- Cisco Community
- Technology and Support
- Networking
- Routing
- How can I make NAT on a Stick (Cisco 881)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2012 03:05 AM - edited 03-04-2019 05:19 PM
I try to make Nat on a stick, but not successful. Can somebody give me a hand?
Network Diagram
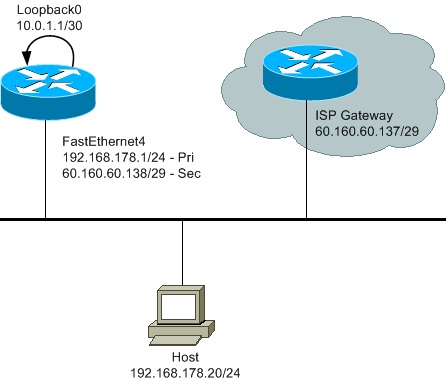
Config File
interface Loopback0
ip address 10.0.1.1 255.255.255.252
ip nat outside
ip virtual-reassembly
!
!
interface FastEthernet0
!
!
interface FastEthernet1
!
!
interface FastEthernet2
!
!
interface FastEthernet3
!
!
interface FastEthernet4
ip address 60.160.60.138 255.255.255.248 secondary
ip address 192.168.178.1 255.255.255.0
ip nat inside
ip virtual-reassembly
ip policy route-map Nat-loop
duplex auto
speed auto
!
!
ip nat pool external 60.160.60.139 60.160.60.139 netmask 255.255.255.248
ip nat inside source list 10 pool external overload
ip route 0.0.0.0 0.0.0.0 60.160.60.137
ip route 192.168.178.0 255.255.255.0 FastEthernet4
!
access-list 10 permit 192.168.178.0 0.0.0.255
access-list 102 permit ip 192.168.178.0 0.0.0.255 any
access-list 102 permit ip any 60.160.60.0 0.0.0.7
no cdp run
!
!
!
!
route-map Nat-loop permit 10
match ip address 102
set interface Loopback0
!
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2012 03:30 AM
Hello,
Try swapping the inside/outside designations on the loopback and the Fa4 interface, i.e. the Loopback0 should be configured with ip nat inside while the Fa4 should be configured with ip nat outside. This is because the return traffic first hits the Fa4 interface, and following the logic of NAT, the first interface must be the outside interface in order for the backward translation to take place.
In addition, remove the second entry from your ACL 102 (the one with the public range). You should not need to take special care about the return traffic with the modification I have suggested.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2012 03:30 AM
Hello,
Try swapping the inside/outside designations on the loopback and the Fa4 interface, i.e. the Loopback0 should be configured with ip nat inside while the Fa4 should be configured with ip nat outside. This is because the return traffic first hits the Fa4 interface, and following the logic of NAT, the first interface must be the outside interface in order for the backward translation to take place.
In addition, remove the second entry from your ACL 102 (the one with the public range). You should not need to take special care about the return traffic with the modification I have suggested.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2012 11:09 PM
Thank you, Peter. I will try it...
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
