- Cisco Community
- Technology and Support
- Networking
- Routing
- Hub Spoke Design with BGP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Hub Spoke Design with BGP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2019 06:43 PM
Hi All,
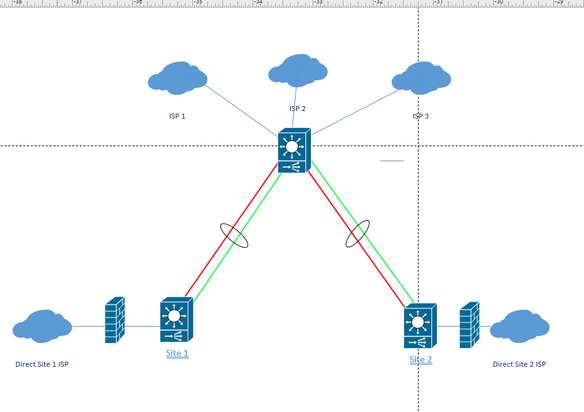
I need help in designing a network. Im currently planning to migrate the core to a Data Center. Below is the initial topology for 2 test sites.
Current Setup
1. Each Site has a Firewall and a Direct Internet Connectivity, Core of sites is connected via P-P links bundled via LAG so incase the Direct Internet on Site 1 goes down it has a backup connection thru the Hub Site which has 3 ISP. All LAN, NAT, DHCP, CFS, GAV and other security services are on a per-site basis.
Proposed Setup
For the proposed setup I am planning to migrate the Hub to a Data Center (DC 1 and DC 2), create an external peering via eBGP to 4 ISPs Form an iBGP with DC 1 and DC 2. I am also planning to use OSPF as the IGP for the Data Center to Sites, configure each Site as an individual area and make it Totally Stubby so Default Route will be created pointing towards DC 1 and DC 2. I have the following problems and questions.
1. Currently all LAN subnets are behind a firewall, firewall is also hosting the DHCP, Content Filtering and Routing. My question is once I migrated the ISPs to the Data Center what changes do I need to make on the firewall. Will I configure NAT on the firewall on a per site basis or will I configure NAT on both DC.
2. We currently have clients that have their own network and we will provide a Public IP Address to them so they can get out of the Internet, are there any additional configuration needed on their end aside from the default route pointing to the IP of the Site Core because client networks wont be participating the OSPF process.
IP block and AS numbers are made up, also I limit the design to two spokes but we have much more than 2 sites.
Hope you can help me. Any help would be appreciated.
Thank You.
- Labels:
-
Routing Protocols
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 12:05 AM
Hello dabechu,
this is not an easy question and not all the details are clear.
In this post I provide some suggestions and I put some questions.
a) routing aspects
I would use totally NSSA OSPF areas for the spoke sites, because if there is a need in the future to redistribute routes in a spoke site the NSSA type allows to do that, totally stub areas do not allow to have ASBR nodes within a site.
You get the same level of control on external routes coming from the backbone ( all of them are blocked at area boundary) and you have the freedom to adapt to possible needs.
b) NAT
>> Currently all LAN subnets are behind a firewall, firewall is also hosting the DHCP, Content Filtering and Routing. My question is once I migrated the ISPs to the Data Center what changes do I need to make on the firewall. Will I configure NAT on the firewall on a per site basis or will I configure NAT on both DC.
Here, it depends on three factors:
b1) are the per site firewalls able to run OSPF ?
If they are you can put them on the path to the DCs at OSI layer 3 (IP routing) and you can perform NAT on them.
Be aware that some firewalls like Cisco ASA may require two different outgoing interfaces to be able to handle multiple default routes.
b2) Have you got your own public IP address block for each site ?
b3) how do you want to make spoke to spoke site communication possible ?
Do you need to use NAT also for spoke site to spoke site communication or NAT is needed only for Internet access ?.
If NAT is needed only for Internet access this can be a point for using NAT on the two DCs.
However the site firewall NAT configuration can be changed to avoid to use NAT (NAT exemption or NAT 0 in Cisco ASA terms) for spoke to spoke communication.
I have a question about your clients.
Where are they connected to your network ?
Do they connect to the central site only or they can connect to a spoke site if needed ?
in the latter case, because you stated that clients do not take part in OSPF you may need to redistribute on spoke sites and so the suggestion to use NSSA areas instead of stub areas.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-06-2019 12:43 AM
Hi Giuseppe,
First of let me extend my thanks for taking the time to review my post. I have answered your questions, hoping you help me even further.
"
Here, it depends on three factors:
b1) are the per site firewalls able to run OSPF ? Firewalls on site are able to run OSPF im planning to join them in the OSPF Process
If they are you can put them on the path to the DCs at OSI layer 3 (IP routing) and you can perform NAT on them.
Be aware that some firewalls like Cisco ASA may require two different outgoing interfaces to be able to handle multiple default routes.
b2) Have you got your own public IP address block for each site? I have a /23 IP Block owned by the company and planning to subnet it and allocate it on a per-site basis but will advertise a /24 and /23 towards the eBGP Peers.
b3) how do you want to make spoke to spoke site communication possible ? Spoke to spoke communication would be thru OSPF since Spokes are configured as NSSA it will just have a Default Inter Area Route going to the Data centers
Do you need to use NAT also for spoke site to spoke site communication or NAT is needed only for Internet access ? No needed for NAT on a site to site basis
If NAT is needed only for Internet access this can be a point for using NAT on the two DCs.I have this as an alternative option on a per-site NAT, I can configure NAT on the Data Center or add a firewall and configure NAT there so I wouldn't burden the process of the router on the DC. If the budget doesn't allow putting a firewall on a DC ill still configure NAT on the firewall onsite.
I have a question about your clients.
Where are they connected to your network? Clients that have their own network is connected to the Central Switch of a spoke, since these clients only need Internet Access and a spoke has already a Direct Internet Access we provide a public IP and they set it on their router.
Do they connect to the central site only or they can connect to a spoke site if needed? Clients only connect to spoke sites
"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide