- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: how to configure ACL on routers?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 10:37 AM
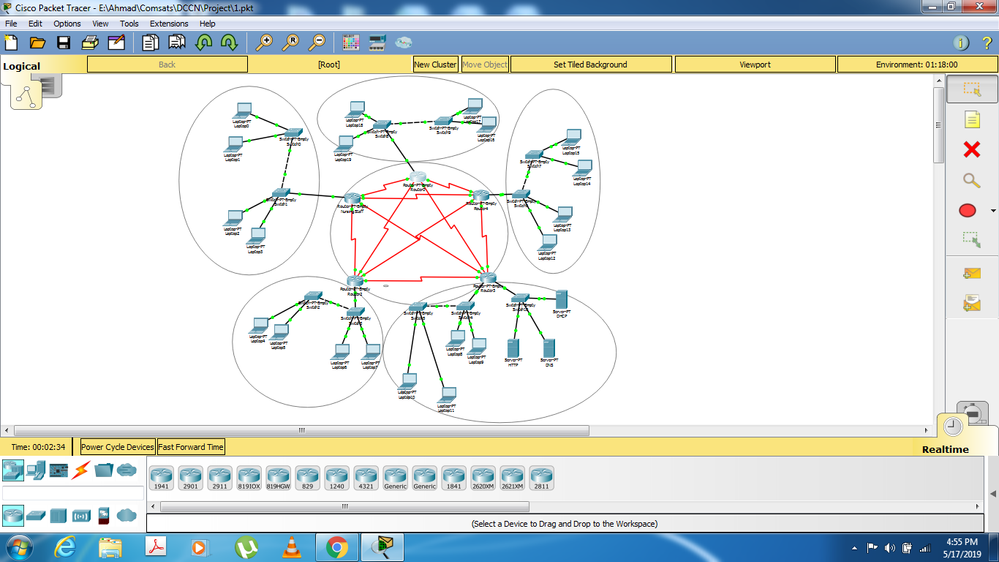
I am given a topology in which I have to apply ACL. The PCs in the left bottom side are not to be accessed by any other PCs. This was done successfully as follows:
access-list 1 deny any
access-list 1 permit any
int fa 0/0
ip access-group 1 out
Now the next task is that the top router should be only accessed by the the PCs in the left side and the ones in the left bottom. How do I do that?
Solved! Go to Solution.
- Labels:
-
Other Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 11:06 AM
Your ACL also blocks the routers and servers; don't know if you intended that too. Also since your first ACL statement is deny any, the subsequent permit any will never be reached.
"Now the next task is that the top router should be only accessed by the the PCs in the left side and the ones in the left bottom. How do I do that?"
That depends on what you mean by "accessed" and also by your network addressing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2019 01:38 PM
access-list extended AllowOnlyPings
permit icmp any any type 0
permit icmp any any type 8
Applied the above (named) ACL to the interfaces facing into the switches whose hosts you want to control. Applying for either in or out should do the job but you can also apply the ACL for both in and out.
BTW, if you're wondering, every ACL has an implicit deny all as the last entry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 11:06 AM
Your ACL also blocks the routers and servers; don't know if you intended that too. Also since your first ACL statement is deny any, the subsequent permit any will never be reached.
"Now the next task is that the top router should be only accessed by the the PCs in the left side and the ones in the left bottom. How do I do that?"
That depends on what you mean by "accessed" and also by your network addressing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 11:25 AM
access-list 1 permit any
access-list 1 deny any
int fa 0/0
ip access-group 1 out
I tried this too but now the deny statement is not working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2019 08:38 AM
Regarding the meaning of "accessed", an ACL can block or only allow "ping" packets. Is that what you want or do you also want to be selected with other traffic? Your original ACL is an all or nothing ACL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-07-2019 10:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2019 05:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2019 07:43 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2019 01:38 PM
access-list extended AllowOnlyPings
permit icmp any any type 0
permit icmp any any type 8
Applied the above (named) ACL to the interfaces facing into the switches whose hosts you want to control. Applying for either in or out should do the job but you can also apply the ACL for both in and out.
BTW, if you're wondering, every ACL has an implicit deny all as the last entry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-06-2019 11:11 AM
Hello,
if accessing the top router means be able to telnet/ssh to the router the exercise is asking you to build an ACL that will be applied to the line vty (that are the logical entities that can accept incoming telnet/SSH sessions).
For example:
192.168.5.0/24
and
192.168.20.0/24 must be able to telnet to the router:
access-list 5 pemit 192.168.5.0 0.0.0.255
access-list 5 permit 192.168.20.0 0.0.0.255
line vty 0 4
access-class 5 in
login
Note the ACL is not applied to a physical interface but to the line vty range.
This is usually what is meant with control who can access the router shell.
Hope to help
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide