- Cisco Community
- Technology and Support
- Networking
- Routing
- How transparent devices don't discard frames?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2010 05:31 AM - edited 03-04-2019 10:22 AM
Some devices like firewalls can be configured in Tranparent mode. Please take a look at below figure.
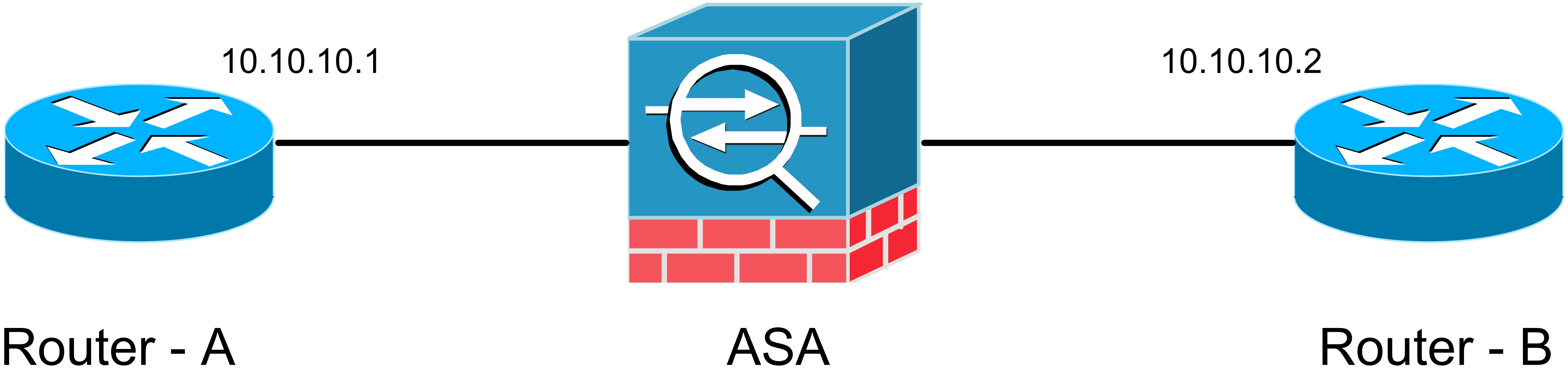
Router A tries to send a packet to router B so it will encapsulate the packet with Data Link header and trailer. Source address is MAC of router A and destination address is MAC address of router B. The Frame receives by ASA. When ASA checks destination address it will find that this frames is not belonged to it but not only ASA doesn't discard but also it will decapsulate it and do inspecting other layers.
It's not clear for me that how the transparent device decapsulates the frame since the destination MAC address is differ from its MAC. Such devices even can not be seen by trace route because that they don't change TTL value.
Thank you,
Solved! Go to Solution.
- Labels:
-
Other Routing
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2010 05:39 AM
Hello Ali,
I don't know in detail how this is technically accomplished in the ASA in particular but you can always direct an Ethernet card to process all received frames (put it into the promiscuous mode). An Ethernet NIC put into promiscuous mode will pass all received frames to the operating system for processing. The operating system can then perform inspection of the frame's contents and make a decision whether the frame shall be forwarded unmodified or dropped. This is how I personally understand the operation of the ASA in the transparent mode.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2010 06:53 AM
Hello Ali,
as noted by Peter the ASA in transparent mode acts as a LAN bridge with the additional duties of packet inspection to decide if the packet has to be permitted or not.
For example: before communication can happen the ASA has to allow the ARP resolution process to happen normally allowing ARP requests from left to right and right to left as necessary and ARP replies in the opposite direction as well.
So the ASA in transparent mode can be seen as a LAN bridge that will forward frames from left to right if permitted by security rules ( ACLs, NAT rules, securty levels ad so on).
>> Such devices even can not be seen by trace route because that they don't change TTL value.
Because it acts as a L2 LAN switch as stated above. We could call it a conditional bridge (it will bridge like a LAN switch if some conditions are met)
Notice also that until recent OS versions transparent contexts were limited to only two interfaces (at least on FWSM).
The typical use of a firewall in transparent mode is when multicast traffic has to flow through it : in routed mode this can be a problem (again at least with FWSM blade implementation).
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2010 05:39 AM
Hello Ali,
I don't know in detail how this is technically accomplished in the ASA in particular but you can always direct an Ethernet card to process all received frames (put it into the promiscuous mode). An Ethernet NIC put into promiscuous mode will pass all received frames to the operating system for processing. The operating system can then perform inspection of the frame's contents and make a decision whether the frame shall be forwarded unmodified or dropped. This is how I personally understand the operation of the ASA in the transparent mode.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-05-2010 10:04 PM
Hi Peter,
Thank you for your reply. I got it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2010 06:53 AM
Hello Ali,
as noted by Peter the ASA in transparent mode acts as a LAN bridge with the additional duties of packet inspection to decide if the packet has to be permitted or not.
For example: before communication can happen the ASA has to allow the ARP resolution process to happen normally allowing ARP requests from left to right and right to left as necessary and ARP replies in the opposite direction as well.
So the ASA in transparent mode can be seen as a LAN bridge that will forward frames from left to right if permitted by security rules ( ACLs, NAT rules, securty levels ad so on).
>> Such devices even can not be seen by trace route because that they don't change TTL value.
Because it acts as a L2 LAN switch as stated above. We could call it a conditional bridge (it will bridge like a LAN switch if some conditions are met)
Notice also that until recent OS versions transparent contexts were limited to only two interfaces (at least on FWSM).
The typical use of a firewall in transparent mode is when multicast traffic has to flow through it : in routed mode this can be a problem (again at least with FWSM blade implementation).
Hope to help
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

