crypto isakmp key petter address 209.165.201.1 crypto isakmp key petter address 209.165.201.2 ! crypto ipsec transform-set HQ-STHLM esp-aes esp-sha-hmac ! crypto map HQ-STHLM_MAP 10 ipsec-isakmp set peer 209.165.201.2 set pfs group5 set security-association lifetime seconds 900 set transform-set HQ-STHLM match address 102 ! interface Tunnel0 ip address 172.16.36.34 255.255.255.224 mtu 1476 tunnel source GigabitEthernet0/0/0 tunnel destination 209.165.201.2 ! interface GigabitEthernet0/0/0 ip address 209.165.202.2 255.255.255.0 ip access-group INBOUND in crypto map HQ-STHLM_MAP ! ip nat inside source list NAT_ACL interface GigabitEthernet0/0/0 overload ! ip access-list extended INBOUND permit ip 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255 permit icmp host 209.165.201.2 host 209.165.202.2 permit udp host 209.165.201.2 host 209.165.202.2 eq isakmp permit esp host 209.165.201.2 host 209.165.202.2 permit ahp host 209.165.201.2 host 209.165.202.2 deny ip any any access-list 102 permit ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255 access-list 102 permit ip any any access-list 102 permit gre 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255 ip access-list extended NAT_ACL remark ****** NAT ACL ****** deny ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255 permit ip 172.16.8.0 0.0.3.255 any !
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2019 11:26 PM
Hello,
the access lists you use are slightly wrong. Take out the lines marked with an '-->' and leave the lines marked in bold:
HQ-IntEdge
access-list 101 permit ip 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255
--> no access-list 101 permit ip any any
--> no access-list 101 permit gre 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255
!
ip access-list extended NAT_ACL
deny ip 172.16.0.0 0.0.3.255 172.16.8.0 0.0.3.255
permit ip 172.16.0.0 0.0.3.255 any
STHLM-IntEdge
access-list 102 permit ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255
--> no access-list 102 permit ip any any
--> no access-list 102 permit gre 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255
!
ip access-list extended NAT_ACL
remark ****** NAT ACL ******
deny ip 172.16.8.0 0.0.3.255 172.16.0.0 0.0.3.255
permit ip 172.16.8.0 0.0.3.255 any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2019 03:28 AM
By removing these lines I seem to also lose my EIGRP exchange over the two sites? How am I supposed to exchange the EIGRP information over the tunnel without these lines?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide